Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

How to build a high tunnel to protect your plants

In this video tutorial, viewers learn how to repair the write protect on an SD card. An SD card is a non-volatile memory card format that is used in portable devices. If the write protect on a SD card is broken, the user cannot record any files onto the card. To fix this, viewers will need a small piece of scotch tape. Put the tape on the notch of the SD card. Do not cover the metal tabs at the back. This video will benefit those viewers who have a SD card and would like to repair the write p...
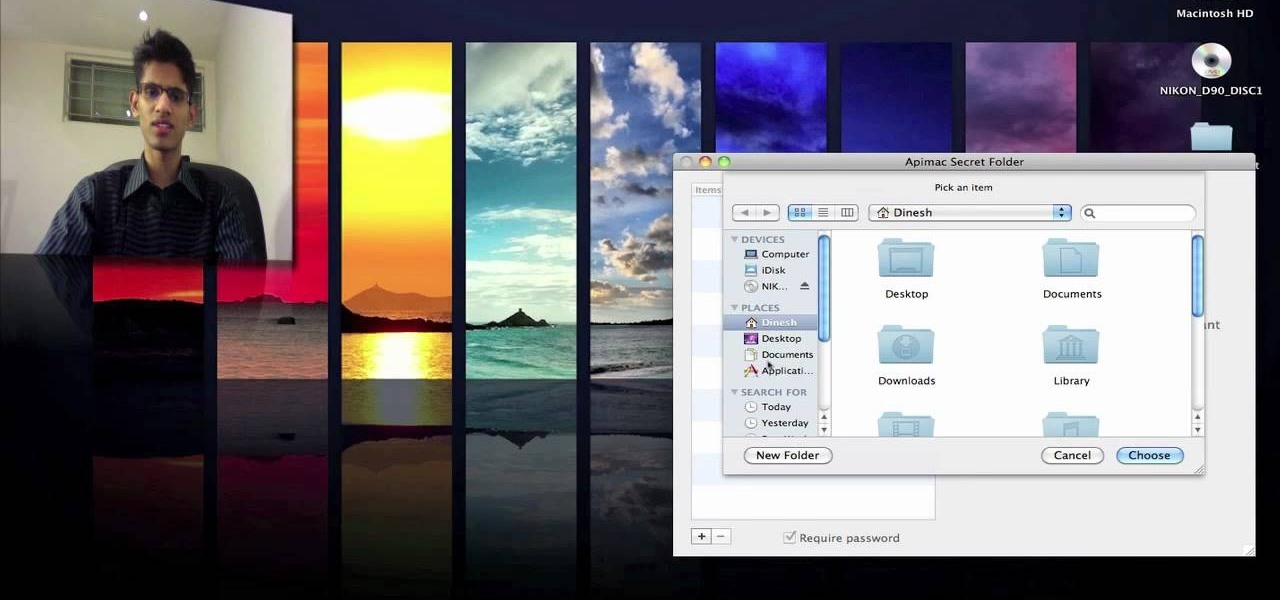
Watch this video for a helpful tip on how to use secret folder application and protect folders in your MAC PC by hiding it. you could download secret folder application from version tracker.com for free go to the Website and click download button to download the application on your Mac PC open the secret folder application. click on the required password button, put your desired password and re enter to confirm. to access your file, click the plus button at the lower left. choose the desired ...

Bed Bug control for luggage is the best way to protect your luggage from infestation. What you will do is, open your luggage and any zippers you may have on your luggage and spray it down the best you can. You will want to spray the seams and any closed area inside and outside you luggage. You should also spray down your handle and wheels (if available). Bed bug control will keep the germs from different hotels or any where you travel, so that it doesn’t follow you back home.

This "Good Morning America" insightful video reveals the truth of hotels room, and what you can do to protect yourself. You'll meet those silent vampire'esque creatures known as bed bugs, you'll even see urine stains on the wall. But, of course you want to be able to travel and see the world without the fear of encountering any of these pesky things. So, you'll learn some helpful tools to help prevent or kill these little bugs for an enjoyable stress free trip and stay.

The cold weather can mean bad news for your home garden. But if you take the right measures, you can protect your plants from dying during the winter months. This video will show you to prepare your plants to survive the cold.

