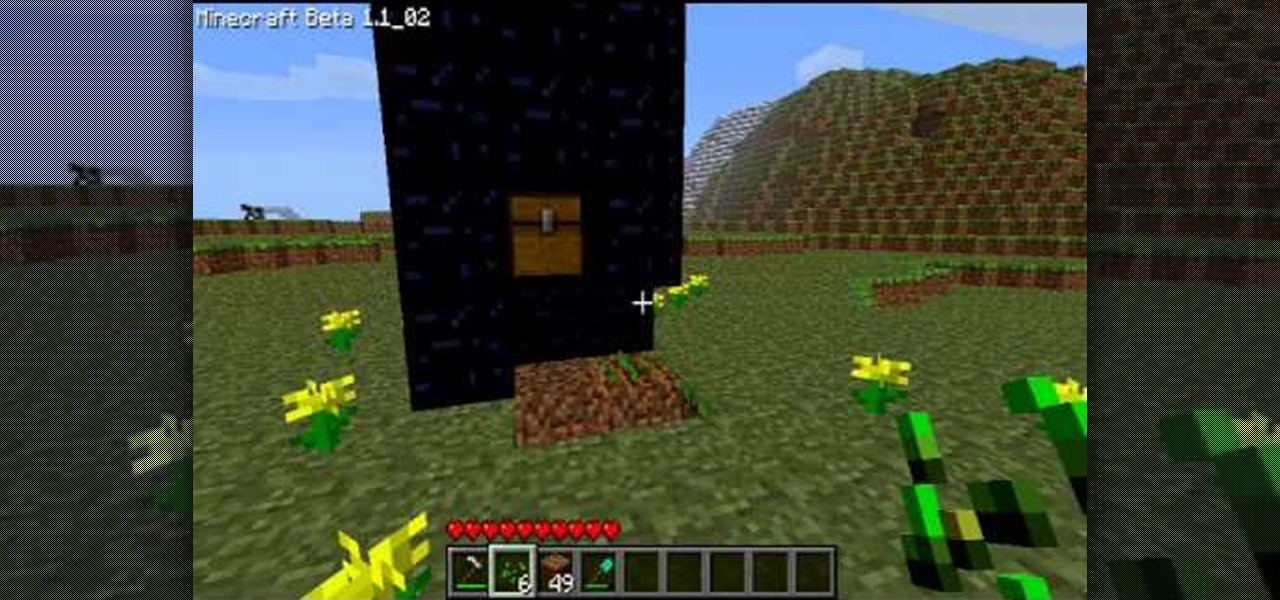
Even if there's a giant block of obsidian, you can figure out a way to exploit a glitch that will let you easily break into it. You're also shown a way to easily break into protected chests on shared servers in Minecraft.
Learn how to password protect your Motorola Droid Google Android smartphone. Whether you're the proud owner of a Froyo Motorola Droid or are just considering picking one up, you're sure to be well served by this video guide. For more information and detailed step-by-step instructions, watch this phone hacker's how-to.

If you have a big beautiful lawn and live somewhere with cold winters, you probably already know about how to winterize your lawn and how doing so can protect your lawn in the winter and make it grow better in the spring. If you don't, watch this video.

If you live somewhere with harsh winters, you know that they can be hell on your garden and the flower pots therein. Watch this video for tips on protecting different kinds of flower pots from the elements during the winter.

