Learn how to cut tile with this DIY video tutorial. If you need to make angular and circular cuts, use an angle grinder and fit a diamond disk. You'll need to fit a continuous diamond disk, not a segmented one, because a segmented disk will chip the tiles. And if you're using an angle grinder, don't forget your personal protection equipment, ear muffs, dust mask, and eye protection.

Eric shares his latest Garden Smart Tip and Ideas. A wonderful addition to your patio garden would be an ornamental fruit tree. Eric shows us a beautiful example of a 'Moro' orange. It's a fantastic tree in a container. There is a lot of flexibility that you have with fruit trees in containers. You can move them around to sunny spots on the patio. In the wintertime you can move them indoors for protection. These trees have great ornamental value plus they have the added benefit of providing a...

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models are rated IP67 under the IEC standard 60529.

One of the joys of having a large yard is the riding lawnmower! It's not that intimidating. This video shows you a few basic ways to use a riding lawnmower. Always make sure you wear close toed shoes and eye protection!

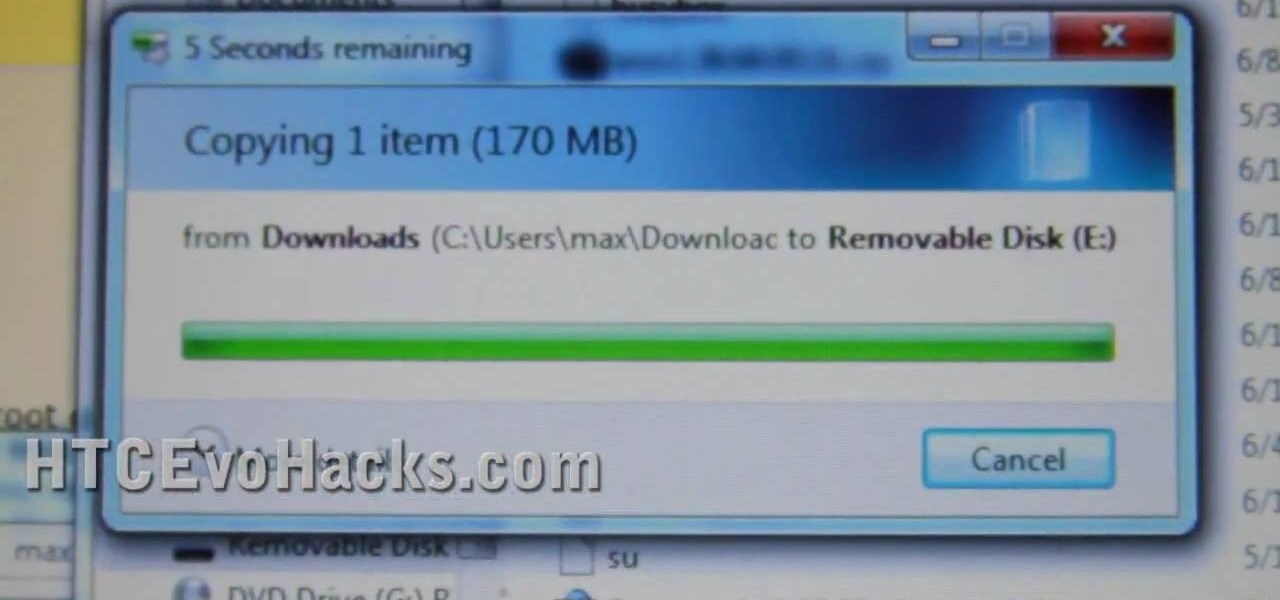
In this clip, you'll learn how to unlock NAND and install a recovery menu on a rooted HTC Evo 4G. Whether you're the proud owner of an HTC Evo 4G Google Android smartphone or are merely considering picking one up, you're sure to be well served by this video tutorial. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