To keep your young tree healthy through the winter there are several maintenance tips to keep in mind. You need to protect them from mice and voles gnawing around the base of the tree because they can easily girdle the bark and cause a tree to die. A simple way to prevent this is to use a plastic wrap. Simply put it around the base of the tree about an inch or so below the soil line and wrap it around the tree all the way up. This will prevent the little mice teeth from gnawing on the bark. A...

If you live somewhere with harsh winters, you know that they can be hell on your garden and the flower pots therein. Watch this video for tips on protecting different kinds of flower pots from the elements during the winter.

In this video tutorial, you'll learn about the risks associated with polysorbate 80, a common food additive. For all of the details, including a list of foods in which the additive is present, watch this video guide from Food Facts.

In this video tutorial, you'll learn about the risks associated with polysorbate 60, a common food additive. For all of the details, including a list of foods in which the additive is present, watch this video guide from Food Facts.

In this clip, you'll learn how to secure a new Microsoft Windows desktop or laptop computer. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started protecting your own new Microsoft Windows PC, take a look.

In this clip, you'll learn about how to prevent SQL injection when writing code in PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

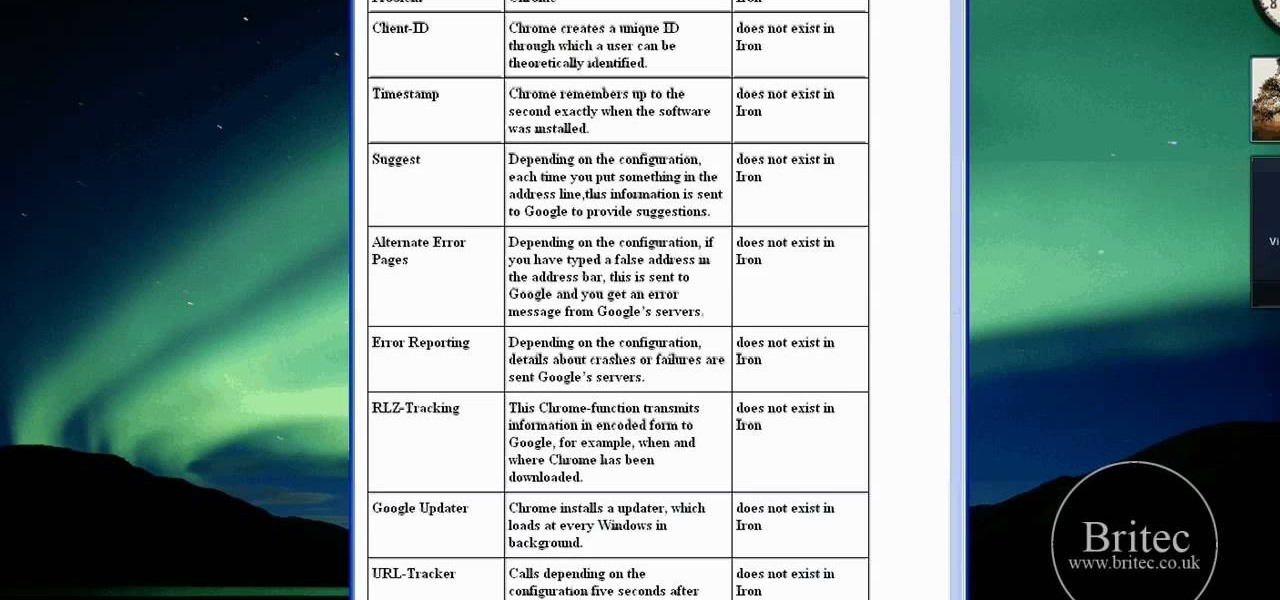
Interested in using Google Chrome but concerned about protecting your privacy while surfing the web? Meet Iron Browser, a secure but otherwise identical clone of the Google Chrome web browser. This clip from Britec will teach you where to find it, how to install it and how to get started using it.

