A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested their method on a Samsung Galaxy S6 and Huawei Honor 7.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.
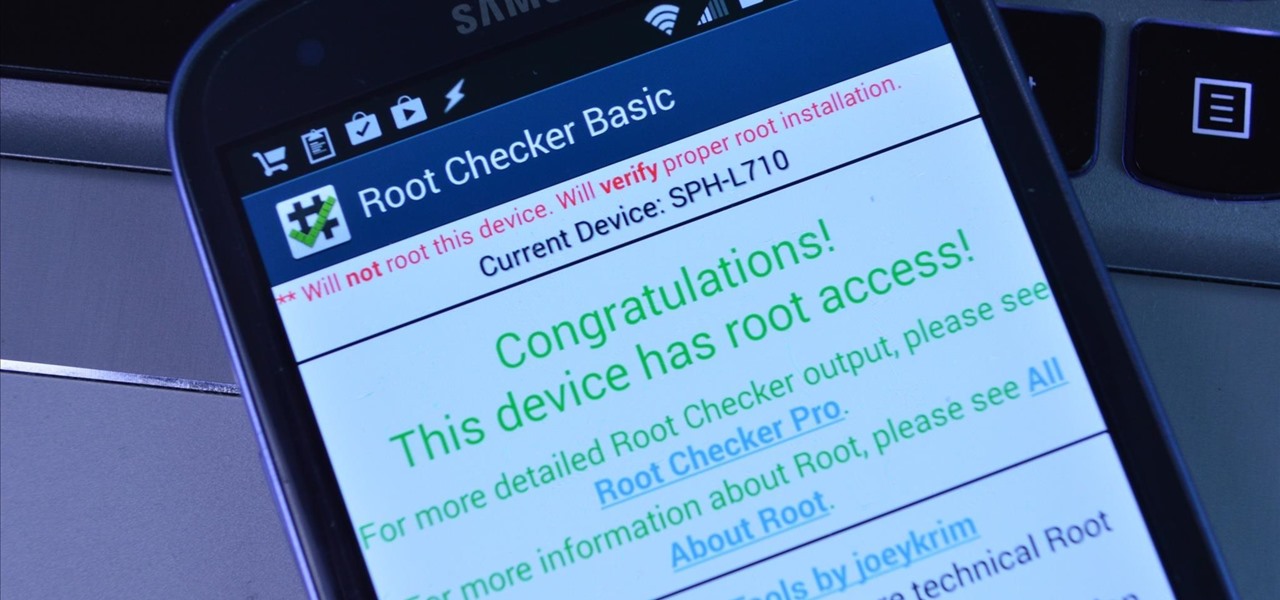
Rooting an Android device used to be a nightmarish labyrinth of .zip files and command prompts, confusing seasoned modding veterans and newbies alike. Thankfully, the process has gotten simpler over the years, with various "one-click" rooting tool kits surfacing and working for nearly every major Android flagship on the market.

Want some protection for the front of your new Arrma-RC Vortex? Here's how!

Digidesign has transitioned all of their plug-in software copy protection from floppy drive based key disks to copy protection authorizations that reside on the iLok technology provide by PACE. The following is some information about iLok technology.

Electrical engineering is a math-heavy business, and you're certainly not alone if you're studying it and having trouble with the math. Watch this video for a very cogent explanation of a simplified method for calculating resistor dividers in a circuit.

Once again, Samsung has certified its flagship Note series with an IP68 rating. With this rating, the Galaxy Note 20 and 20 Ultra have some degree of dust and water resistance.

The Pixel 4 and 4 XL are the first Android phones released in the US to support secure facial recognition. You no longer have to hate on your Apple's friends because you now have "Face ID" as well. So I assume you want to set it up right away — here's how.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

You know the signs—sneezing, fever, nagging cough, no energy, no appetite. It's the flu, but this time, it's your dog who's down and out. Yes, dogs get the flu, too. However, a team from the University of Rochester Medical Center and their collaborators have developed a new vaccine that may make the doggy flu a thing of the past.

In this video we learn how to make a poppet. A poppet is generally used to give protection, healing to the ones we love. It may be our cat, aunt, home, or whatever we like to do it for. Here in this video we make a poppet for an animal. So the requirements are color shields, scissors, lavender and roots (for protection), citrine. Citrine helps in cleansing. Draw the shape of the animal we require on a cloth of two stacks and cut it using scissors. Use the thread to attach the edges. Leave a s...