During the winter and freak weather events in spring and fall your garden can take a beating from frost and excess cold. Watch this video to learn how you can protect your plants and flowers during the cold so they are healthy and ready to grow when the weather improves.
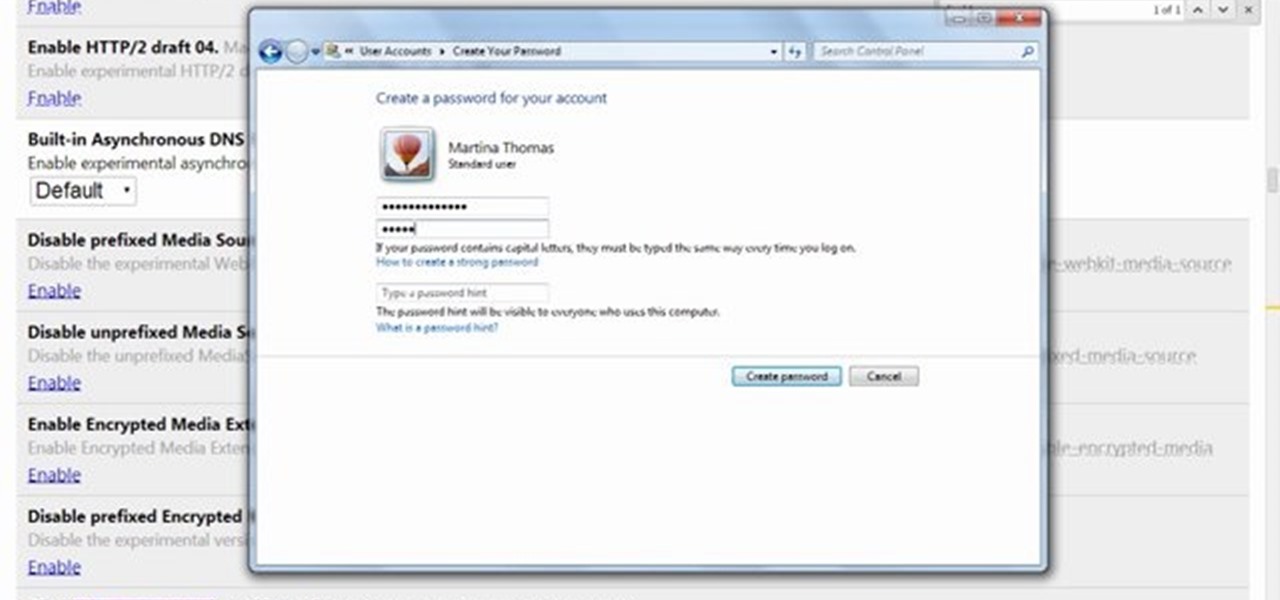
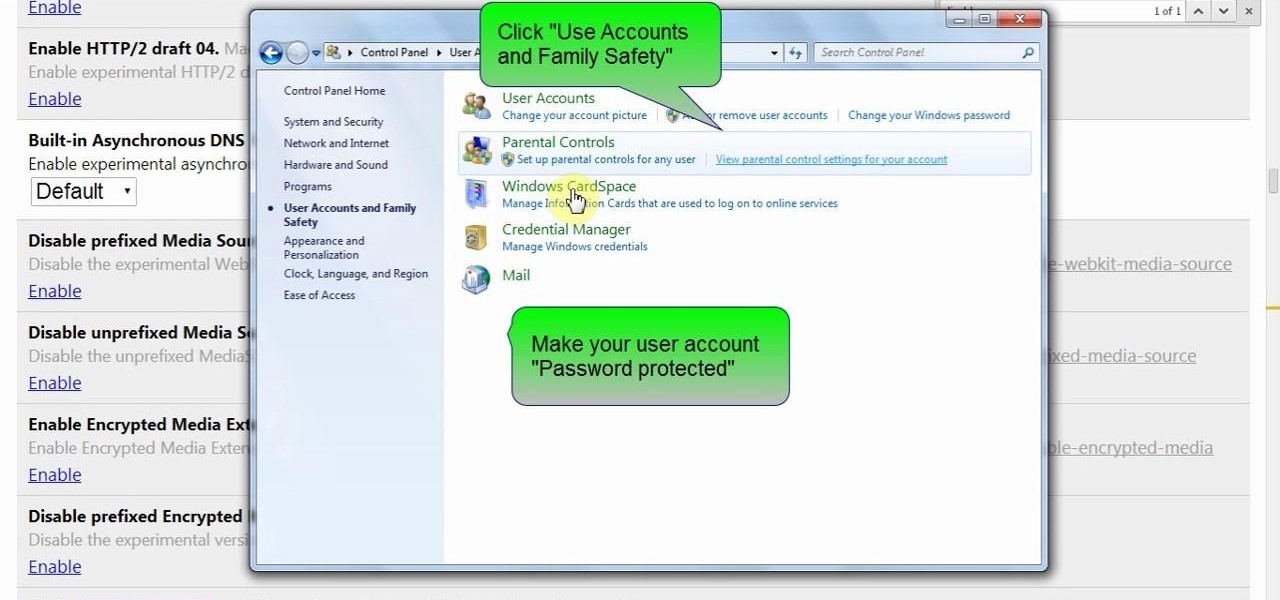
In this clip, you'll learn how to secure a new Microsoft Windows desktop or laptop computer. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started protecting your own new Microsoft Windows PC, take a look.

