This video will teach you how to properly use the sleeper hold in order to subdue an attacker, but not damage their larynx. This is a real way to protect others and yourself. It is meant to help Police Officers from choking people and avoid law suits from performing the wrong maneuver.

In this video Bob Schmidt shows you how to cut PVC plumbing using a unique method to protect adjacent areas in your home.

Protect yourself from Lyme disease without exposing yourself to a lot of pesticides. This how-to video will show you how you can get rid of those ticks before they even bite you.

West Nile virus is rare but can be deadly. To avoid getting it, you’ve got to avoid mosquito bites.

Learn how you can protect your home in a pretty radical and fun way by transforming two cheap household items into a stealth hi-tech, anti-burglar, security system! Literally to hot for any bad guy to handle!

How many women have heard "You can't do that here!" when trying to nurse in a public place? Parents TV's Anne Ebeling explores the issue of public breastfeeding from etiquette to laws that protect nursing mothers.

Even though I am not the best locksmith in the world, the four-digit #175 model Master Lock is so easy to pick that all the hardened steel in the world isn't going to protect your belongings.

If your home is not protected by impact-resistant windows and doors, or impact resistant shutters or panels, consider building your own temporary emergency panels. www.flash.org

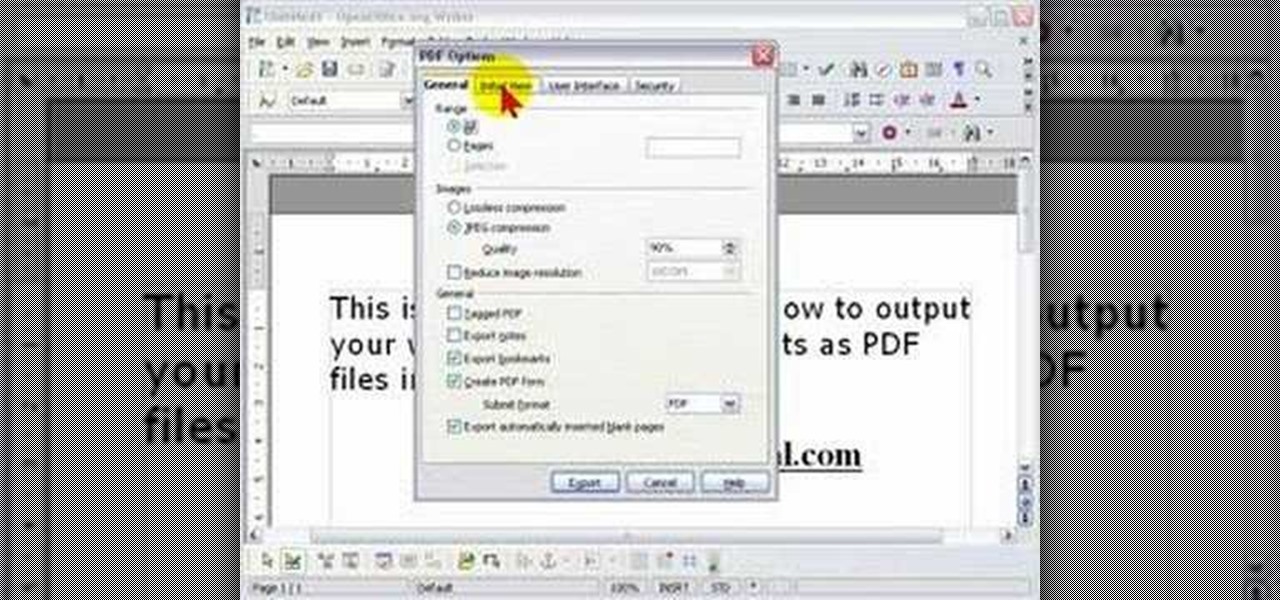
In order to protect your word processed documents, it is a good idea to export them for distribution as PDF files, which allows you to encrypt, and add password protection to your work.

