
How To: Chrome Your Web Experience with Google's Cr-48 Notebook
Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.


Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

Want to be able to print wirelessly without having to buy a pricey network printer? Now you can! All you need to do is follow these simple, quick, steps.
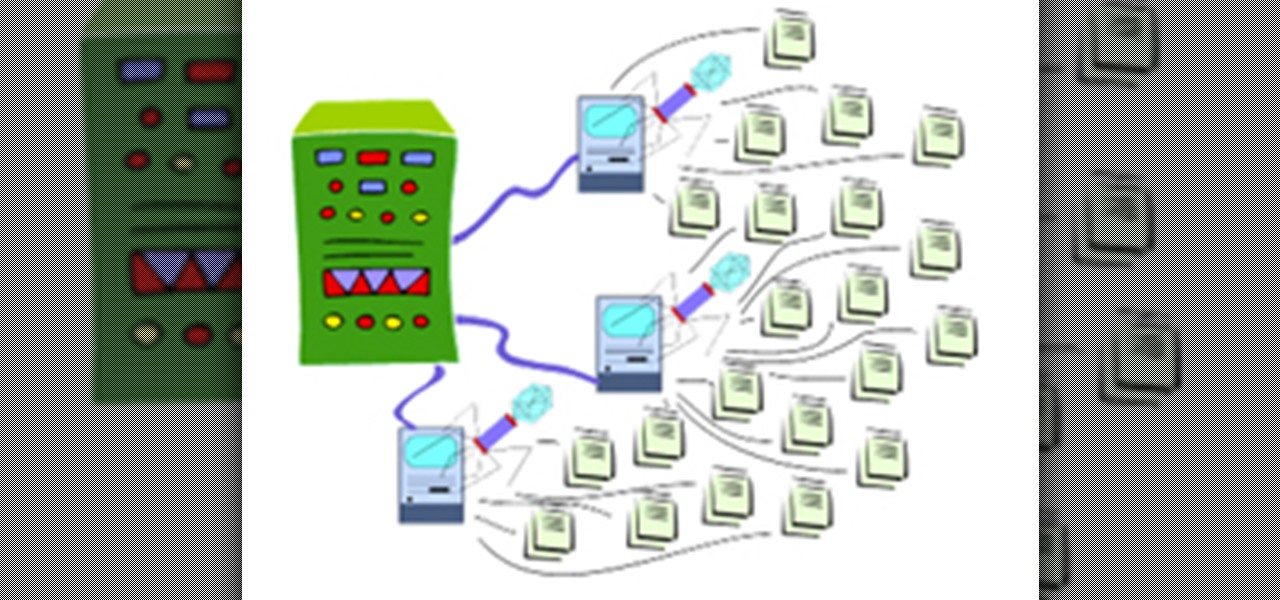
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

Materials Needed! Video: Undo a door's chain lock from outside with string, yarn or shoelaces.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.
A 12-year-old Minnesota girl was reduced to tears while school officials and a police officer rummaged through her private Facebook postings after forcing her to surrender her password, an ACLU lawsuit alleges.

Forget the millionaire superstars from soccer’s biggest teams. It is the tournament referees who are the World Cup’s most coddled and protected species...

This video production was released in coordination with the 2009 job posting for Army National Guard “Internment Specialists” that Kurt Nimmo reported on at the time. (The original post has been conspicuously removed since then). Notice that the job description, title and duties all seem to match the terminology used in the leaked document FM 3-39.40: INTERNMENT AND RESETTLEMENT OPERATIONS (at Army p/w protected link) outlining the plan to set up camps both globally and domestically (Yes, the...
Just a quick post. Xorg is the graphical server that handles the desktop environment you choose for your Linux box. A pretty big flaw was found in Xorg versions 1.11 and later that allows anyone to bypass the screen lock mechanism on xscreensaver, gscreensaver, and many others.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Alter Evo on Flickr has created this amazing starfighter and service unit vehicle. This is what he says about it:

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.

Google has caught a lot of flack for various privacy infringements over time. Google Buzz was the latest uproar, when lack of proper prior testing allowed the tool to expose a slew of information users did not necessarily want shared, resulting in massive complaints. A Harvard student even went so far as to file a lawsuit (read more).

Looking for the best way to to pay or transfer money for your overseas property can be difficult. Should I make a money transfer with my bank or a broker? And many other questions that we ask ourselves.

Scrabble Bingo of the Day: * FINNESKO [n/pl.] A finnesko is a boot made of tanned reindeer skin, with the reindeer's fur on the outside. It's an especially good, warm boot for subarctic regions. These boots originate from the Sami, indigenous people from the cultural region of Sápmi, located across four countries in the Arctic Circle; Norway, Sweden, Finland, and Russia. This area is also referred to as Fennoscandia.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

I'm not going to lie. I was Catholic. But one of my reasons for my faithful departure was having to tell my innermost secrets— my sins— to a silhouetted figure behind a latticed screen. With the creepy enclosed booth structure and separation of sinner and confessor, its anonymity was clear, yet deceiving. You always knew the priest and he always knew you. If I wanted total privacy, was there really a need for this intermediary to God?
Windows Live SkyDrive which is initially termed as Windows live folders is one of the parts of Microsoft Windows online service. It is a password protected service that allow users to store file and share them with others. Here the windows live id is required to access the users profile. Anyone can make his/her files private or public. Public share file are easy to access without requiring any Windows live id.Initially it was available only few states in United States. But nowadays it expande...
Rockets are lots of fun when you are launching them. However, finding them can be an arduous if not maddening task. Fancy space rockets have lots of tracking equipment to make touchdowns as simple as pie. Today, we look at embedding LEDs into your hobby rocket for easy night flight fun!

