Let's face it — our phones are our heart and soul. We do everything on them, from banking to media consumption. However, sometimes we download apps that we don't want others to see. Sometimes, we wish to hide apps so that, in the rare times we lend our phone to someone, we don't get judged for a lifetime by what they find.
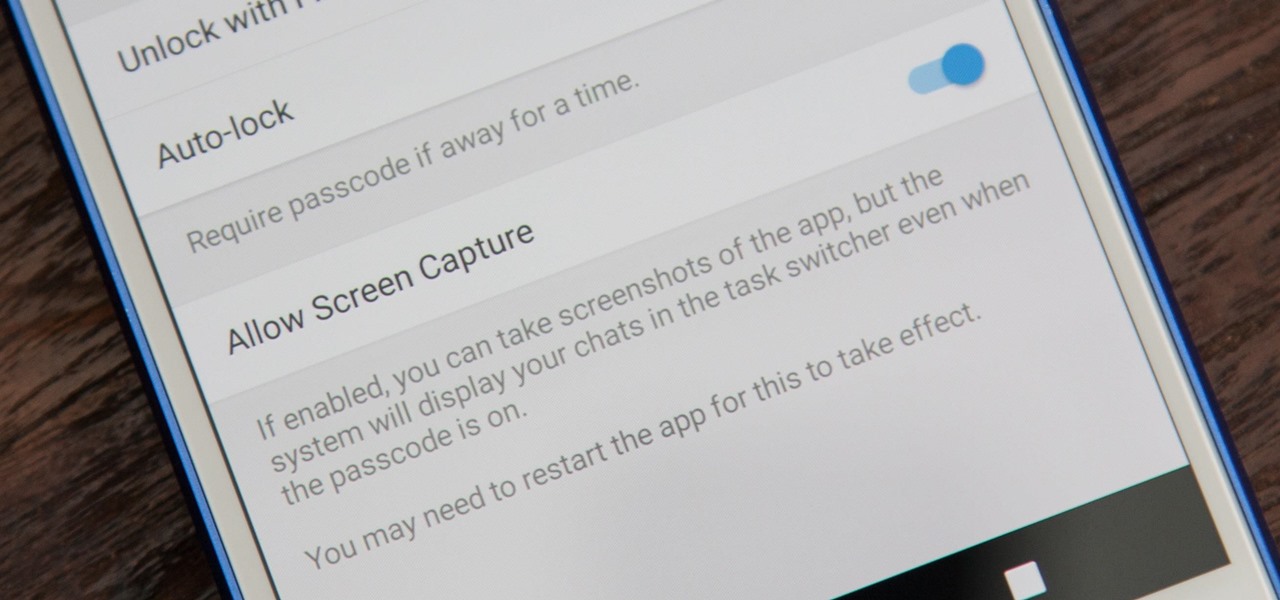
While it's easy enough to take a screenshot of an end-to-end encrypted Telegram chat thread using an iPhone, it's an entirely different story on Android phones. Telegram disables screenshots for Secret Chats by default on Android, and not everyone can turn it on.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.
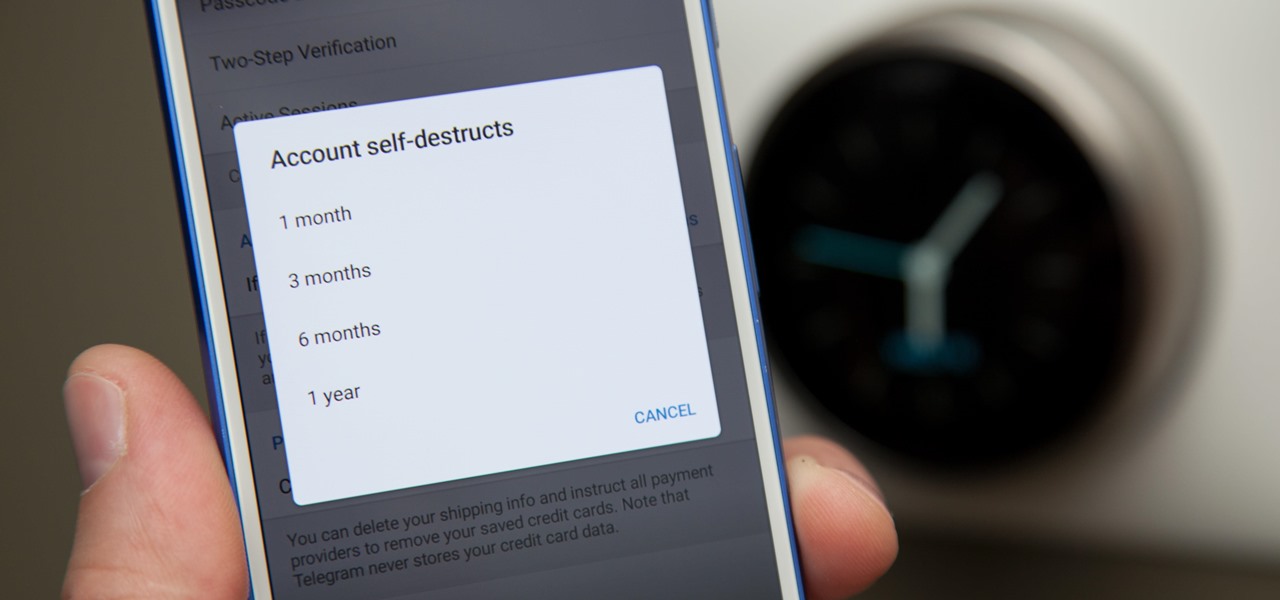
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.

