Seagrass may help your favorite beach stay a little less toxic. A new study, led by Joleah Lamb, a postdoctoral researcher in the Harvell Lab at Cornell University, found that coastal seagrasses reduce levels of pathogens dangerous to humans and marine organisms in near-shore waters.
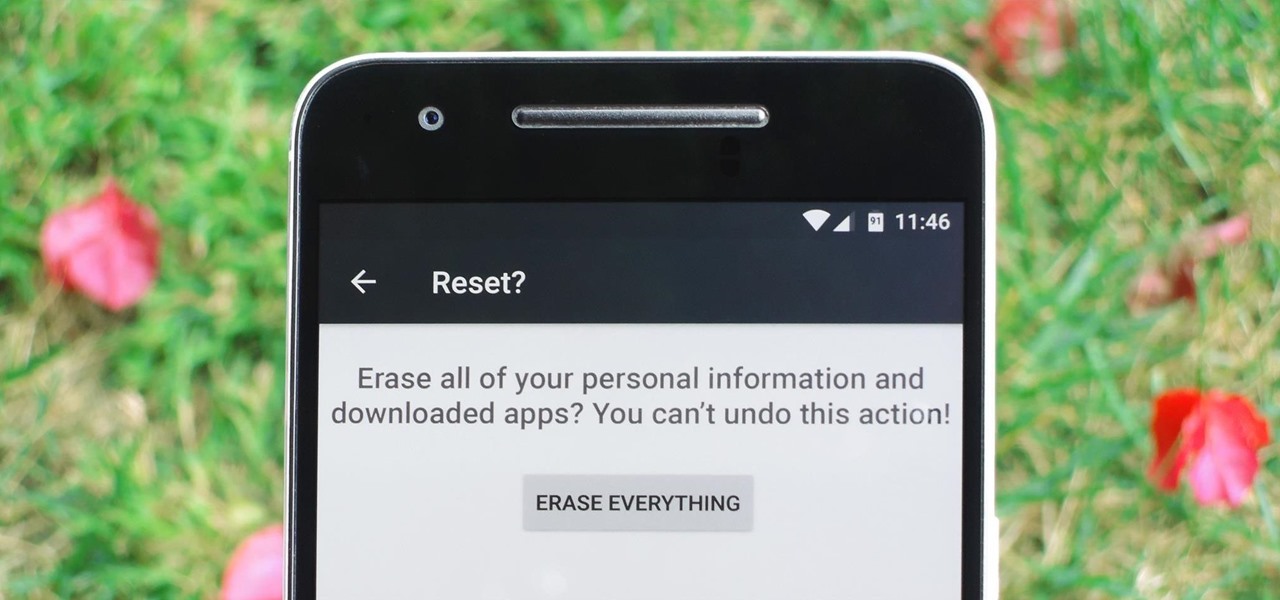
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

You've been there. Those precarious few seconds between dropping your expensive smartphone right on its face and reaching down to survey the damage. Or maybe you got thrown in a pool while your device was in your pocket, or you dropped that sucker right into the toilet bowl. Heck, I've managed to accidentally wash two devices by leaving them in my pants pocket when throwing in a load of laundry.

