The original frozen hot chocolate is from Serendipity 3, an extremely famous eatery in NYC. However, its fame had created many copycat recipes, which eventually prompted its owner, Stephen Bruce, into releasing the delicious recipe in 2004.

We like our Egg McMuffins around here, albeit homemade with our preferred ingredients: whole wheat (or homemade sourdough) English muffins, a slice of thick Tillamook cheddar cheese, a meat, perhaps, like Canadian bacon, and finally—that perfectly-fried, perfectly-shaped egg.

A cup of ginger tea with lemon first thing in the morning, a pick-me-up cup of green tea (or matcha) to fight off the afternoon slump and a soothing cup of chamomile tea to help me unwind before bed—I would be lying if I said I weren't a major tea enthusiast.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

I am officially breaking up with my daily breakfast of avocado toast and embarking on a promising new relationship with savory oatmeal. Yes, you read that right—savory oatmeal.

My Cuisinart ice cream maker was a wedding gift; it wasn't something on my list, but I jumped up and down with delight when I unwrapped it. I never would've purchased this appliance on my own because it didn't seem practical, yet I loved the idea of making homemade ice cream.

On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodified, Vanilla Android devices like the Nexus series.

Uh-oh: you wake up one morning with the telltale signs that you are coming down with something. Your throat is sore, you can barely breathe out of your nose, and you have a nagging cough.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

Before I get ostracized by all of you whisky lovers who live and die by whisky served neat, let me say my piece.

During my time living in dorm rooms and small apartments, I would find myself in need of many different appliances—a food processor for making hummus, a blender for vegetable smoothies, or even a mortar and pestle for muddling mojito-bound mint leaves. Luckily, there was one tiny, inconspicuous tool that solved all of these problems: the coffee grinder.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Regardless of your culture or your age, eating with your hands is fun. Flouting social convention and just digging in with your fingers provides a whole other level of epicurean enjoyment. And one of the most entertaining hands-on foods is monkey bread. Food historian Tori Avey provides a comprehensive history of the origins of this pull-apart treat, including the important detail that no actual monkeys are involved in the making of monkey bread. Originally a savory culinary creation from Sou...

I held the orange packet in my hands and presented it to my friend, Seth, as though it were a plastic-wrapped jewel—rather than three ounces of dehydrated noodles.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

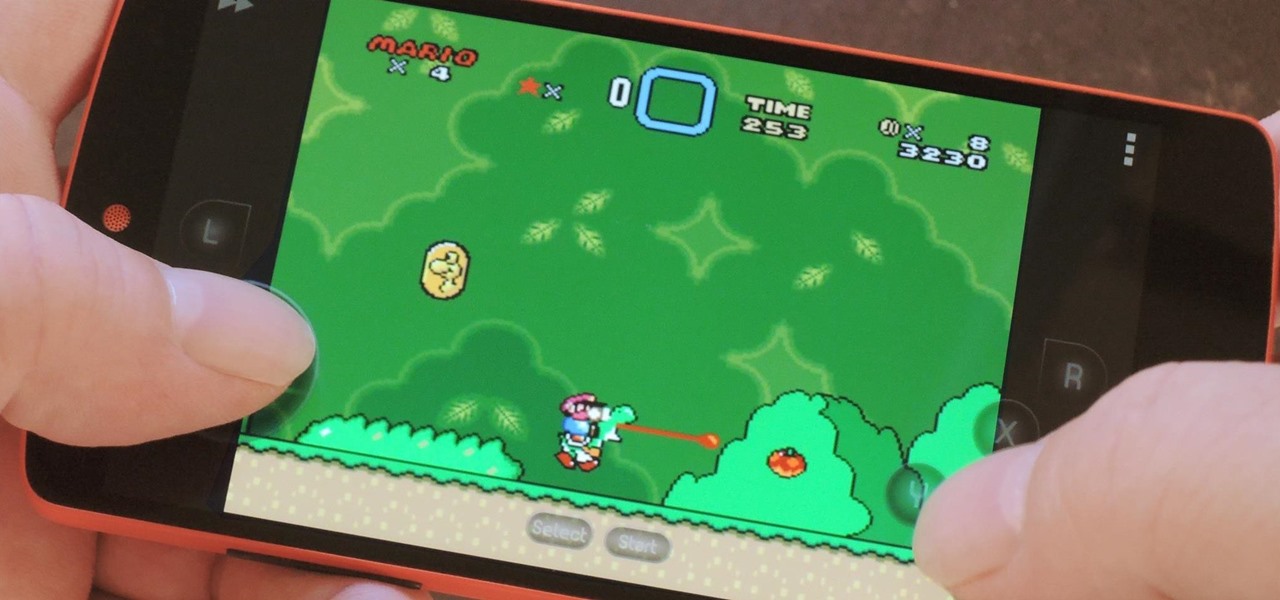
Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

