While it may be impolite to play around on a smartphone at dinner, having it consume my attention while I'm on a deadline or trying to study can prove disastrous. With Netflix and social media just a tap away, it's a dangerous game of wills, one that the phone usually wins.
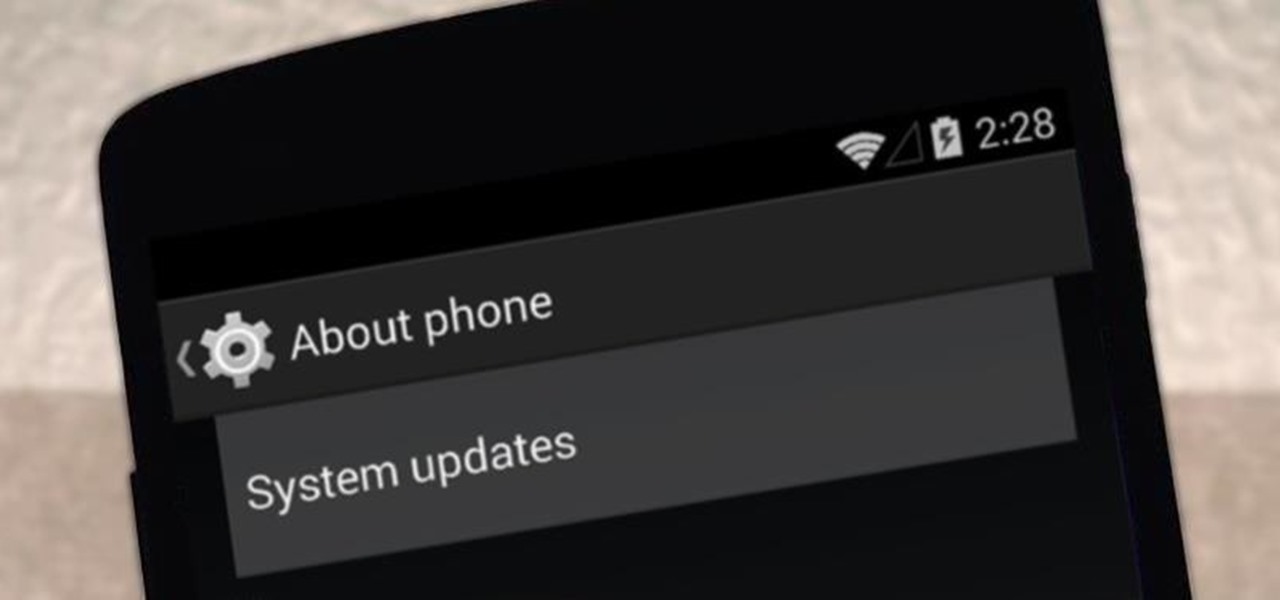
It appears that the next iteration of KitKat, Android 4.4.3, is fast approaching. If the past is any indication, today's update to the Nexus 5 software changelog on Sprint's website tells us a new version of Android will begin rolling out within 24 hours. Sprint has broken the news of a forthcoming Android release twice in the past. With 4.4.1 and 4.4.2, a mini-changelog was posted on the Sprint website about a day before Google began pushing updates to its Nexus devices.

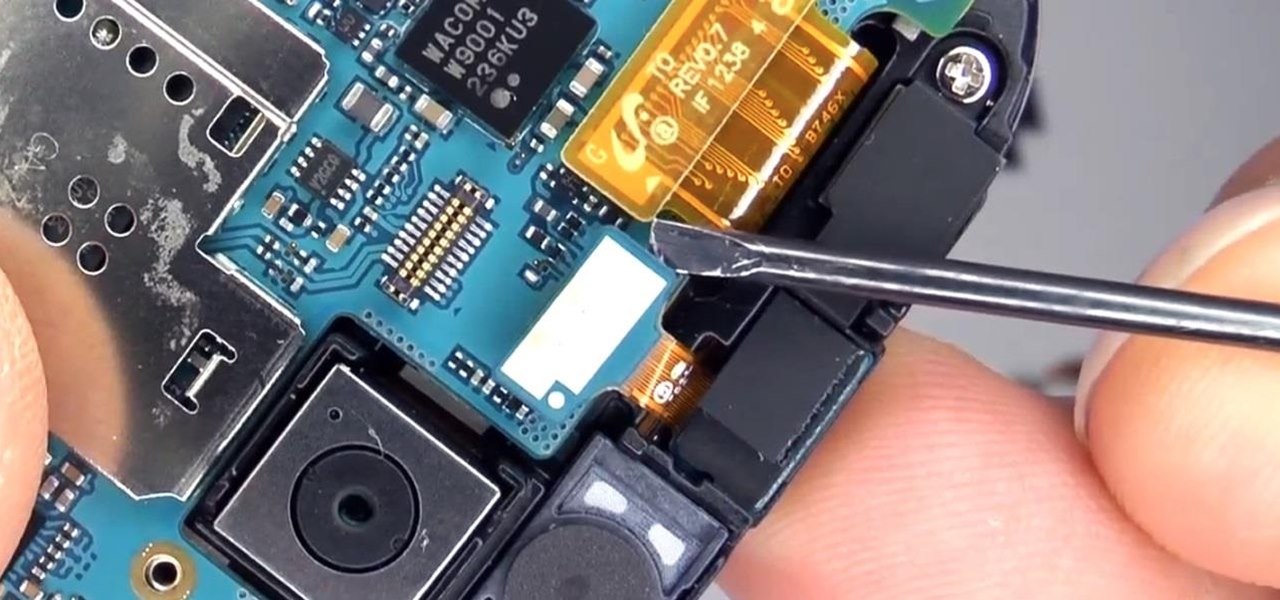
The "Knock Knock" features on LG's G2 phone have proven popular and useful enough to spawn various apps and mods cloning these abilities for other devices. Porting the "Knock On" feature to our Samsung Galaxy S3 isn't as easily doable, since developers would need to create a modded kernel, like they did for the HTC One. The "Knock Off" function, on the other hand, is a lot more manageable.

