
News: Facebook Testing 'Profile Picture Guard' to Protect You from Scammers
Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.


Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

Even though the Ebola virus was discovered as recently as 1976, over 30,000 people have been infected since, and half have died a horrible death. Since there's no way to cure the infection, the world desperately needs a way to prevent it — and the five similar viruses in its family, the ebolaviruses.

Pertussis, or whooping cough, is a highly contagious disease that can be life-threatening for young children. New research backs a recommendation that all pregnant women receive a pertussis booster with each pregnancy, as it can help their infants fight off the infection.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Arsenic occurs naturally in the environment, but it is also one of the most commonly found heavy metals in wastewater, deposited there by inappropriate disposal and arsenical pesticides, for example.

Over 1.2 million people in the US are infected with human immunodeficiency virus (HIV)—and one out of eight of them don't know it. Even after decades of intense research into the virus, there's still no cure for it. One of the big problems is that the virus hides out in certain cells of the body, resisting treatments that kill it.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.
The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

I hate to break it to you, but you're probably here because you were trolled. Thanks to a Photoshopped image making rounds across Twitter, Apple fans were tricked into believing that iOS 8 allowed them to lock individual apps, accessible only through a passcode or fingerprint ID. While that's not technically true, we've got the solution for you.
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing."
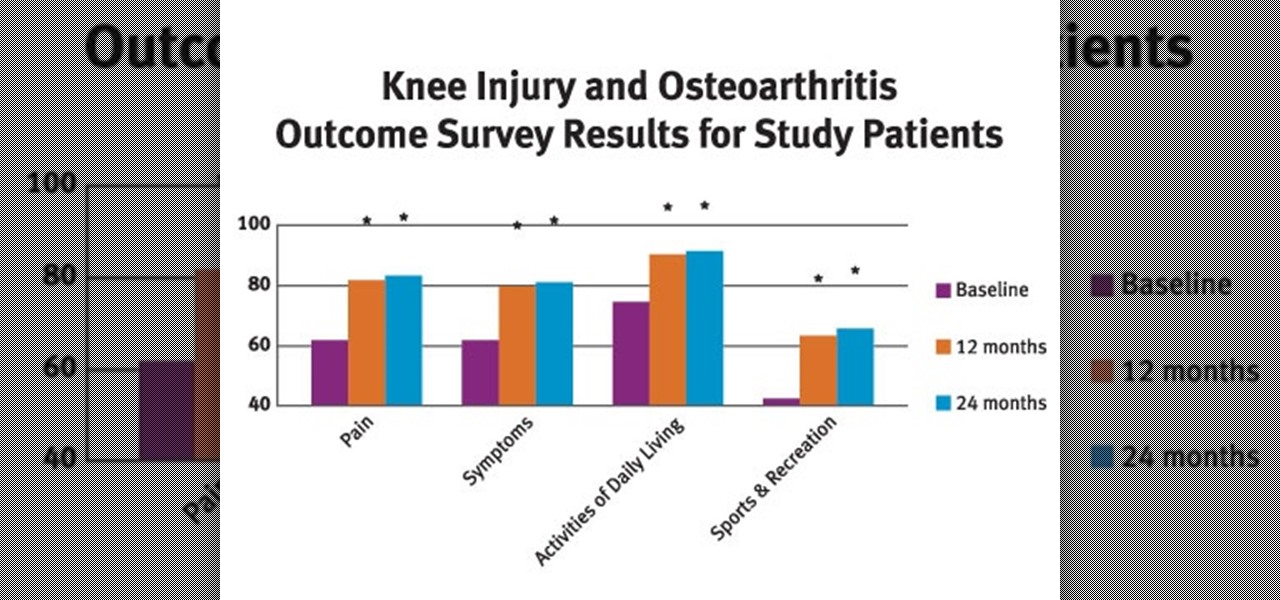
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.
There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?

Fasting—or the practice of regularly abstaining from ingesting anything except water—is a pretty drastic move. I tried to fast for two days and made it to the 12-hour mark, which is when I broke down and ate a quart of ice cream.

