As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

One option you won't find buried in the Galaxy Note 9's Settings is the ability to return the navigation bar to black. Samsung changed the default color to white with the Note 8, removing any ability to bring the black color back. But thanks to a neat app, Note 9 users can do it themselves.

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

In recent days, I've twice talked about brining the Magic Leap One out into the world with me to test its mobile capabilities. But you may have been wondering how I carried the device with me. Did I just stuff my brand new $2,300, hard to obtain device in a backpack and hit the road? Hardly.
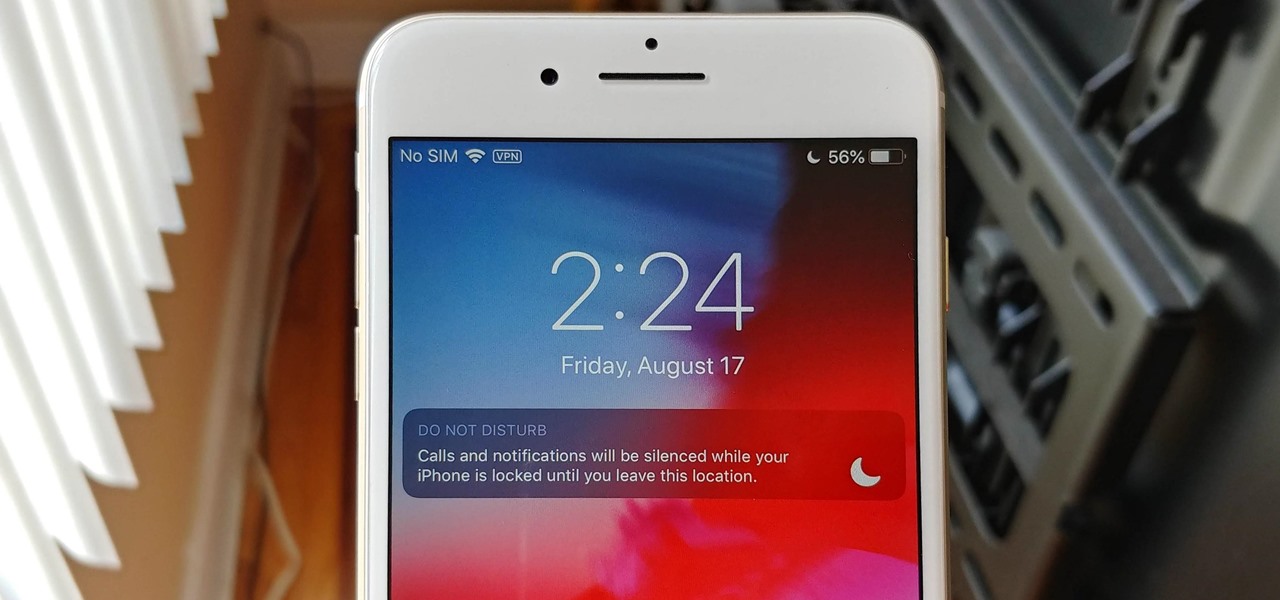
One of the new iOS 12 features for iPhones is an enhanced version of Do Not Disturb mode. Instead of being limited to times you manually input, Apple added new ways to manage the feature, including activating it based on location. For those on the go, this can be done pretty quickly.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

In the tech world, upgrades are normally a good thing. On iOS, it means bug fixes and security patches that protect your iPhone and keep it up with the times. In the jailbreak world, however, upgrades can mean certain death, as we are reminded today when Apple stopped signing iOS 11.4. That means if you upgrade to 11.4.1, you will no longer be able to jailbreak your iPhone.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

