SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

This Guy Has My MacBook is a gripping tale for iOS nerds far and wide, documented via interaction designer Joshua Kaufman's tumblr. When Kaufman's MacBook was stolen from his apartment in Oakland, CA, on March 21, 2011, he quickly activated Hidden, a previously installed app that enabled Kaufman to collect photos of the thief, as well as screen shots of the computer in use.

It's not uncommon for nature to inspire technology and innovative products. Airplanes were inspired by birds, Velcro by burrs and dog fur, bullet trains by owls and kingfishers, and gecko tape by... well, you can probably figure that one out. And one of the deadliest fish ever to swim the oceans has also influenced its share of merchandise; Sharks made humans faster in the water with Fastswim Suits, and now they've helped make one of the most rugged smartphone cases in the world—SharkEye's Ru...

Child Safety Window Treatments

Designer Andrew Clifford Capener has made an alternative to the classic Scrabble board that celebrates the expression of typeface. It isn't in production yet, but Capener's set would offer tiles in a variety of different fonts:

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

Looptaggr is an ingenious drive-by tagging device by Ariel Schlesinger and Aram Bartholl. It's cheap, quick and easy to make, and even speedier to use. Cities and small towns across the world may be littered with graffiti mayhem in no time at all... From Looptaggr, how to make your own:

How can a small curtain cover a window three to four times its own size? With a motor and a robot brain, that's how!

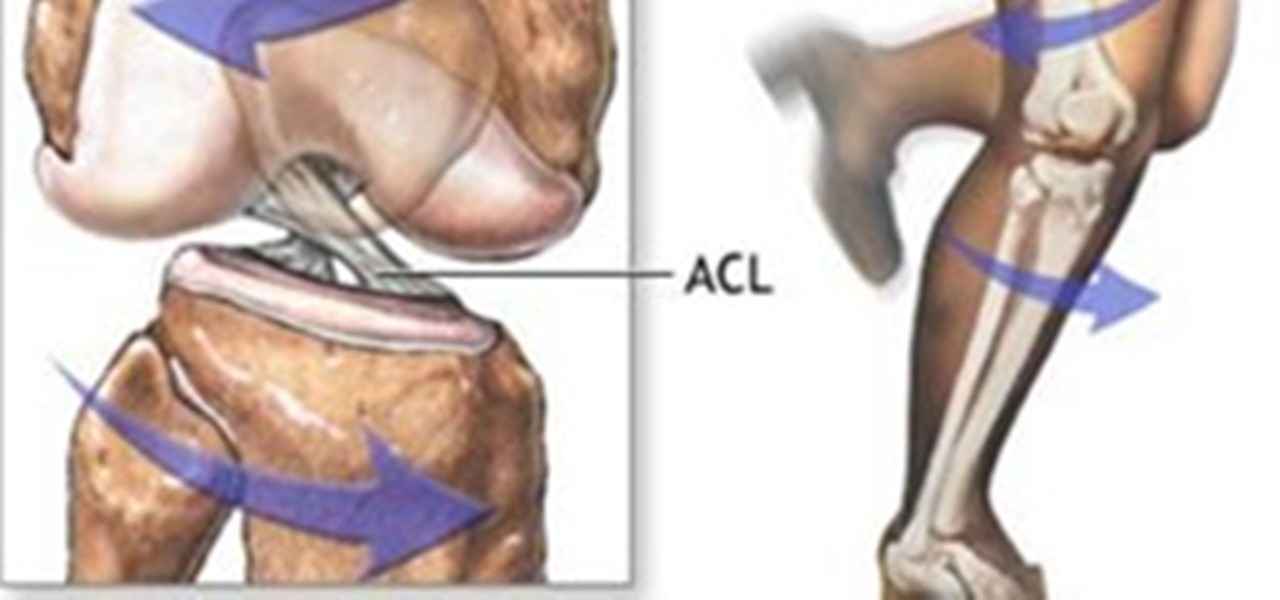
The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who

The sudden deceleration, shifting in the knee, popping sound and screaming from the intense pain that immediately follows is becoming increasingly common among our young athletes. Those who have witnessed or suffered a torn anterior cruciate ligament (ACL) are familiar with the pain, surgery and intense 6 to 8 month rehabilitation that accompanies the injury, not to mention the disappointment of ending a season. Nationwide, this will occur more than 500,000 times this year, and female athlete...

The one arm dumbbell chest press is perfect for strengthening the pectoralis (chest) muscles. Most chest exercises involve compound movements, or the use of more than one joint. Invariably, the triceps and anterior deltoid are often involved in chest exercises.

The step-up is a great exercise for the muscles of the upper leg. It effectively works the thighs, hips, and butt. The calf muscles work as synergists during the step-up exercise. They assist with balance. The step-up exercise can either be done one leg at a time or alternating between legs.