While using end-to-end encryption may be enough security for most of your messages in Telegram, you can go a step beyond this by sending messages that disappear after an allotted amount of time. This prevents you from having to manually delete the message at a later time, so you can send it and forget it without worrying about whether or not it's still out there.
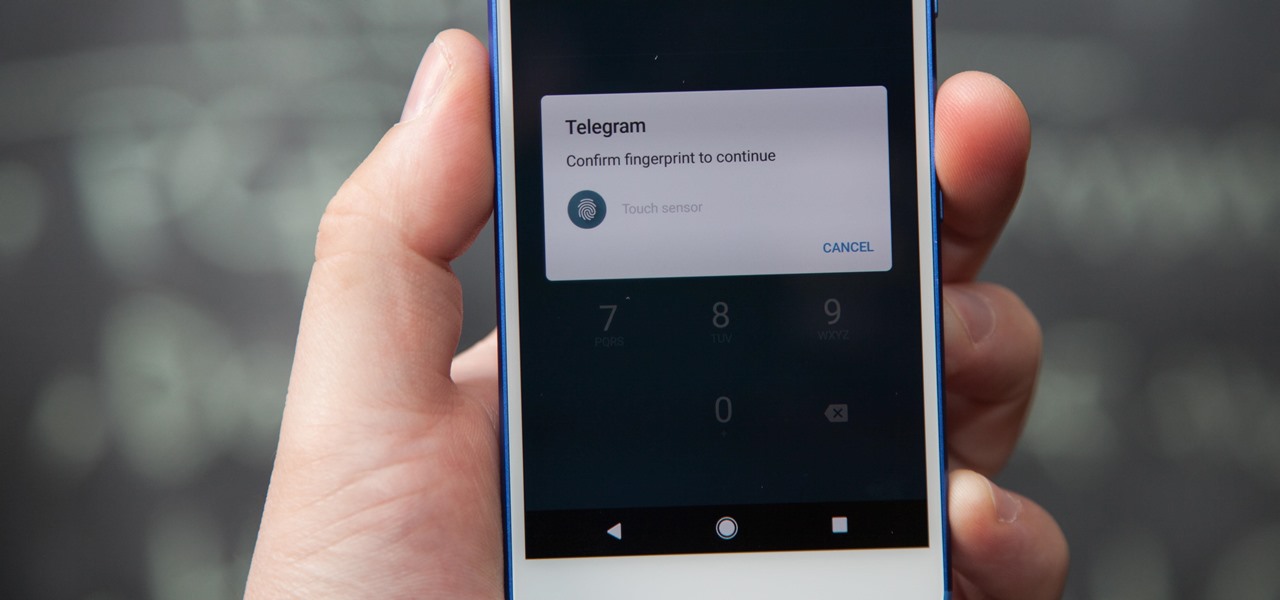
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

An update to the iFramed social media gateway app for iOS adds an augmented reality feature called JuxImage that gives its users Snapchat-like photo and video effects.

Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

This may not matter to you if you only FaceTime from your iPhone occasionally, but if you're FaceTiming every day on a limited data plan from your cellular provider, you're going to want to conserve as much data as possible by making sure that you're connected to Wi-Fi only — especially if they are video calls.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

Despite packing some really nice camera specs, the OnePlus 3 and 3T don't take the best pictures. That's because, these days, great software is just as important as great hardware when it comes to image quality.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

After a brief reprieve, Zika fear is back with a vengeance as the US mosquito population booms. And we're just now seeing the true impact of this devastating virus, as babies of mothers infected with the virus are being born.

Officials in Colorado are concerned as 61 cases of the mumps were reported so far this year, a significant increase in the prevalence of the contagious disease in the state.