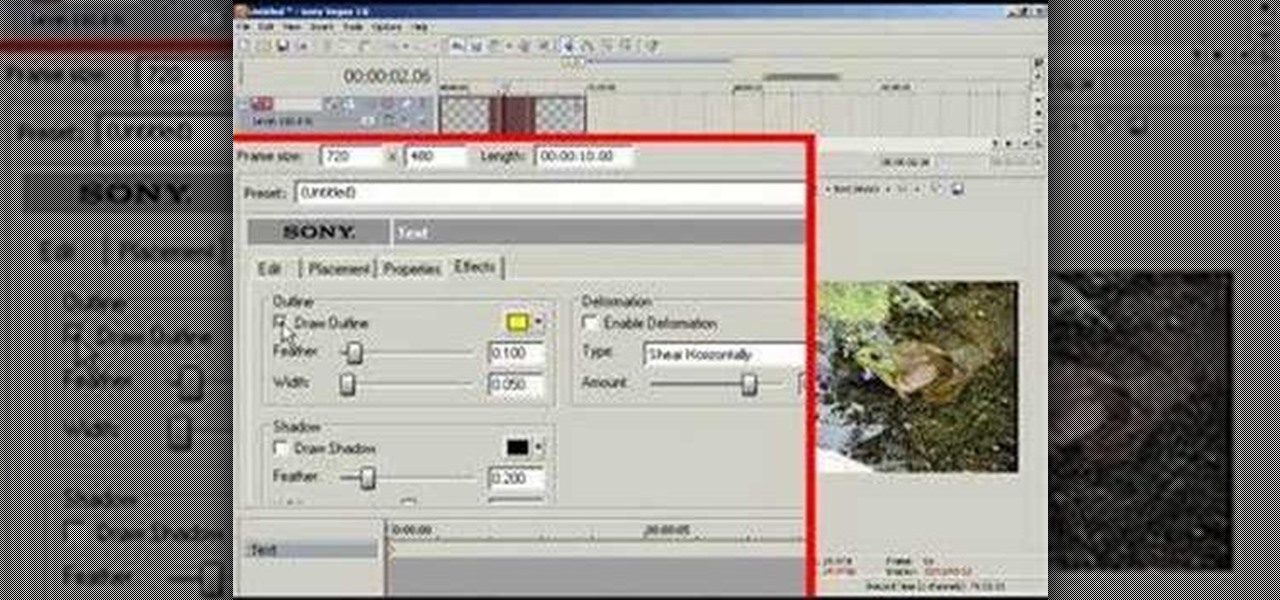
There are many uses to adding translucent text to your videos. None more important than that of ownership. Protecting your videos may or may not be important to you but since videos from YouTube can now be downloaded and converted in a matter of minutes, you may want to start watermarking your videos.