There's no shortage of ways to filter water, but it doesn't get much simpler than this. Researchers at MIT have found that you can turn dirty water into drinking water with nothing more than a stick.
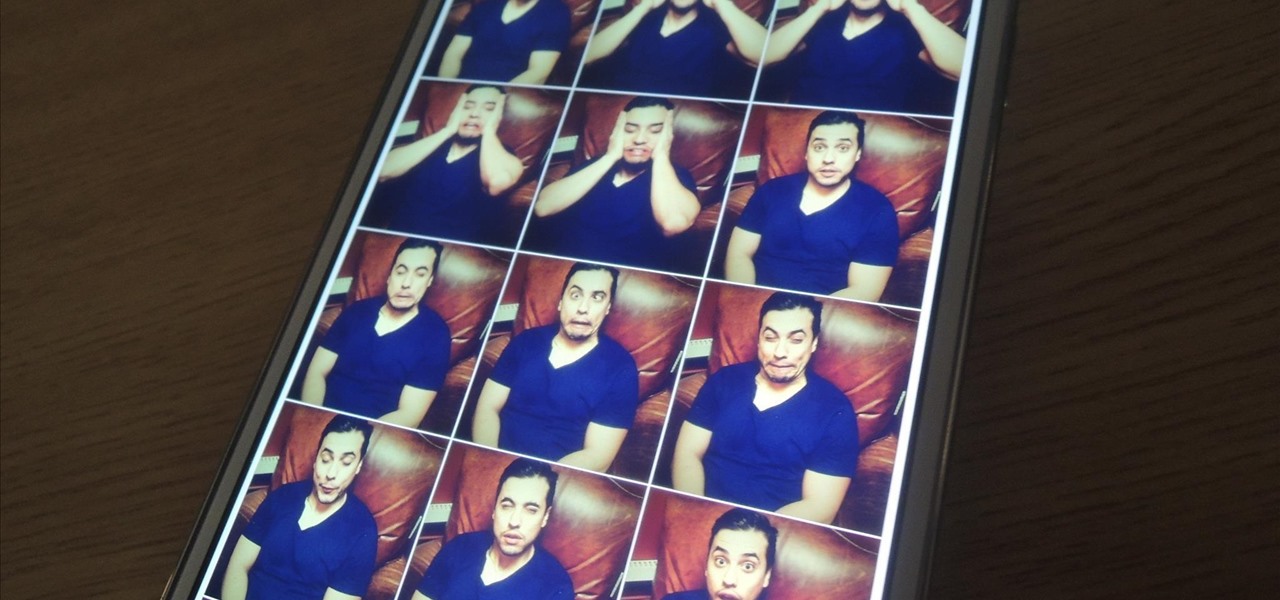
When we take pictures with our smartphones, it’s safe to assume we’re taking more than one. We're either trying to capture the right light, look, or expression… or maybe a slight nod to the right to show off your good side.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

The new Samsung Galaxy S4 may be the only phone to include temperature and humidity sensors, but your Galaxy Note 2 has a few weather-detecting features of its own.

Whether you're at work or in class, there are times when using your phone is unacceptable, regardless of that subtle yet sudden twitch in your arm that arises every time you hear the vibration of a text message.

Portal has been one of the most critically acclaimed and universally loved games of the last few years, and there's plenty of fan art to prove it. From building a Portal gun, to a gravity defying Companion Cube, and even installing Portal onto a graphing calculator, fans have found some innovative ways to show their love for the games.

With the ever-evolving technology that imbues photography, we are never short of fantastic awe-inspiring shots. Digital cameras can capture things that the naked eye only wishes it could see, like streaking lights, rapid movements, and faraway objects, and it's fairly easy to capture these things if you know the basics.

When the time comes to move home, the logistics of moving your belongings can easily become tiresome, tricky and even disastrous. However, with a little careful planning and foresight, the act of packing can be a simple process. The key to getting the most from your move is in efficiency, planning and care. Here, we take a look at the best ways to pack in order to ensure a safe and simple move.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

The best way to show your parents that you are ready to date is by being responsible. Document just how responsible you are and present them with possible, mind-easing dating options and you’ll be dating in no time.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

Every day we pass bridges, whether it's a foot bridge, a highway overpass, a span over water, or a viaduct over a valley. We pass on these structures without even thinking of the engineering genius that went into their design and construction, let alone the science behind their strength.