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

Tera Online is a beautiful Korean MMO with real time combat. The game is coming to the states towards the end of the year. Unlike other MMOs were combat is target specific (lock on target) and dependant on skill timers and macros, Tera Online focuses on fast area of effect action. Your blade or spell will hit whatever is in front, or miss if it's not. The closest thing to the game play of Tera is Vindictus, a free to play MMO with the same concept of game play. If you've played Vindictus, the...
Fads, Fiascoes and Good Stuff in FrontierVille This Week The second in a series of weekly columns.

The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who
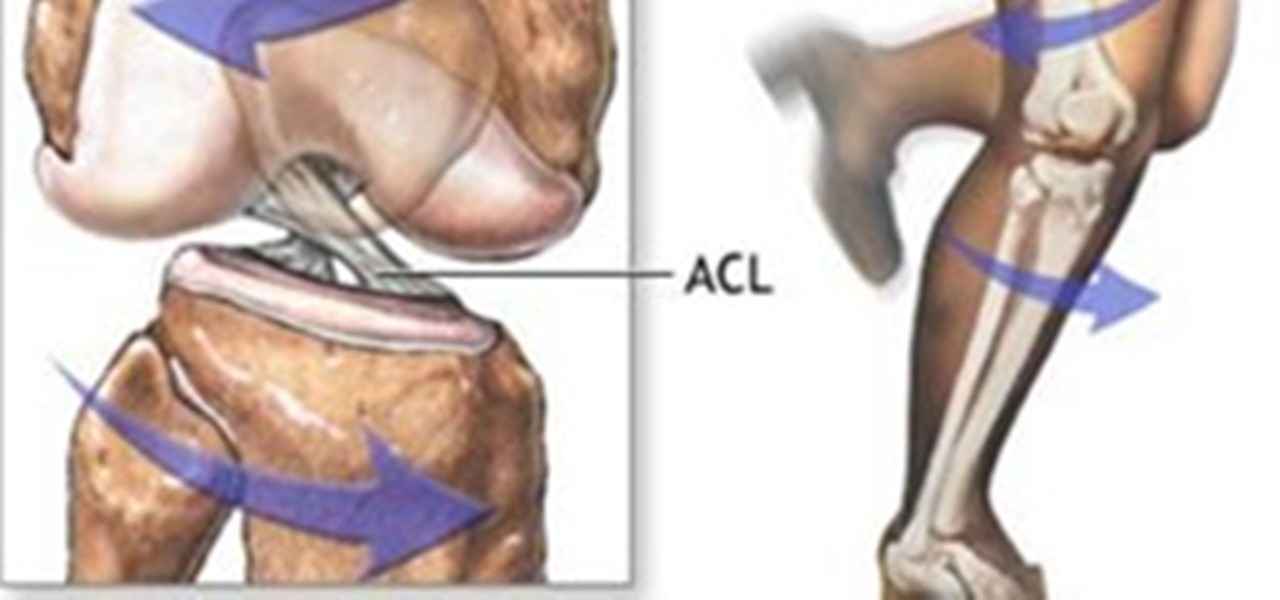
The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who have witnessed or suffered a torn anterior cruciate ligament (ACL) are familiar with the pain, surgery and intense 6 to 8 month rehabilitation that accompanies the injury, not to mention the disappointment of ending a season. Nationwide, this will occur more than 500,000 times this year, and female athlete...

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

It's once again Monday, which means it's time to highlight some of the most recent community submissions posted to the Math Craft corkboard. Since two of these posts were on polyhedral versions of M.C. Escher's tessellations, I thought we'd take a look at building a simple tessellated cube based off of imitations of his imagery.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

The widely used expression "free as a bird" intimates an enviable existence: delicate, yet mighty wings transporting to destinations no human could so breezily venture. But despite their fanciful, superhero ability, in truth, the avian race leads one of the most difficult existences in the animal kingdom. Yes, birds have existed for eons—they likely evolved from small dinosaurs of the Jurassic period—but for these creatures, life can be ruthless.

THE FOLLOWING IS ONLY FOR YOUR ALIENWARE WARTIME THE BELOW SETTINGS ARE FOR YOUR ALIENWARE WARTIME EDITION DESKTOP PC, THAT HAS THE CORE I7/X58 MOBO AND DDR3 TRIPLE CHANNEL MEMORY INSTALLED;

The worst part about playing darts is that when you miss—it can damage not only your ego, but also the wall behind the dartboard if it's not protected. Redditor mavantix found a solution to this problem in wine corks. Over a year, he collected over 1,000 corks from family and friends to make this DIY Cork Dartboard Cabinet—that's a lot of wine!

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be in total blackout in protest against the proposed legislation in the United States. And that's not all. MoveOn, Reddit, BoingBoing, Mozilla, WordPress, TwitPic and other popular websites are down today in protest.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.