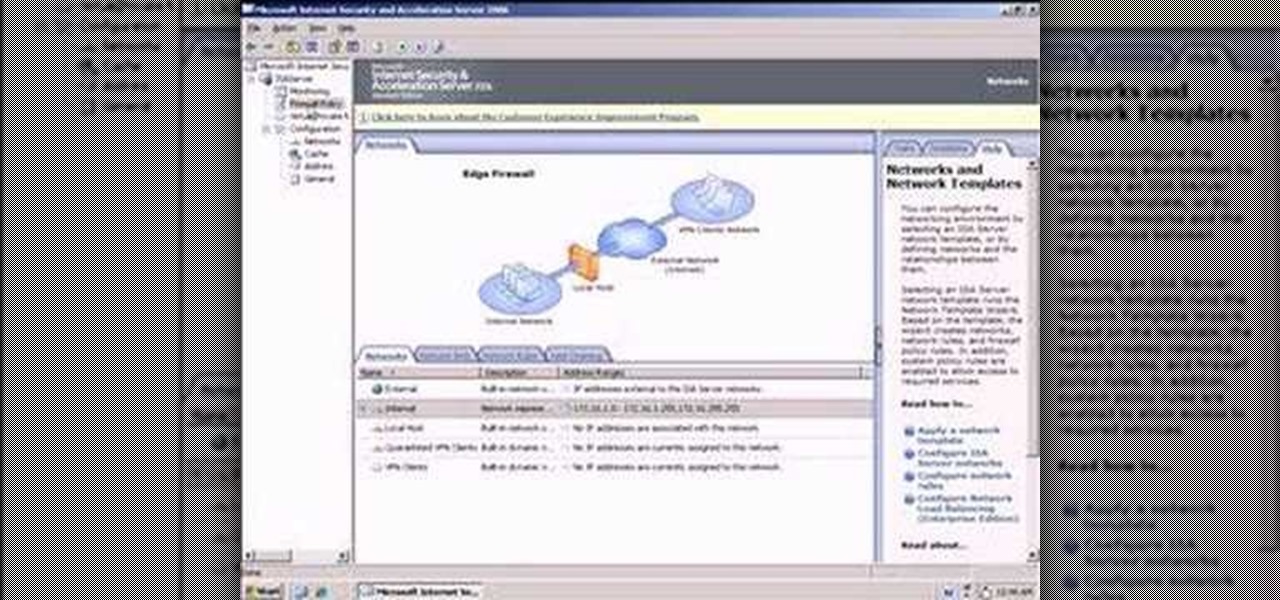
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

If you want to pull a small trailer with the Chevy Aveo, you are going to need some wiring for the trailer lights. This video will demonstrate how easy it is to connect a modulite circuit protected wiring harness. Now, even though you don't have a truck, you can run to the hardware store to pick up supplies and it will be safe, convenient, and legal.

Learn how to plant tulip bulbs correctly and protect them from critters. A garden expert gives detailed instructions.

Learn how to develop good pass blocking to protect your quarterback when playing football.

When you're ready to remove the pistons, start with the rod caps. You'll also get to see the crankshaft, rod bearings and journals for the first time and inspect them for damage as they come out. Great tips on protecting the cylinder bore while removing the pistons and connecting rods.

This video helps you to protect your computer against viruses and spyware often contracted when using peer to peer (p2p) networks like limewire, kazaa and emule.

To save energy, protect your garden, and keep warm during the winter follow these simple tips to winterize your home.

Reviews of products used to protect your home, family, and other pets. Also, we'll have a look at the legal side of pet damage in a rental property and how to prevent it.

Protect the kids from playground falls and mulch the plants at the same time! Landscape designer Michael Glassman spins his wheels finding inventive ways to use recycled rubber tires in the backyard.

This may sound like a terrible thing to show you how to do, but the Neistat Brothers are simply victims of bicycle theft who got fed up. They use their own bikes to show you how to steal a bike in NYC (in broad daylight) so hopefully you can learn from them, how to better protect your ride.

Protecting a new or young tree by staking it enables it to grow the strong root system it needs to secure itself in the ground. We will showyou how to stake a tree.

This video tutorial belongs to the software category which is going to show you how to convert a Word document to a password protected PDF file with NovaPDF. Go to NovaPDF and download the program and install it. It is a paid program. Select the word document that you want to convert and select print option. Under the name of the printer you will find novaPDF option. Select this and click 'preferences'. Now click on 'security' and select high level encryption. In the document permissions, sel...

If you're serious about keeping your diary for your eyes only then you might have to take some drastic steps. There are some very clever ways to distract from, encrypt, hide, or disguise a diary if you're willing to put in the work.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

The mainstreaming of augmented reality won't happen overnight, but it's becoming increasingly clear that traditional media is leading the charge in the effort to introduce the public to immersive computing. A recent example came from none other than USA Today via its 321 Launch app.

Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

Before The New York Times brought augmented reality to its iPhone app, the only way Winter Olympics fans could get this close a view to the world's best athletes would be to acquire a press pass.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

Ok, I have to admit, I drop my phone around 2–4 times a week. I'm horrible at protecting it and I've gone through my fair share of cracked phones. Most of the time, once the phone is cracked it's just easier to get an entirely new phone, rather than have to fight your phone provider for a fix.

