Place 2 Tbsp. oil in a wok or large frying pan over medium to high heat. Add garlic, galangal (or ginger), shallots, and chili. Stir-fry until fragrant (about 1 minute). Stir-frying Tip: Add a little water to the wok/pan when it gets too dry instead of more oil.

These videos show you how to use baking strips to make a better cake. Use caution when using baking strips, and watch your oven carefully.

The first thing anybody really thinks about after watching Rear Window is how much they want their own telephoto lens. These days, they aren't cheap, so how do you go about spying on your neighbors without putting down so much dough?

Everyone gets cut every once in a while, but sometimes those cuts can be more serious than expected. It could turn into severe bleeding, and there's a certain way to deal with this type of bleeding in a victim. How would you treat someone who was bleeding severely?

Shaun Alexander was an amazingly productive NFL running back. In this video, he takes some time to explain for young running backs how to hold the ball properly, protecting it from the defense and potential fumbles. Proper finger positioning and placing the body between opponents and the ball are both crucial elements.

In this video, Karlyn M. Campbell, an Information Technology student, goes through how to set up and secure a wireless network on a laptop. For a wireless network you will need your computer, a wireless router and its CD, and a USB wire. First the video goes through how to set up the router by using its installation CD. This video uses a Belkin router, and so shows the steps the Belkin installation CD takes the user through. The CD also lets the user decide which security settings he or she w...

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database securely via SSH tunneling. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a secure connection between a given MySQL database and the DreamCoder for MySQL, take a look!

Babies have no way of communication other than crying. = Touch is one of a baby's most highly developed senses at birth. Holding, caressing and cuddling your infant is crucial to helping her feel safe and secure. There are a number of tips demonstrated in this instructional video to help calm a crying baby. Watch this video child care tutorial and learn how to comfort a baby.

This video demonstrates how to install or replace a dead bolt in your door. Having a dead bolt lock gives you a added sense of security, because it is more secure than just the lock on the door handle.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

The story of Meta and its Meta 2 augmented reality headset isn't over, there's a new development that could impact its ultimate fate.

Augmented reality optics maker WaveOptics has just infused its operations with a fresh round of funding to facilitate its objective of bringing consumer-grade smartglasses at a $600 price point to market in 2019.

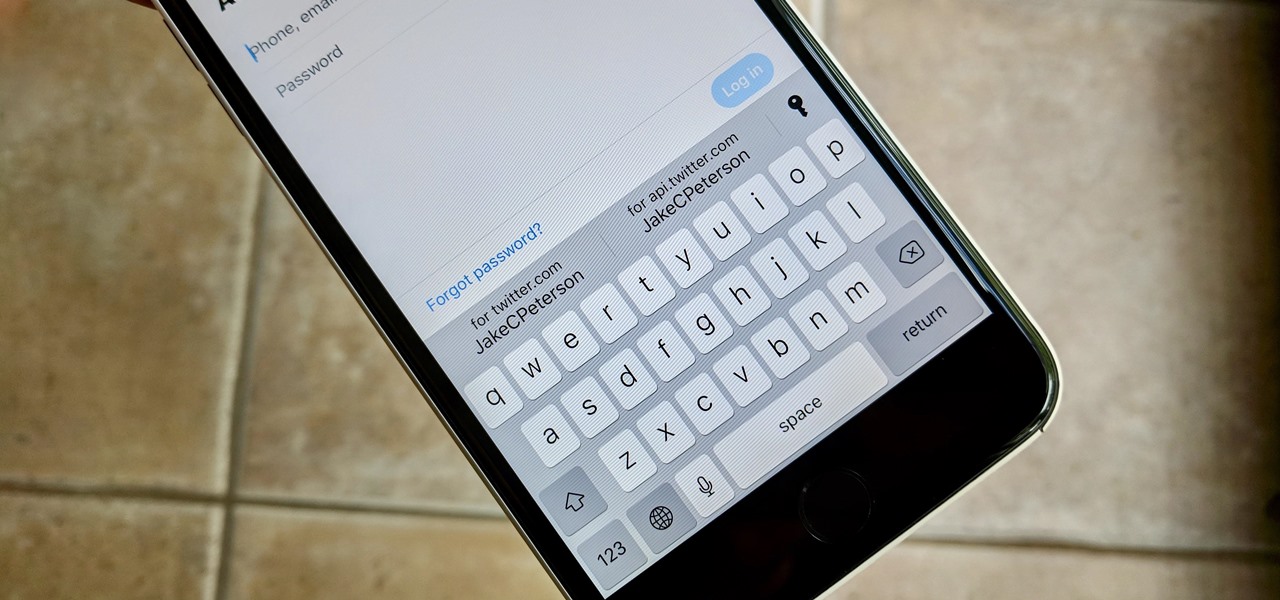
Apple's dedication to iPhone security is one of the company's biggest selling points. It's no surprise then that iOS 12 offers users a simple yet powerful way to make, save, and auto-fill strong passwords to your iCloud Keychain when creating accounts in both Safari and in apps. The best part? You hardly need to do a thing.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Apple released the third beta for iOS 11.4 on Tuesday, May 1. This update comes exactly two weeks after the release of the second beta, which, in addition to adding a new wallpaper, fixed issues with AirPlay, Music, and Keychain. The only noticeable change in beta 3 is a fix for unresponsive 3D Touch.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Nissan began to offer Level 2 driving capacities in a mainstream model when it debuted its ProPilot self-drive option for its Serena minivan in Japan last year.

Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Google's monthly Android security updates are generally welcome—at the very least, they provide a feeling of security that our device is now somewhat safer than it was 30 days ago. Vulnerability patches, slight enhancements to performance, and overall bug fixes are generally included in the monthly OTAs, but as it turns out, they're not always for the better.

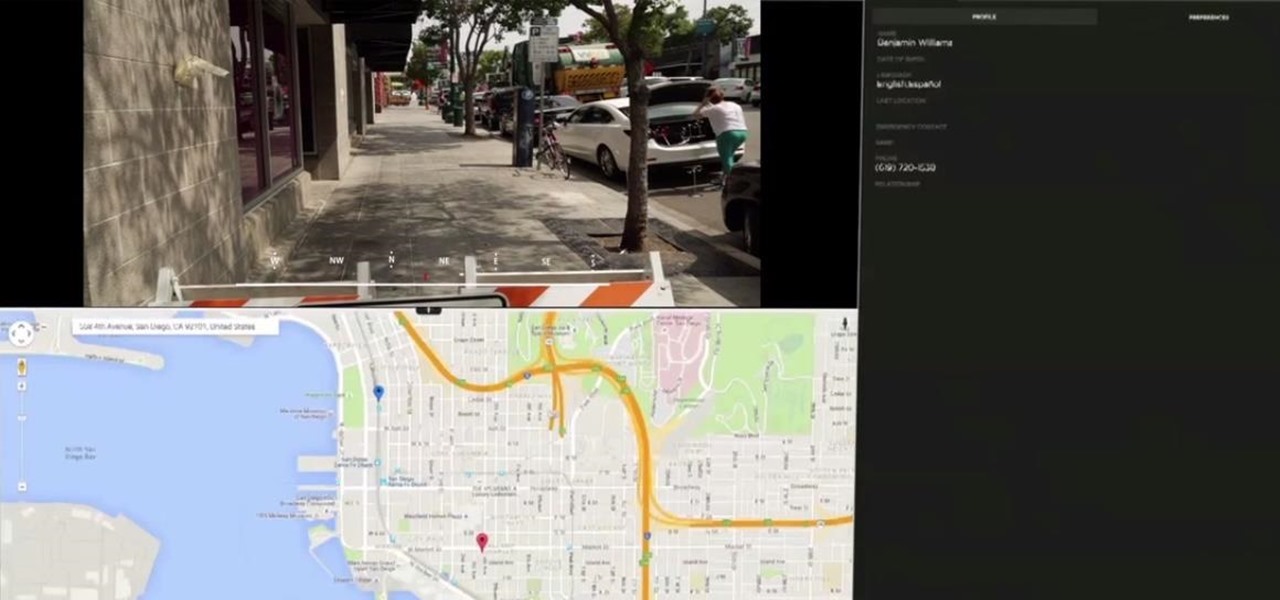
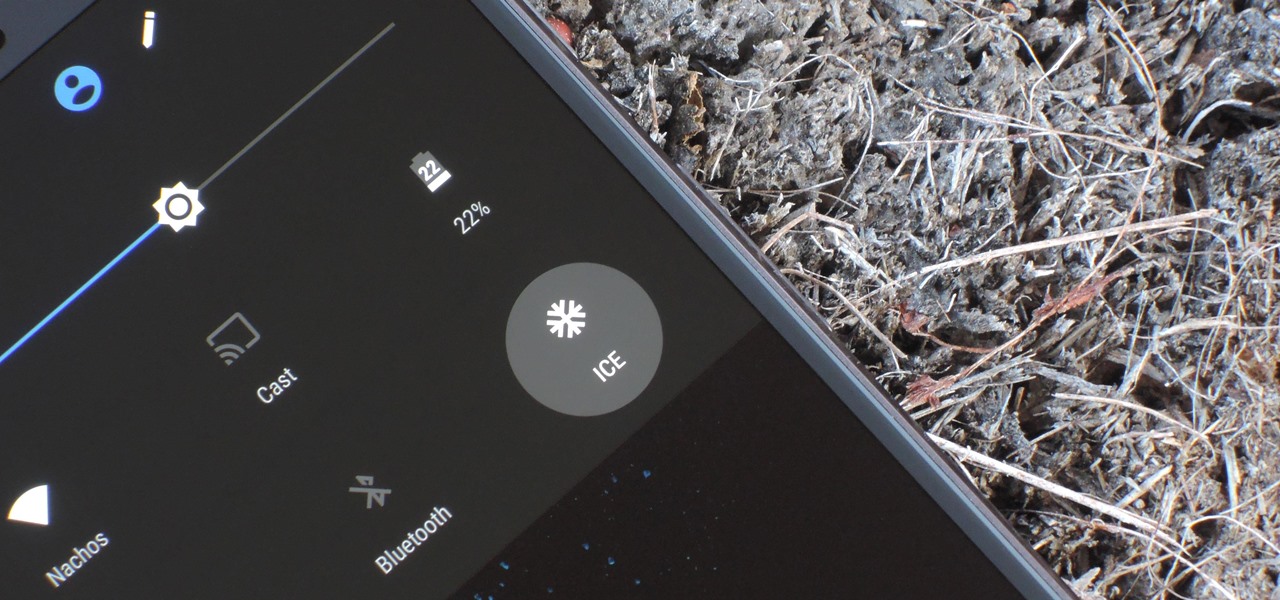
If you're ever in a major accident or have a bout with acute onset health problems, first responders will need to know as much information about you in order to provide proper care. For this reason, paramedics and firemen have been trained to search a subject's cell phone to find ICE (in case of emergency) contacts that know your allergies, blood type, and other vital details.

Google's new Pixel and Pixel XL flagships are some very powerful smartphones, but as with any high-tech gadget, they're only as capable as the user allows them to be. So if you're a proud new Pixel owner, it's time to bone up on a few new features to help get the most out of your device.