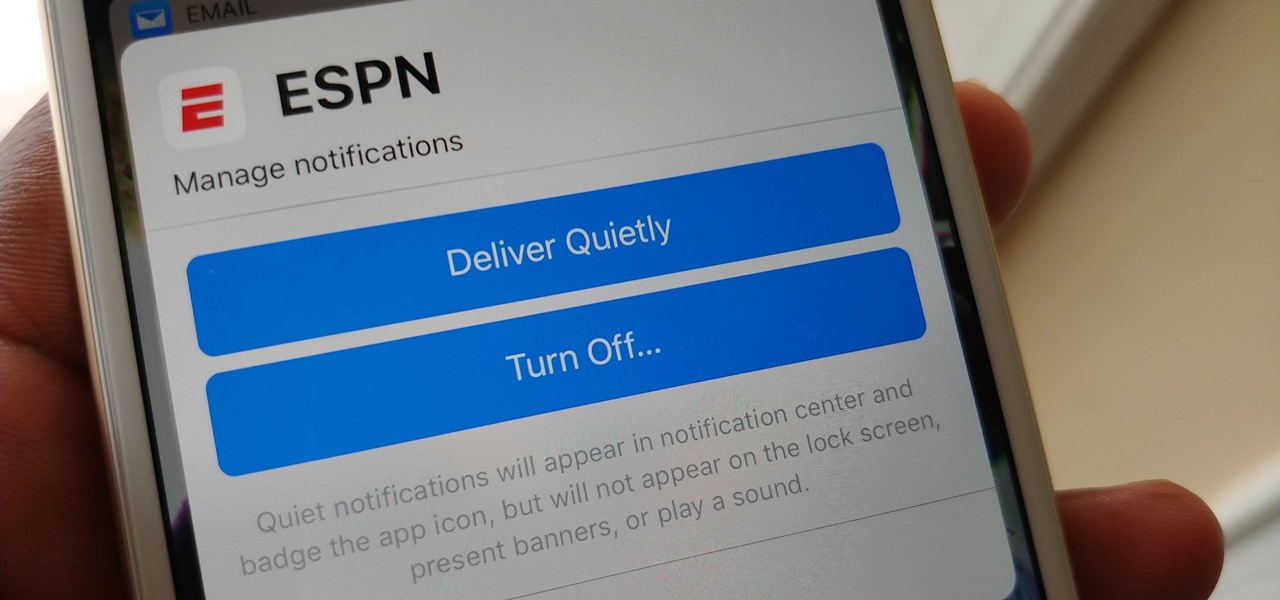
Apple's notification system for iOS was in desperate need of a revision ever since they removed app grouping for new alerts. In iOS 12, they finally brought that back, new and improved, but Apple has also added more useful notifications features, such as Instant Tuning, which helps you quickly manage how notifications come in for each app — if you even want them to.

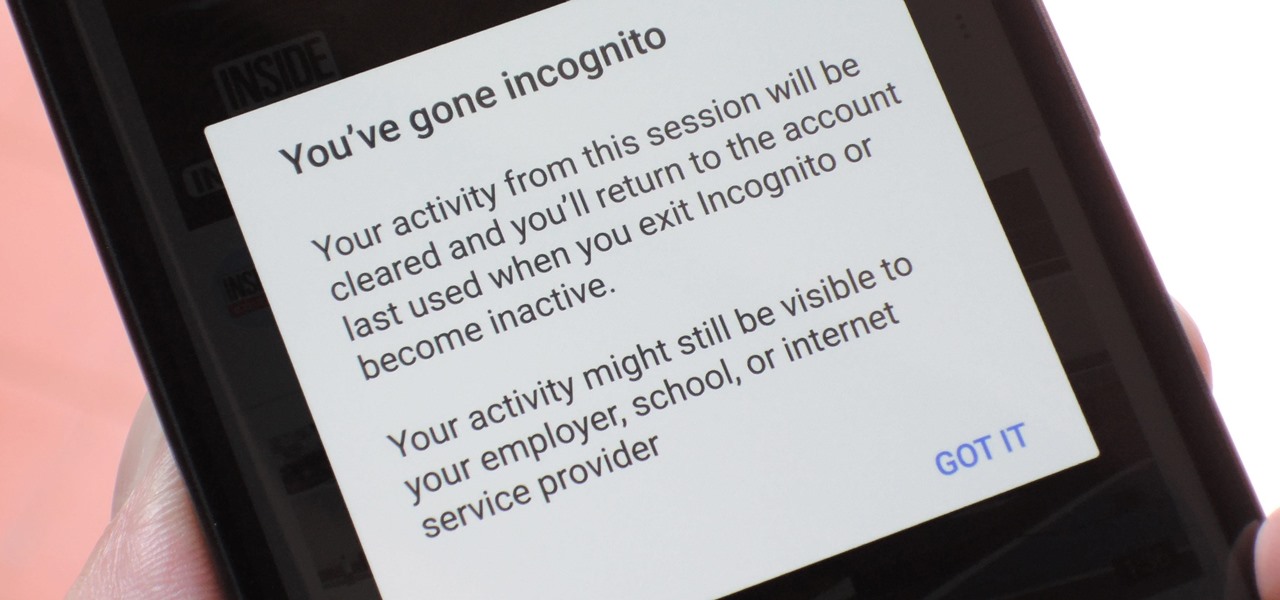
Incognito Mode is a privacy feature that was popularized by Google Chrome, and it recently made its way to GBoard. Now it's coming to the YouTube app to help make your video watching experience truly private.