Monday has been a big update day for Apple. Alongside the release of iOS 10.3, iWork has been updated across both iOS and macOS. The biggest change is the ability to unlock password-protected files with Touch ID, either on iPhone and iPad, or on the new MacBook Pro with Touch Bar.

I hate to break it to you, but you're probably here because you were trolled. Thanks to a Photoshopped image making rounds across Twitter, Apple fans were tricked into believing that iOS 8 allowed them to lock individual apps, accessible only through a passcode or fingerprint ID. While that's not technically true, we've got the solution for you.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

Photobombing, the act of covert sabotage on a photographer and unsuspecting subject, can be a terror. This malicious and disingenuous art form has steadily grown since it first received significant coverage in 2009.

When you have a lot of equipment, dragging it everywhere with you can be a pain, especially when the weather's bad. Sure, you can put it in a camera bag, but a lot of them don't protect your stuff from water, and waterproof cases can get expensive.

This video shows us the method to make a universal motion alarm to protect your home. You will need a reed switch with an alternating contact, a 9V battery with a battery clip, a switch, a buzzer, a small plastic box and a magnet. When a magnet is brought near the reed switch, it switches to the other contact and the switch is open. If the magnet is removed, the switch is closed and the buzzer starts ringing. Make the circuit with correct polarity for battery and the buzzer. Make a hole in th...

Many acoustical or popcorn ceilings that were put in, in the 1970's, contained asbestos. If you are unsure about the contents of the ceiling take a piece and put it in a plastic bag and send it to a lab for testing. Once you know that the ceiling is asbestos free and you are ready to take it down, start by turning off the power to the room. Next put down a plastic drop cloth to cover the floor and furniture in the room and protect it from the water that you will be using in this process. Tape...

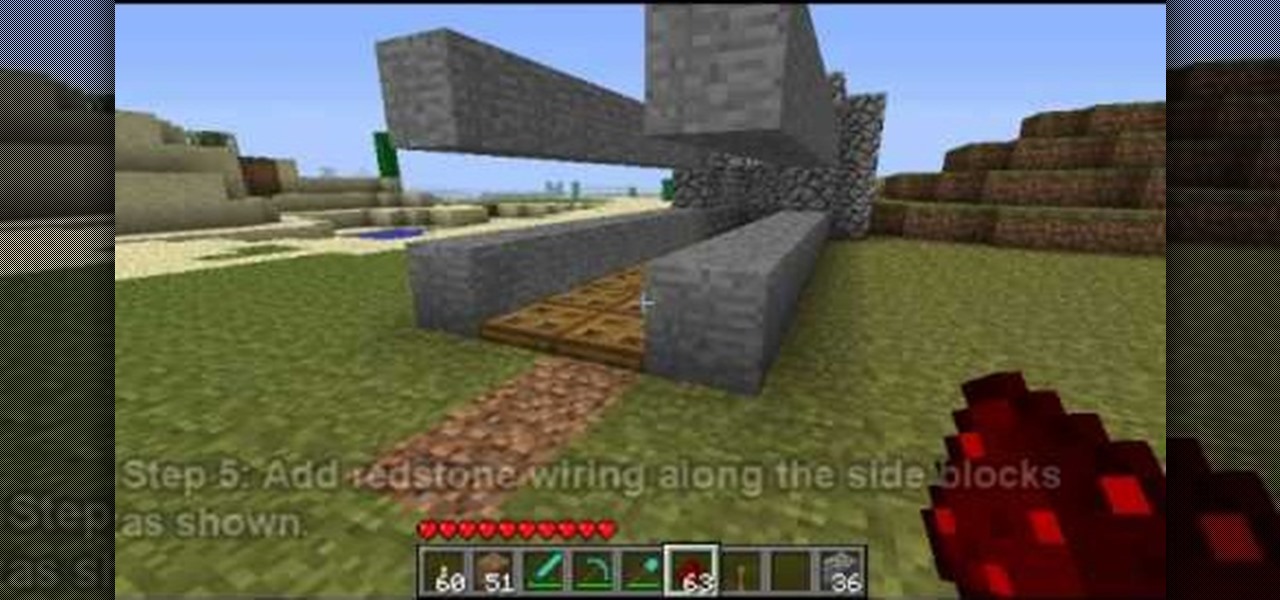
A man's home is his castle. That makes his Minecraft world his... world? Protect the castle in your Minecraft world, learn how to build a drawbridge by watching this Minecraft guide video. You'll get tips on building this design and see which materials are needed.