Sculpting hands in polymer clay can be difficult. Clays like Prosculpt and Sculpey can be brittle when used to make hands without armatures. A mix of Puppen Fimo, Cernit and Fimo Mix Quick has proved to be strong thus far. Watch this video sculpting tutorial and learn how to make hands out of polymer clay.

Dr. Christopher Lepisto on a study that proves Kolorex (Horopito) is as effective as the leading pharmaceutical drug to killing fungus, without the side effects.

Learn how to cornrow by watching this video, which proves it is so easy that it can be done in a moving car!

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

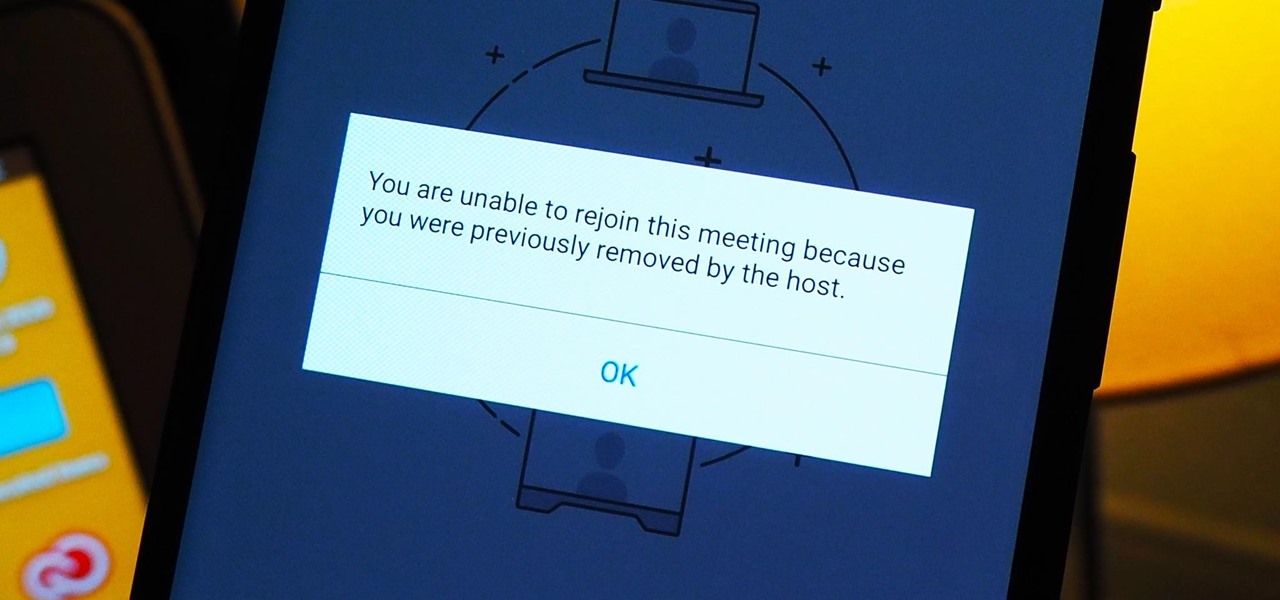
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

It's a good sign for any emerging technology when one of the leaders of an industry adopts it. So when Mastercard, a brand so recognizable that it dropped its name from its logo at CES last year, decides to develop a mobile augmented reality app, the moment is a milestone for the AR industry.

Best known for its mobile phones and television sets, South Korea's LG has had a quieter presence in the US compared to the country's homegrown efforts.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Now that Lego Movie 2, a film about an imaginary world made of plastic bricks existing parallel to the real world, is in theaters, it's the perfect time to shop for Lego apparel at a store modeled after that world.

Among a crowded field of AR cloud companies aiming to power the future of augmented reality by creating a world of persistent holographic content that lives in a cloud, accessible across devices and accounts, Ubiquity6 is hoping it has found a way to differentiate its platform.

With Pokémon GO as its cash cow and the forthcoming Harry Potter: Wizards Unite and Niantic Real World Platform promising future revenue streams, Niantic has convinced investors to bet on its flavor of augmented reality

Occasionally, a not-so-great movie also does something so right that you have to forgive some of its sins and give it a little love. Such is the case with the latest film from Keanu Reeves, Replicas, which takes a HoloLens-style device and gives us a look at how future research labs might use that kind of augmented reality device, sort of.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Magic Leap continues to launch new AR apps on its fledging app store before the door closes on 2018, and this time the app is a sequel from a veteran VR developer and early Magic Leap development partner.

Hollywood has already proven that it's on board with augmented reality, with examples ranging from Avengers: Infinity War to Ralph Breaks the Internet. But one startup wants to make the augmented reality content that's being used to promote TV and film entertainment smarter.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

It turns out that attending the L.E.A.P. conference last month may have mostly been best for demoing the Magic Leap One in person, as the company has now uploaded the majority of the insider panels held at the event in Los Angeles.