You never know when you're going to need a knife. Whether you carry it on your person for protection or simply use it to open stubborn packaging and envelopes, pocketknives are super practical yet also very dangerous if they accidentally open up in your pants.

This hair tutorial is called a wispy bird's nest after its, well, wispy quality and organized jumble of hair strands that forms into a cohesive whole.

Whatever your favorite flower may be, you can't deny that roses are the most romantic and alluring flowers around. In this tutorial, Reiberry bases a delicate hairstyle on the robust beauty of a rose. This pinned-up side bun is unlike any chignon you've ever seen, and though a bit difficult, the results will be well worth the effort.

This hairstyle could easily be mistaken for simply missing a spot while you're pinning your hair into an updo during the morning rush, but the lovely rosebud hair accessory ties it all together.

This video explains how to build a shaded vegetable garden. The instructor begins the video my explaining the benefits using a shaded garden as it offers protection from hail, heavy rains and gives you the ability to control the outdoor temperature better. The simplest way to build your shaded building is to place large wood forms into the ground and place wood planks over the top of each and nailing them into place. The entire frame is then covered with a plexiglass roofing to keep out rain ...

“Great beach hair” doesn’t have to be an oxymoron, if you follow our advice in this how-to video. The elements aren't always kind to your hair, but an arsenal can keep your hair in top shape. To help tame your hair at the shore, try leave-in conditioner, anti-frizz spray, straightening cream, clarifying shampoo, baby shampoo, apple cider vinegar, a swim cap, and when all else fails, a hat (which is great protection from the sun-your skin will thank you too). Check out this video hair styling ...

Watch this science video tutorial from Nurd Rage on how to make copper sulfate from copper and sulfuric acid in three ways. They show you how to make copper sulfate from copper and sulfuric acid using two chemical methods and one electrochemical method.

To pick locks, one must either have an expensive lock-picking set or be skilled with whatever they have available to them. Bobby pins, soda cans, and even butter knives can get the job done, but each needs to be reworked into something more appropriate for the lock in question.

Check out this Do It Yourself (DIY) RV maintenance and repair video to learn how about RV battery maintenance. Know how to do it to keep your batteries running strong in your recreational vehicle with this RV tutorial video.

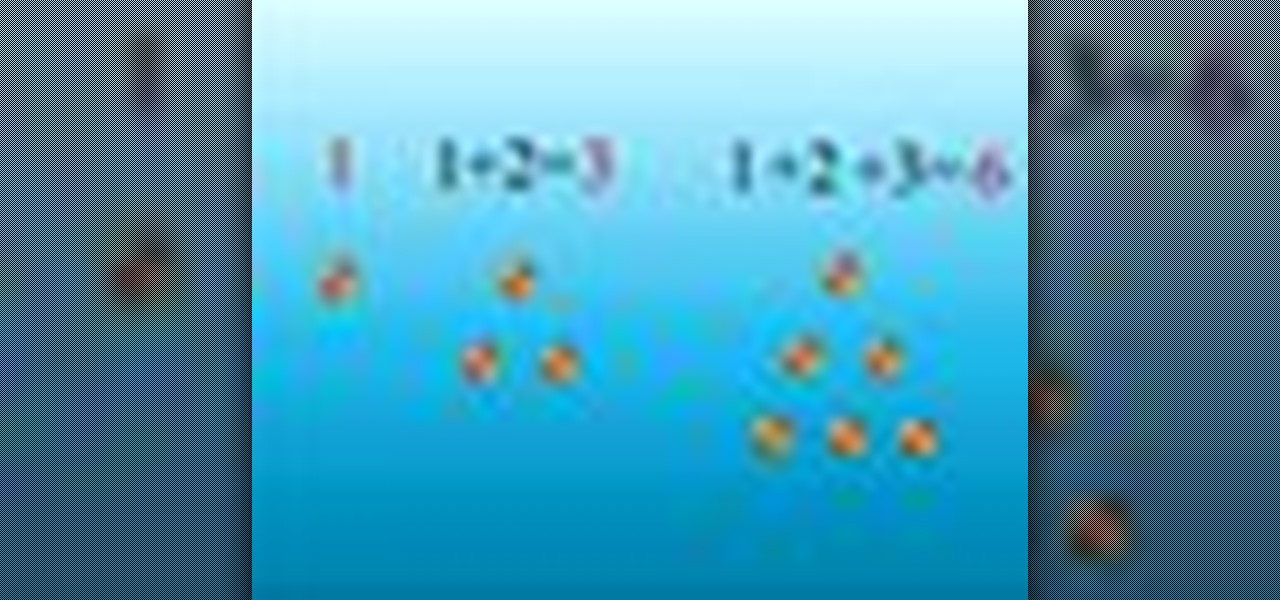
The first video is an elementary explanation of triangular numbers and a Gauss demonstration for the sum of the first 100 natural numbers.

