Learn how to tie a variation on an Icicle Hitch - This version can easily be tied in the middle portion of the fixed object with no need to pass a bight over the end. The Icicle Hitch is a knot with far greater holding power than a Rolling Hitch, used to secure a rope to a railing, pole, or another rope where the direction of pull is along the length of the fixed object. This knot greatly resists sliding and slipping. This knot can be used in sailing, boating, general use, camping and bondage.

Sometime we can't ride our bike everywhere and we need need to take public transportation. This instructional how-to video shows you how load your bicycle onto a bus rack. Follow along and learn the proper way to ride the public transportation with your bike.

There are tricks to hooking plastic baits. A fisherman will show you how easy it is to hook a grub bait in this video tutorial. Take action: push hook into nose, noting where hook should come out of bait, and push nose up over hook barbs to secure. Ron, the instructor in this how-to video from Live Strong, is a professional bass fisher and has qualified for the Bass Master Classic and has won two B.A.S.S. Western Divisionals. He has also recorded multiple top ten finishes on F.L.W. tournament...

Installing a slab door is a project that some people choose when they don't want to replace the door jam but just the door itself. In this DIY video tutorial, you'll learn what it takes to hang a new slab door or to replace a damaged one. See the process of removal, hinge mortise measurement and securing the new door in place and learn about the tools required for this moderately difficult job. For more information, or to get started installing your own slab door, watch this how-to!

Getting you, your family and your friends in and out of the house is not the only thing an exterior door is about. When you install a door you want it to swing smoothly, latch tight, seal out the weather and be secure. You can get a big head start on reaching these goals by choosing the right set-up to begin with, and this usually means buying a pre-hung door. In this DIY video tutorial, you'll find step-by-step instructions for installing a pre-hung door in your own home. For more, or to get...
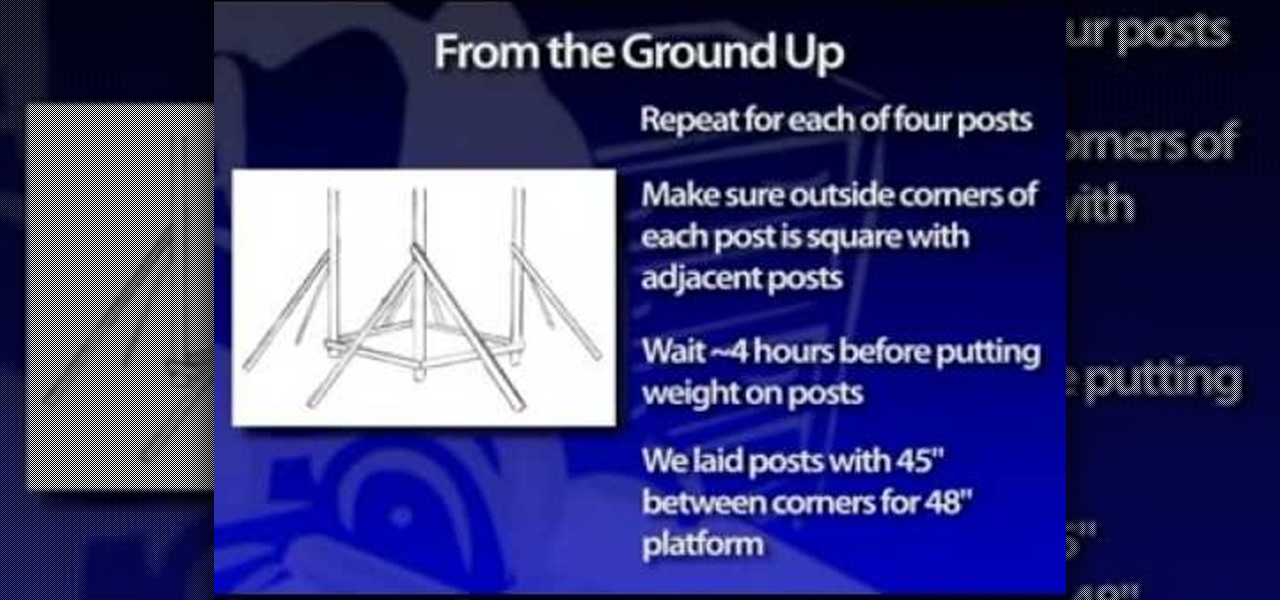
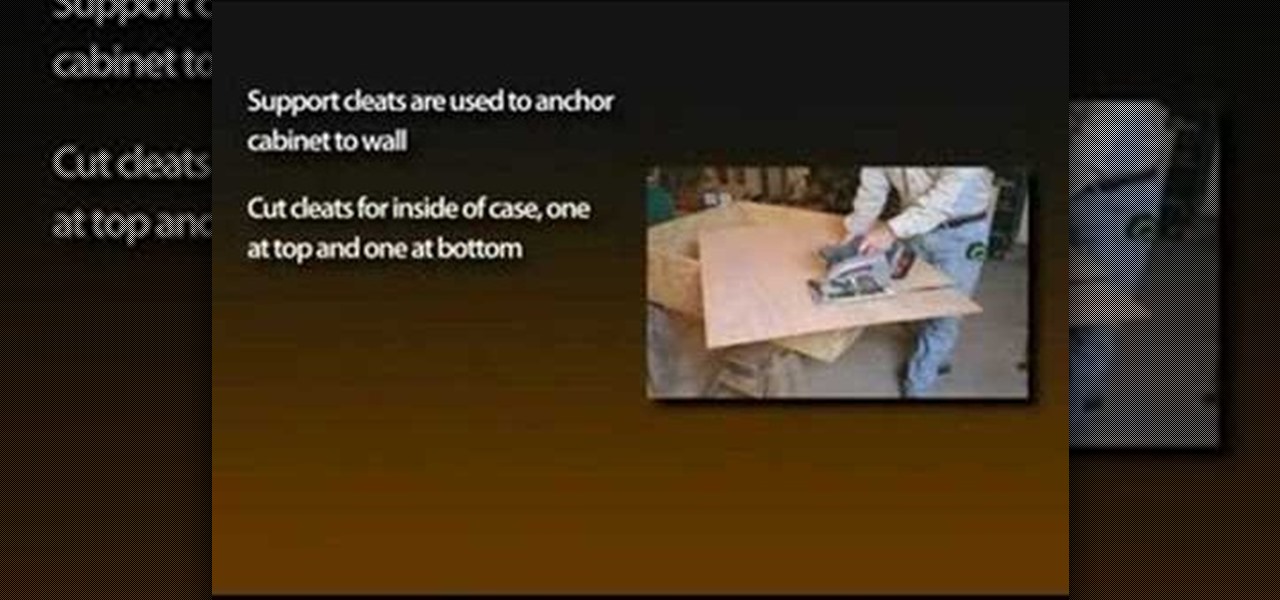
In this video tutorial, you'll find instructions for building a standard joist design playground slide, supported by 3-by-4 posts and secured with galvanized fasteners. All fasteners exposed to the outdoors must be weather-resistant, galvanized, zinc-coated brass or stainless steel. Standard homeowner tools are all you'll need to complete your slide—a tape measure, post-hole digger, circular saw, sawhorses and a level. A good drill/driver is a great tool if using decking screws as fasteners. ...