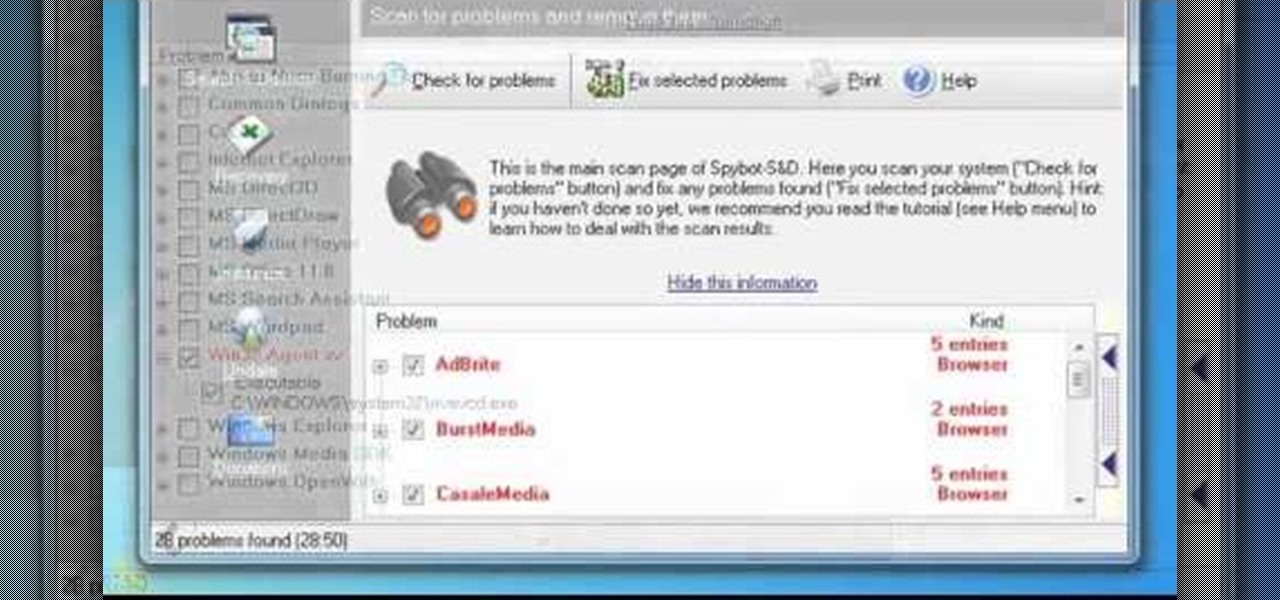
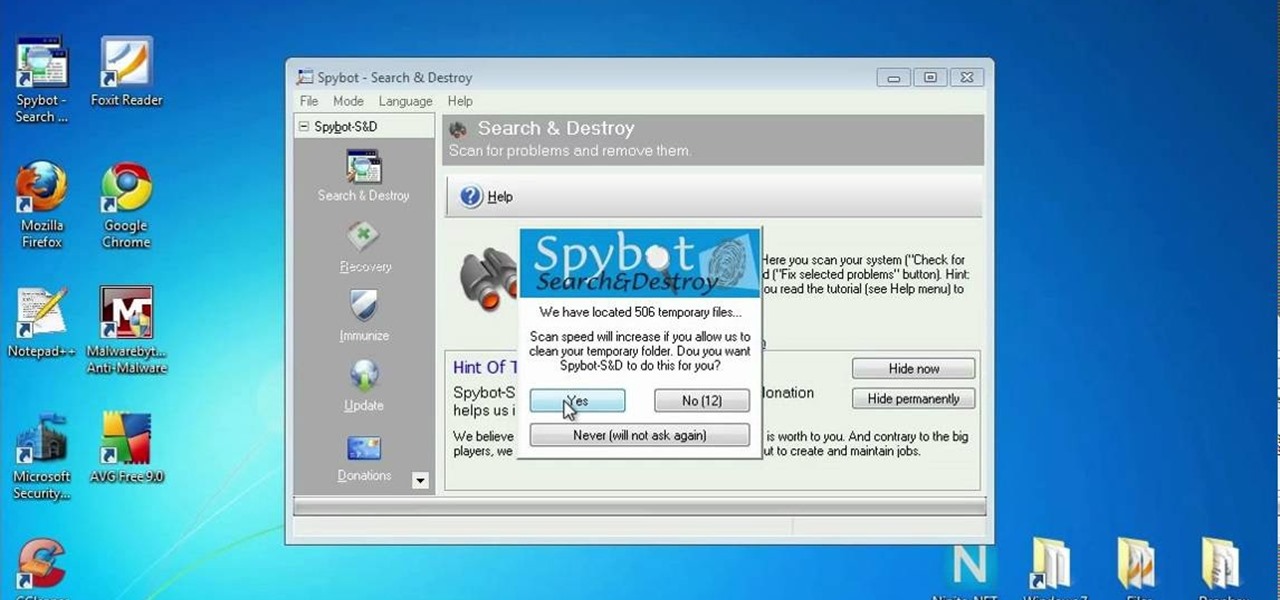
In this clip, you'll learn how to use the free Spybot Search & Destroy tool to protect against and remove malware on a Microsoft Windows PC. For more information, including detailed, step-by-step instructions, and to get started using Spybot on your own Win PC, take a look.

Looking for an easy way to protect your privacy when using Google Search? With the right habits, it's easy. So easy, in fact, that this home-computing how-to from the folks at CNET can present a complete overview of the process in just over a minute. For more information, including detailed, step-by-step instructions, take a look.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.

