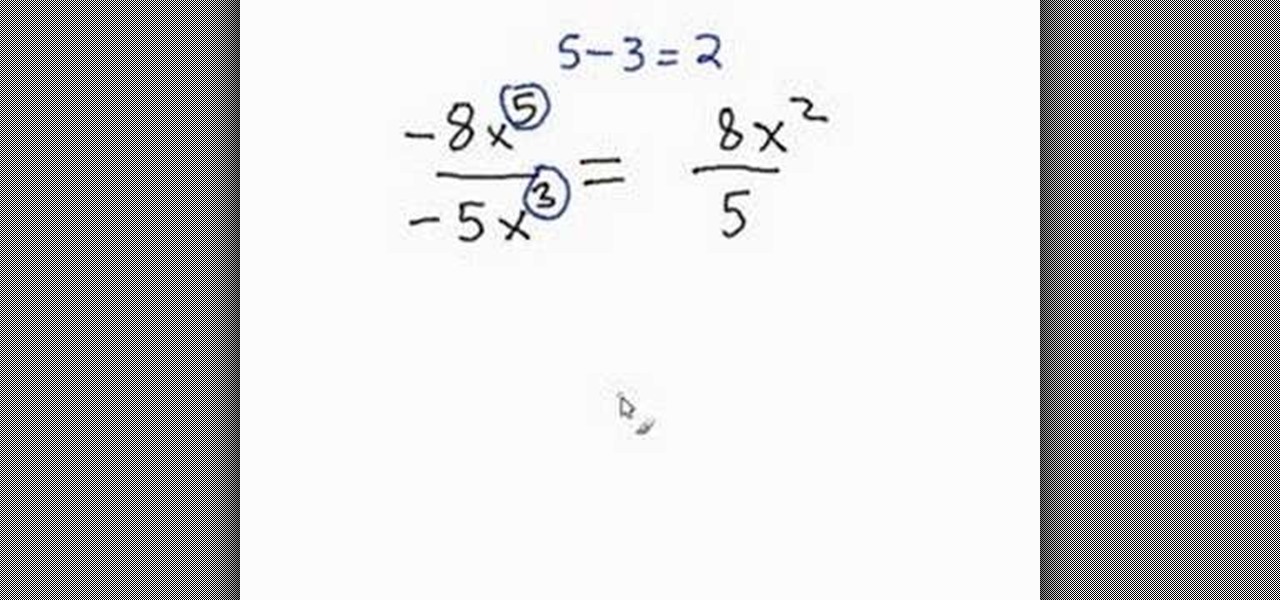Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.
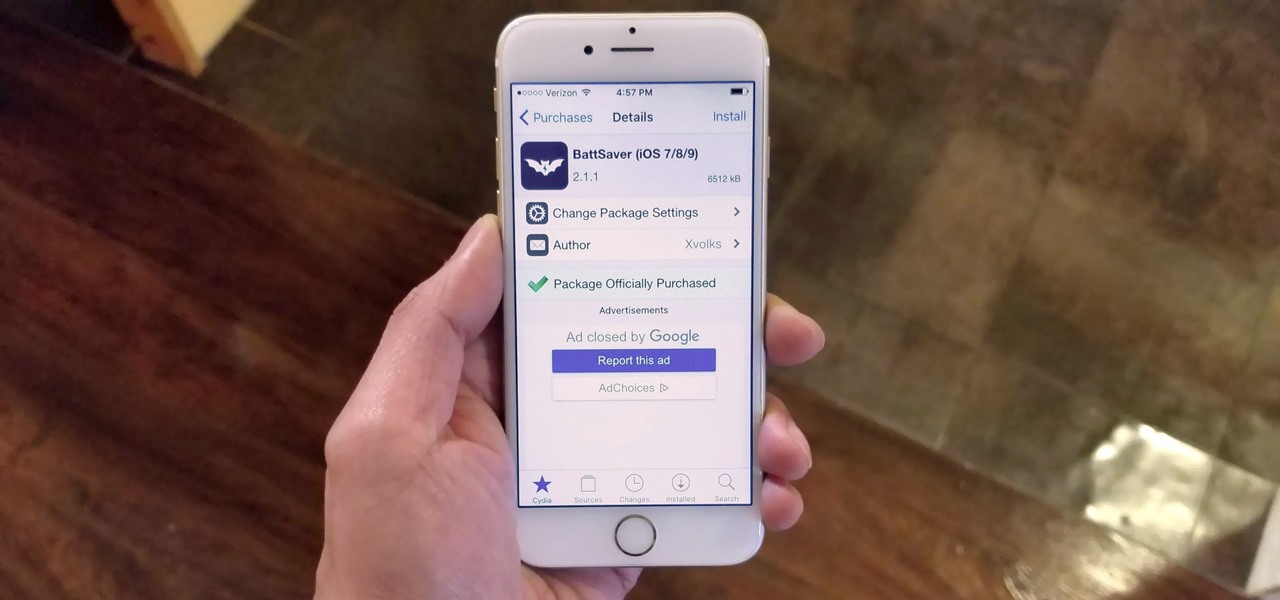
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

