
How To: Delete history from Skype
Ho to remove your call log/history from Skype to protect your privacy.


Ho to remove your call log/history from Skype to protect your privacy.

How to crack the WEP encryption on a wireless (WiFi) network.

Now we'll learn how to secure PDFs so that we can safely send them out to clients for review and be assured that they can only access the content the way we want them to. Turn off things like printing and content extraction. Password protect your PDFs so that they can't even be opened without a password.
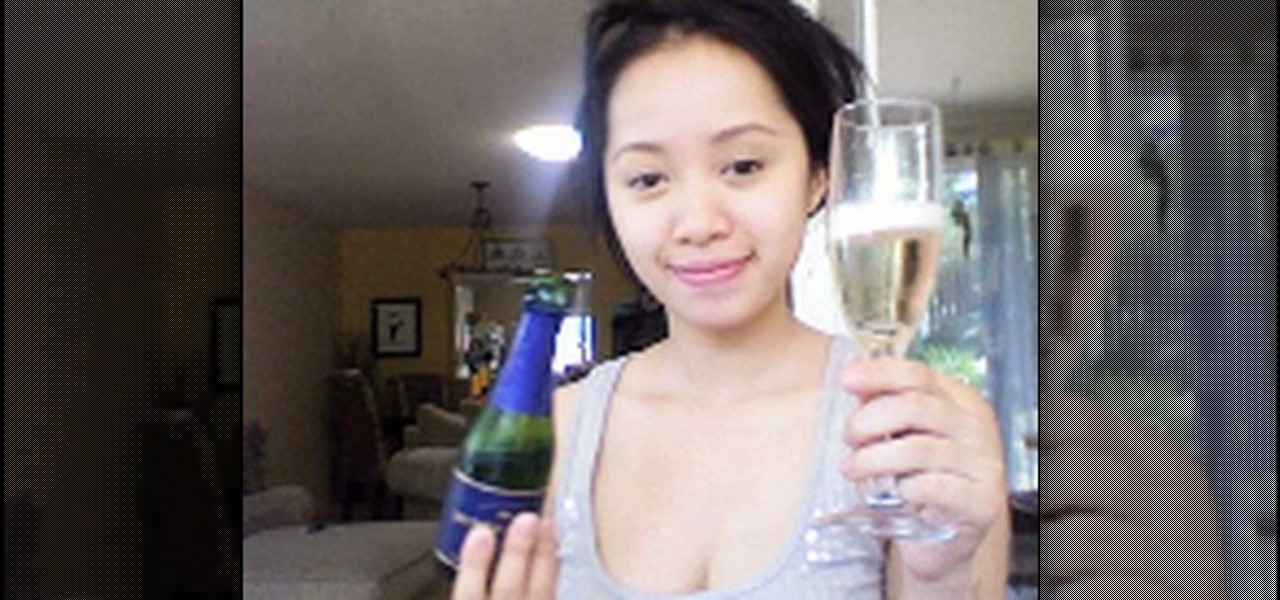
Michelle Phan presents this tutorial video on caring for your skin with champagne. You can use less than a sip of your champagne as a detoxifying cleanser/ toner.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

In the Xbox 360 game Darksiders, you're nearing the end of the game when you get to the Black Throne, which consists of three guardians and Straga. Proceed across the bridge as it constructs itself then enter the main room of the Black Throne. Here you will find Azrael who will tell you about Straga and how he gains great power from the Well of Souls. You will need to defeat the three Guardians that protect the Well of Souls and use their power to destroy the three statues that imprison Azrae...

Ten verses are in this level of the Xbox 360 game Bayonetta. In Chapter 9 - Paradiso - A Remembrance of Time, get ready to fight Golem. From the floating clock face you can jump to the yellow floating disk. Follow the path of floating objects to the floating courtyard garden.
If you're tired of the boring old ringtones on your iPhone but don't want to shell out extra dough to buy a new one, here's an easy way to make your own.

There's nothing more maddening than opening the office fridge and discovering your lunch is gone. Put an end to the stealing with some of these strategies. This video will show you how to deter coworkers from stealing your lunch.

Video chatting over the Internet is an inexpensive way to keep in touch with your family and friends. This video will show you how to set up web video chat.