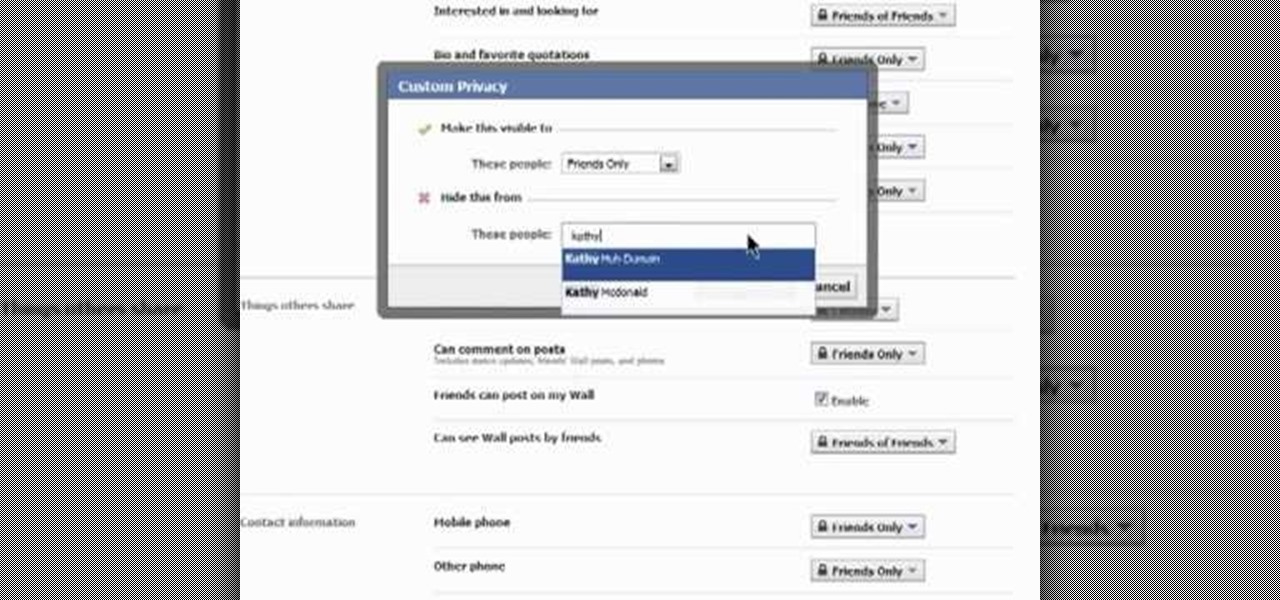
Want to change your Facebook privacy settings? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

See how to avoid compressive forces on the wrist and still do abdominal and arm work when using a Pilates Reformer machine. With Pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates.

We often complain that people bug us, but when dogs complain (by excessive scratching and general agitation) about bugging, they're talking about the real thing.

Keep private info from prying eyes and earn some peace of mind when you safeguard your PC or Mac against nosy intruders. You will need several great passwords, virtual desktop software, snoopware blockers, a screen filter, a mirror, a healthy sense of paranoia, WPA encryption, and an understanding IT specialist.

The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about protecting your VBA code from snoopy little trolls. For more information on keeping your VBA code secure, watch this MS Access how-to.

West Nile virus is rare but can be deadly. To avoid getting it, you’ve got to avoid mosquito bites.

Andrew Burke from Videomaker magazine gives some advice for protecting your equipment while shooting in the rain.

Giving your kid a bath is an integral part of child care. What's that saying? Cleanliness is next to Godliness? Okay, maybe not, but a clean baby is a great sight, but there are things to worry about when filling up the bathtub. Could the water temperature be too hot? NFPA's Amy LeBeau on the importance of testing the temperature of bathwater before putting children into the tub. Safety also comes first.

This clip offers advice on how to save your wrists and build strength in your back when using a Pilates Reformer exercise machine. With pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates. For complete...

