
How To: Make fake blood
In order to make fake blood for Halloween, you will need the following: a towel, a spoon, a container, red food color, white corn syrup, and blue food color.


In order to make fake blood for Halloween, you will need the following: a towel, a spoon, a container, red food color, white corn syrup, and blue food color.
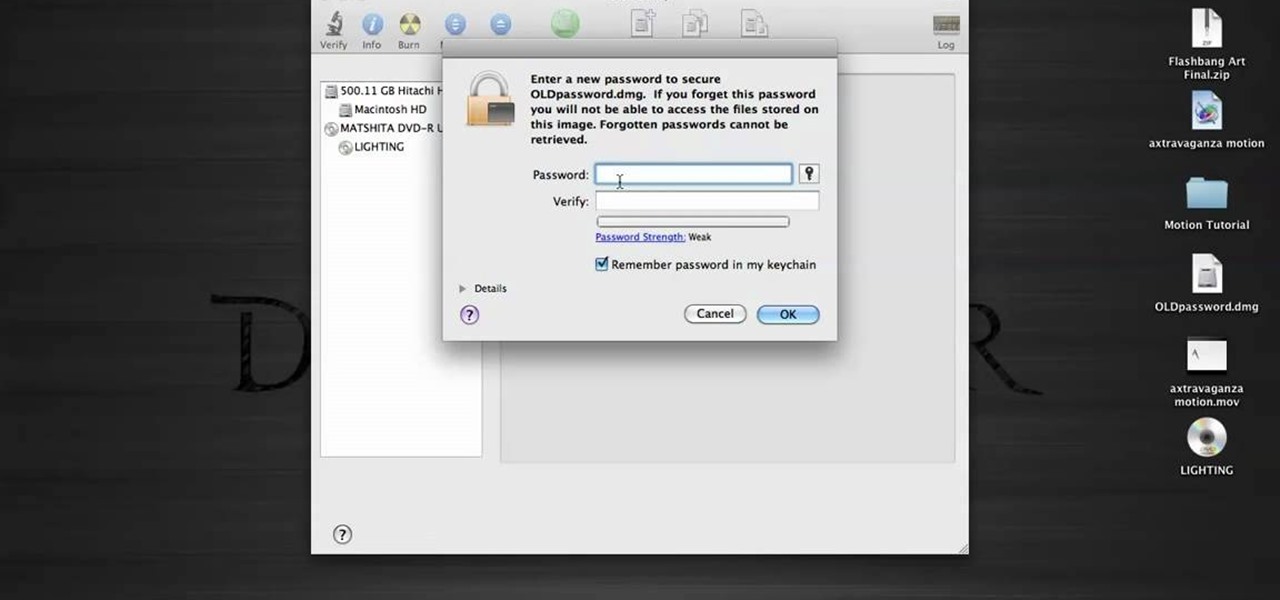
In this tutorial, we learn how to password protect a folder in Snow Leopard on your Mac. First, go to the finder and click on "utilities". Now go to "file, new, disk image from folder". Now, you can select the folder you want and then click "image". Make it a read/write folder so you still can edit the files and enable the encryption. Save this, then it will ask you for a password. Create a password and then verify it. When finished, uncheck the "remember my password", then click on "ok". Now...

In order to make an ombre style custom beach bag, you will need the following: a canvas tote bag, dye, gloves, a paper place, sponge brush, stencils, fabric paint, containers, white vinegar, and water.

In this tutorial, we learn how to care for kid's eyes. First, make sure you get an eye exam for your children at a young age. This should occur while they are in pre-school. This can help track any problems with the eyes and see if they are developing correctly. Make sure to have the eyes checked out by a professional every year after the initial visit to the eye doctor. If you don't have insurance, there are many places out there that participate in programs for free eye exams. Next, make su...

If you would like to create the look of stitches or sutures on your clay sculptures, you will need the following: clay, a toothpick or sharp implement, and a cutting tool.