On Thursday, waveguide maker WaveOptics announced that semiconductor and microelectromechanical systems supplier EV Group (EVG) will provide the manufacturing infrastructure for the production of its waveguide displays designed to support lower-cost, third-party augmented reality wearables.

Patent holder Genedics, LLC has filed a legal complaint alleging that hand-tracking startup Leap Motion is infringing on its intellectual property.

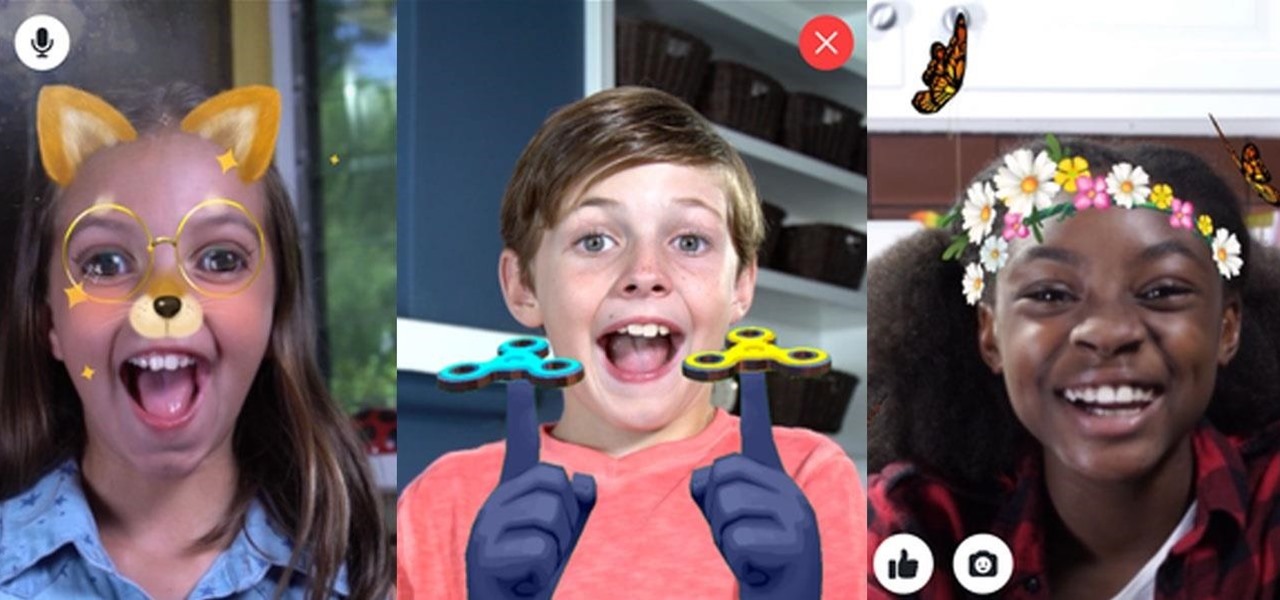
Next to millennials, one of the groups most coveted by brand marketers is "Generation Z," the consumers of tomorrow who were born between 1996 and 2010. On Monday, Facebook established a beachhead with that demographic in the realm of augmented reality by launching Facebook Messenger Kids.

Most of the free apps you'll find on the Play Store have ads. These ads are personalized — in other words, they're for products and services Google believes you might be interested in. The way Google knows about your interests is by collecting data from your smartphone, including your location and app usage. While personalized ads have their advantages, the collection of data is unsettling.

If you live in New York City and are itching to sell your Yeezys, you're at risk of falling victim to thieves. A devious duo is searching Facebook to find people selling the popular sneakers and then robbing them at gunpoint when they meet up in person.