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.
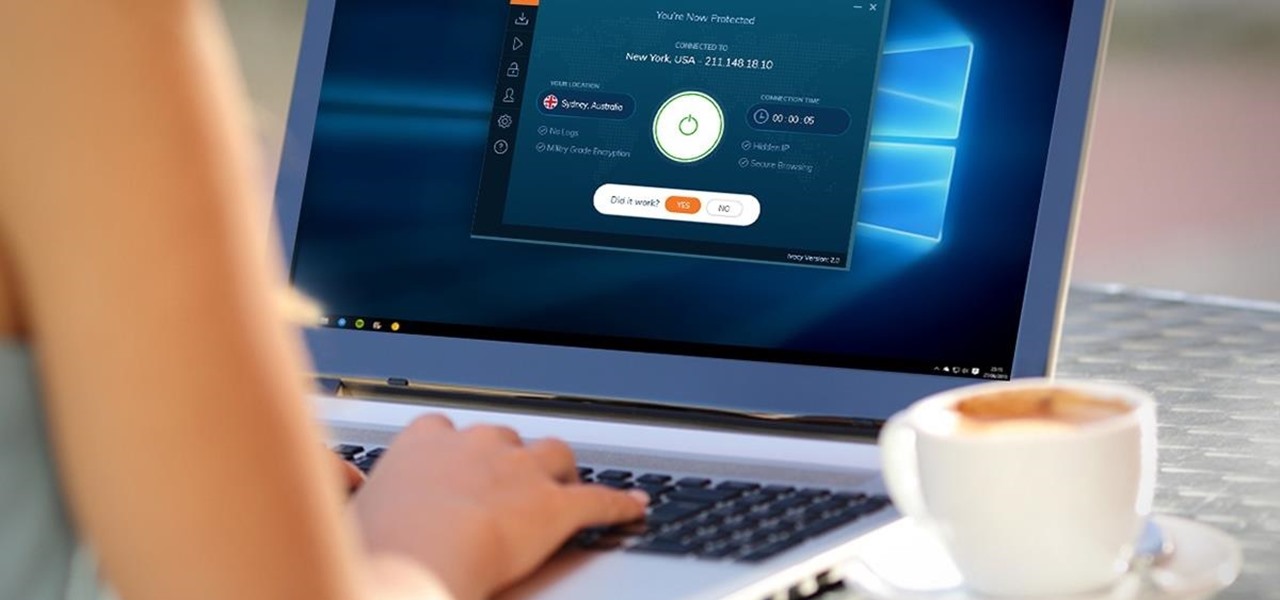
Your privacy is important, especially online. Almost anywhere you go on the internet, you leave a trail of data that companies can use without your permission. VPNs are the easiest way to keep your browsing private and your information safe. Ivacy VPN is one such service, and it's one of the best deals you can get on a VPN because it will cover 5 of your devices for a lifetime, and this is a two-account bundle, so you'll be able to cover 10 total devices for $49.99.

Among the various components of the emerging augmented reality space, the most lucrative is the advertising market. The prospect of turning every object, every location, ever signpost in the real world into a discount code or virtual transaction interface is why AR will ultimately be more profitable than VR.
Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

It is a scary time to be alive. As states start to ease back shelter-in-place restrictions, the new world you're entering is still unsafe. With a vaccine months away, your best bet is to follow CDC guidelines and use the tools at your disposal.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.
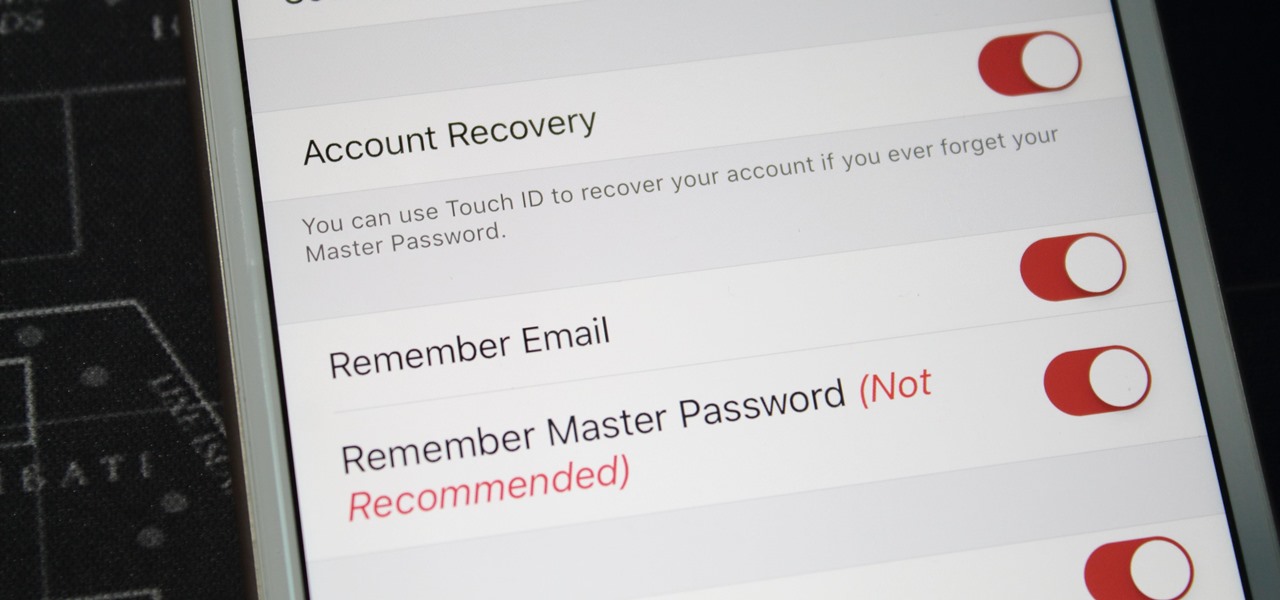
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.
When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