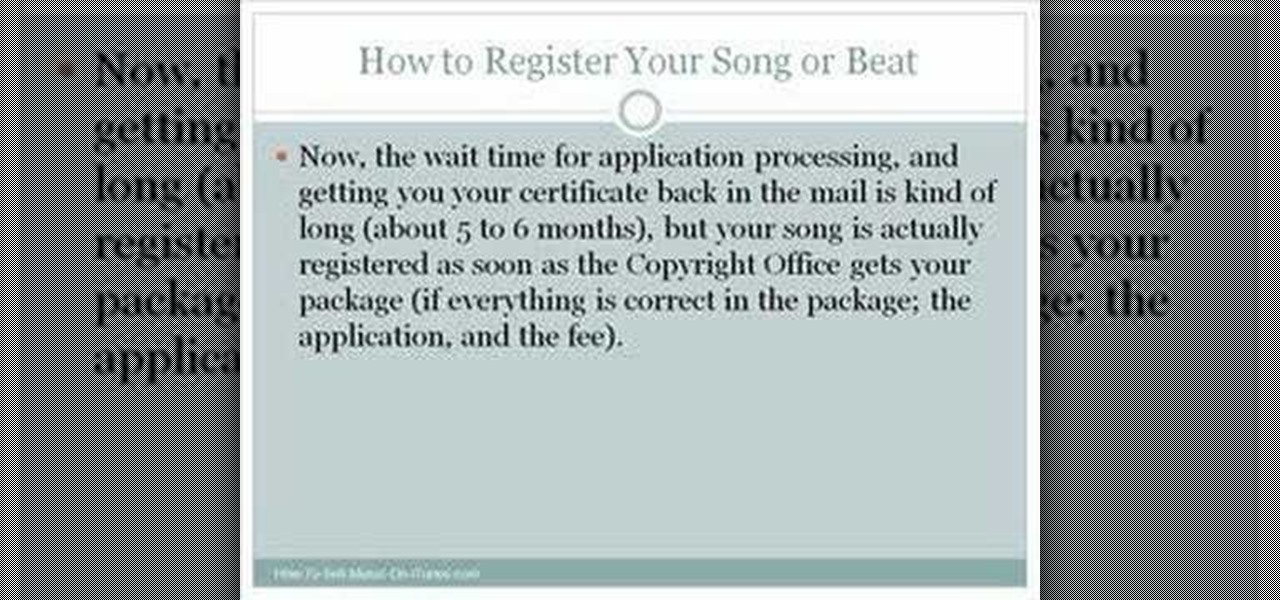
While big parts of copyright protection are applied automatically to creative works like songs and beats (hence the need for orginizations like the Creative Commons), registering your work with Copyright Office is useful to the extent that it can allow you to seek greater damages in the event of an infringement. For more information, including how to register your own songs with the US Copyright Office, watch this free video tutorial.

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

Once we recover from the respiratory infection pneumonia, our lungs are better equipped to deal with the next infection — thanks to some special cells that take up residence there.

This video shows you how to remove the Digital Rights Management(DRM) protection from iTunes music. DRM is a way for Apple ITunes to control your music and where you save it. Hack the iTunes so that it does not interfere with you like this.

If you're considering purchasing Apple's new 2020 iPhone SE, which brings many modern components into the compact body of an iPhone 8, you should know what its dust and water resistance rating means. Just how dirty and wet can the iPhone SE get without breaking any functionality?

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

You don't have to spend hours weeding your garden - just use a weed whacker! Always make sure you wear close toed shoes and eye protection when using a weed whacker. And make sure to keep your hands away from the strings!

In this video, you are shown how to apply epoxy to your car area after it's been repaired. Epoxy is a great primer because of its advantages in adhesion and corrosion protection. You can apply one or two coats if you so desire. Watch this video and you'll learn all about the advantages of epoxy primer.

Oh no! You're lost in the wilderness without an adequate survival shelter! Protect yourself from inclement weather by using soil, clay, mud and other materials found in nature to build your own mud hut for protection from the elements.

Fumbling the ball is the most embarrassing thing that a running back can do on the football field. This video features NFL skills instructors demonstrating one good drill for teaching ball protection skills: having the running back player run through a gauntlet of other players who will all try to strip the ball from them.