This video is from AskMeDIY and covers how basement sump pumps work to keep your basement dry. The sump pump fits underneath the basement below the concrete slab. The sump pump in the video pumps 2,000 gallons per hour. The presenter turns the pump off to demonstrate how quickly the water would fill in with the pump off. He contends that the basement would be flooded in only three minutes if the pump would malfunction. The pump is plugged into a GFI protected outlet and the pump outlet flows ...
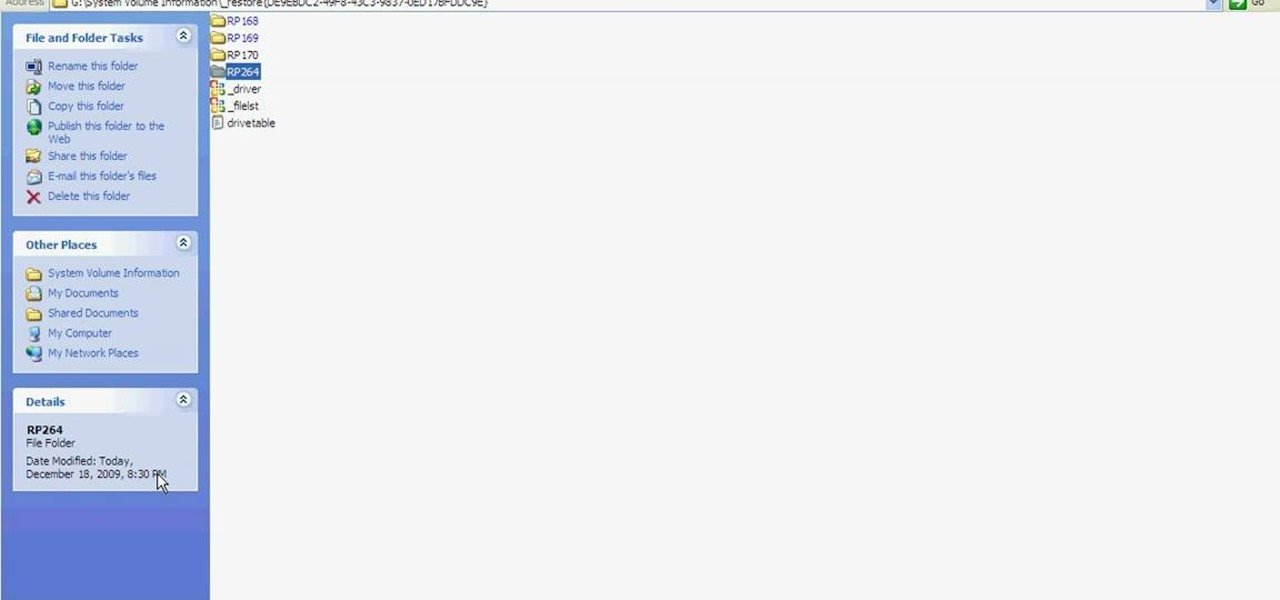
Learn how to fix or recover a corrupt windows registry following the steps outlined in this video tutorial. To begin, take the hard drive out of the computer with the corrupted registry and connect to another computer. To find the files you need to replace go to Start and My Computer. Look for the hard drive that you just added and double click on it. Go to Tools and Folder Options. On the View tab under Advanced Settings click Show Hidden Files and Folders, and unclick Hide Protected Operati...

This video discusses Dead Drop Devices and how to use them to transfer messages. The video starts by explaining what Dead Drop Devices are. They are basically common everyday objects that are hollow inside to store a message. The video shows a large lag bolt and a spike that are actually Dead Drops. The head of the dead drop bolt screws off and reveals a hollow cylinder used to store something valuable. The second object is a spike that is supposed to be shoved into the ground so that it will...