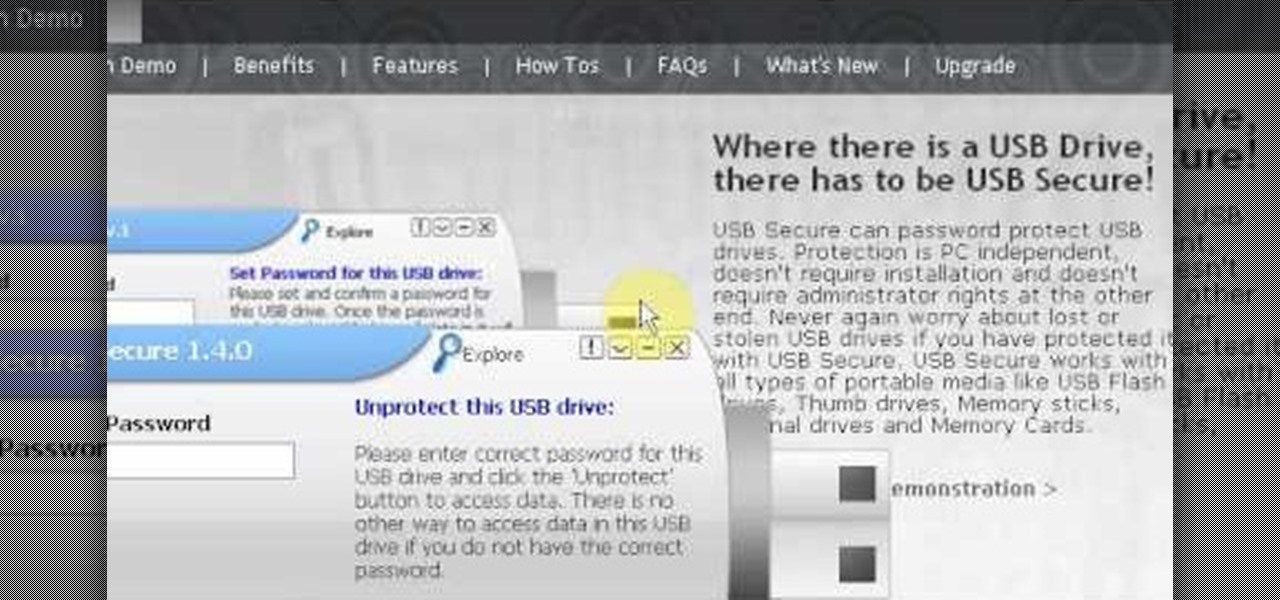
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

This video talks about protected mode for internet explorer 7 and Windows Vista. The person tells you that protected mode helps protect your computer from types of spyware. It is not the best solution and they tell you one should not rely on this alone. By default protected mode is on. You want to make sure it hasn't accidentally been disabled. To check your settings, double click on the area on the bottom of the screen that says protected mode. The security tab will pop open. Look to see if ...

An associate from Garden Years discusses the danger frost poses to small, outdoor plants. Since you don't have a lot of control over the weather, there are a few tips you can follow to try an avoid any unwanted damage to existing plants. The host examines a peach tree to identify when a plant is blooming and thus very delicate. If a plant is fully blooming, then any temperature below freezing (32 f) can damage the blossoms. Aside from putting cloth over the plant, mulch is also very helpful i...

