
How To: Add, ignore, accept and remove friends on Facebook
Ever wonder what happens when you hit "ignore" for a friend request? In this tutorial, presented by Facebook, you will learn exactly how to manage your contacts online.


Ever wonder what happens when you hit "ignore" for a friend request? In this tutorial, presented by Facebook, you will learn exactly how to manage your contacts online.

Watch Monty Don, as he plants and trains a nectarine tree up against a fence, using wires and tensioners. With tips on mixing compost and protecting trees from frost damage. Nectarines aren't too difficult to grow. All you need is sunshine, good drainage & plenty of moisture. You want to train a nectarine tree against a fence in the spring time. The how to video lends expert tips when dealing with nectarine trees. Train a nectarine tree against a fence.

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

A team of Japanese researchers have developed an airbag system for the exterior of the car, rather than the interior, with the purpose of protecting pedestrians.

A bipartisan group of 51 senators on Thursday threatened to oppose a global treaty regulating international weapons trade if it falls short in protecting Americans' constitutional right to bear arms. 51 US senators voice concerns with UN arms treaty | kvue.com Austin.

This seems unbelievable and quite unnatural, but the backyard surgery of reconstructing an insect's wing is possible.

It works. Very cool. Thanks, Kip. You will get to the nearest subnet of the ISP. You will not get to the actual street address.

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

Child Safety Window Treatments

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

HEXEREI n pl. -S witchcraft 67 points (17 points without the bingo)

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

These are the KGB Agent Guidelines as taken from 542542.com/guidelines. kgb Guidelines
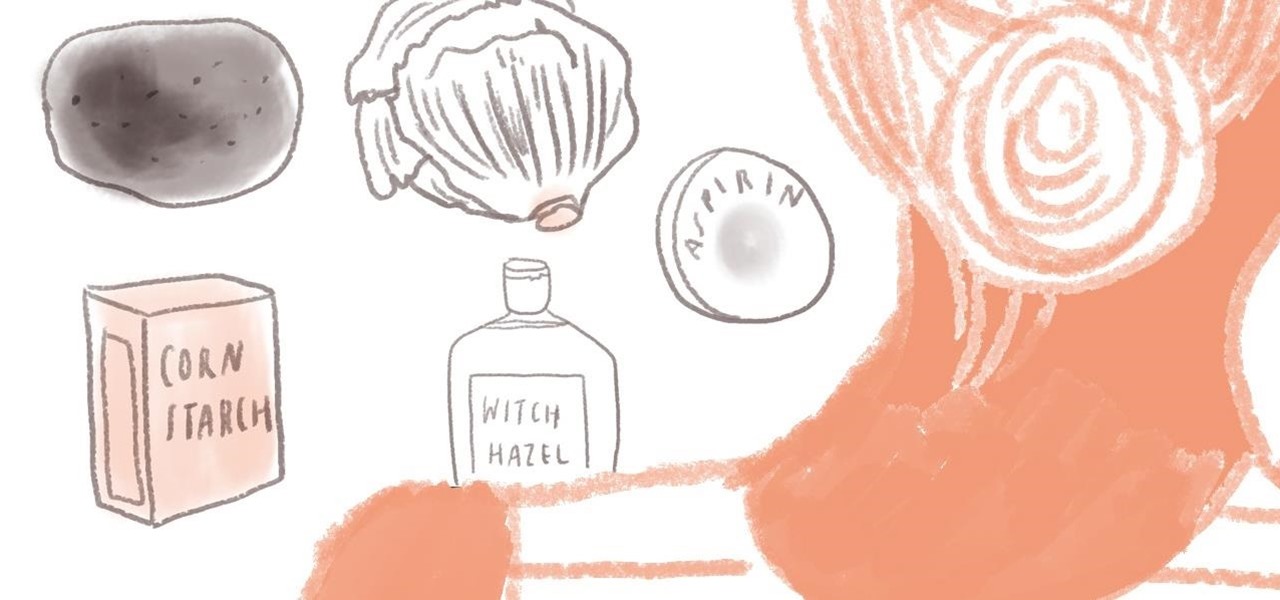
Though summer is almost over, that doesn't mean you should ever be lax when it comes to protecting your skin from sun overexposure. However, should you find yourself with red and burning skin after a last-minute weekend trip to the beach, listed below are 9 simple and cheap home remedies for relieving symptoms of sunburn.