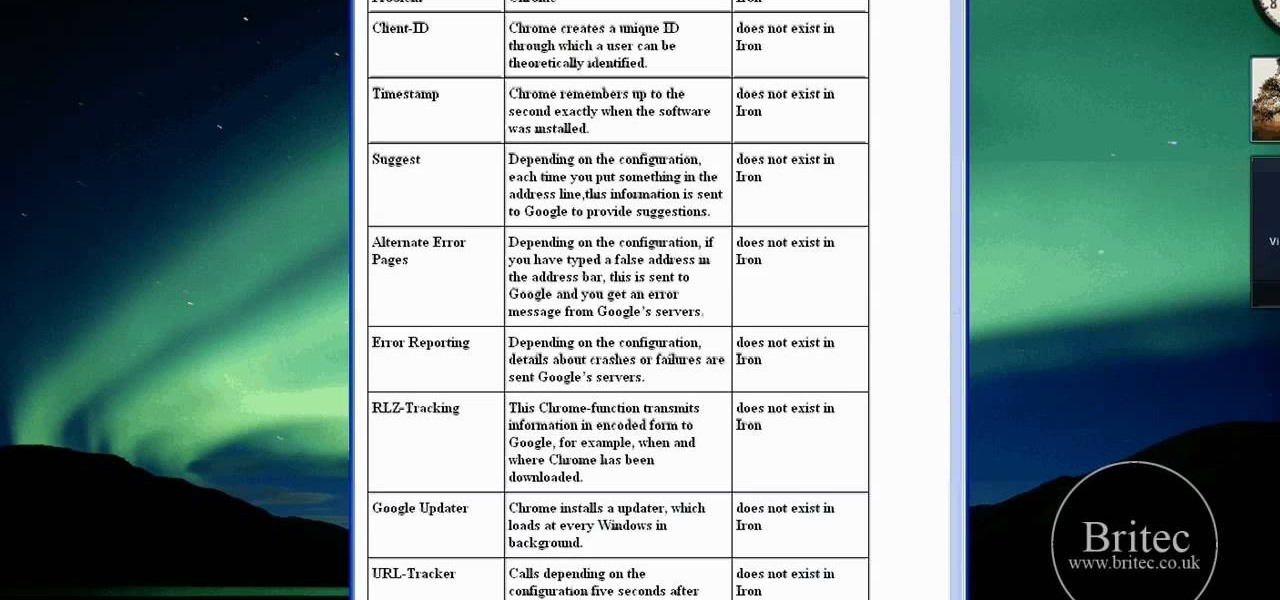
Interested in using Google Chrome but concerned about protecting your privacy while surfing the web? Meet Iron Browser, a secure but otherwise identical clone of the Google Chrome web browser. This clip from Britec will teach you where to find it, how to install it and how to get started using it.

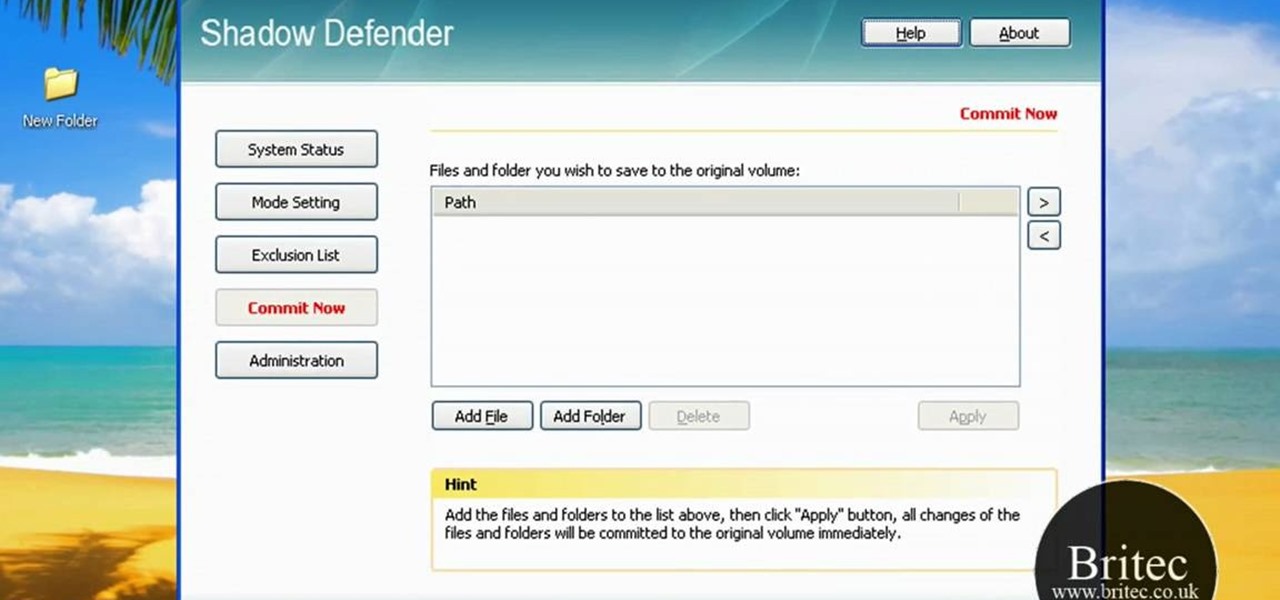
Looking for a security solution for your Microsoft Windows PC? With Shadow Defender, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under ten minutes. For more information, including step-by-step instructions on how to get started using Shadow Defender to protect your own desktop computer or laptop, take a look.

If you're restoring an old vehicle, it's always important to make sure you take the necessary precautions for preventing any damage. In this particular video tutorial, you'll find out how to protect your door panels on a classic VW Beetle Bug without any problems. So good luck, pay attention, and enjoy!

As any SLR or DSLR owner knows all too well, the price of lenses can often approach or even exceed the cost of your camera. As such, it's important that you take the necessary precautions to protect them. With this free photographer's guide, you'll learn about using UV (that is, ultra-violet) filters to protect your single lens-reflex camera lenses from sun damage.

If you live in a hurricane prone area, it is a good idea to protect your windows with security film. This video will teach you how to install hurricane security window film on your own and protect your home and assets.