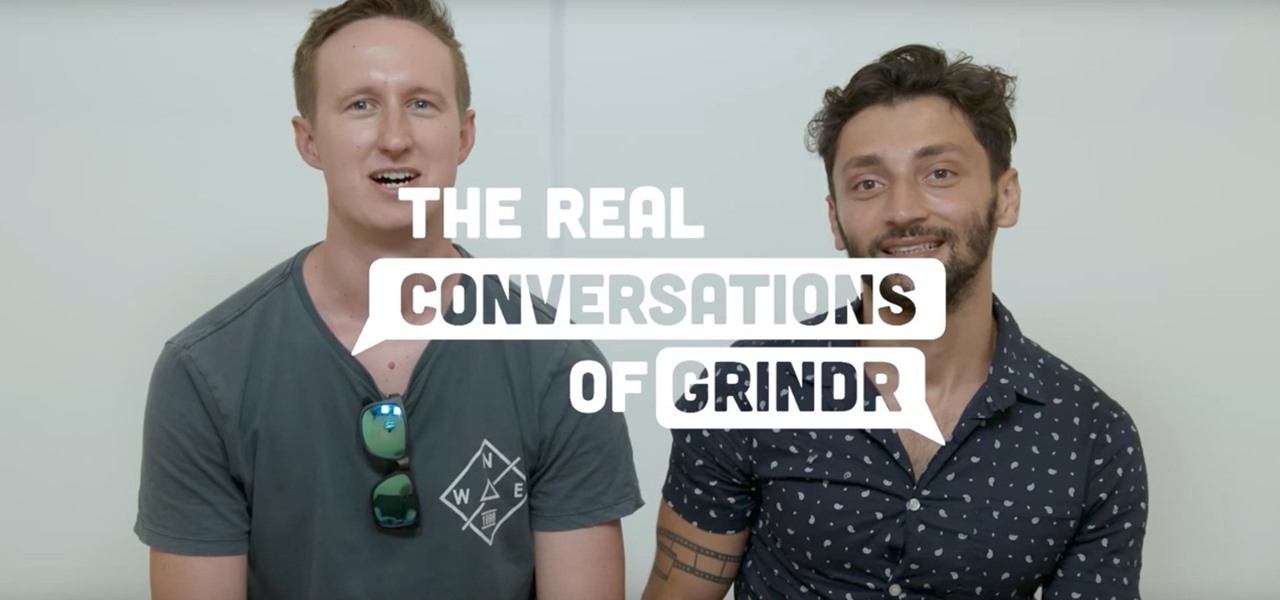
With significant advancements in the treatment and prevention of HIV, you'd think the stigma surrounding the deadly virus and AIDS, the syndrome the infection causes in the body, would have lessened. Unfortunately, a new project looking at conversations on Grindr — a social networking app for gay, bi, curious, and queer men — has shown that this stigma is very much present.

With the hype surrounding the iPhone 8, Apple's announcement that it's developing driverless software, and the new iOS 11 beta out, it seems like the tech giant is constantly in the news. Today, Apple's continuing this streak with updates for its iWork app suite on iOS and macOS.

After SquareTrade tested out the Samsung Galaxy S8 and found it to be the first phone to shatter on all sides after only one drop, it's nice to know we may have a solution for this $500 problem.

Firefox Focus has been out for iOS for a while now, so it's about time Mozilla began porting the app over to Android. It's an amazingly private browser that protects you from trackers and ads when you're surfing the web. It blocks a wide range of online trackers, erases your browsing history, hides passwords, and deletes cookies. This essentially means ads won't be able to follow you around, in the sense that you won't see ads related to your last ten searches on Google.

The May 2017 security update has begun rolling out to Nexus and Pixel devices, which is usually great news. It means that your device is now being updated to protect you from the latest exploits and vulnerabilities found in Android. At other times, though, security updates patch root methods like Dirty COW, which is extremely frustrating for users and developers alike. Especially since most OEMs don't condone rooting or even unlocking the bootloader on their devices.

Google's Allo is still a work in progress, but the innovations to the chat and messaging app just keep on coming. The latest update rolling out now includes chat backups and a group incognito feature that we're very excited about.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

A baby with severe Zika-related birth defects was born in San Diego County this week, prompting officials to urge pregnant women to avoid disease hotspots.

Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested their method on a Samsung Galaxy S6 and Huawei Honor 7.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.