If you ever need to wash your beanie and need some sort of hat mould to retain the shape of the fabric while it is drying, blow up a party balloon until it is about the size of your head. Place the beanie on top of the balloon until it dries.
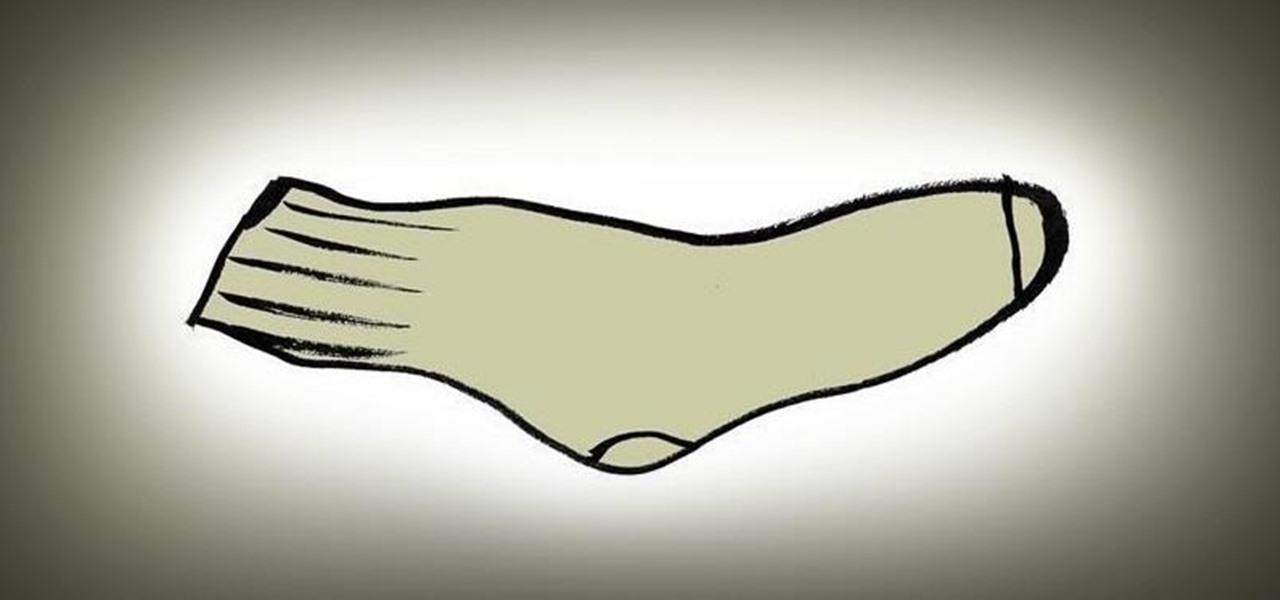
Need to give yourself a super-cheap back massage? Place a few tennis balls inside a long sock, tie the end, and place the sock on the floor. Then, lie down and roll your back against the sock to relieve your sore back muscles.
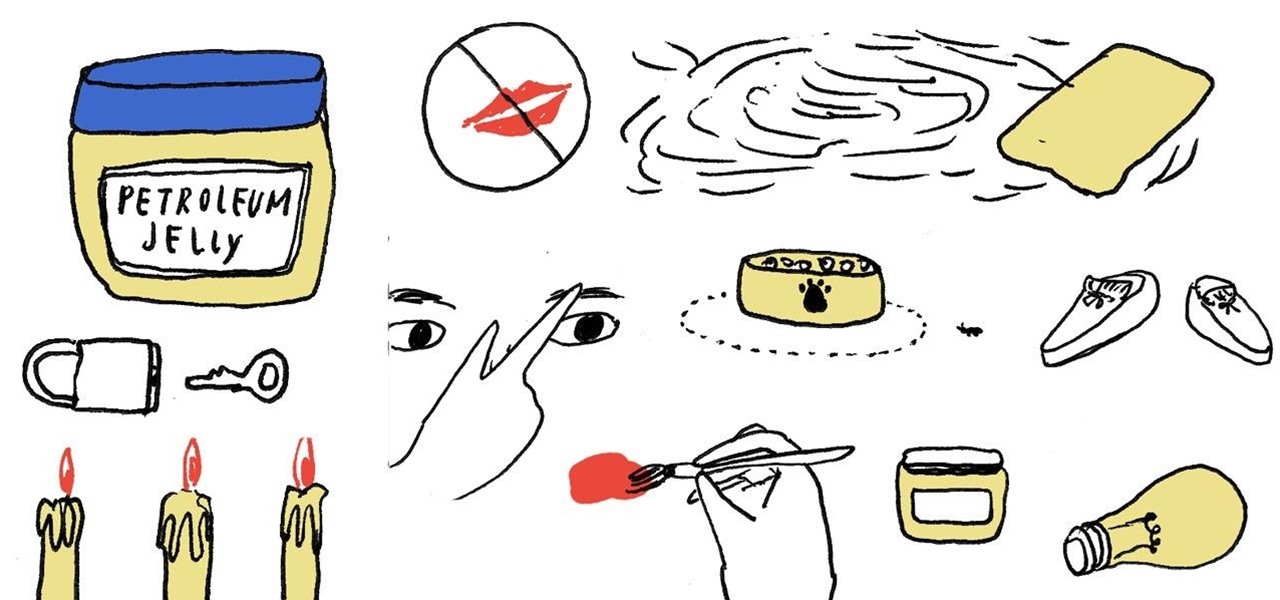
In 1859, 22-year-old chemist Robert A. Chesebrough accidentally discovered petroleum jelly when he visited a working oil well in Titusville, Pennsylvania. Oil workers complained of a gooey substance referred to as "rod wax" which kept getting into the machinery and slowing them down. Chesebrough noticed that oil workers also smeared this same substance on their burn marks or dry skin to help speed the healing process.

