Learn to steal Kim Kardashian's pin curls and bangs with this video tutorial! Items needed: curling iron, straightener, blow dryer, hair spray, mousse, dual prong clips or bobby pins, comb and medium length bangs.

Want softer skin, and to see in the dark? Then step right up for your daily dose of Vitamin A!

Cast iron skillets are the original non-stick "Teflon" coating. An iron skillet seasoned properly will keep food from sticking, and its is great for browning and easy to care for. And good cast iron cookware will last a life time. Cast iron skillets have been handed down from generation to generation. Rita's favorite cast iron skillet was handed down from her mother and is at least 100 years old.
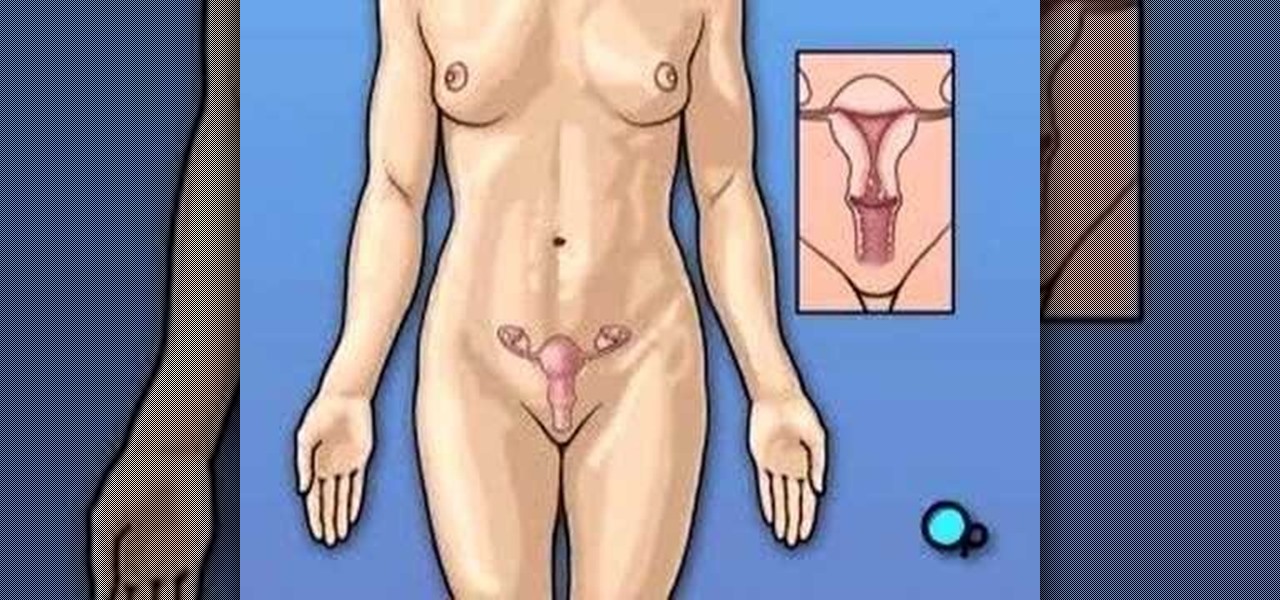
Your gynecologist has recommended that you undergo surgery to remove vaginal fibroids. But what does that actually mean?

The Drink Of the Gods. Yerba Mate. Learn how to prepare Yerba Mate and drink it properly with sexy Gianny L! You will enjoy the ceremony and will notice a subtle lift, due to the caffeine (mateine) contained in it. GiannyL demonstrates how it's all done.

f you are going to be towing a trailer, using an enclosed cargo carrier with lights, or if you want to use an electrical accessory (such as lights, or a winch) you are going to need to add a wiring harness. This video will show how to install a wiring harness on a Chevy Express full size van. It also includes some helpful tips about installing the ground wire, using dielectric grease, and installing a bracket to hold the wires so they are protected from damage.

The augmented reality industry has a bright future built on innovation and growth, but that doesn't mean we can't look back at the close of the year to see what the industry has accomplished from a business perspective.

Cited by many listed on this year's NR30 list as the most important event in the last 12 months, last year's release of ARKit catapulted Apple CEO Tim Cook to the top of Next Reality's rankings. This week, we dug deeper by explaining why he's at the top of the list of NR30 Mobile AR leaders.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

Wound infections don't usually enter the blood and become systemic, spreading the infection throughout our bodies, and there's a good reason for that: Our bodies actively work to prevent it, according to research that discovered a new use for a protein first discovered decades ago.

Call them what you will—moss piglets, water bears, or by their real name, tardigrade—but these intriguing tiny creatures can come back from the brink of death. They can survive boiling, deep freezing, UV radiation, completely drying out, and even a trip to space—without the benefit of being in a spacecraft.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

Taking care of your car requires effort, whether you take it to the pros for washes, waxes, and detailing, or you spend time to make it shine yourself—and it often seems that, right after your car is sparkling again, rain or midnight moisture appears to cover its surface in water spots. With a small tweak to your typical car care routine, you may be able to keep your car's surface and windows shining longer and better: you just need to add a little hair conditioning liquid.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

We live in a time where privacy is rare and our files can be easily accessed by just about anyone. Having your phone protected by a passcode is great, but if someone figures it out, they can easily access anything on your phone.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

The Problem If you are working on a car restoration project, then you are going to faced with rust damage. This problem can’t be overlooked, as the entire project depends on repairing and eliminating rust. This would be like laying down new carpet to a house that was flooded, without cleaning the mess and making necessary repairs before laying the carpet down. The problem will still be there and the new carpet will be ruined.