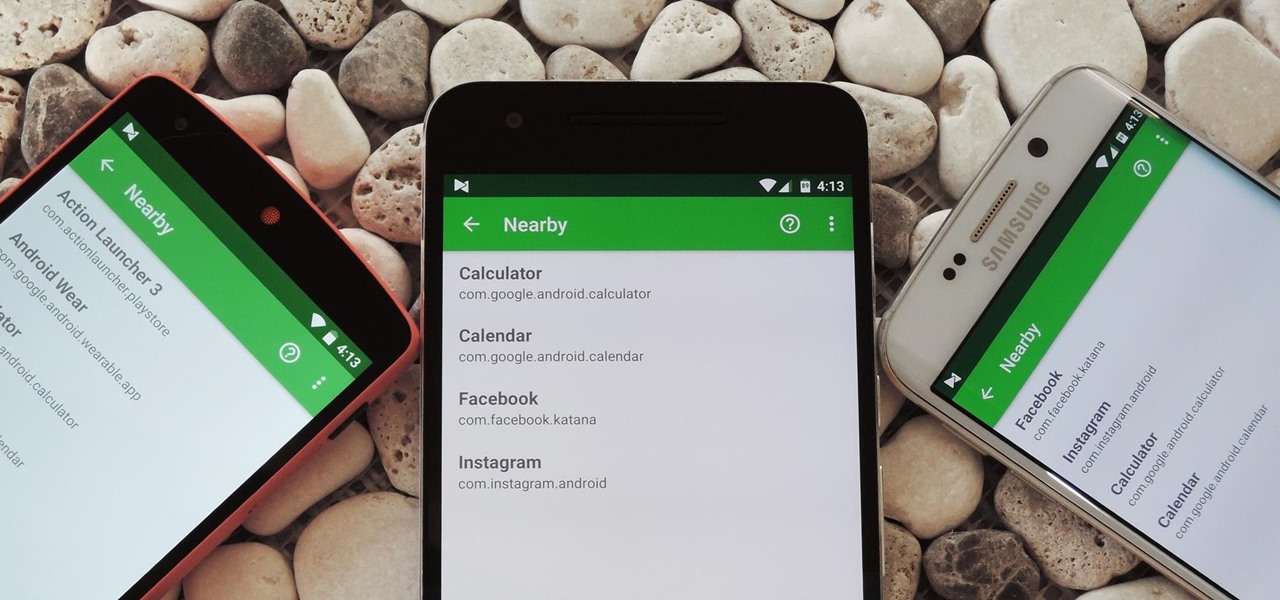
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

Android has a built-in browser called WebView that any app can use, which makes it easy for developers to display webpages without actually having to build an internet browser into their apps. But WebView is a stripped-down, bare bones browser with no ties to Android's default browser, Chrome, so none of your synced data like bookmarks, passwords, and history is available when an app is using WebView to display a page.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

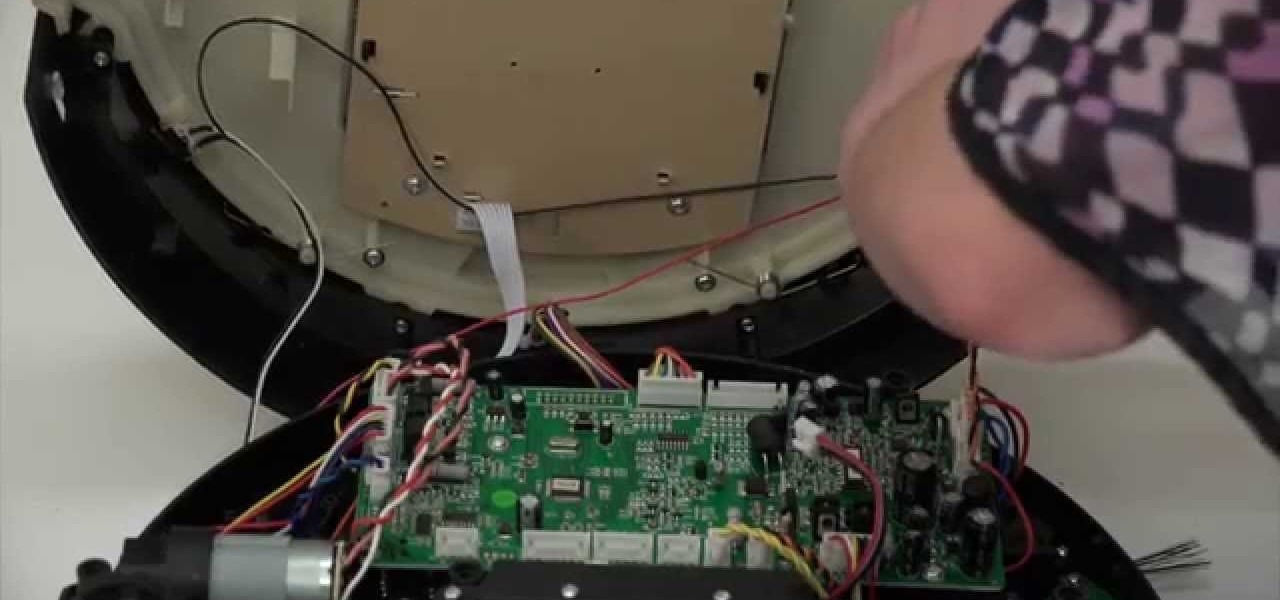
A step-by-step guide to replacing the side brush motor on bObsweep Standard or Pethair. Follow the video or multimedia directions in order to open up bObsweep, remove the main board, replace the side brush motor, then close your vacuum for future use.