Politics(the Government) is built to accomplish a few things: maintaining order, providing necessities, operating businesses (stimulating the economy, trade), maintaining public relations and the most important of all, protecting the rights of the individuals it governs. It has a broad role, and as such, an array of bills, laws and rules to regulate itself and the country.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Three years ago, Double Fine productions held an in-house event called the Amnesia Fortnight. The company was split into four teams, each of which set out to spend two weeks developing an idea for a small game and present it to the other groups at the end of the duration. All of the ideas turned out to be winners, and founder/owner Tim Schafer secured publishing deals for all four games to be released on a combination of XBLA and PSN. In honor of the excellent Trenched becoming the third game...

The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who
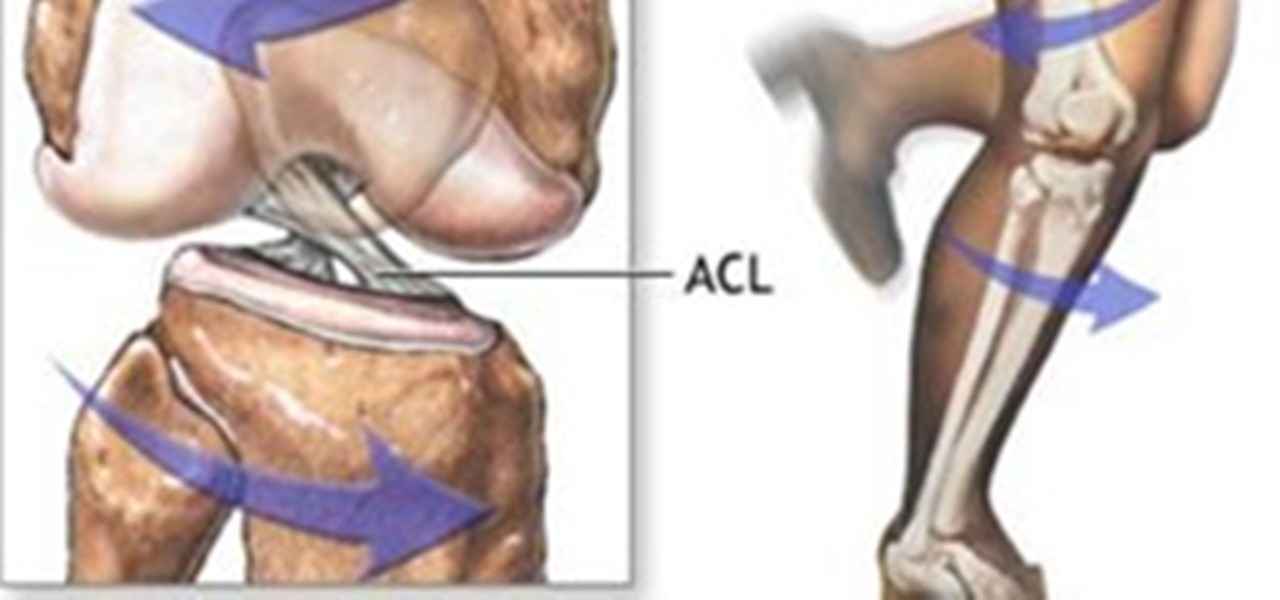
The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who have witnessed or suffered a torn anterior cruciate ligament (ACL) are familiar with the pain, surgery and intense 6 to 8 month rehabilitation that accompanies the injury, not to mention the disappointment of ending a season. Nationwide, this will occur more than 500,000 times this year, and female athlete...

Oh, LifeHacker, we love you. You've brought us so many handy HowTo's: Hack Wireless Internet, Bypass Blocked Websites, Convert a Laptop Into a Projector, Watch TV & Movies on the Web For Free, 10 Must-Know Google Privacy Settings, and more.
Does this video prove that otherworldly intelligent life has visited Earth? No. It does not prove anything other than there are designs ‘etched’ onto the surface of a field. Does the video immediately above prove that otherworldly intelligent life hasn’t visited Earth? Yeah, you saw it coming; no, it proves nothing more than humans are able to ‘etch’ designs in a field of grain.

