Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

Monday has been a big update day for Apple. Alongside the release of iOS 10.3, iWork has been updated across both iOS and macOS. The biggest change is the ability to unlock password-protected files with Touch ID, either on iPhone and iPad, or on the new MacBook Pro with Touch Bar.

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

The fingerprint sensor on the Samsung Galaxy S5 gets a little flack for its functionality, and that's mainly because the setup instructions ask you to swipe your index finger over the sensor to unlock your device or make mobile payments (and of course, because it was already hacked).

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Smartphone users these days can get bombarded with texts and emails every hour. Online retailers sending you coupons to get you to buy stuff. Girlfriends asking where you are. Service providers reminding you to pay your bills on time.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities.

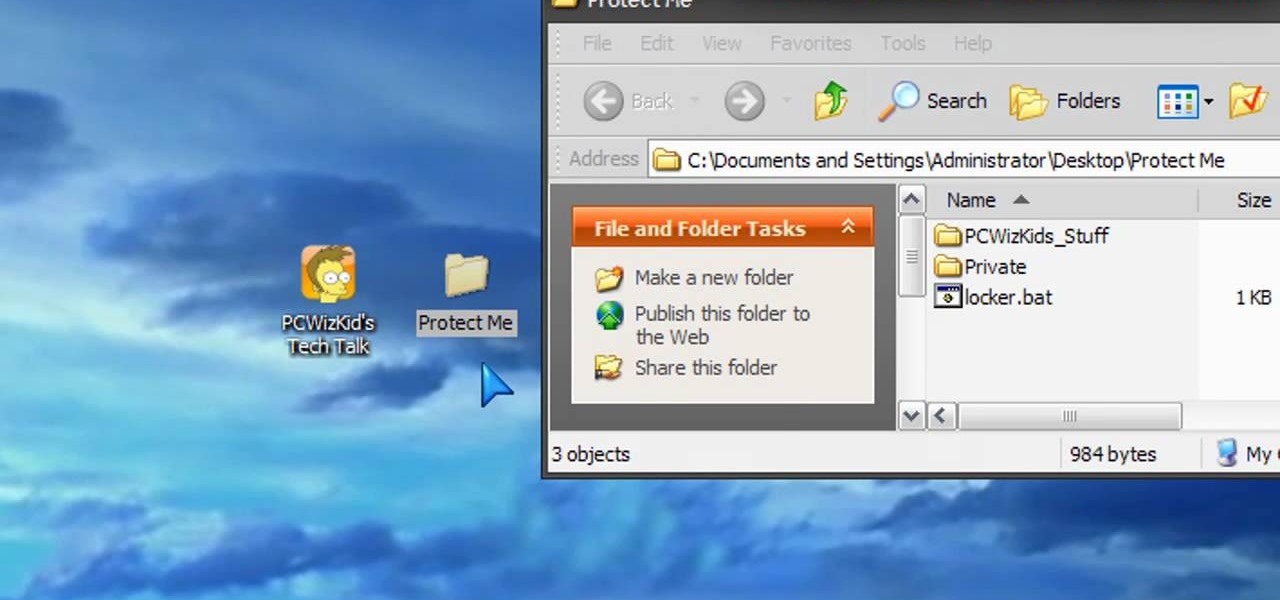
If you've got something on your Windows PC that you don't want to share with the world you're going to want to create a private, password protected folder. This simple video shows how to easily set it up. This works for Windows 7, Vista and XP.

Ever have the problem of people messing with your word documents? This guy shows you the solution by telling you how to create password protected encrypted word documents. The process starts with your open file. Clicking on save as... and in the popup window clicking the tools button in the bottom left corner and clicking general options. There it shows you text entry boxes, one for setting a password to open the file, another to set a password for rights to modify the file. Enter your passwo...

This VB.Net tutorial teaches you some tricks with duel forms and how to do create very basic password protected applications.