If hearing the names of classic PC games like Commander Keen, Fallout, Master of Orion, and Wolfenstein 3D send you into a fit of nostalgia, then DosBox Turbo is the perfect app for your Android device.

The Problem If you are working on a car restoration project, then you are going to faced with rust damage. This problem can’t be overlooked, as the entire project depends on repairing and eliminating rust. This would be like laying down new carpet to a house that was flooded, without cleaning the mess and making necessary repairs before laying the carpet down. The problem will still be there and the new carpet will be ruined.
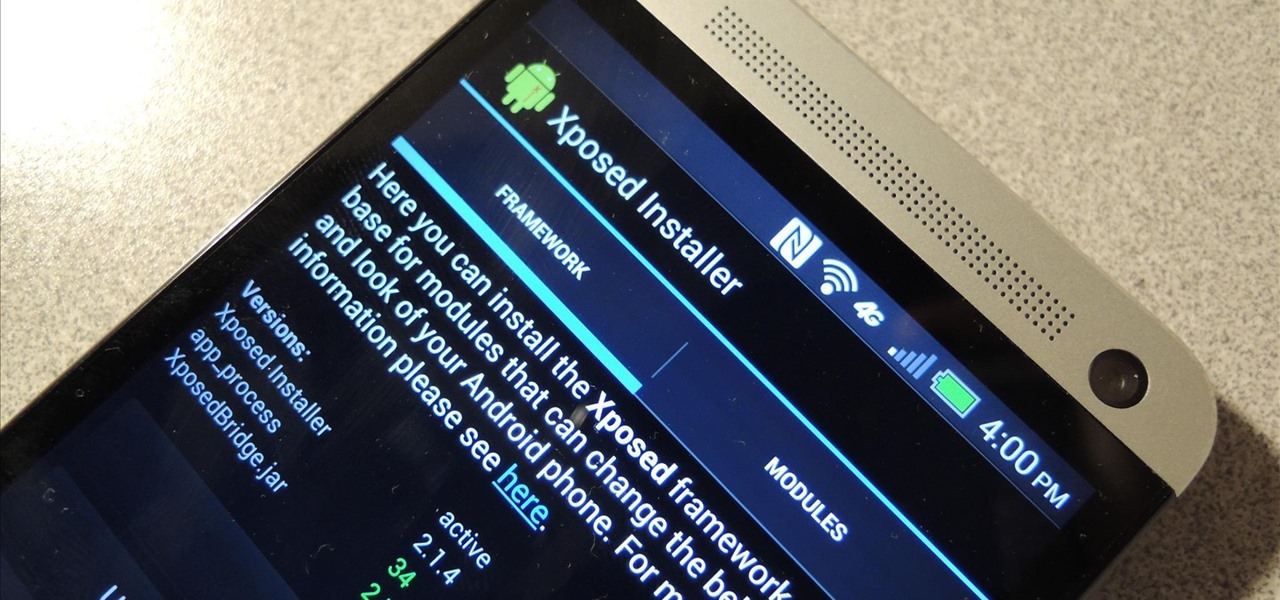
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!
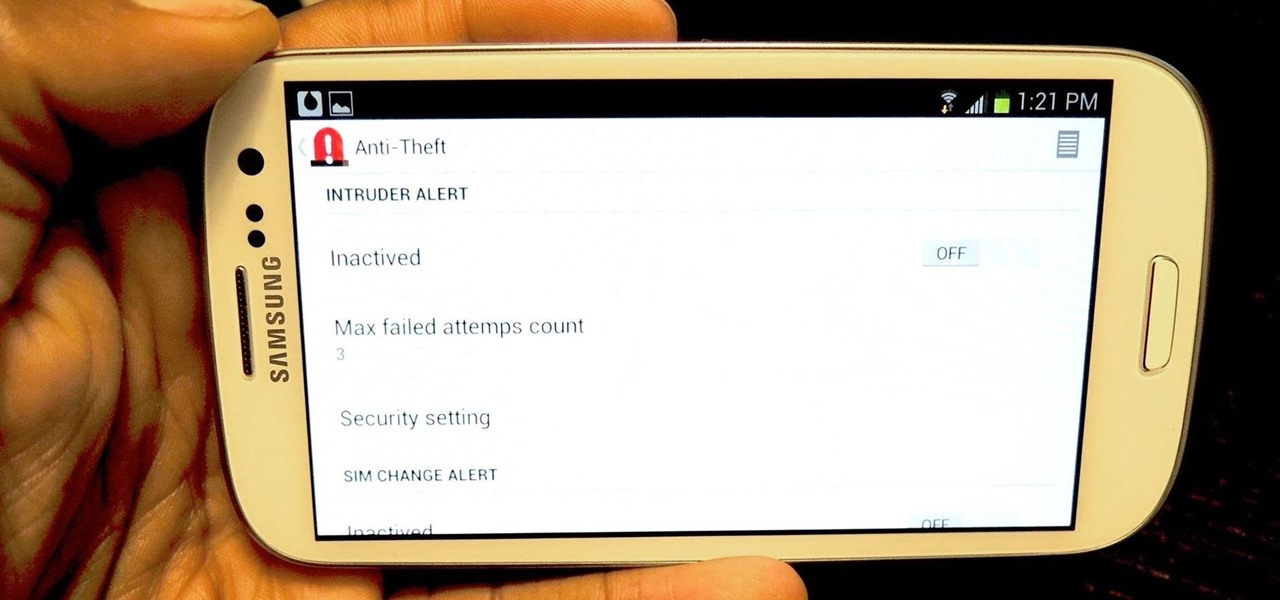
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