I've cracked thousands of eggs in my life, yet I still usually mess up when I make my morning eggs. Sometimes I crack the egg to hard and end up leaving half of the white on the counter. Other times I don't crack the egg hard enough, and end up spending 20 seconds digging with my fingers until I can pry apart the shell. Sometimes I puncture the yolk on the shell, and other times the entire thing slips out of my hands.

Modern medicine utilizes cutting-edge technology more than ever, so it would only make sense that the powerful handheld computers we all carry around these days could play a big role in wellness.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitting, even if you can't sit in a sunny office or work from home.

I hate to break it to you, but you're probably here because you were trolled. Thanks to a Photoshopped image making rounds across Twitter, Apple fans were tricked into believing that iOS 8 allowed them to lock individual apps, accessible only through a passcode or fingerprint ID. While that's not technically true, we've got the solution for you.

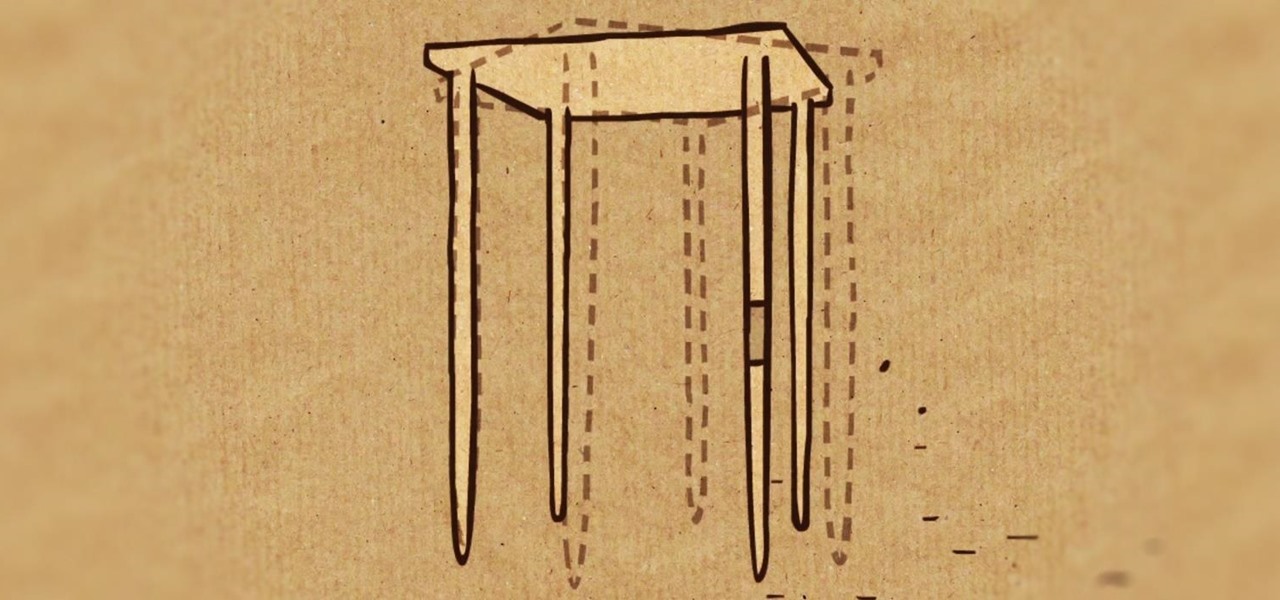
As sure as death and taxes, sitting at a wobbly table at one time or another is inescapable. With your weight on it, the table shifts from one end to the other, lifting one leg in the air and then the other; a parade of seesaws, especially if you have someone sitting on the other end.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

If you're like me, you spend a lot of time on your computer, which can be damaging to your eyes in the long run. Studies have shown that staring at a computer screen or television up close for extended periods of time can have harmful effects on your vision.