In this video, we learn how to get into a password-protected Windows machine. First, you need to have this software onto your computer from http://www.piotrbania.com/all/kon-boot/. Once you have this, you will burn it onto a disk. When you forget your password, pop this disk into the drive on your computer. After this, boot it up and then reset your computer. After this, you will see a pop up appear on your computer and it will start to go through your computer to get the password. When it fi...

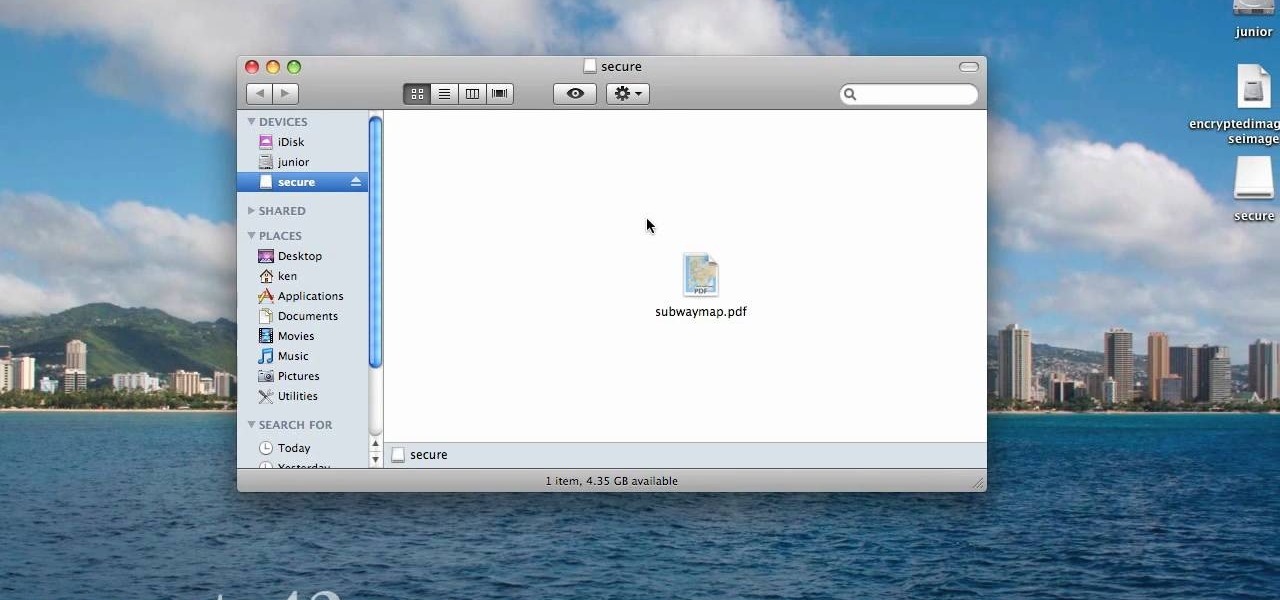
When you are sending any files over a network it is advised to encrypt it so that no can read it even if they get hold of it. You can encrypt files in Mac OS for this purpose. So first take any file or program that you want to encrypt. Open your hard disk and go to the applications. In the applications, under utilities open the Disk Utility program. Using this disk utility program you can create an encrypted disk image. Now this image will act as a disk image or other flash drive, but we can ...

This video talks about protected mode for internet explorer 7 and Windows Vista. The person tells you that protected mode helps protect your computer from types of spyware. It is not the best solution and they tell you one should not rely on this alone. By default protected mode is on. You want to make sure it hasn't accidentally been disabled. To check your settings, double click on the area on the bottom of the screen that says protected mode. The security tab will pop open. Look to see if ...