In this garden video, you'll learn how to get ready for the winter by laying down mulch for new plants. Mulching new plantings for the winter is very important for protection during the snowy months, and it improves the look of the beds, keeps some weed down, and keeps the moisture in the soil (although too much keeps the moisture out).

This is an instructional video featuring Doug Prime, founder of the Future Engineers Center at the University of Massachusetts Lowell. Aviation snips cut small metal like aluminum, but not big pieces like nails. Nails and large pieces of metal should be cut with bolt cutters. Use eye protection during all cutting of metal. This video shows the cutting of pipe straps.

The most important items in a tool kit, are the protection and safety equipment, like a breathing mask, ear muffs, and eye goggles. Other than that, tools vary on your needs. Some basics are a handsaw, a hacksaw, a level, a hammer, screwdrivers, a measuring tape, a shifting wrench, a chisel, pliers, a combination square, a utility knife, and a clamp. Watch this video home improvement tutorial and learn how to select tools for a basic tool kit.

Make your iPod do so much more than carry tunes. An individual iPod can keep your iPod from getting mixed up with someone else's. Cases and skins can offer protection from damage. Watch this video iPod tutorial and learn how to customize your iPod.

Between "genuine danger" and "raving safety paranoia," there must be some sensible middle ground for dry ice.

After you've taken your iPod Nano apart and fixed it, you might want to put it back together. Check this video out to see how to assemble the iPod Nano Generation 2 with narration for each step.

I explain how to view and control your computer from your iPhone/iPod Touch. This works over Edge and Wifi connection, but obviously the better your connection the faster it will go. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.

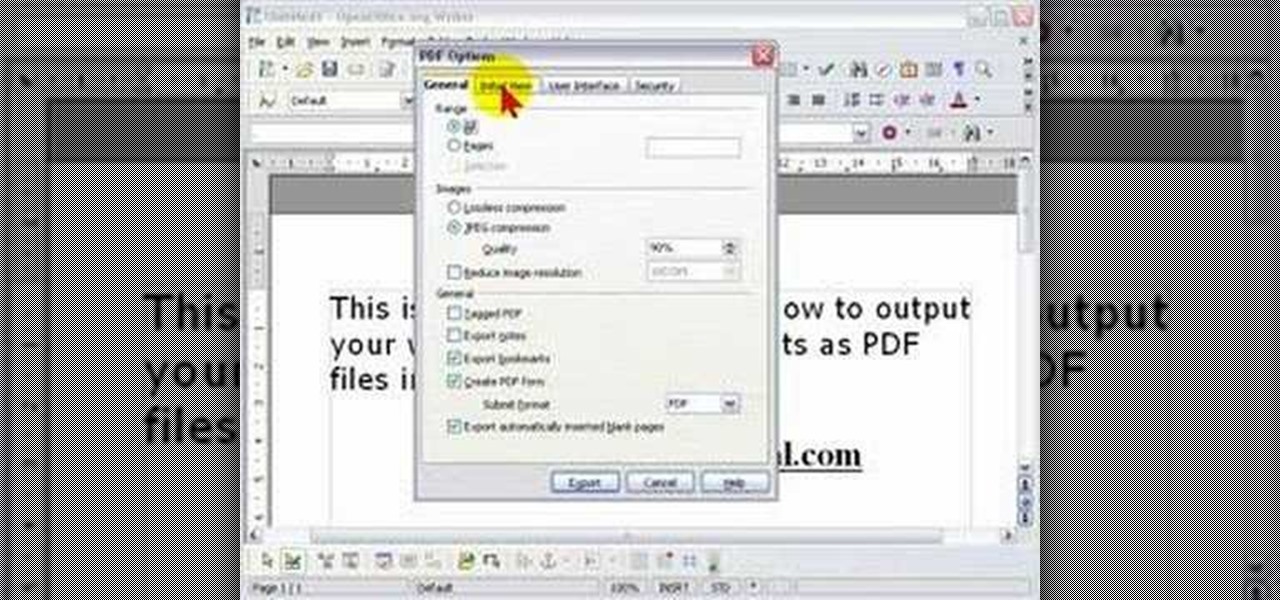
In order to protect your word processed documents, it is a good idea to export them for distribution as PDF files, which allows you to encrypt, and add password protection to your work.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