As useful as VPNs are for securing your browsing experience and bypassing frustrating barriers online, it's hard to find the right one among the horde of choices. VPN.asia: 10-Year Subscription is a great choice for a VPN that keeps your browsing safe and smooth, and right now, it's only $79.99.

Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity.

Data restrictions suck, but Google wants to make it suck just a little less. Rolling out is the latest update to their mobile Chrome browser, Chrome 32.

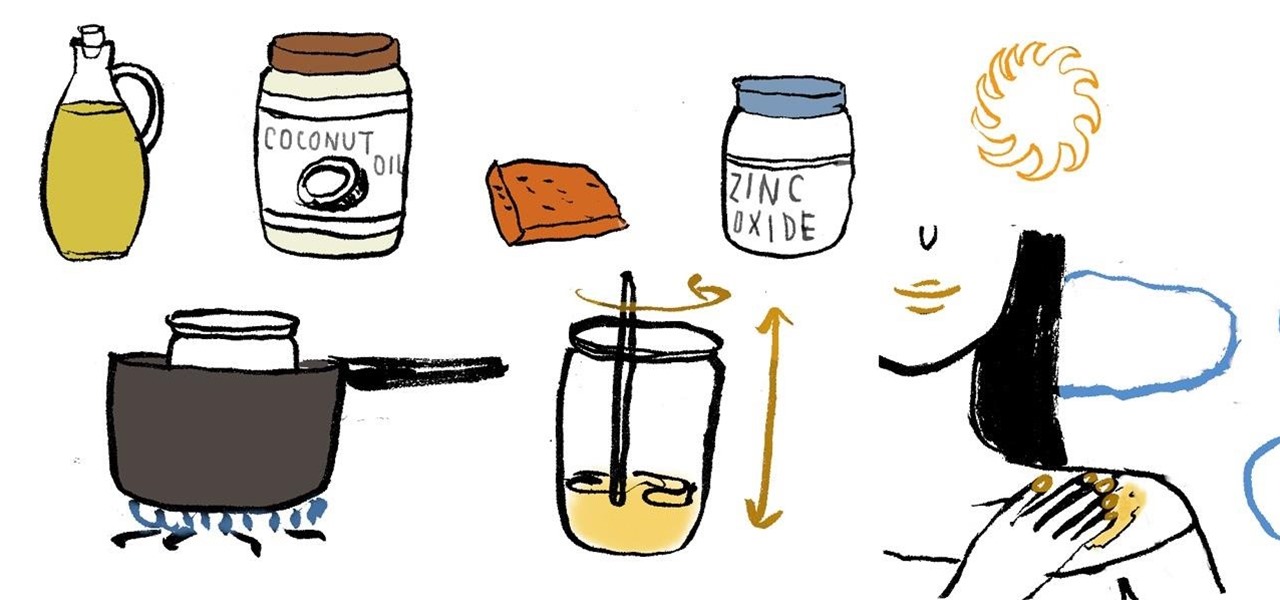
Getting sunburned sucks, and according to the Environmental Working Group's 2012 survey of over 800 sunscreen brands, 75% of them contained potentially harmful ingredients linked to hormone disruption and even cell damage that may lead you to skin cancer. Yikes.

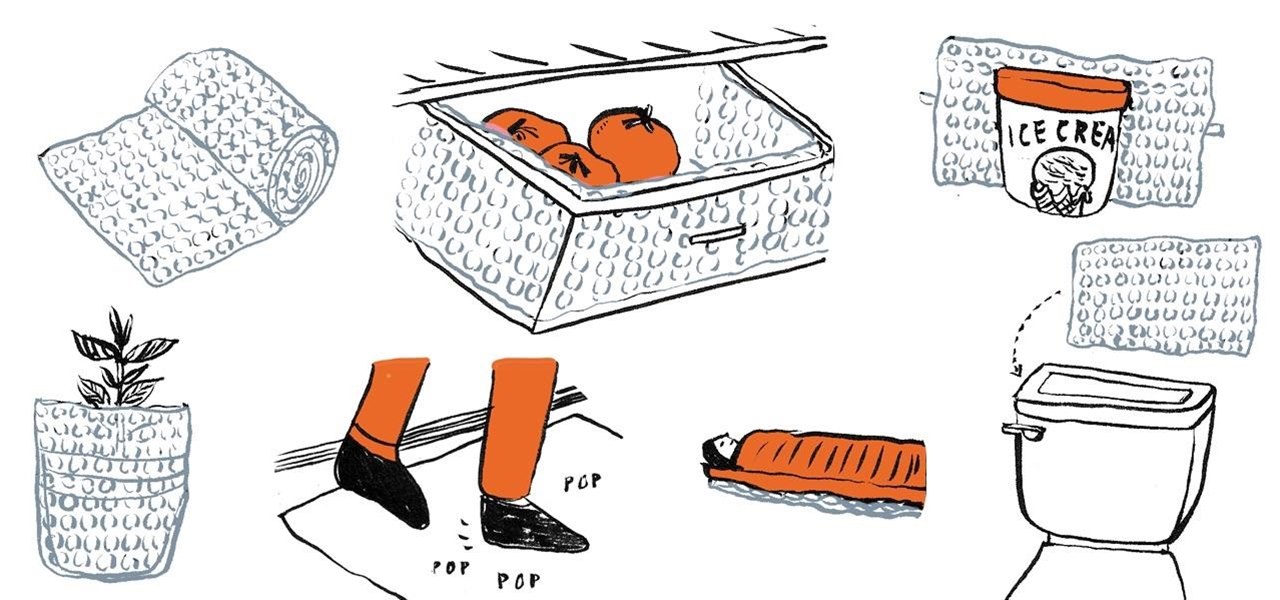
If you're like me, you have a secret dream of living in a house completely covered wall-to-wall and carpet-to-carpet in bubble wrap. Until you have enough of that pliable transparent plastic with air-filled bubbles, there are some truly practical things you can do with the little you do have—besides packing fragile objects.