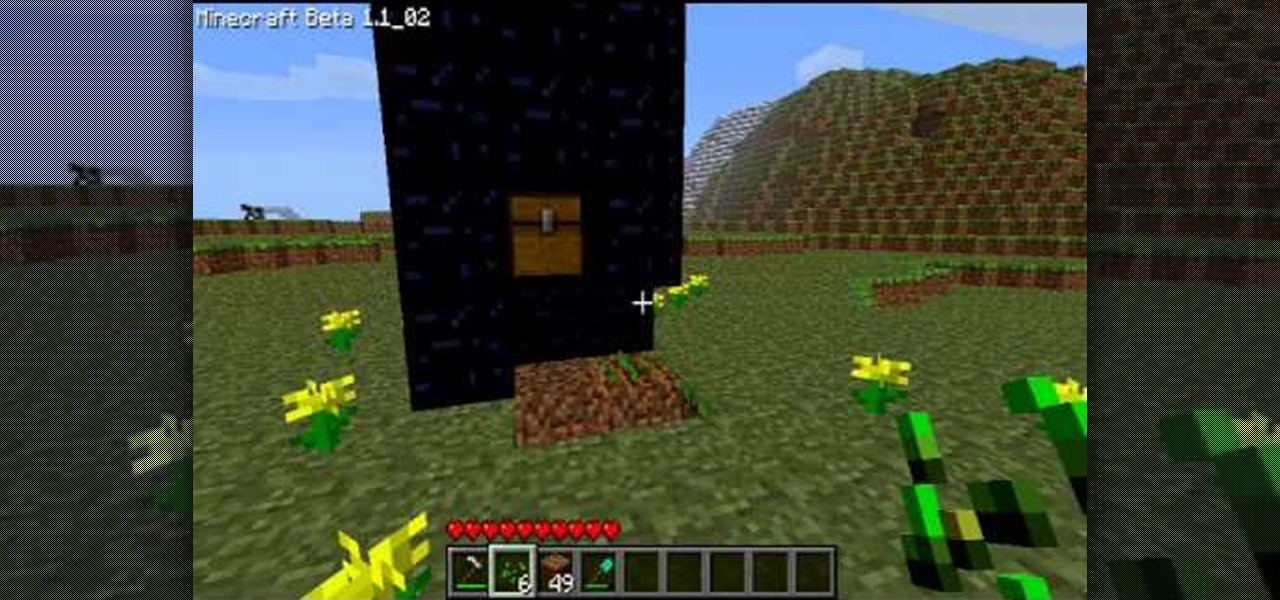
Even if there's a giant block of obsidian, you can figure out a way to exploit a glitch that will let you easily break into it. You're also shown a way to easily break into protected chests on shared servers in Minecraft.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.

Need to unlock your music? Want to save Rhapsody or Napster files on more than your own computer? This is how to unlock, remove drm and convert protected wma files from napster and rhapsody to mp3 without having to pay for them. Also how to put napster and rhapsody files in iTunes and on your iPod.

Watch this video to learn how to make a password protected video.

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

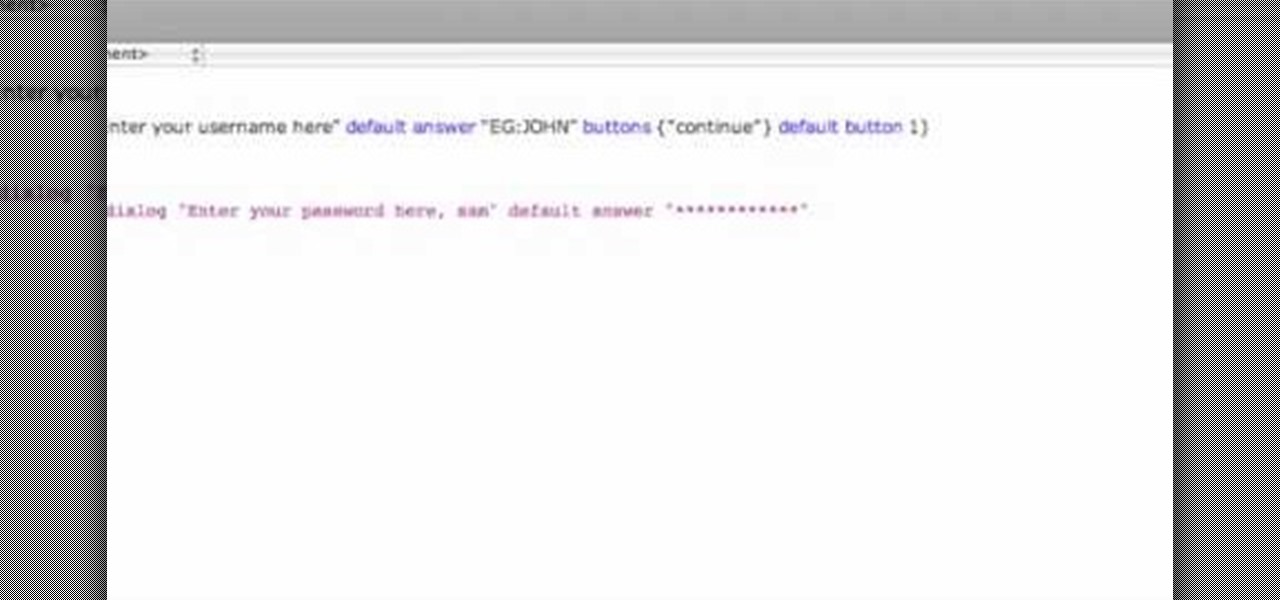
This video shows how to program a password and user protected application in AppleScript.