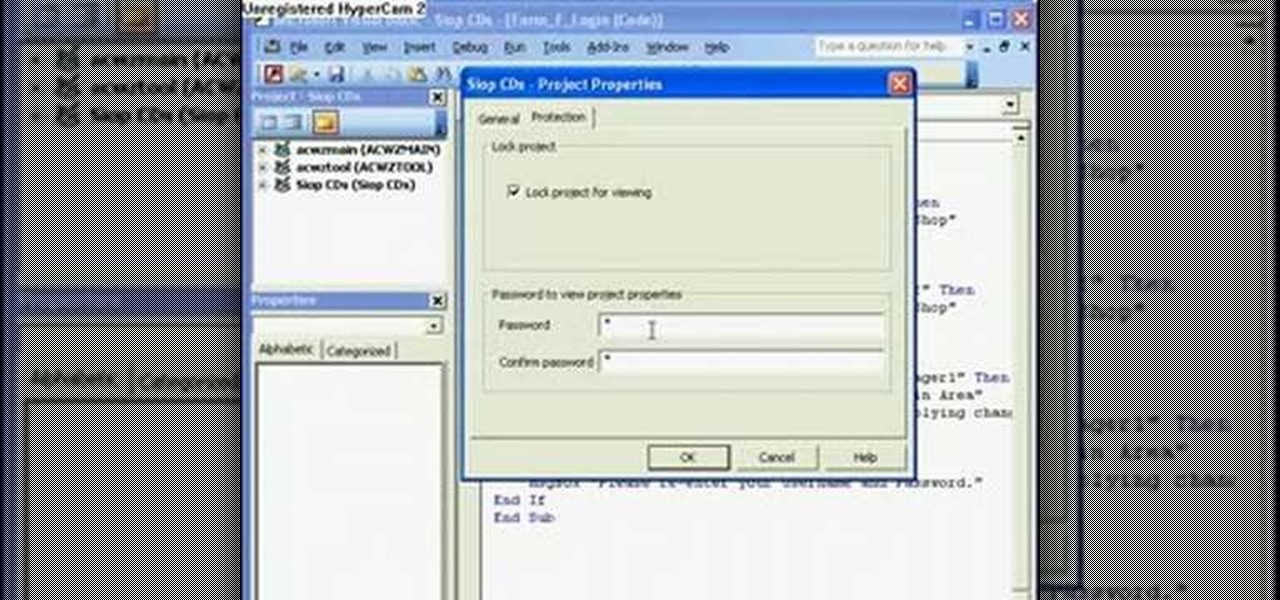
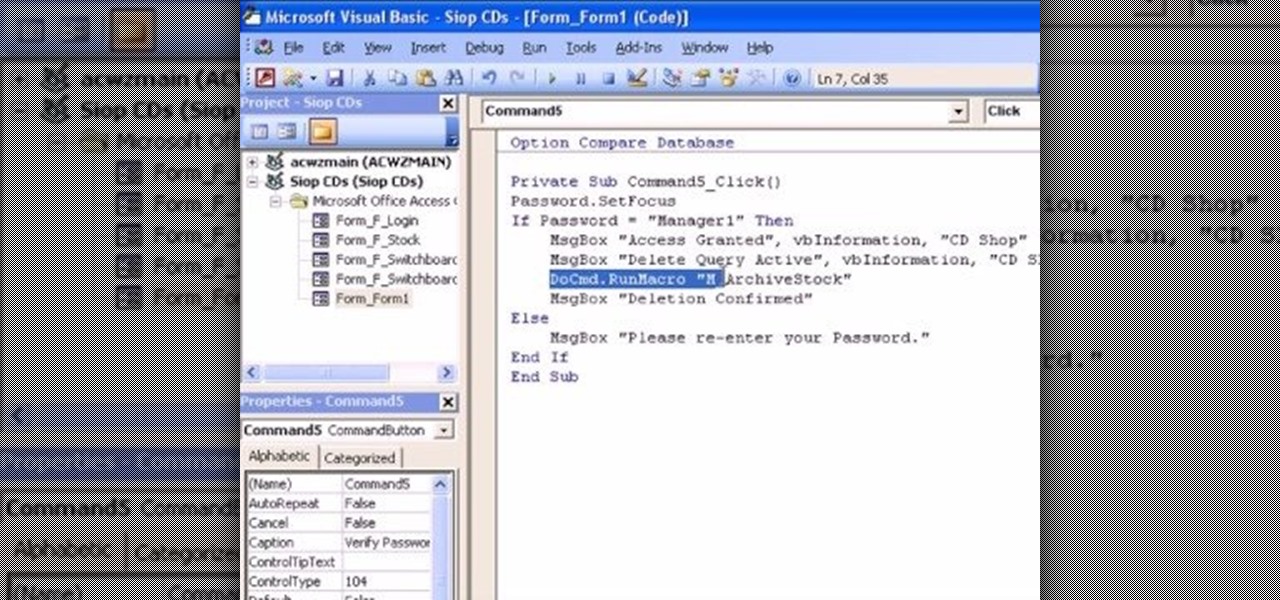
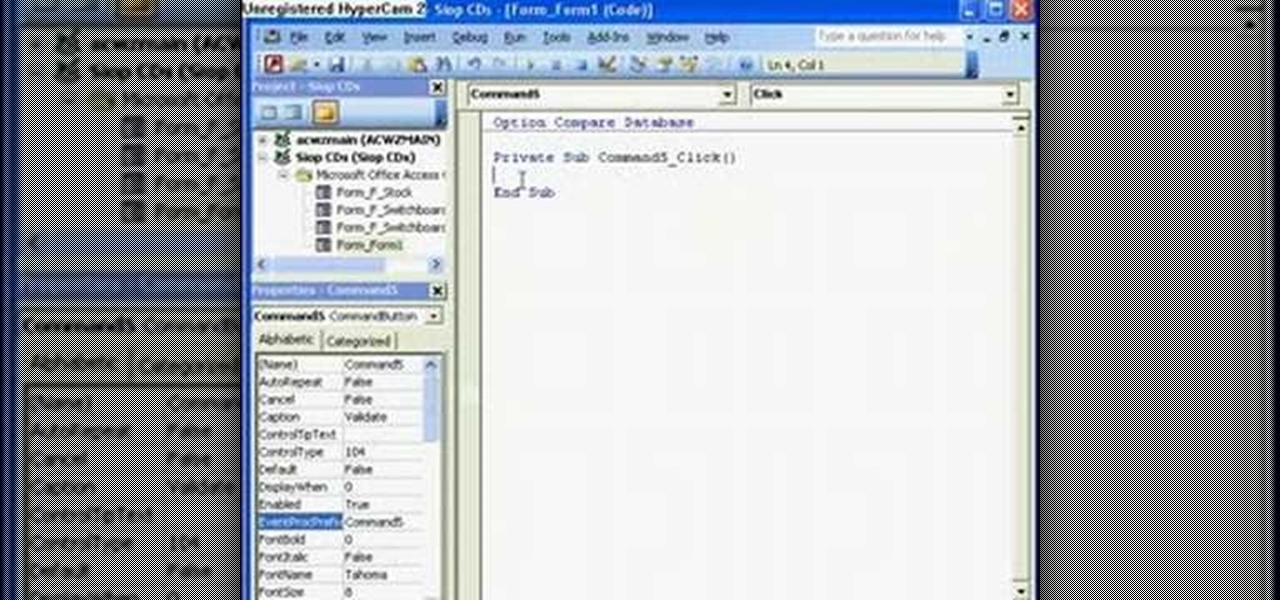
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn how to force a password to be entered in order to run a query.