This science experiment deals with sublimation of dry ice into carbon dioxide (CO2) gas. In the video, I'll demonstrate how pushing a quarter into a block of dry ice makes the quarter scream and shake vigorously.
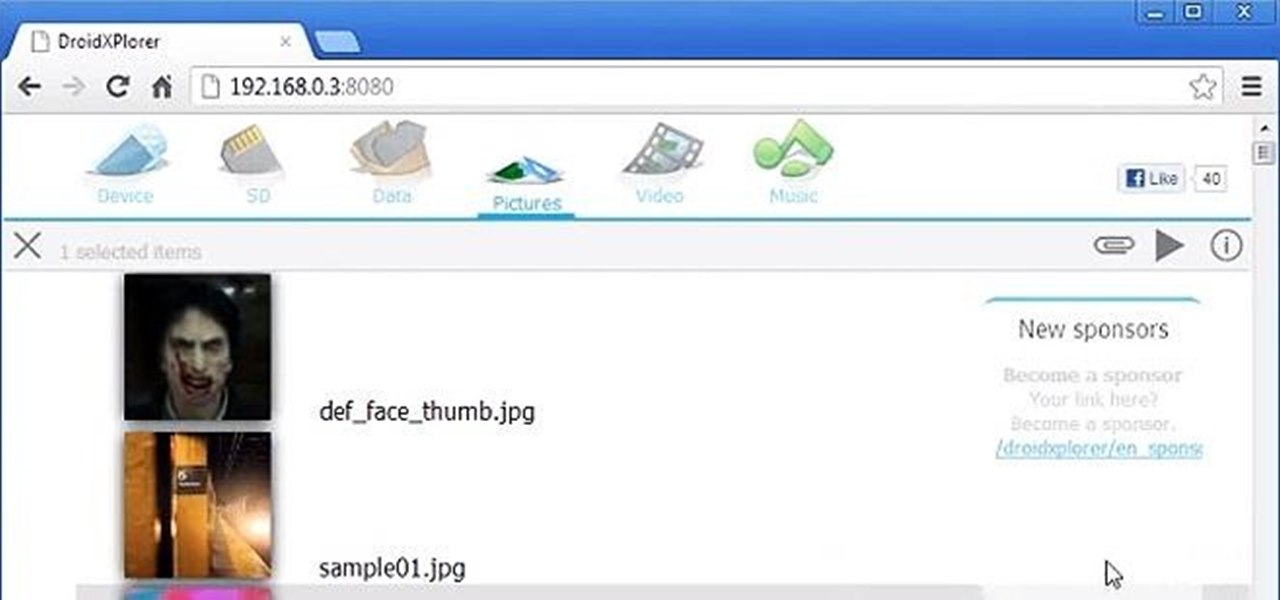
Want to search through your Samsung Galaxy S III or other Android smartphone using only a web browser? Thanks to XDA-Developers member Metal Droid, you can now access and download anything from your phone through any browser on your computer using DroidXPlorer.

Your first bank account can be exciting and confusing at the same time. Check out this video and learn how to manage your money and accounts so you don't wind up in the red. You don't have to earn an MBA to make good financial decisions; this video offers plenty of suggestions to keep your accounts on track.

Do you watch women with sleek and shiny hair with envy? Now you can transform your frizzy hair into a silky smooth style. This isn't magic and does take a little more time than toweling dry. But with a few products, a blow-dryer and a little extra time in the morning you can achieve this look.

Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got the best picks to slim you down to the essentials.

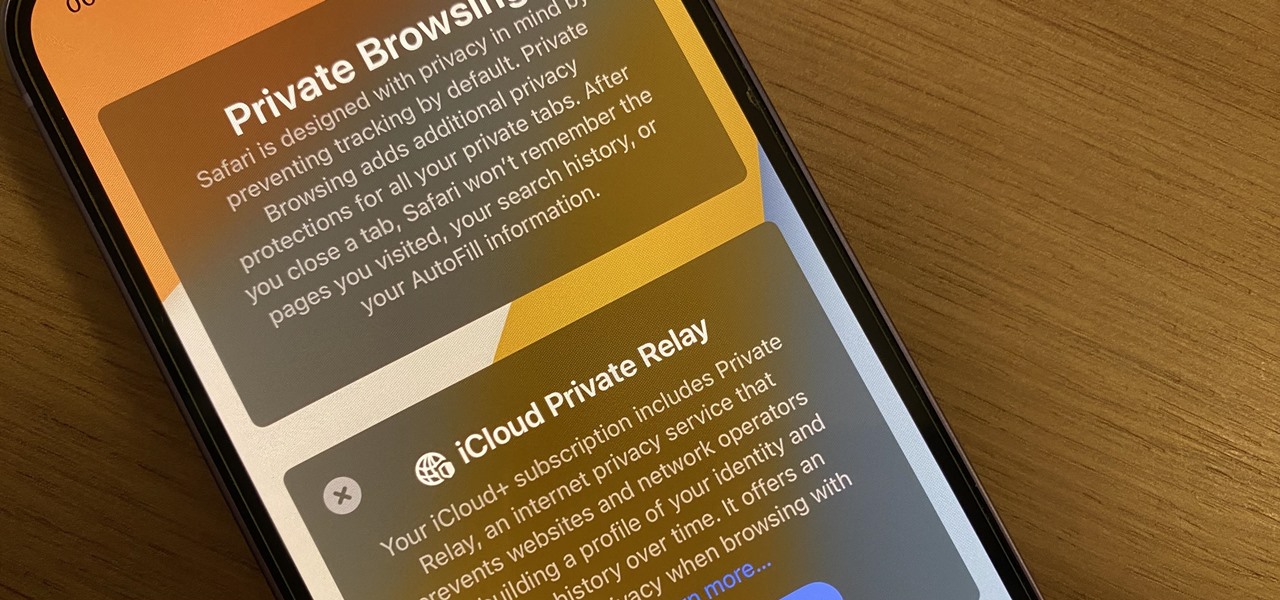
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