In this how-to video, Andrew Price of Dryad Bushcraft teaches methods of trapping animals in a survival situation. Learn methods of tracking animals as well as the West County trap and wire snare method. Watch this video hunting tutorial and learn how to trap animals like a real Bushman.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Ok, I have to admit, I drop my phone around 2–4 times a week. I'm horrible at protecting it and I've gone through my fair share of cracked phones. Most of the time, once the phone is cracked it's just easier to get an entirely new phone, rather than have to fight your phone provider for a fix.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.

This video tutorial belongs to the Electronics category which is going to show you how to reset the Blackberry Bold 9000 / 9700 with three methods. In the first method you hold down the Alt key, the Caps lock key and hit Delete. Your Blackberry will start resetting. This process will take about 2 minutes to complete. The second method is the double reset. Hold down the Alt key, the Caps lock key and hit Delete twice. This method is helpful if your Blackberry is frozen. The third method is cal...

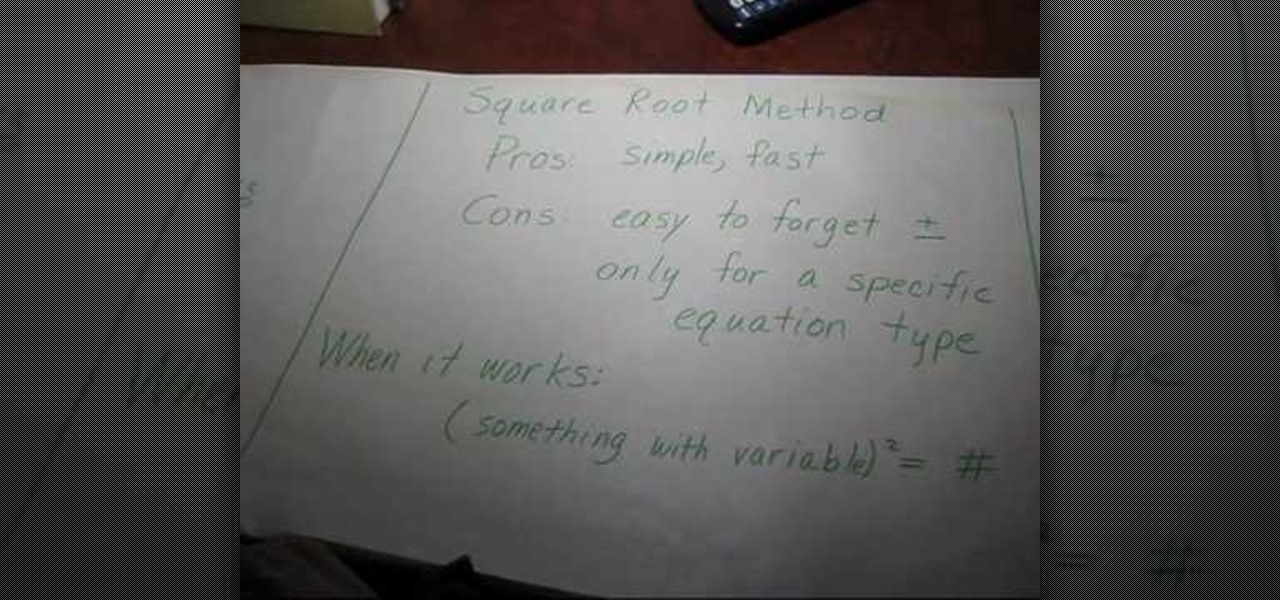
In this video the instructor shows the different methods of solving quadratic equations. There are many methods to solve quadratic equations each with its pros and cons, each method suitable for a particular situation. The first method to solve quadratic equation is factoring. The advantage of using this method is that it is quick and easy. But the problem is not all equations can be factored very easily. This method requires a lot of practice and intuition. Use this method when the discrimin...

In this instructional harmonica video, learn which of two methods to use when playing the harmonica. There is sometimes a debate among harmonica players on which method is better to use: the lip pucker method or the tongue block method. Both methods play their part in helping the beginner become a more well rounded harmonica player. This tutorial teaches you both harmonica methods.