Need to unlock your music? Want to save Rhapsody or Napster files on more than your own computer? This is how to unlock, remove drm and convert protected wma files from napster and rhapsody to mp3 without having to pay for them. Also how to put napster and rhapsody files in iTunes and on your iPod.

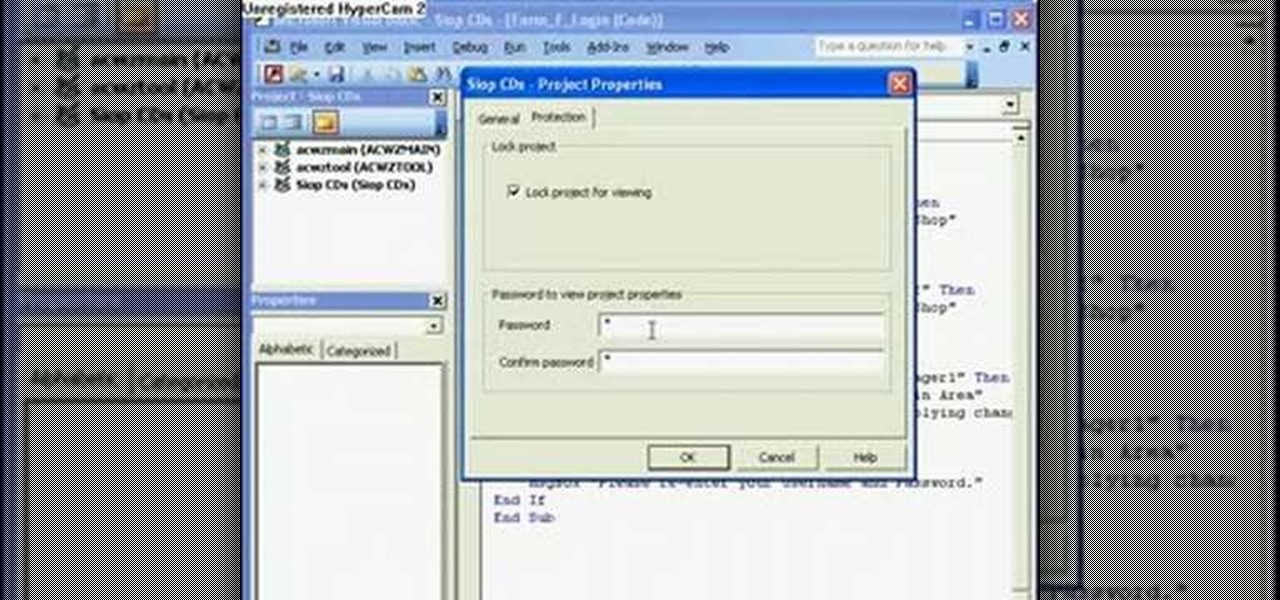
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about protecting your VBA code from snoopy little trolls. For more information on keeping your VBA code secure, watch this MS Access how-to.

Sadly, into each life at least one mean, nasty, low-down, no-good boss must fall. When it's your turn, you'll want these survival tips. Trying to remain calm and protecting yourself are important strategies to protect your career. Watch this video job skills tutorial and learn how to cope with an unfair boss.

In this video Bob Schmidt shows you how to protect yourself when working with fiberglass insulation when insulating or doing removals during your home improvement projects.

Watch this video to learn how to make a password protected video.

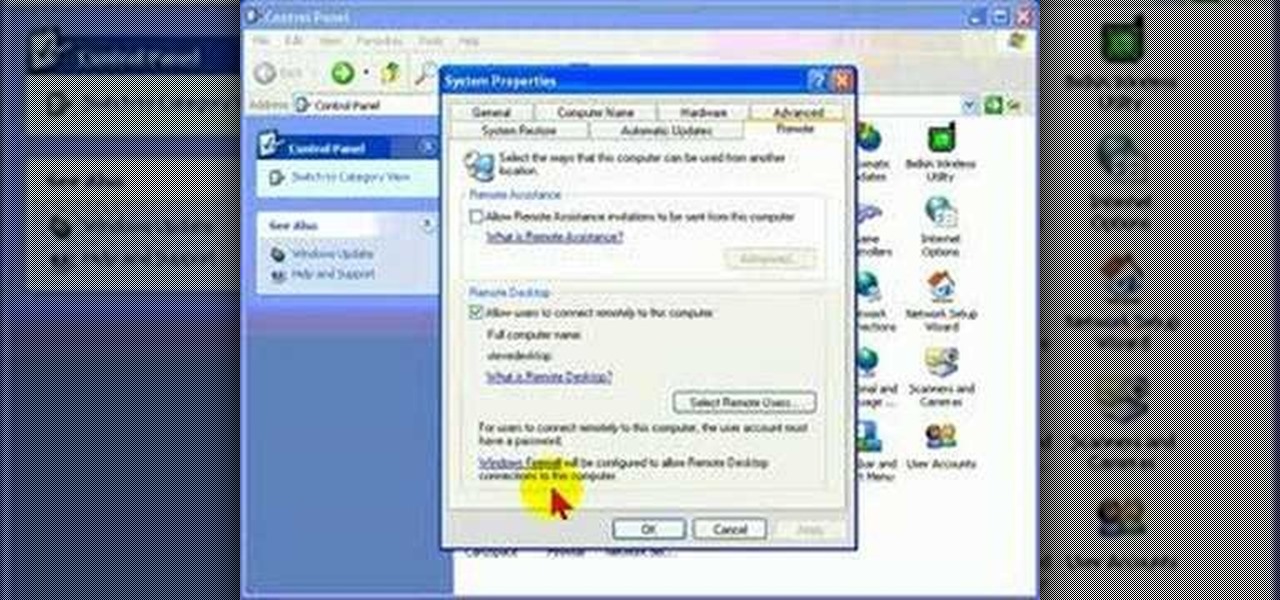
Remote Desktop is a feature of Microsoft Windows, that allows you to access your PC from anywhere in the world, and use it as if you were sat right in front of it.

