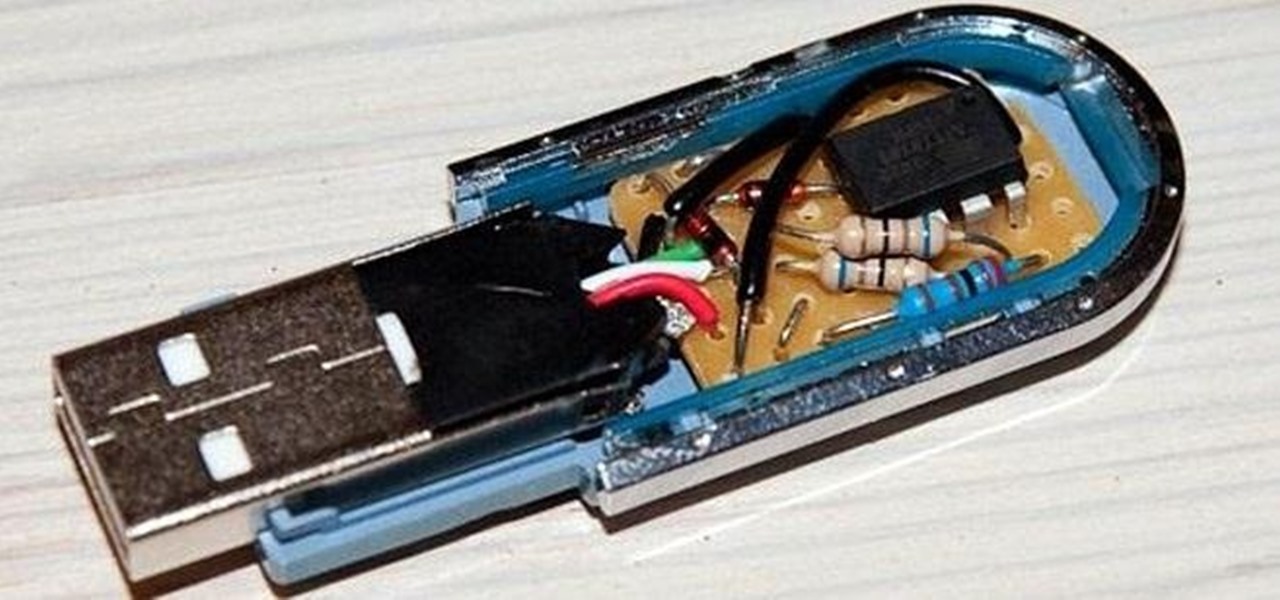
In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

With the new year just around the corner, it's a time we all reminisce about the year that was. In the midst of families fighting over white elephant presents and the financial stress that comes with holiday gifting, you may also be dealing with the stress of hosting parties and get-togethers as well as the decorating that goes with it.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.

Everyone knows that using your phone and driving is illegal, and rightfully so. Tons of people die on the road everyday due to careless people texting or calling someone. Everybody knows that it's wrong, yet everyone still does it anyway.

In these video tutorials, viewers learn how to tie the ribbon on ballet shoes. Make sure that the elastic and ribbon are adequately secured on the shoe. Begin by flexing your foot. Take the inside ribbon and loop it across the top of your foot. The outer side ribbon will go over the inner ribbon. Pull the ribbons tight enough so there is no gaping or sagging. Then, wrap the ribbons around the ankle and tie them together. Now, tuck the tie under the flat part of the ribbon. These videos will b...

Washington State has a history of large earthquakes, as does California. More than 1,000 earthquakes are registered in Washington State each year. More than 10,000 are recorded in California each year. In an earthquake, non-structural elements, which is anything that does not actually hold the building up, may become unhooked, dislodged, thrown about, and tipped over. this can cause extensive damage, interruption of operation, injury and even death.

First of all keep the chicken under the running water and then pad it dry. Then you have to remove the neck, inner portions and the fat from the abdominal cavity. Now season the inside of the chicken with salt and pepper by standing it up inside the bowl. You can now add the desired spices. In this case you can use garlic cloves and lemon pieces. Now close the abdomen cavity and lay the chicken on the cutting board. Wedge the wing tips under the wings. Close the neck cavity by wrapping the sk...

Fifty cent coins and quarters made before 1964 were made of 90% silver. This is considered jeweller's quality silver so can easily be made into a ring. Kennedy Half Dollars can be found at coin shops or on ebay for four or five dollars a piece. Begin with an anvil which can clamp onto a table. This will allow you to hammer without damaging the table. If you don't have a anvil, you can use any flat surface that is sturdy and made of metal. Next, take a small hammer, position the coin on its ed...

It only takes 15 minutes to install new RAM in a Macbook Pro. Before starting, remember to make sure that the power is off. Turn it over and release the latch in the left hand side. This will release the door and expose the battery. Remove the battery. With a #00 Philips screwdriver, remove 4 small screws lined up on the top of the opening. Next, remove the other 4 screws on the other side next to the hinge. When that is done, remove the cover. You will see the RAM directly in the middle. On ...

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Check out this informative video tutorial from Apple on how to set up iChat to text, video or audio chat with friends. iChat is an application that's part of every new Mac. It lets you stay in touch with friends and family in fun innovative ways.

Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

Create and animate a stop motion LEGO brickfilm! Yes, that's right... you can make your very own animated brickfilm, but wait... what exactly is a brickfilm? Brickfilms are animated films using LEGO, Mega Bloks, or other plastic construction building block toys. Most are stop motion, but some brickfilms are even made with CGI, traditional animation and live action.

Norway-based production tools company Vizrt is putting the real into augmented reality with its broadcast AR solution that's designed to keep sports fans (and other audiences) watching.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

Watch this video to learn how to properly secure a bookcase in case of an emergency.

Whether you're using your phone's map to navigate or entrusting your passenger with the responsibilities of the mobile DJ, your phone needs a secure place in your car. And if it could charge while it's there, that's great too. The Naztech Smart Grip Wireless Charging Car Mount is exactly what you're looking for if you need a place to keep your phone secure, charging, and able to be used when it's safe to do so. Right now, this adjustable phone mount is on sale for $39.99, an 11% discount.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

As much funding as Magic Leap has secured, another round of funding will still catch headlines. However, the latest funding solidifies the company's strategy for succeeding in the consumer segment of AR.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

Not content to merely assist surgeons via the HoloLens, Medivis has expanded its augmented reality suite to Magic Leap One with an app for medical students.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.