Seeing that you probably can't go ten minutes without lying (according to this study), you're probably interested in becoming a better liar. The best way to do so is to learn what makes a bad liar, and then do the opposite.

Are you searching for a homemade cat repellent solution? This article will cover natural indoor and outdoor deterrents for every scenario where cats are causing trouble. The first part will cover home remedies for training cats to stay away from furniture and other restricted areas inside your house. The second part will cover outdoor repellents for keeping cats away from your garden, plants and yard. Step 1: Indoor Repellents for Training Cats

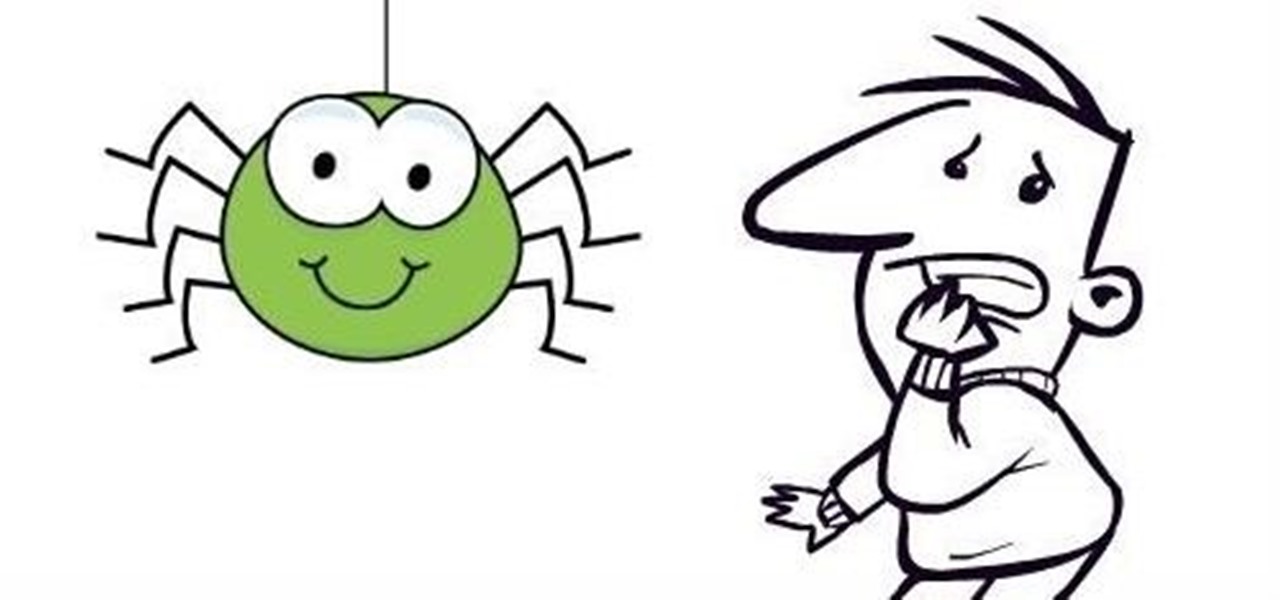
Spiders are common pests that typically prefer to live outdoors. However, insects and warmth will eventually attract them into our houses. They like to spin their webs in corners, crevices and unused areas of your house. Most species are harmless and even act as a natural repellent for getting rid of other insects. However, in some cases, spiders can be very dangerous. Whichever the case may be, they are scary and people are always looking for natural ways to get rid of them.

While we've already covered several good ways to tame the itch of a mosquito bite, you're much better off preventing them from biting in the first place than dealing with the itchy aftermath.

Let's take a minute and talk about something you're doing wrong — using the restroom. Many view the subject as improper or even taboo, but why? Thanks to your upbringing, you've assumed you know the basics... But you don't. Avoiding discussion on the subject has led many of us to unwittingly interact incorrectly during our private time with our old friend, Jon.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.