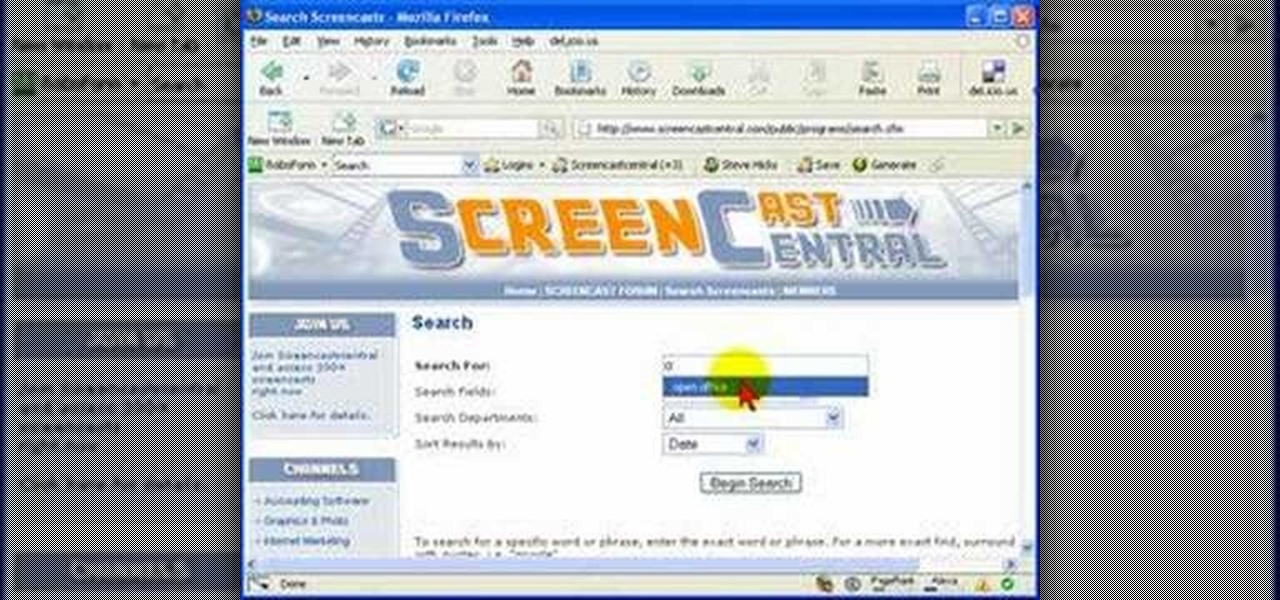
One method you can use to protect yourself, is to ensure you clear your private data, such as your search history, and in this screencast tutorial, we show you how to do just that in Mozilla Firefox.

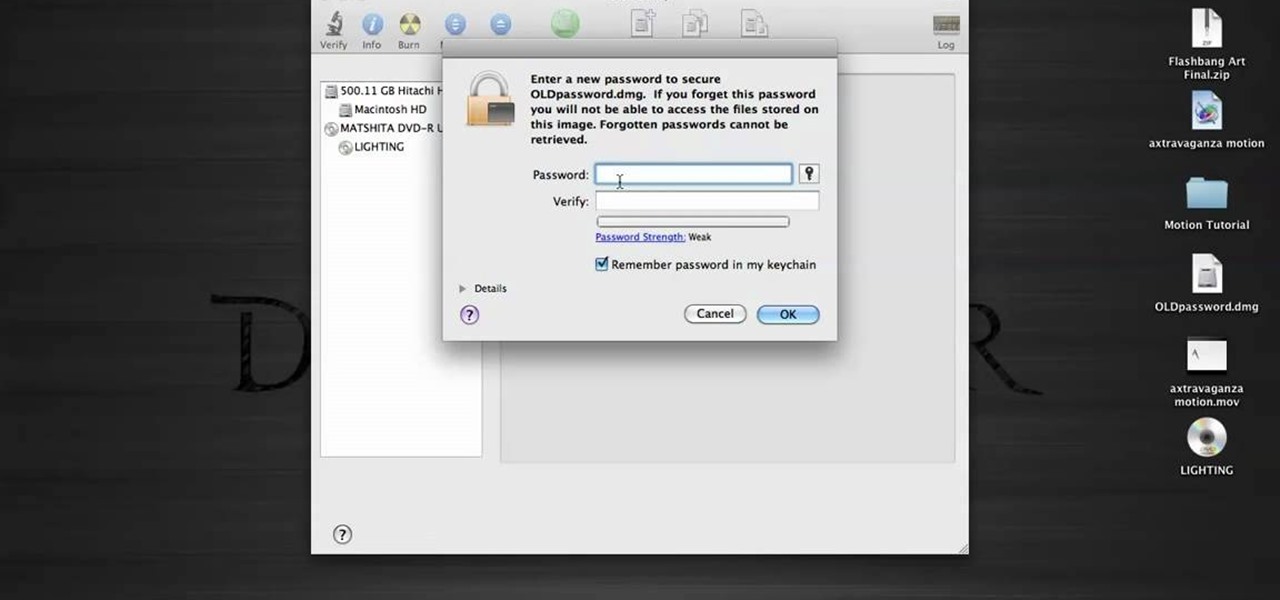
Gary Rosenzweig from MacMost looks at one method to protect a set of files with a password on a Mac. It involves using Disk Utility to create an encrypted disk image.

Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.

This video segment will show you how to protect your LCD or DLP TV which is susceptible to irreparable damage. We can build you a custom screen for far less cost that a TV repair.

Andrew Burke from Videomaker magazine gives some advice for protecting your equipment while shooting in the rain.

Want to make your fingers look like they have flames shooting out of them? Learn how to protect your fingers while they are ablaze and make your friends think you are impervious to pain. Use easy to find material to protect your fingers while you light each one on fire.

Once you've patched all of the cracks and potholes in your home driveway, it's time for protecting it from further damage. Sealing your driveway will protect from further ghastly and bothersome cracks and potholes. Lowe's knows what works best— QPR's Professional Grade Driveway Sealer.

In this video, we learn how to use the reverse hyper to protect and rehab the back. First, you need to lay down on the machine correctly. Make sure your core is out and your arms are holder the levers. Now, lift your legs up on the straps and slowly lower them down. Continue to do this as you work out, this will result in a great work out in just a few reps. As you continue to do this you will be able to do heavier weights. This will help protect your back from injury and get it back into shape!

In this video, we learn how to protect your privacy while using Twitter. Your personal information can get stolen in an instant with the internet. With Twitter, when you are doing updates showing where you are and what you are doing, someone could try to find you and potentially create harm to you. To help you avoid situations like this, you need to go to the security settings of your Twitter account. When you go here, you can change the account so that it only allows people you want to follo...

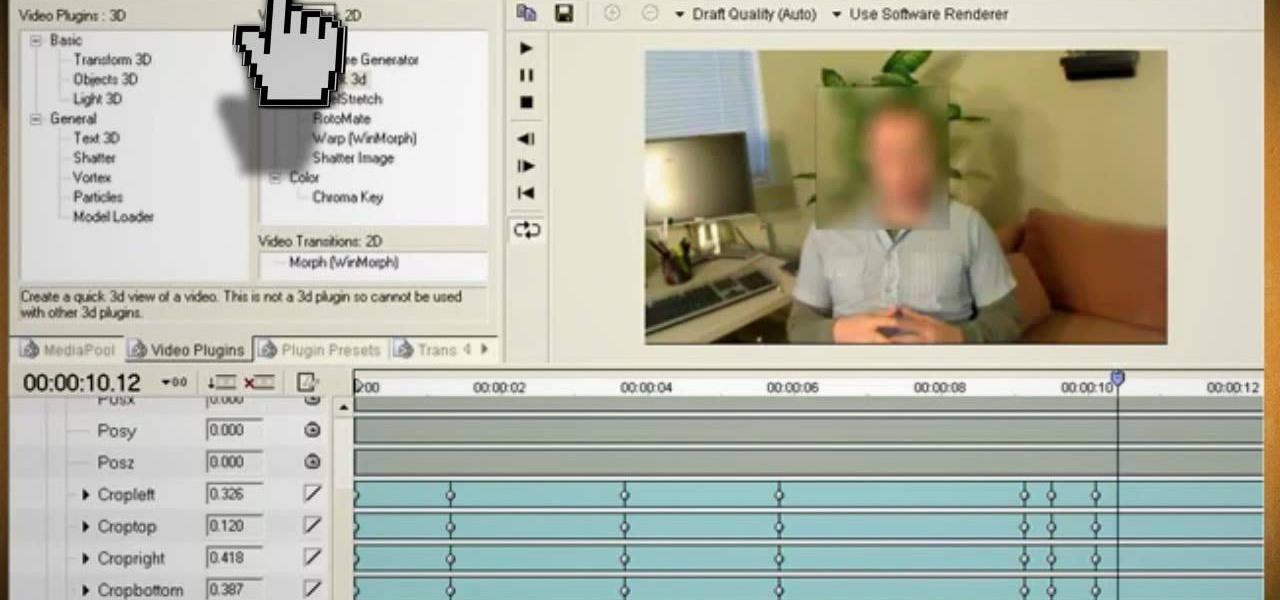
Watch this video and learn how to protect your identity on the internet. This clip will help you learn how to blur out your face and alter your voice when posting videos on the web, where your identity is an important secret. Stay anonymous while portraying your opinions. This software can also be used to avoid release issues with strangers in the backgrounds of your videos. Preventing passers by from having there picture posted with your opinions opening you up for legal action. This can als...