Everybody loves the stars. Well, I certainly do. As a child I'd spend hours outside during summer nights marveling at the seemingly endless amount of sparkling dots spanning the sky. Maybe you have children of your own and want to create a sparkle in their eyes, or in your own. This tutorial will provide a basic method of bringing the stars inside—at least, in part.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

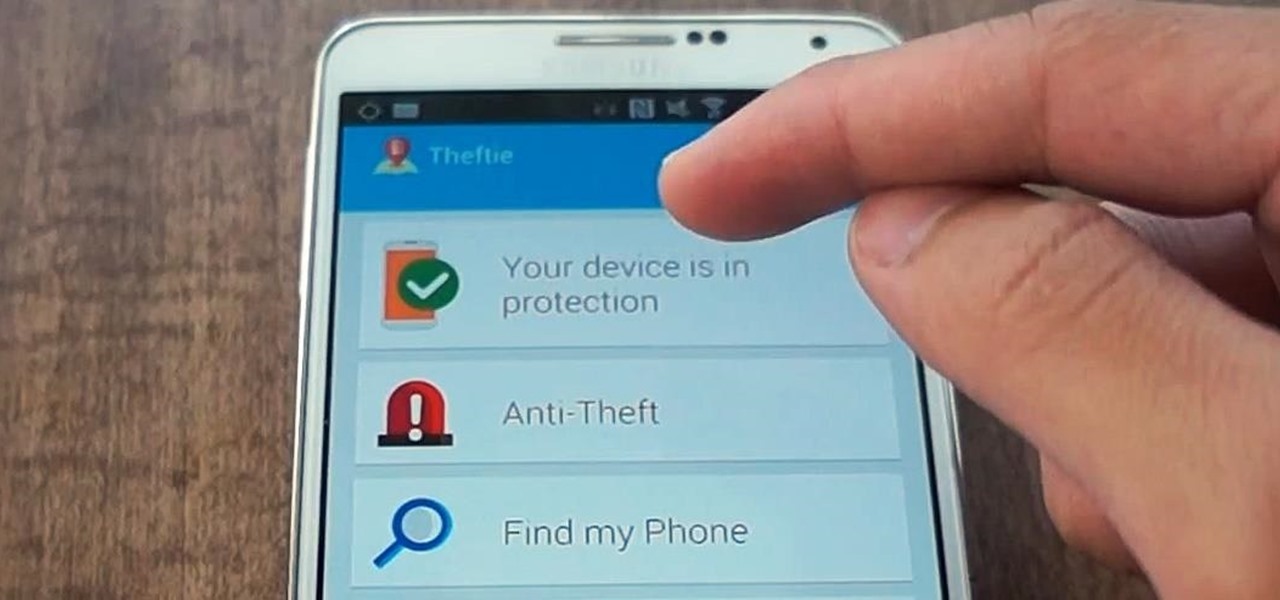
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

There's a lot of personal information residing on your phone, possibly even more than on your computer, so it's only a matter of time before someone tries to access it.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.