With the growing popularity of cordless power tools, it's extremely easy these days to accumulate a lot of portable tools, and when you add in quality corded tools, such as circular saws, routers, planers and air nailers, you can end up with a pretty hefty investment. These same tools are the first to “walk away” in a theft. Left lying around a shop or garage, they can also be somewhat dangerous for youngsters. A locking cabinet not only provides a secure place, but protects the tools as well...

Keep your RV Entrance Steps in tip top condition with this instructional RV video. This tutorial demonstrates how to maintain and repair your recreational vehicle entrance steps. Most RVs have electric steps, which are fairly maintenance free. The biggest component is lubrication. Make sure to lubricate once every thirty days using a lithium-based grease and spray every point. Learn how to inspect the wires underneath your RV and make sure everything is secure. Just follow the simple steps in...

One important part of jewelery making involves properly attaching clasps. This how-to video jewelry making tutorial demonstrates the proper way to attach them. Begin by threading the crimp bead and the clasp onto the bead wire. Using chain nose pliers feed the thread around and loop it back around through the crimp bead. Use the pliers to hold the crimp bead tight. Crimp the bead down securing the wire and clasp.

Take a look at this instructional video and learn how to load virtual console games onto your Nintendo Wii. You'll need the Twilight Hack and an SD card for this process. The Twilight hack allows you to run unofficial software through the SD (Secure Digital) card inserted into your Wii. Since the Twilight hack was found through the lastest Zelda game Twilight Princess, the game needs to be loaded every time before you can run any "homebrew" software.

In order to build a trip wire, you will need the following: a knife, fishing line, a rope/string, sticks, and a large stone.

First of all you have to place your thumb or attach a pin on the ribbon such that there is a space of two to three inches left outside. Bend the ribbon back to the center to create your first loop. Now you have to pass the ribbon back underneath the bow. Then you have to again return to the center to create a complete second loop. Now continue passing the ribbon over and under the bow. Now return to the center and then repeat this step to create six loops in total. After this you have to turn...

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

On Sunday, Microsoft did what everyone expected the company to do by unveiling the long awaited HoloLens 2.