The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about creating a login form and password protecting your database.

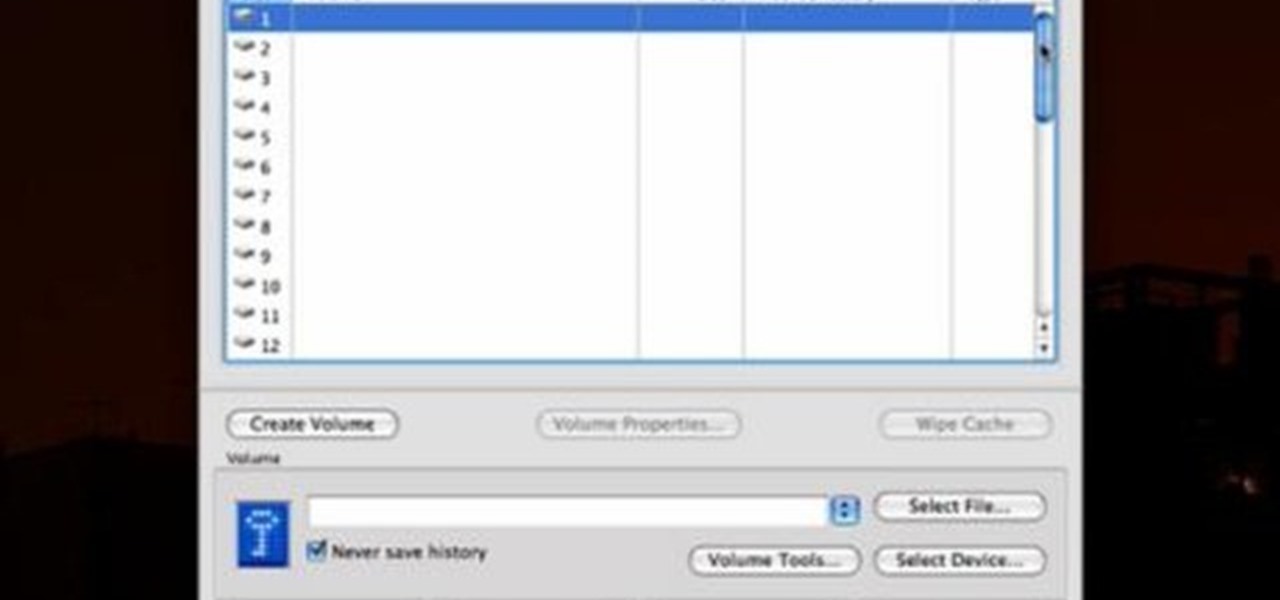
Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

Keep your possessions safe from thieves with these tips. You Will Need

Death by stingray is extremely rare, but getting hit with their barb still hurts like hell – which is why you need to learn how to play footsie safely with these sea creatures.

