Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge your phone's battery up to 70% power in just 30 minutes. What's not to like?

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

We had some friends over for a barbecue a few weeks back. Among other items, this outdoor soirée featured an epic potato salad (bacon, basil, crushed potato chips, pickles—the whole nine yards). And, like many potato salads, ours was made with a hearty amount of mayonnaise.

Our brains do a magnificent amount of work to process visual stimuli, but they aren't difficult to fool. Optical illusions can trick our minds into believing what we're seeing is real, even if it's not—and virtual and mixed reality technologies take advantage of this little loophole in our brain to help us accept the unreal.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Today's pollution, hectic lifestyle, inadequate sleep and no time for pampering can leave your skin lackluster resulting in drying skin and making dry skin drier ultimately causing the early appearance of wrinkles and aging. A good fruit facial helps relax your skin from deep inside and the proper messaging gives it a rosy glow by increasing blood circulation imparting your face with a luminous glow. These are even better because they are natural and chemical free unlike the artificial facial...

Several years ago, I moved to Brooklyn, New York, just outside a Spanish neighborhood. It was here that I was introduced to chayote. Fast-forward to present day: I live in Los Angeles and buy several chayote squash a week to cook with—yes, I said several. It's so versatile and healthy! For the uninitiated, chayote (chai-YOH-tee) is a light green squash shaped like a pear originating from central Mexico. Although it's considered a fruit, chayote is a member of the Cucurbitaceous (gourd) family...

Hey guys I am starting this Series because I thought there was a lack of post about Hacking from Android.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

We here at Food Hacks are all about saving you, our wonderful readers, time and trouble in the kitchen. So when I saw that Barilla had come out with their Pronto line of "One Pan, No Boil, No Drain" pasta, I had to give it a try. While no-boil lasagna noodles have been around for a while and allow the pasta to essentially cook en casserole, this relatively new addition to the pasta scene includes elbow, penne, spaghetti, and rotini varieties that allow for usage in a greater variety of pasta ...

There's a feature in Google's Photos app for Android, iOS, and the web that lets you create shared albums with your friends and family. It's really a useful feature that makes it fun and easy to collaborate on an album with a person or persons of your choosing.

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Initially reluctant to port Firefox over to iOS, Mozilla has finally released the first public preview of their famed web browser. While this is great news for all Firefox users, the bad news is that the browser is currently available for download only in New Zealand.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

Few things in life are as exciting and magical as fire. And setting things on fire while cooking? Well, now you're speaking my language. I'm not talking about grilling, though I do love some outdoor cooking. No, I'm talking about the most badass trick in any cook's arsenal: the flambé.

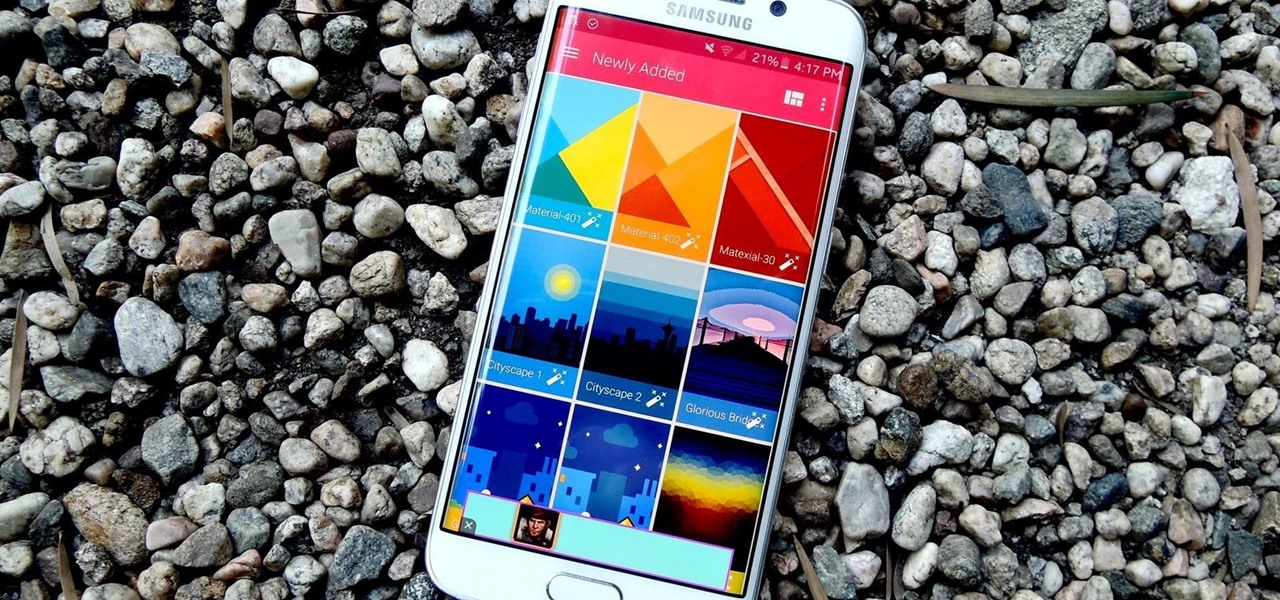
Out of all the questions that we receive from our readers and viewers here at Gadget Hacks, the most frequently asked one is "What wallpaper is that?" On occasion, our wallpapers may be personal or images from the web, but for the most part, they come from dedicated wallpaper apps.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.