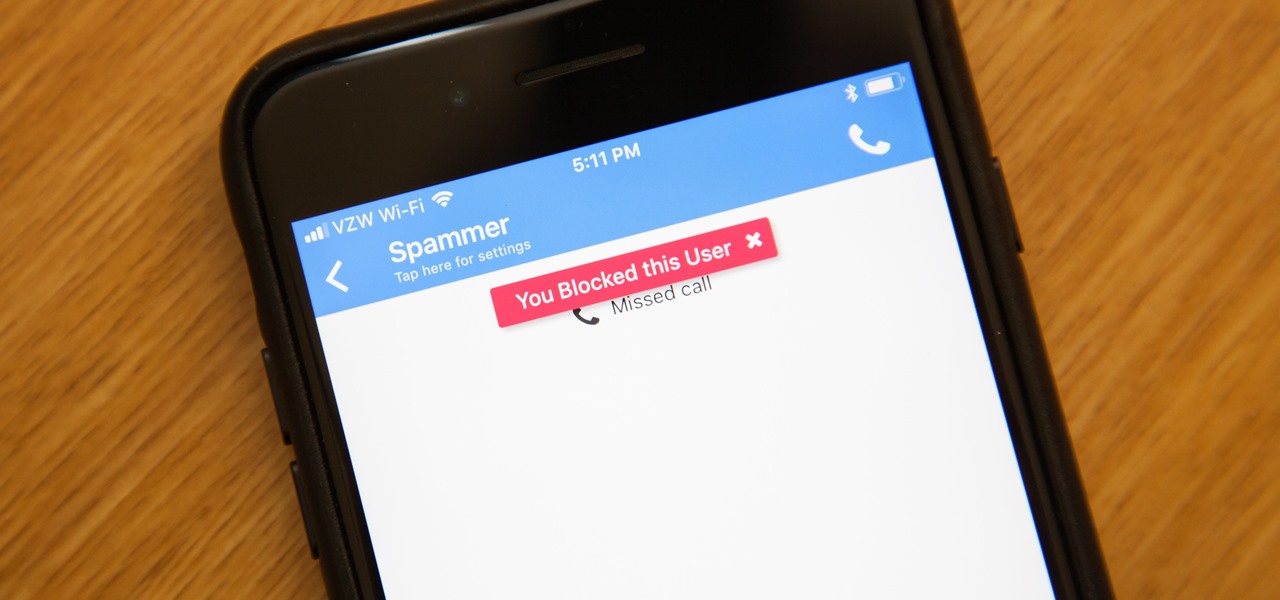
While it's a more secure platform for messages and calls, Signal's job isn't to prevent unknown users from contacting you, so you run into the same issues you would with a regular phone number. People you know that you don't want to talk to may try to strike up a conversation and you'll still get spam messages. Luckily, it's easy to block these suckers.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

One shrinks their nose when the name of Durian fruit is brought up but are you aware of all the health benefits it can provide? The Durian fruit on its own can help control Blood pressure, blood sugar, Anaemia and depression. Not only this, the fruit has the miraculous qualities that can prevent cardiovascular diseases, better the digestive system, better the Libido and provide instant energy. For all the skin conscious people, here's news for you! The fruit can delay ageing process and make ...