If you use Office 2008 for Mac and all its applications (Word, PowerPoint, Entourage, Excel), than you need to know about the predefined workflows available using the Script menu that uses Automator to help perform mind-numbing tasks. The Microsoft Office for Mac team shows you just how to save time by using predefined workflows in this how-to video.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

This gorgeous '60s hairstyle was inspired by the Audrey Hepburn film "Breakfast at Tiffany's." This look is quite elegant and suitable for formal events. Most importantly, it is very easy to create.

Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play the basics in Evony online. See exactly what the game Evony is!

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Once again, Samsung has certified its flagship Note series with an IP68 rating. With this rating, the Galaxy Note 20 and 20 Ultra have some degree of dust and water resistance.

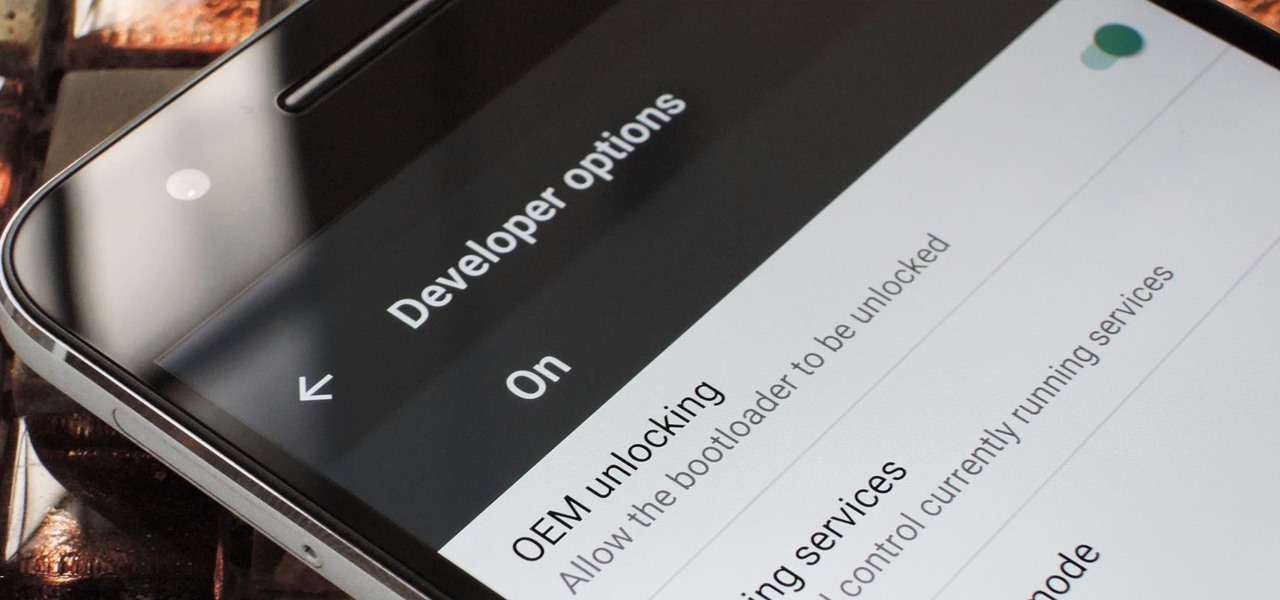
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

With all the documents ready, we need to fill our wallet with money for the travel. This video discusses various ways of filling the pocket. That is how to prepare the money for international travel. Over the years credit cards have been widely used by many travelers, which is safer than carrying cash. In this case we need to contact the credit card provider well in advance and notify them about the travel. Also we need to learn about the various fees applicable to international purchases. Th...

In this clip, you'll learn how to get started using Symantec's Endpoint Protection Small Business Edition on your Microsoft Windows PC. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over four minutes. For more information, including detailed, step-by-step instructions, take a look.