A boxer knows that during and after a fight, their bodies will be aching. As a part of the job, they grit their teeth, focus and get past the pain. The most important part of a boxer's body, though, is arguably his hands. A boxer depends on his hands to win fights and to train. The best thing one can do to protect their hands is to wrap them properly. This video will show you exactly how to wrap your hands so that they are cushioned and protected against injury. An ideal wrapping job would pu...
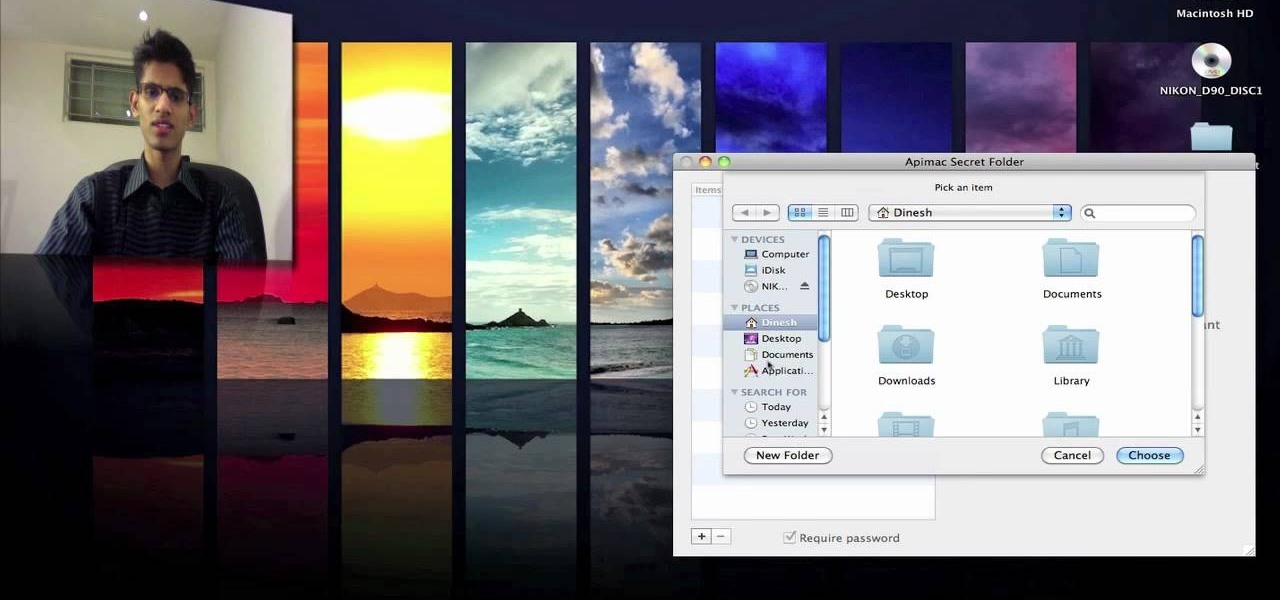
Watch this video for a helpful tip on how to use secret folder application and protect folders in your MAC PC by hiding it. you could download secret folder application from version tracker.com for free go to the Website and click download button to download the application on your Mac PC open the secret folder application. click on the required password button, put your desired password and re enter to confirm. to access your file, click the plus button at the lower left. choose the desired ...

This is a short tutorial on safety on how to start skating hybrid with your dog. Heelys are great because they let you keep control of your dog. You can brake and handle your dog much better than on other skates. Find a smooth, clean street or parking lot, and make sure your dog is just as protected as you are. Learn how to pull a dog on skates by watching this video pet trick tutorial.

The procedure was adopted to build a waterfall in Oregon Coast Garden Center, Wald-port. 1. A level pad was cut to arrange the first row of blocks

Use tough skin spray adhesive, under wrap or pre-wrap, athletic tape to wrap an ankle. Position ankle in 90 degrees of dorsal flexion. Spray the adhesive to insure tight taping. Heel and lace pads are placed over tendons. Pre-wrap is applied, the goal here is to apply anchors so adhesive from tough skin will adhere to tape. Three layers are applied working towards the calf. Apply heel lock tape from the calf towards the heel, applying tension as you cross the bend in the ankle. The correct lo...

Maybe one of the hardest jobs you can do around the house is cleaning the gutters. When cleaning the gutters by hand, you have to constantly keep moving the ladder to get to the various spots of the gutter which contain a mess. If not done properly, the gutters can get clogged, which will not help the appeal of your home. This video explains a simple and easy way to clean the hassle-prone gutters. The powerful leaf blower makes cleaning the gutters simple and easy. Just make sure to keep your...
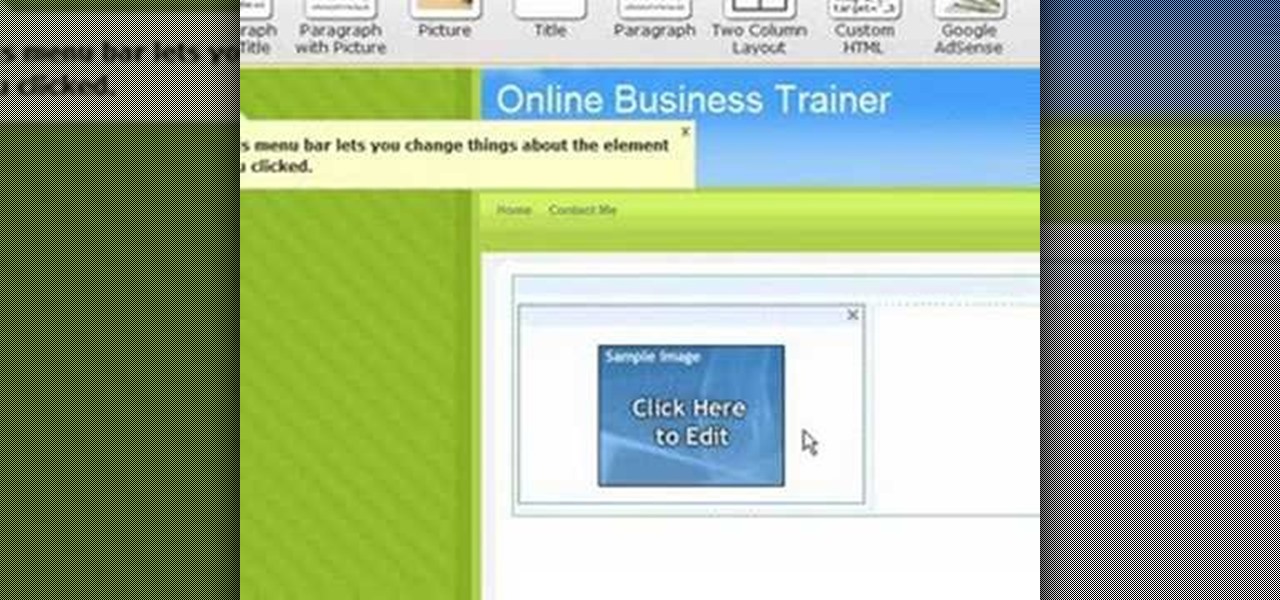
1. On the browser, type www.weebly.com. If you are a new user, then sign up. Write your username, email, password, and click on Sign Up and Start Creating.