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

If you're as bad at locking your Nexus up as I am, you have the "slide" option set for your screen lock. It may not be the most secure option, but it's definitely the easiest way to unlock your device while being able to utilize lock screen widgets.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Nine times out of ten, when you pick up your Samsung Galaxy Note 2, you already know what app you're going to be using. If you only have Swipe to unlock enabled, finding that app is as easy as swiping and locating the app on your Home screen or in the app drawer.

I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

Bacon is the cornerstone of many comfort food combinations: Baked potatoes topped with bacon bits, bacon served alongside a biscuit and eggs for breakfast, bacon burgers.

In order to format graphs and charts using Microsoft Word 2007, click on Chart Tools. The tabs at the top of the screen provides you with your options. You can change the type of chart or graph by clicking on Change Chart Type. If there is a particular type of chart that you would like to use again and again, then you can save it as a template via the Save As a Template icon. You can edit the data in your chart of graph by clicking on Edit Data. You can modify the chart layout by clicking on ...

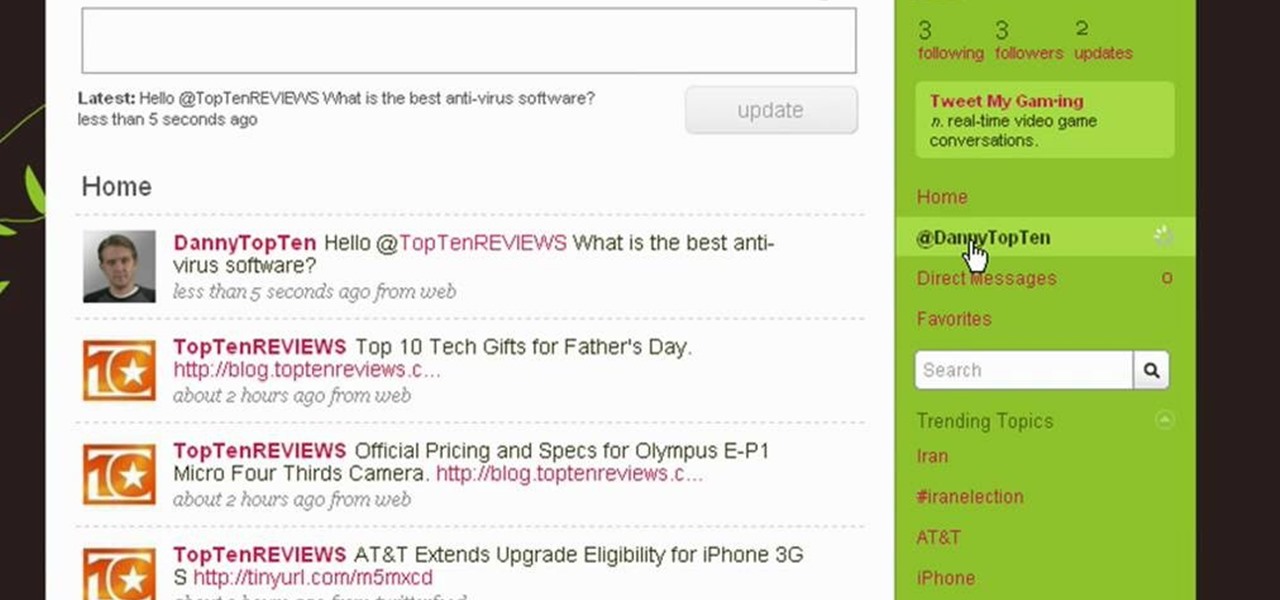
Twitter is a powerful social networking website which can be used to update you friends on what you are doing. To send different messages through twitter you will need a twitter account. Twitter account can be registered for free. Log in to your twitter account and go to your home page. There is a text box provided at the top with the text 'What are you doing?'. Enter the message you want in the text box provided. Click update and this message will be shown to all the people that are followin...