Despite their awkward appearance, Apple's AirPods have become the earbuds of choice for working out, largely thanks to quality audio without any wires to tangle. However, at $159 to start, they aren't exactly for everyone.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

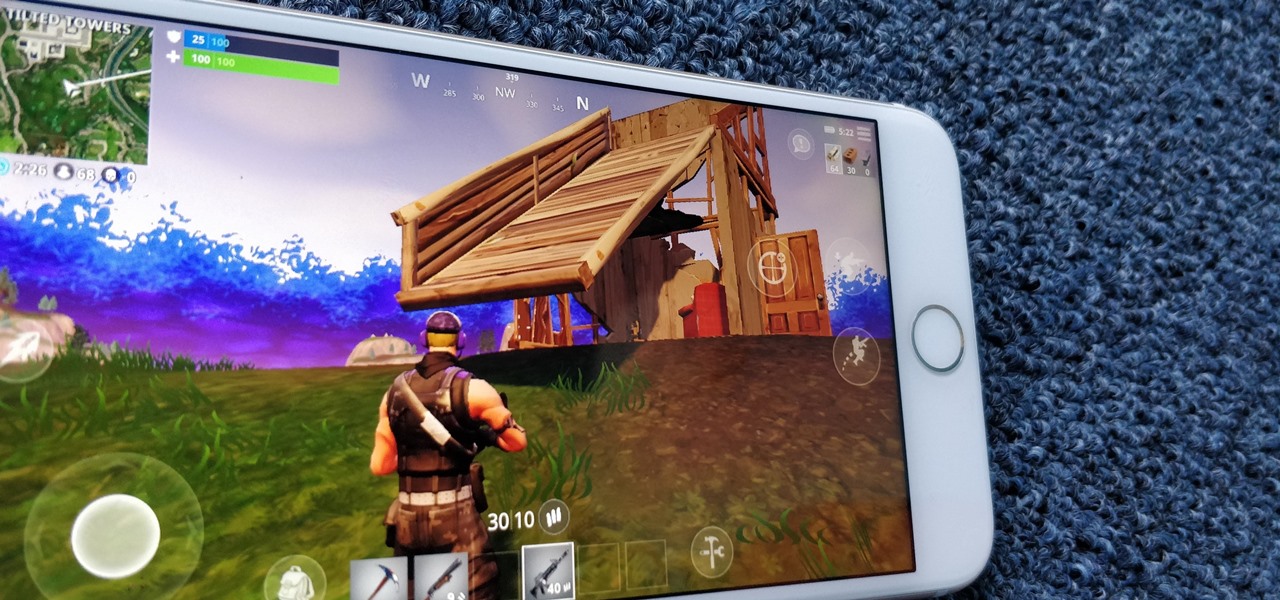
One of the more unique aspects of Fortnite Battle Royale is the ability to create structures. Using in-game materials, players can create walls and ramps for cover and to extend mobility. But creating isn't limited to just the basic generic structures. To really maximize their benefits, great players edit their creations to fit their needs.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