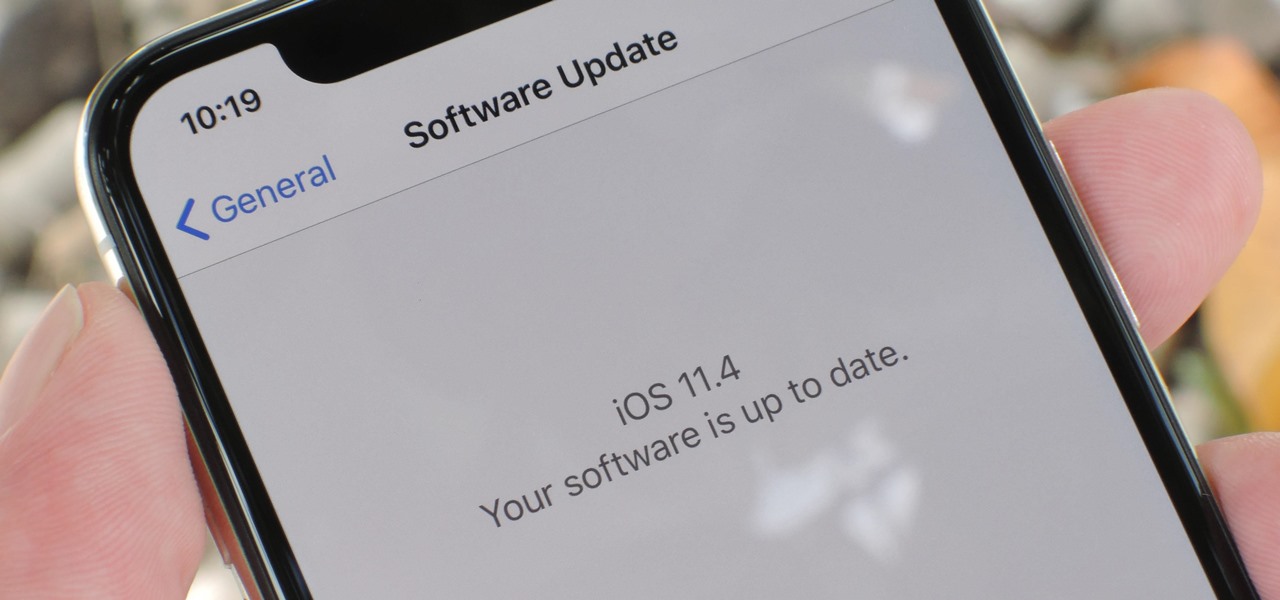
Talk about rapid-fire. Apple released the sixth beta for iOS 11.4 on Thursday, May 17. The update comes just three days after the release of iOS 11.4 beta 5, indicating that Apple is readily approaching the official release of the software. Apple has not issued an official iOS update since 11.3.1, which found its way to users over three weeks ago.

Taking one-handed pictures with your phone can quickly devolve into a juggling act. You have to secure the phone in landscape mode (if you're doing it right), tap to focus, and then somehow hit the shutter button without shaking the device too much. Fortunately, Samsung has a nifty feature that'll help you keep a more secure grip on your Galaxy S9 or S9+ as you take photos with one hand.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

Replacing your iPhone fingerprint sensor has been one of Apple's most cruel tortures. It's a slow and painful process made worse last year when Error 53 messages started appearing on the phones of users who had tried to repair their sensors outside of Apple. The error rendered the phones essentially useless. Since then, Apple has provided fixes but is now finally making it much easier to replace your iPhone fingerprint sensor with the releasing of "Horizon Machines" to official repair locations.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

I'm often reluctant to use a home screen launcher other than the stock one on my Android. Once you're well acclimated with something, complacency sets in, welcoming change with much resistance. Well, my friends, I have seen the error of my ways...

bObsweep Standard and Pethair both come with their lithium-ion battery installed for you. But if you ever need to remove and replace the battery on either model, follow the walk through below.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

The original implementation of Android's face unlock feature was a mess. It took too long to unlock (when it worked), brought up a huge interface that overpowered the lock screen, and maybe most egregiously, was able to be "hacked" by someone holding up a picture of your mug.

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Buns make the look of a woman highly fashionable and cool. Transform your appearance into highly swanky and dashing by following this simple tutorial to make an awesome Long Hair Messy Bun and instantly transform your simple look into a fashionable one. Step 1: Comb Your Hair and Make a High Pony. Now Take Small Section of Hair from the Pony and Start Backcombing the Surface Side. Step 2: Now with Your Fingers

When you're on the go, it's important to keep your belongings organized and at an arm's distance so you're not fumbling in public for your keys, cards, or phone.

UPS offers a four-step guide to prepare packages for shipping. These instructions include shipping advice on packaging materials and proper labeling that can help items arrive safely and on time. And when you are ready to ship, UPS Internet Shipping guides you through the required address fields. Packaging solutions made easy. That’s logistics.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

In this how to video, you will learn how to build a patio enclosure with seating walls. You will need measuring tape, a level, a dead blow hammer, a square, masking tape, safety glasses, and work gloves. You will need the courtyard collection as well. First, draw out a plan for the enclosure. Mark the locations of the posts and panels with tape. Openings should be three to four feet wide. Start building walls at posts. Adjustments must be made at corners. Start by placing four corner blocks. ...