Ever have the problem of people messing with your word documents? This guy shows you the solution by telling you how to create password protected encrypted word documents. The process starts with your open file. Clicking on save as... and in the popup window clicking the tools button in the bottom left corner and clicking general options. There it shows you text entry boxes, one for setting a password to open the file, another to set a password for rights to modify the file. Enter your passwo...

Sick of damaging your hair with all the products and flat irons? Those products don't have to cause your hair damage if used correctly. In this two-part hair video tutorial, learn how to blow dry and flat iron long hair in a way that does not cause damage. Blow dry your hair and minimize the heat damage and breakage by following the tips in these two videos. Shampoos & conditioners are are also gone over, as well as how to use a flat iron minimally to get the results you want, with less damage.

Using blue tape and a dental bib during tattooing to protect a portable tattoo armrest from ink and blood. The process of protecting the armrest is simple. This process would prevent ink from being transferred to another person or even onto their clothes. Using the dental bib you place it over an armrest and use blue 3m tape to secure the dental bib. Once this is done you are ready to start tattooing. Very cost effective and efficient way to protect an armrest and others.

Samsung and Hulu have gotten together in a big way to partner the Huluplus interface with Samsung TV's and Blu-Ray players and allow Samsung users easy access to Hulu's massive library of TV shows and movies. This video will show you how the system works on a Samsung Blu-Ray player.

In this video, we learn how to protect yourself and your mattress from bed bugs. These bugs live in your bed and hide anywhere in your home and even hotels. To see if you have them, you will see blood stains on your mattress and look on your skin for any bites you may have. If you suspect you have them, you should call a professional to help take care of the problem. Check the edges and corners of your bed to see if you have been infested with bed bugs, and look at the label as well. Be caref...

This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

This video will show you how to protect Google Chrome password from others. If you don't protect them from others anybody using your PC could access all your account detail. Now you can realize this is dangerous. Watch the video and employ the technique in your PC.

Are you tired of keeping all the music on your mp3 player to yourself? Share it with the world by hooking your mp3 player up to a radio and using the speakers for output. This simple radio hack of connecting a capacitor to the potensiometer will bring you endless hours of music enjoyment.

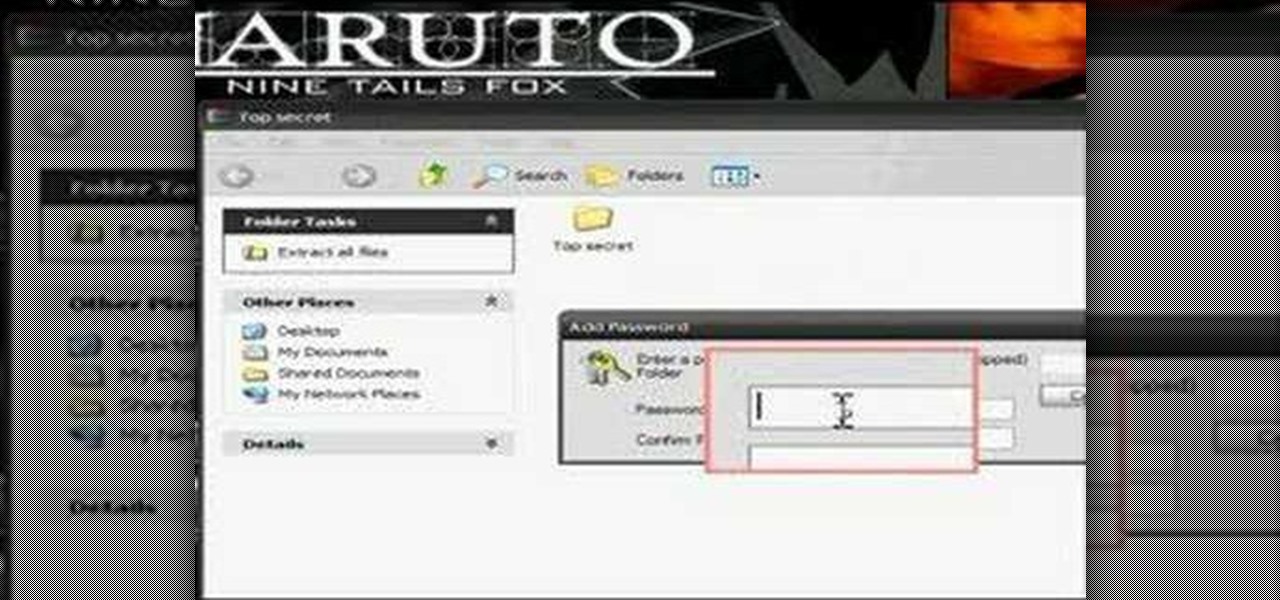
In this tutorial, we learn how to password protect a folder in Snow Leopard on your Mac. First, go to the finder and click on "utilities". Now go to "file, new, disk image from folder". Now, you can select the folder you want and then click "image". Make it a read/write folder so you still can edit the files and enable the encryption. Save this, then it will ask you for a password. Create a password and then verify it. When finished, uncheck the "remember my password", then click on "ok". Now...