At one point, UltraViolet was the go-to way to maintain a collection of digital movies. Fast-forward to 2019, and things are different. The service is shutting down on July 31, largely due to the massive competition in the digital movie marketplace. If you're an UltraViolet user, don't worry too much, because you can save your movie library — as long as you act before UltraViolet closes its doors.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

The day has finally arrived — Samsung has unveiled the Galaxy S9 and S9+. Apart from minor upgrades, the two might not appear to be much different from last year's S8 and S8+, but that's not necessarily a bad thing. One feature that hasn't changed is the Galaxy's IP68 water-resistance rating. That's a great score, but it begs the question — what does that number really mean?

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can become contaminated too.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Even though HIV rates declined 18% between 2008 and 2014, 1.1 million people in the US are living with the infection. Part of that is because HIV is treatable, but not curable.
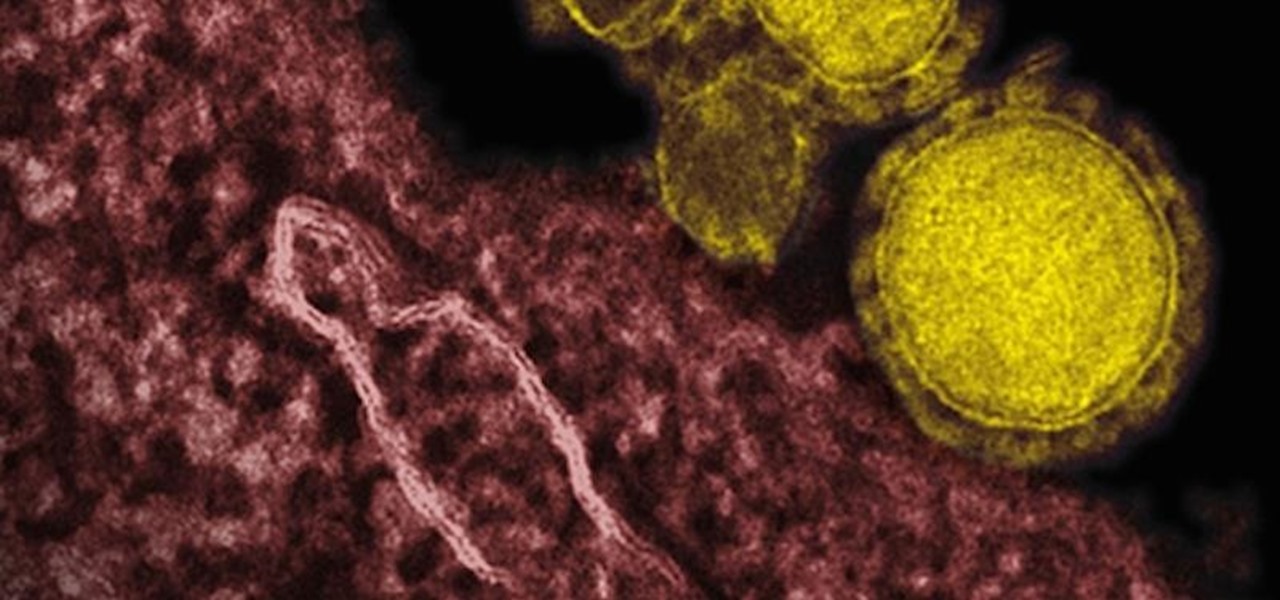
Coronaviruses are common viruses, and most of us catch one at some point — they cause about 30% of all common colds. A new accidental discovery could help fight these viruses, even the deadlier, emerging ones.

It's not always easy to get to the root of an infection outbreak. Epidemiologists study infected people, contacts, and carefully examine where the infections happened and when. In the case of a 2012 outbreak of pertussis — whooping cough — in Oregon, scientists just published an analysis of how vaccination status affected when a child became infected during the outbreak.

When you're taking a video in the Camera app on your iPhone, there's a little white shutter button in the corner that lets you take a still image while you're filming. Apple brought that same concept over to the FaceTime app in iOS 11, iOS 12, and higher, so you can take Live Photos of your friends during video chats.

Long admired for their active and cooperative community behavior, some types of ants also wear a gardening hat. Nurturing underground fungus gardens, these ants have a win-win relationship that provides food for both ants and fungi. If we humans understand it better, it may just help us out, too.

In the worst measles outbreak in the state since 1990, the Minneapolis Department of Heath races to contain the spread of an infection believed to have originated from an infected traveler. Mistaken attitudes and unvaccinated travelers are creating a world of hurt and disease for Americans. A recent study found that more than half of eligible travelers from the US are electing to skip their pre-trip measles vaccine.