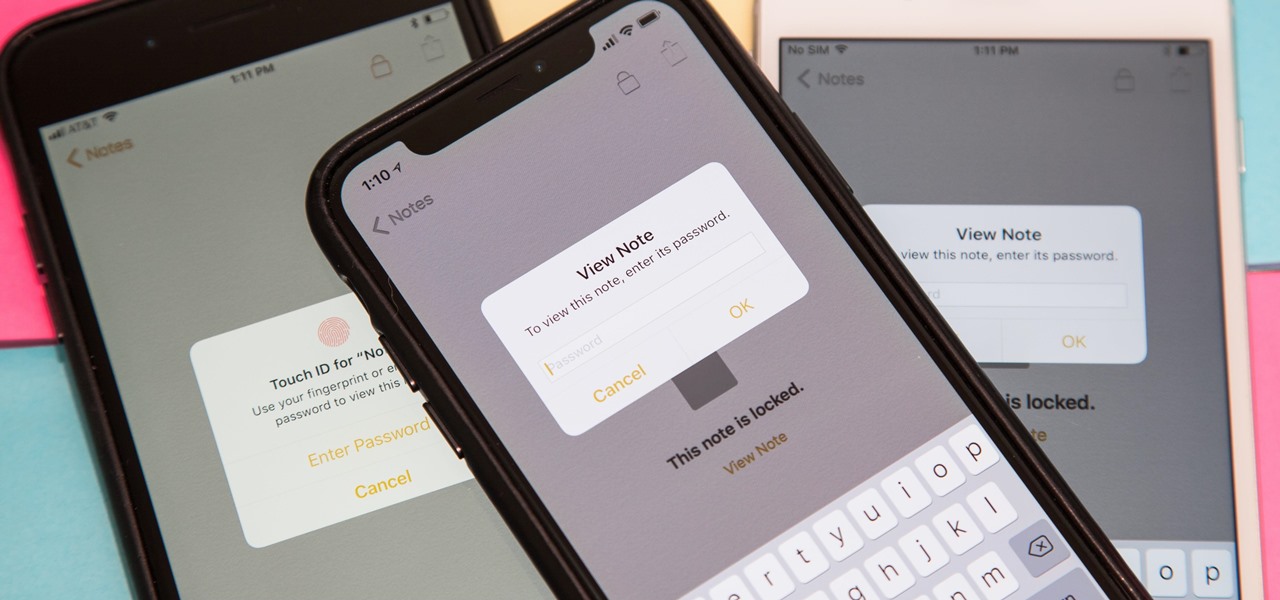
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

The food TV chefs prepare make our mouths water. From one scrumptious creation to another, they fly through preparation without frustration or error. They make us think we can do the same with similar ease and delectable, picture-perfect results. Some of us have noticed, though, that these TV chefs don't always adhere to the same safe food handling guidelines we've been taught to follow.

Cats give us so much—companionship, loyalty, love... and now the bird flu. Several weeks ago, a veterinarian from the Animal Care Centers of New York City's Manhattan shelter caught H7N2 from a sick cat. According to a press release from the NYC Health Department on December 22, "The illness was mild, short-lived, and has resolved." This isn't the first time cats have passed infections on to humans, but it is the first time they passed on the bird flu—avian flu H7N2, to be exact.

As a former repair tech, I've heard the same reasons over and over as to why people opt not to purchase phone insurance. Some cite the cost—why pay extra every month for insurance when you're careful with your phone? Deductibles are expensive, so why not just spend that money on a repair instead of getting a refurbished phone as a replacement?

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff.

Android Messages, formally named simply "Messages" now, has built-in spam protection. This doesn't get every spam SMS message, however — in fact, you can still get unwanted texts multiple times daily even with the feature enabled. Thankfully, you can manually block numbers, too.

There are plenty of reasons to upgrade to the iPhone 12 mini. Maybe you want to take advantage of the improved camera system, or you're intrigued by the return to a smaller form factor. But one of its coolest features might be MagSafe, a completely different way to charge and accessorize your iPhone.

The new iPhone 12 Pro Max is equipped with MagSafe, the iPhone 12 lineup's most talked-about feature. While Apple previously used MagSafe for its magnetic charging connectors on older MacBook models, it's given new life to it on the iPhone, and in a much better way. But can it do for you exactly?

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

Tax season is always stressful, especially for entrepreneurs and small business owners. Rather than wait until March to get your finances in order every year, learning how to keep track of your expenses is a valuable skill that saves you and your business time, money, and plenty of anxiety.

Everyone seems to be talking about Elon Musk's new futuristic Tesla Cybertruck, the vehicle that either looks like a cool moon rover or an outlandish video game replica, depending on your tastes.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

When we reviewed the best file managers on Android, MiXplorer easily topped our list with its abundance of features, including tabbed browsing, support for up to 19 different cloud services, file and folder encryption, and much more. The only major complaint we had was the fact it couldn't be installed from the Play Store, but now, that is no longer the case.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.