The procedure involves downloading a program called "hand brake". Hand brake is free to download. You can find it by searching for "hand brake" on Google. The direct website is Handbrake. You have to install this program on your computer. You must also download a program called DVD43. That program can be found the same way as hand brake, by using Google. DVD43 is also a free program to download. You use the DVD43 program to by pass copy protection on a DVD. You can use hand brake to change th...

How to crack the WEP encryption on a wireless (WiFi) network.

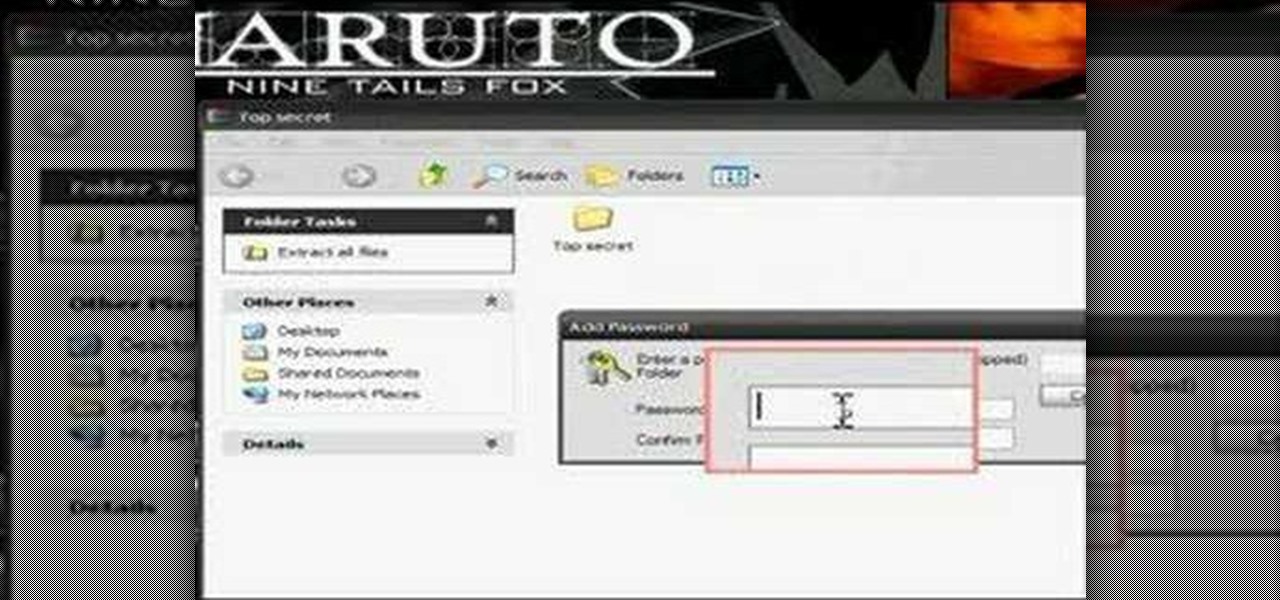
Learn how to protect your documents and pictures by using a password. Free software needed: WinRAR