Nervous about breast feeding in public? You shouldn't be. Breast feeding outside your home doesn’t have to be a source of anxiety. Create a calm and modest approach to nursing in public.

Moving is such a hassle! Packing is a big job but this video shows and easy way to pack out pots and pans. You will need 4-5 cubit foot cartons. You can get these from your mover or you can purchase them from a moving company. You will also want to get clean newsprint, packing tape, a moving blanket, and a permanent ink marker. Prepare your 4-5 foot carton by putting crushed paper on the bottom. This will act as a cushion for the pots and pans. Put the moving blanket or a protected pad on the...
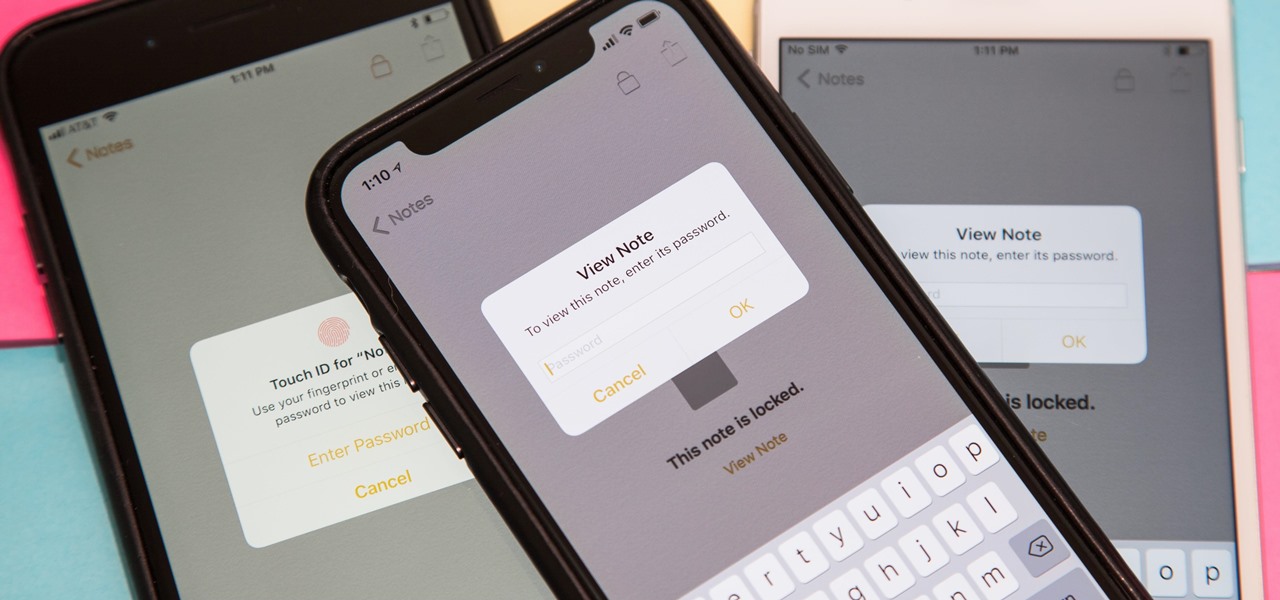
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.
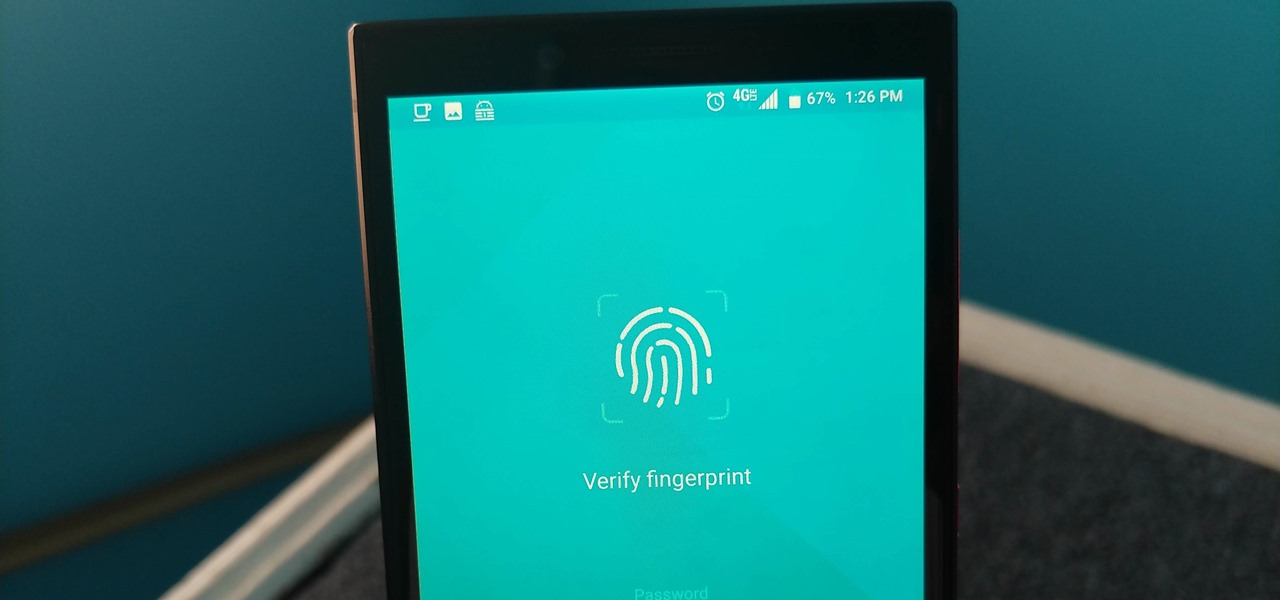
Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Ok, I have to admit, I drop my phone around 2–4 times a week. I'm horrible at protecting it and I've gone through my fair share of cracked phones. Most of the time, once the phone is cracked it's just easier to get an entirely new phone, rather than have to fight your phone provider for a fix.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

Learn how to set up an Epson printer wirelessly when you bring your new printer home you will want to start by installing the software that came with the new printer. You can set up your printer to work without wires and it will print from all over the house. There are 3 ways to set up the printer including the Epson way, with cables, and WPS. To determine is you need to use WPS, which is more complex, check your router to see if it has a sticker on it that says Wi-Fi Protected Setup. If that...

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

In this video, you'll use Scope and create a simple calculator while learning a little about private, public and protected properties in OOP programming. If you're looking to bone up your PHP coding skills you'll want to check this video out.

It is possible to convert your Excel spreadsheets into a PDF file by using your PC's Print Manager and Save As functions. This video shows you a step by step to create a password-protected PDF version of your Excel file.

Having a backup sump pump is integral in making sure your basement is always protected from water, and if you have the Basement Watchdog battery backup sump pump system, this video will show you the complete installation procedure. Find out how to build a pipe connection to the discharge pipe, install check valves, connect to the backup system and more.

Storing tools properly will keep you working wood and not doing maintenance on them. Shopsmith Academy shows you an easy way to ensure your tools will be protected from nicks and dings. Watch this video for useful woodworking tips. Search Shopsmith Academy on WonderHowTo for more woodworking videos.

This tutorial Tibetan fashion video will teach you to wear a Tibetan chupa. A chupa is a long, robe like garment that will keep you protected from the elements.

Installing a home security system can be expensive, but it doesn't have to be. This how to video shows you some easy practices that keep your home well protected. All you need is a few inexpensive items such as flood lights, signs, and light timers.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.
When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.