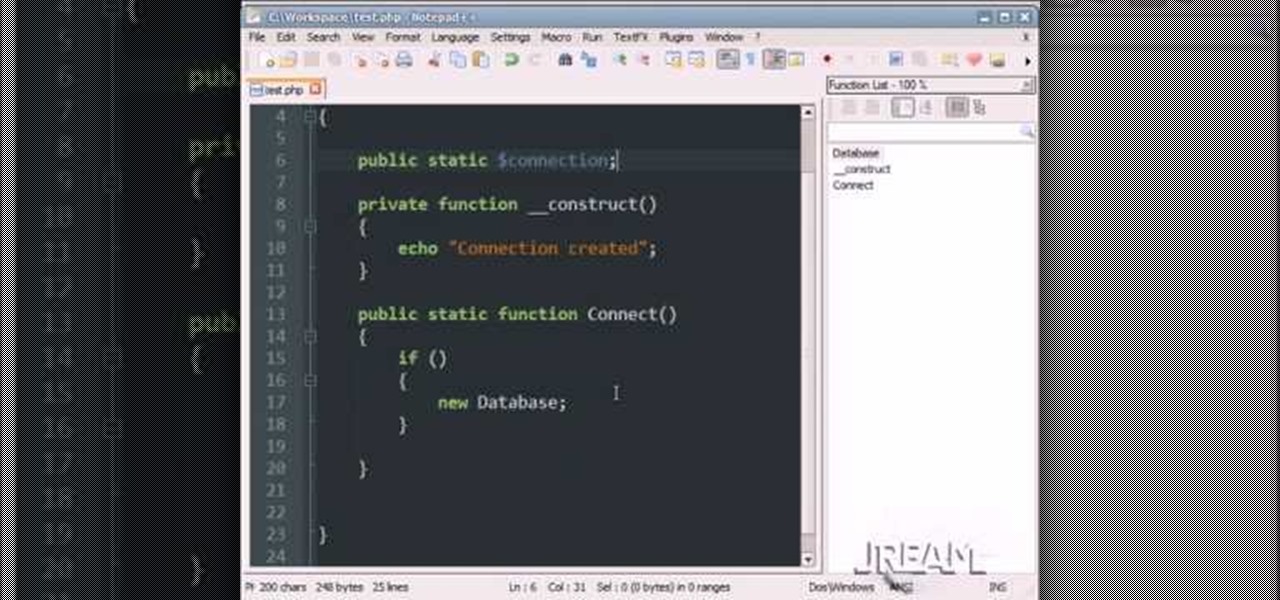
This PHP newbie video with teach you what a Singleton Pattern is and how to use it in your PHP programming. PHP OOP Singleton is great for a database connection when you only want one consistent connection in your application. So, to prevent wasting space accidentally by calling it twice in different areas, this is good way to protect it. Singleton is very popular and used often in Database Connections.

In this video, you'll use Scope and create a simple calculator while learning a little about private, public and protected properties in OOP programming. If you're looking to bone up your PHP coding skills you'll want to check this video out.

If you're paranoid about the security on your web-browsing activities, fear not. This Firefox add-on, called HTTPS Everywhere, was created by the Electronic Frontier Foundation (EFF) to help you protect you from curious sites. Installing this add-on will make most websites default to the more secure version.