I'm not sure exactly when it happened, but it's awesome that you can now download music from the iTunes Store that's free of DRM (digital rights management) limitations. That was always my biggest problem with buying music from iTunes. Paying a buck for a song that I can only play on Apple devices? Really? That's what finally led me away to other legal music downloading services like eMusic and Amazon.

Video games are the newest major expressive media. As such, their role in society is still being defined continuously. A monumentally important example of this took place yesterday at the US Supreme Court. After a long deliberation, the highest court in the land handed down a decision invalidating a California law banning the sale of violent video games to minors on the grounds that video games are protected speech under the First Amendment, like movies and books.

It's been a great year for video games, kind of. Sure, the AAA release lineup has been a trainwreck and hacking has been a bigger problem than ever. But two things have happened involving the federal government that have made video games more legitimate in the United States than ever before. The Supreme Court ruling establishing that video games were the equivalent of movies and books, not porn, was the more significant decision. But in May, the National Endowment for the Arts made another si...

If you have a group of large files that need to be sent to a client, you might want to compress it into one single file for easy access or even protect its content from outsiders with a password. This video will teach you how to create password-protected zip files with WinRAR. WinRAR provides full RAR and ZIP file support, and can decompress CAB, GZIP, ACE and other archive formats. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so ...

In order to clean your fish tank, you will need the following: a bucket, water conditioner, aquarium salt, a clean filter, a suction tube, and clean fresh water.

In Obstetrics and Gynecology (OB/GYN), doctors deal specifically with the female reproductive organs, which means a lot of visual inspection of the vaginal area. Whether you're a doctor, surgeon, nurse, or nursing assistant, knowing how to properly drape a patient is detrimental to the patient feeling protected and secure with the hospital staff, along with having some privacy. This video will cover different types of draping techniques.

This week, Etsy How-Tuesday presents Kari aka ikyoto and Stella aka lookcloselypress of The {NewNew} York Team. Today we're going to learn how to screenprint our own snowflake gift wrap for the holidays. Kari and Stella remind us that recycling paper bags is a great source for materials for this kind of project.

Maybe you're heading back to school, or maybe you just want to make sure that your book doesn't get damaged. In either case, this guide will teach you how to cover your book using a piece of paper as a bookcover so that your textbook is well protected.

Getting back to nature can be an incredibly rewarding experience – unless critters come along and ruin it! Here's how to keep your food from being plundered. To keep your food protected while camping out in the great outdoors, try bringing along a cooler, a cloth or nylon sack, a sock, some rope, and sealable, waterproof plastic bags. Keeping your provisions safe will decrease the risk of animal attack, and make your journey out into nature a fun experience.

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

Eddie from the Long Island Boaters Club shows in four easy steps how to prepare the engine of your boat for the winter. He discusses the three items needed for proper preparation and makes product suggestions. Then he takes us through the procedure. He starts by pouring an additive to the oil tank and a stabilizer to the fuel tank. Eddie shows us how to attach a hose to the water jacket to flush salt water. He runs the engine for ten minutes. At the end of that period, he demonstrates how to ...

Watch this science video tutorial from Nurd Rage on how to get lithium metal from an Energizer battery. They show you how to get Lithium Metal from an Energizer Ultimate Lithium battery.

1. First of all you need go to the 'view' button at the top bar menu. From the drop down click on 'view options'. Then click a 'check mark' against the 'kind' and then click 'ok'.

Have a file or a number of files too sensitive to be stored on your desktop hard drive? Thwart would-be snoopers with an encrypted USB flash drive. This free video tutorial from the folks at CNET TV will show you everything you'll need to know to create your own password-protected thumb drive directories.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.