Google and eight top Android partners have just signed the Android Networked Cross-License, nicknamed PAX. On the surface, this looks to be a peace treaty of sorts that could end several patent wars.

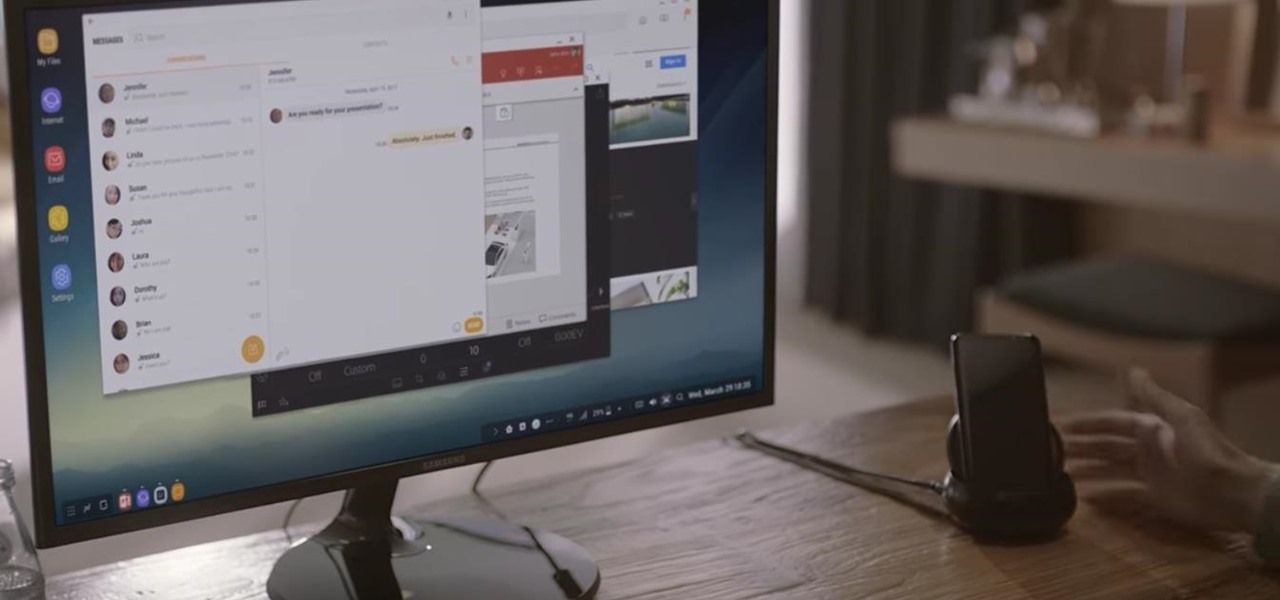
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

There have been mumps outbreaks in three different US colleges so far this year as instances of the illness are on the rise, according to the Centers for Disease Control and Prevention (CDC).

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

Most people know atopic dermatitis by its common name, eczema—that dry, flaky skin that itches incessantly. Along with the scratching comes frequent skin infections, often with Staphylococcus aureus.

Most of us equate feeling cold with catching a virus—but we've also heard plenty of debunkers proselytizing that being cold isn't what gives you the flu.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

The Google Chrome browser for Android is packed with many great features, but it definitely has a bad rep for being slow and laggy on low-end or midrange devices. Without a top-notch processor, you'll likely notice some stutter with choppy scrolling, and pages can take too long to load in general.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

When we talk about augmenting our reality, we often first think about vision instead of our other senses—but there's more to an immersive experience than what you see. One inventor figured out how to utilize sound and touch to create a simple, upgraded version of laser tag that you can play with your smartphone.

When Apple announced its new iPhone 7 and iPhone 7 Plus models in San Francisco, one of the biggest new features was an "IP67" water-resistance rating. Couple that with a few official renderings that show the new iPhone covered in water, and you'd probably arrive at one logical conclusion: The iPhone 7 is waterproof.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Today's pollution, hectic lifestyle, inadequate sleep and no time for pampering can leave your skin lackluster resulting in drying skin and making dry skin drier ultimately causing the early appearance of wrinkles and aging. A good fruit facial helps relax your skin from deep inside and the proper messaging gives it a rosy glow by increasing blood circulation imparting your face with a luminous glow. These are even better because they are natural and chemical free unlike the artificial facial...

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

One of the best qualities about fresh bread (such as sourdough) is a thick, crispy crust—which is easy to create in a commercial oven, but can be tricky for home cooks to replicate. Luckily, the the trick to baking a professional-style crust is a simple one—just bake your loaf with steam using one of these three methods to achieve the perfect, crispy crust.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.