Minecraft was first released just a few years ago, but when a paradigm-shifting piece of media comes along the rest of the world is quick to take inspiration from it. The absolutely terrible XBLA knock-off FortressCraft was the first, and last month a much more interesting game called Terraria came out on Steam for $9.99. It is clearly inspired by Minecraft, and there is a long checklist of identical features. It is, nonetheless, a very different product, and just might be called the first in...

Hello, everyone. My friend and I recently released a Defense of the Ancients (DotA) map that went viral and thought I should share it with Minecraft World on WonderHowTo since you guys helped me out when I first started making videos! We were featured on Kotaku, RockPaperShotgun, Gamespy, The Verge, Joystiq and many more websites!Exciting!You can see the full details below are head straight here for the downloads.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Dungeon Defenders is the most exciting craft game on the Fall 2011 release schedule. I got a chance to play it at PAX in August and interviewed developers Trendy Entertainment last month. After more than a year of publishing difficulty and delay, the game finally came out on PSN, XBLA and Steam. I put about 20 hours into the XBLA version over the past weekend, beating all the campaign maps and racking up a huge pile of in-game money. It is not a perfect game. But it is a huge, challenging, an...

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Once you get past the initial quick start setup of the Canon EOS 5D Mark II, capturing pictures in auto mode is a breeze. But what do you do after you've snapped those photos? This quick guide will show you the easy steps to viewing your images directly on the camera.

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.

There’s no point to playing all of the different tower defense games available today. Most adhere to the original formula, so playing 2 or 3 really good ones (like those mentioned in my previous post) would be more efficient.

Working from home is already challenging. Add the threat of a cyberattack into the mix, and the situation gets even hairier.

Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity.
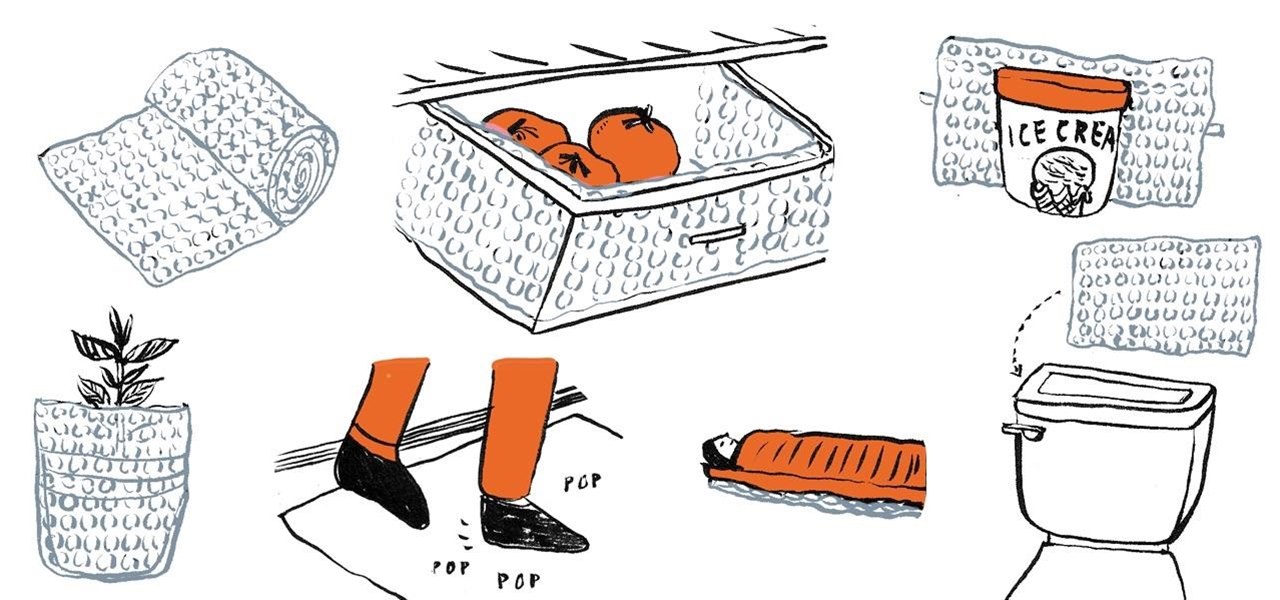
If you're like me, you have a secret dream of living in a house completely covered wall-to-wall and carpet-to-carpet in bubble wrap. Until you have enough of that pliable transparent plastic with air-filled bubbles, there are some truly practical things you can do with the little you do have—besides packing fragile objects.

Windows has its own built-in antivirus program called Windows Defender, which kinda sounds like a sweet arcade game, but it actually does a pretty good job of protecting your Windows PC from spyware and malware.