Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Star Wars season is definitely upon us. No matter where you turn, you can't go a day without being bombarded by merchandising and co-branding advertisements that attempt to draw a parallel between some character from a galaxy far, far away and a galactic cruiser like the Dodge Viper, or a midichlorian-laden power source like Duracell. Yep, it's kind of annoying, but at least we can get some fun out of it here and there.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

Please read the following in Rod Serling's voice. Picture, if you will, a mother. She comes home after a long day at the office, relieved that she took some chicken breasts out to thaw and will be able to make a quick and easy dinner for her family. She opens her refrigerator to get the chicken, but to her horror she does not see it… she forgot to take the chicken out of the freezer after all. What will she make for dinner now? How will she feed her family? She has entered…the Panic Zone.

There was one company at the 2015 LA Auto Show that had everyone intrigued. They didn't have a big booth, and they only had one car on display, but they definitely had everyone's attention.

For those times when you can't get something done by clicking a few buttons with your mouse, the Windows command prompt has always been an indispensable tool. But as much as advanced users have relied on this useful utility, it hasn't seen a significant update since the Windows 95 days.

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

Whether you've watched Game of Thrones or read the A Song of Ice and Fire series by George R. R. Martin, you probably know the White Walkers (aka the Others) all too well. They're creepy, otherworldly humanoids shrouded in icy white skin and ice-blue eyes. They are not to be confused with the wights, the reanimated corpses that the White Walkers control.

Ask around anywhere that Android users gather online, and you'll find that SwiftKey is almost unilaterally the most highly-recommended keyboard for our favorite mobile operating system. It's no surprise either—SwiftKey's combination of insanely accurate word predictions and rapid-fire gesture typing comprise a hard combination to beat.

Live Photos is an interesting new feature introduced by Apple on the iPhone 6S and 6S Plus models that captures the moments immediately before and after you snap a picture in the Camera app, resulting in a GIF-like animation.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

At this point, it'd be surprising if an iPhone release wasn't coupled with some sort of new scandal or controversy; it's gradually becoming Apple's new modus operandi. First, there was antennagate with the iPhone 4. Then it was scuffgate with the iPhone 5. Last year, it was bendgate with the iPhone 6 models. This year, it's chipgate with the iPhone 6S models, which affects something important to all on us—battery life.

Nothing makes my stomach growl and my mouth water quite like the smell of roasting chicken. It's a pretty universal reaction, too—there's a reason every grocery store places its rotisserie grills and delis near the entrance, after all.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase that app you've been lusting after that doesn't offer a free version.

Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

If you ever need help troubleshooting an issue that you're having with your Android device, one of the most useful tools you have available to you is the screenshot. Essentially, this is an exact copy of everything that is showing on your screen at any point in time, which you could use to capture the issue you're having, then share the screenshot with your tech support.

If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to transfer images, messages, contacts, mail accounts, calendars, and more over to your iPad or iPhone running iOS 10.

Apple revealed the new iPhone 6S and 6S Plus at their September 9th event, and there are two particularly awesome features built in just for selfie photogs. The first is 3D Touch, which gives you a quick shortcut to taking selfies just by pressing the screen in a certain way. The second feature is a front-facing flash to help illuminate your face in dark lighting.

Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

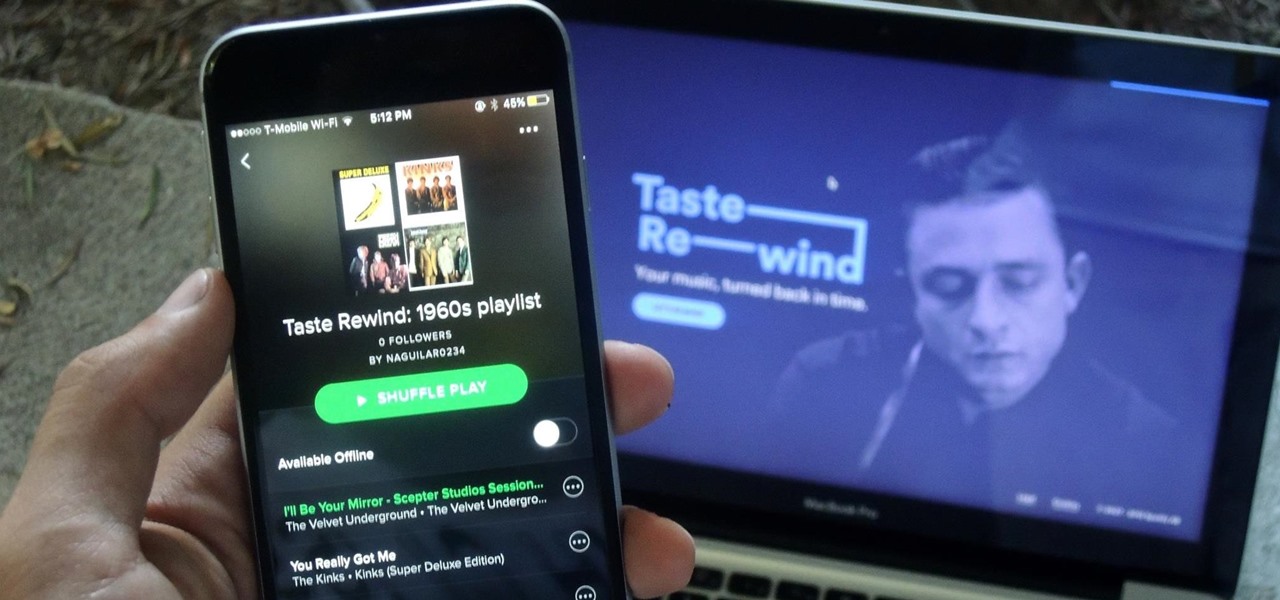
Spotify has a feature called Taste Rewind that claims to know what you would've listened to back in the '60s, '70s, '80s, '90s, and oughts ('00s), all based on your listening history and favorite artists. You can essentially time travel into the past and already have "favorites" songs to listen to! While I was skeptical at first, I tried the feature out for myself and was pleasantly surprised with the results. So if you want to create uniquely tailored playlists from the past five decades, st...

Time takes its toll on your home screen. Before you know it, your clean app pages start filling up with social media, music streaming, video, and dozens of other kinds of apps. And let's face it, a lot of those apps are never touched after the first few times you use them.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

The horizontal dotted icon in your iPhone's status bar serves as an indicator of your device's network strength. And while it does help provide an approximation of how strong your signal is, swapping it out to display an actual numeric value is a lot more precise and can change up the look of your iPhone (or at least the status bar). The process is quick, painless, and you don't even need to jailbreak your phone.

In the U.S., smartphone users spend more time on Facebook and Instagram than on any other app. If this sounds surprising for any reason, it shouldn't. Anyone that's browsed Instagram in a moment of boredom knows that a few minutes can quickly turn into an hour down a rabbit hole filled with Likes, Follows, and straight-up lurking.

Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs.

One of the highest rated posts on Spotify's own community forum is titled "Add support for Google Chromecast," a clear indicator of not only how much this feature is desired, but also of Spotify's lack of care for it. Remaining consistent with statements made in the past, Spotify is firm in their decision to not pursue Chromecast support at this time—or maybe ever—thanks to a deal with Sonos and Spotify Connect.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.