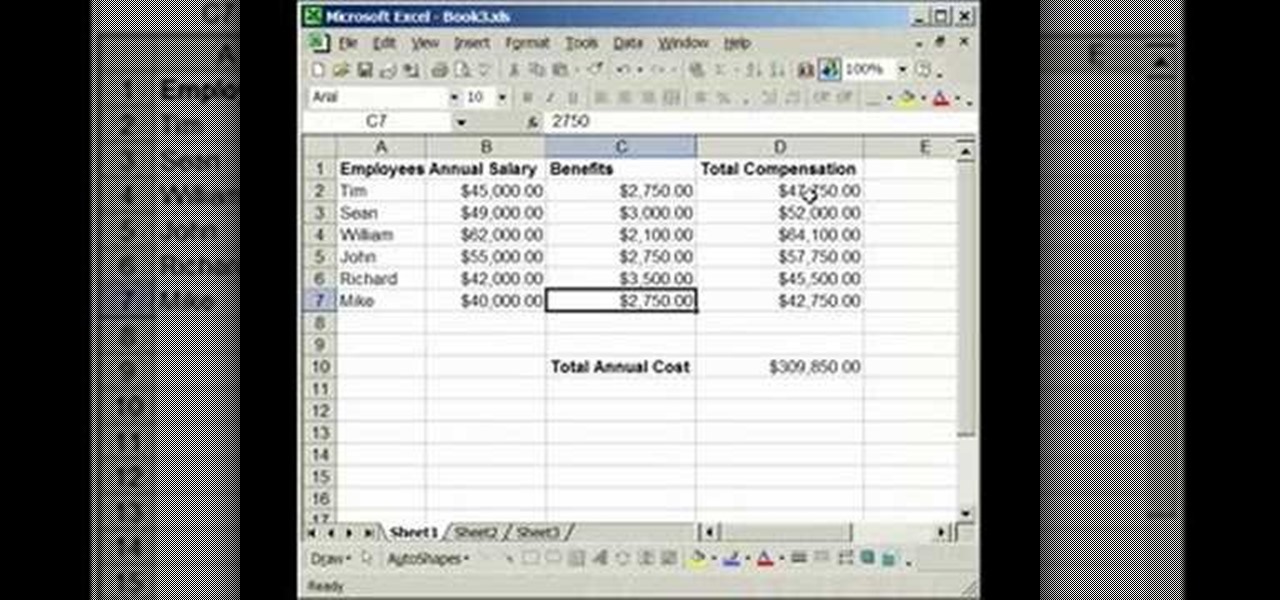
In this tutorial, we learn how to lock and unlock cells in Excel. First, right click one cell and click on format cells. Go to the protection cell, and then un-check the locked category. Click ok, then go to protect sheet, inside of tools. Now, do now allow locked cells to be checked. Now, you will not be able to select cells in the worksheet except cells that are unlocked. This is a great way to protect your information, so it won't accidentally get deleted or ruined. You can do this for ent...

In this tutorial, we learn how to prevent edits or changed in documents in MS Word 2007. Start by going to the review tab, then click on protect documents. Then, click restrict formatting and adjust the different settings. Click on the check marks to choose what types of settings you want to restrict from being changed. This can make it impossible for anyone else to edit the pages except for the original author. You can also make an enforcing protection password so only the document creator c...

Achieve alluring and sexy waves rather than Shirley Temple-esque tight finger curls by watching this hairstyle tutorial on how to do a deconstructive waving technique. Girls with longer hair should opt for a smaller barrel curling iron, since a larger barrel will not create the same type of wave that we are trying to achieve.

This gorgeous crescent moon hairstyle consists of loose hair braided behind your head into a twisted chignon, the rest of your hair on the other side let loose for a novel take on the idea of a half up, half down hairstyle.

Summer is just around the corner, and though many of us are going to dash out of our schools in relief and joy and then head straight out the pool in our skimpy bikinis, we should be covering up with sunblock and hats to prevent noxious nasties like cancer.

This video involves beauty tips on how to get rid of chapped lips. The video starts out by listing items needed to take care of chapped lips; the first item listed is chap stick. The video specifically recommends a chap stick that has SPF protection. The other items needed are a tooth brush and a clean towel. The video next explains to rub chap stick on your lips. Next, a tooth brush is used on the lips in circular motions to remove dead skin cells. The purpose is to allow your lips to heal m...