Windows has its own built-in antivirus program called Windows Defender, which kinda sounds like a sweet arcade game, but it actually does a pretty good job of protecting your Windows PC from spyware and malware.

Turning unused items into usable pieces of furniture is a great way to save money and create some really good-looking pieces for your room. And nothing beats repurposing old wooden pallets. Redditor BaconStripsandFishin used old wooden pallets and a month's worth of coffee to create his own unique coffee table. To make this, unscrewed all of the wooden panels (top and bottom), placed them all together, and then screwed them back in reusing those same nails. Once he had all of the board togeth...

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

Microsoft just revealed the preview of its latest incarnation of Webmail, Outlook.com. One particular Outlook.com feature worth noting, is its support of multiple e-mail aliases. They're a great way to protect your primary e-mail address. And because you can't log in to your Outlook.com account with an alias, it adds another level of security. How To Add an alias

We all know the dangers of logging on to our personal accounts on public networks, but we pretty much all do it anyway—especially when it comes to Facebook. But the next time you're in a public place and can't wait to check out your Facebook news feed, use this simple trick to make sure that no one gets a hold of your password. In order for this to work, your mobile phone needs to be linked to your Facebook account. All you have to do is text "otp" (for one time password) to the number 32665.

Incredible. A company called Berry Plastics (in partnership with the U.S. Army Corps of Engineers) has developed a working bomb proof wallpaper. The technology has the ability to protect against both natural disasters and warfare.

Henna. Beautiful, fun, exotic... and best of all... Do-It-Yourself (with a little practice). Also, unlike tattoos, it's temporary. Henna generally lasts for 1-3 weeks. An ancient tradition, henna is believed to "bring love and good fortune, and to protect against evil."

Need to find some directions? No problem, use Google Maps. Want to find some spy photos of yourself? No problem, use Google Street View.

Michael Faraday was an English chemist and physicist - a bona fide electromagnetism and electrochemistry genius. Without him, men couldn't walk on live electrical wires. Wait, what?

If you ever wondered how to keep your car looking great and protect the paint for years to come, read on.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

Once you get past the initial quick start setup of the Canon EOS 5D Mark II, capturing pictures in auto mode is a breeze. But what do you do after you've snapped those photos? This quick guide will show you the easy steps to viewing your images directly on the camera.

There’s no point to playing all of the different tower defense games available today. Most adhere to the original formula, so playing 2 or 3 really good ones (like those mentioned in my previous post) would be more efficient.

Roses, the world’s favorite flowers, are great garden performers that, if well cared for, will live for many years and produce thousands of exquisite blooms.

Warfare strategies have become an inspiration to different marketing professionals, many of them drawing influence from Sun Tzu’s Art of War. This ancient Chinese text provided treaties on how to effectively manage resources, tactical positioning, and timing attacks. It also states that “..if you know your enemies and know yourself, you can win a hundred battles without a single loss”, a basic concept in which you have to always watch your competitor to anticipate his next move.

Want to be able to print wirelessly without having to buy a pricey network printer? Now you can! All you need to do is follow these simple, quick, steps.

Christmas is almost over— all of the presents are unwrapped, all of the prime ribs have been eaten, the whole family's drunk off eggnog— and soon it will be time to forget about Christmas until next year.

If you love action and adventure then you've come to the right place. Get ready for a red-hot science explosion as the A-TV science superstars show you how to make your very own erupting volcano!

A Self-Protection Guide 1) You can help protect yourself from violent crimes.

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.