Everybody into the pool! Or the ocean! But not before you take measures to prevent your hair from getting fried.

When protecting your garden, you can stay green with some environmentally sound solutions. You Will Need

Frost is in the air. If you have tender plants like basil, pepper or impatients when that cold weather comes it will zap those plants. Often, if you can get through those first couple frosts, an Indian summer, that can last weeks and weeks, will follow. If you can protect your plants during this time you can have blooms for much longer. There are several ways to protect your plants. You can use a traditional device like a glass cloche. The nice thing about them is they are decorative and will...

In this clip, you'll learn how to get started using Symantec Backup Exec to protect SharePoint & Exchange servers. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just under five minutes. For more information, including detailed, step-by-step instructions, take a look.

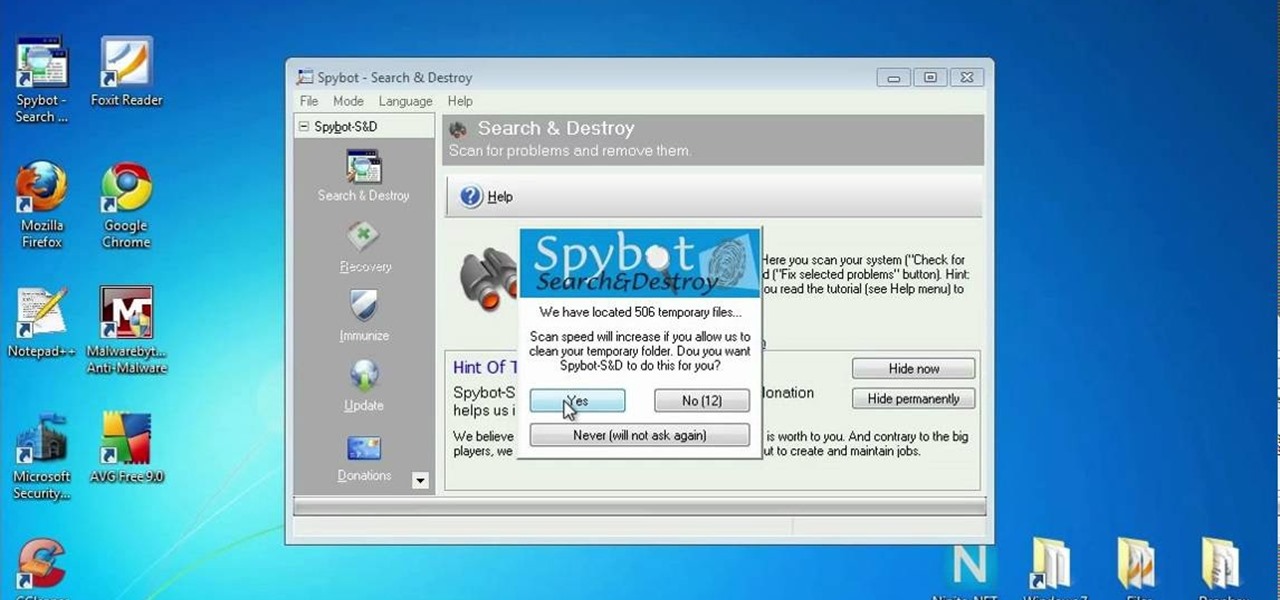
Protect your Windows desktop or laptop computer from malicious software with anti-virus applications. This handy how-to presents a complete overview of the process. It's easy! So easy, in fact, that this video guide can offer a complete overview of the entire process in just over four minutes. For more information, including step-by-step instructions, take a look.

Ever wanted to password protect a Firefox This clip will teach you everything you'll need to know. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For more information, including detailed, step-by-step instructions, take a look.

In this plumbing video Bob Schmidt shows you how to protect a basement floor drain from potential sewer back-up during flood water conditions.

In this video, Bob Schmidt shows you a product to use during remodeling to protect your carpet. Keep dirt and debris off your carpet with this easy to install product.