One of the vital fashion accessories is sunglasses. Sunglasses assist in creating a sort of unique identity for you. Your age, the shape of your face and of course your personal taste influences the precise style you decide on. There are some basic factors that must be put into consideration when you are thinking of buying your pair of sunglasses. It is important to be educated about what makes a quality pair of sunglasses. So when you want to choose your next pair of sunglasses, keep the fol...

It's hot this summer, but it's not that easy to cool down when you're on the go. You can't take an air conditioner with you, and a handheld fan will just tire you out, so you'll need to find more creative ways to cool down when you're on the go. One of these ways is a DIY solar-powered fan baseball cap.

It starts innocently enough, with a nosy friend hovering over your shoulder to see what you're texting. Somehow, that doesn't satiate their inexplicable thirst for curiosity, so the first chance they get, they're rummaging through all of your super private photos—even though you told them not to.

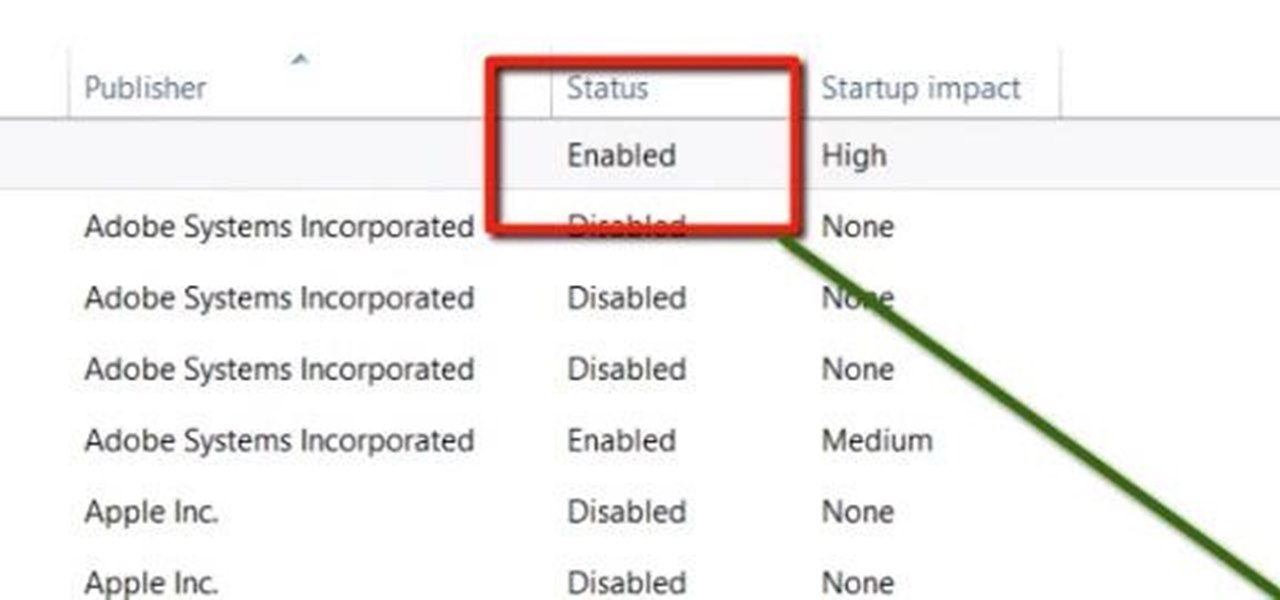
This Windows 8 tutorial will show you how to enable or disable applications from starting up when you boot up your computer. It is sometimes important to disable applications to ensure a smooth start, especially if you computer doesn't have very powerful hardware.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

Hello! This tutorial is made for all who like to sunbath, but also do not want to get those tiny first wrinkles too soon. Or even skin cancer.

Long term power outages can be an inconvenience. It means that you no longer can heat or cool things. This how to video talks about how to protect your home from a long term power outage, or how to protect your valuables from power loss with a generator.

Once you've reached an age where sparklers are no longer fun, it's time to upgrade to science and steel wool. It may be basic chemistry, but as you'll see in the video, simplicity can amaze more than complexity, as well as create some really impressive fireworks that are perfect for the Fourth of July.

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

In order to clean your fish tank, you will need the following: a bucket, water conditioner, aquarium salt, a clean filter, a suction tube, and clean fresh water.

In Obstetrics and Gynecology (OB/GYN), doctors deal specifically with the female reproductive organs, which means a lot of visual inspection of the vaginal area. Whether you're a doctor, surgeon, nurse, or nursing assistant, knowing how to properly drape a patient is detrimental to the patient feeling protected and secure with the hospital staff, along with having some privacy. This video will cover different types of draping techniques.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

In recent years, Google's Arts & Culture project has been leading the way in terms of innovating the practice of using technology to preserve landmarks and great works of art via digital 3D copies. Increasingly, these efforts are also giving history buffs the chance to experience classic works and spaces with unparalleled intimacy through the wonders of augmented reality.