While the PlayStation 3 is an awesome gaming console and the iPhone is an awesome smartphone, Apple and Sony have made two devices (that could be perfect for each other) nearly incompatible. Truth be told, this is more Apple's fault than Sony's, but we'll get into that later.

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

For the vast majority of people, coffee is a must-have in the morning. It provides a stimulating effect that not only wakes you up, but sets your mood and attitude for the rest of the day. Personally, I wouldn't get anything done without coffee.
With Apple's Photos app, you no longer need a third-party tool on your iPhone, iPad, or Mac to blur or pixelate faces in your photos, helping you safeguard identities when sharing online.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.
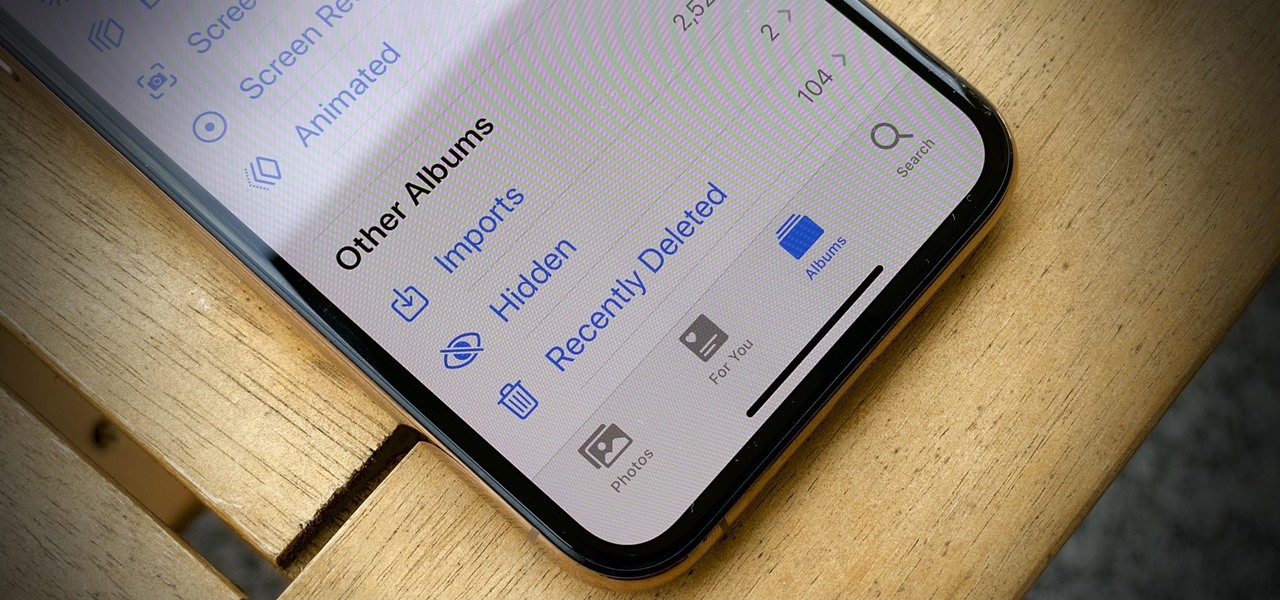
The "Hidden" album on your iPhone has always had one problem — it was never truly hidden. Since iOS 10, when the feature was introduced in the Photos app, any image or video that you conceal in the private folder could be seen by anyone with access to your unlocked device. Finally, that has changed.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.
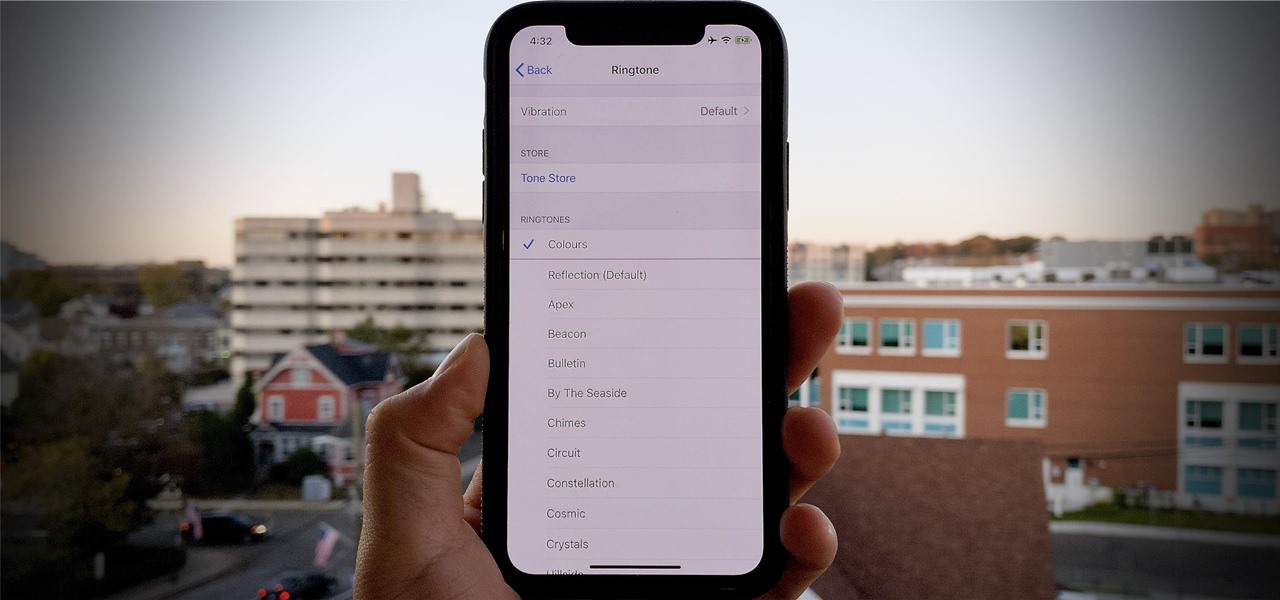
Have you ever heard someone else's iPhone ringing and thought it was yours? Of course you did. iPhone ringtones are iconic, but not varied. If you're using one of the more popular iOS sounds, you'll likely encounter it in the wild multiple times. Why bother, when you can create your own custom ringtones right on your Mac.