Gourmet editor, Ruth, tells us all about the different graters and why choosing the best grater for each job is very important. The classical grater is called a knuckle bleeder. This is because when you're at the end of the item you're grating, you have to get your hand really close to it and you might scrape your knuckles. The hand grater is easier to use and provides smaller pieces which makes it ideal for most grating jobs. A zester grater is also easy to use and provides more volume than ...

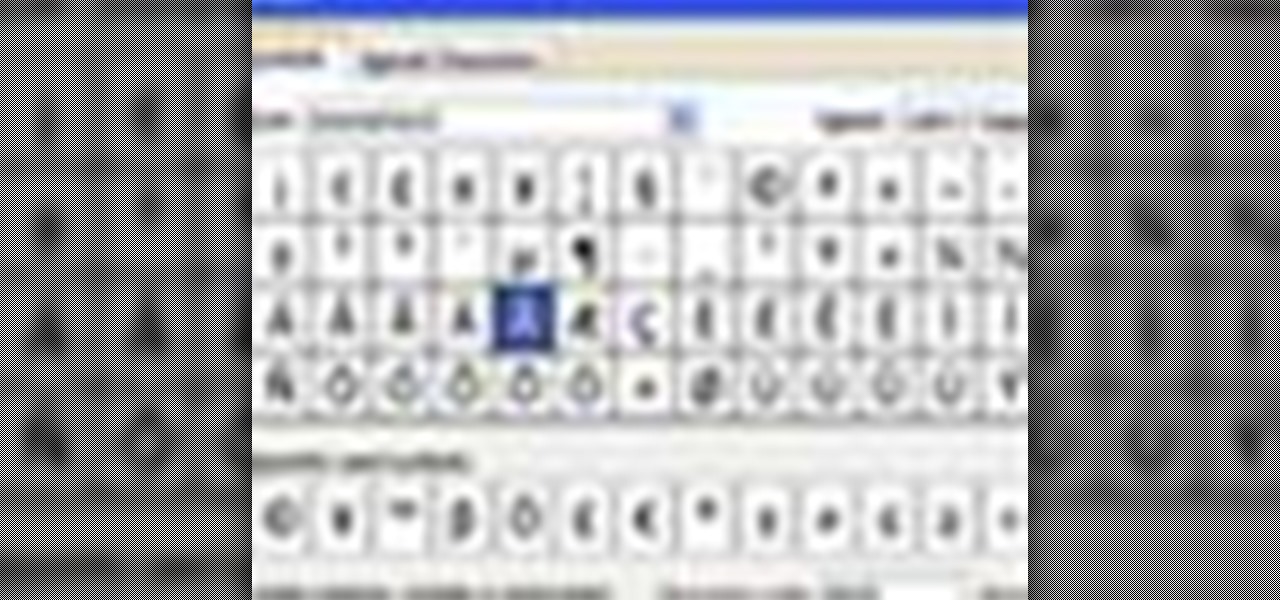
A video from Helpvids.com that shows how to insert special characters in MS Word 2007. A seldom used function in MS Word is the Insert Symbol function. Symbols like the copyright, infinity, registered trademark, Yen, Pound, Euro etc can be of use in some documents. Word provides an easy way to insert these and many other such symbols into your documents without much hassle (For example, using the Character Map utility provided with Windows).

In this video tutorial, viewers will learn how to make two pairs of simple earrings. The video provides all the materials required to make the earrings. The materials required include: freshwater pearl disk, 4 mm Swarovski crystal, bally bead accent, 2 mm silver bead, head pin, flat nose pliers, round nose pliers and wire cutter pliers. This video provides step-by-step instructions and a visual demonstration for viewers to easily understand and follow along. This video will benefit those view...

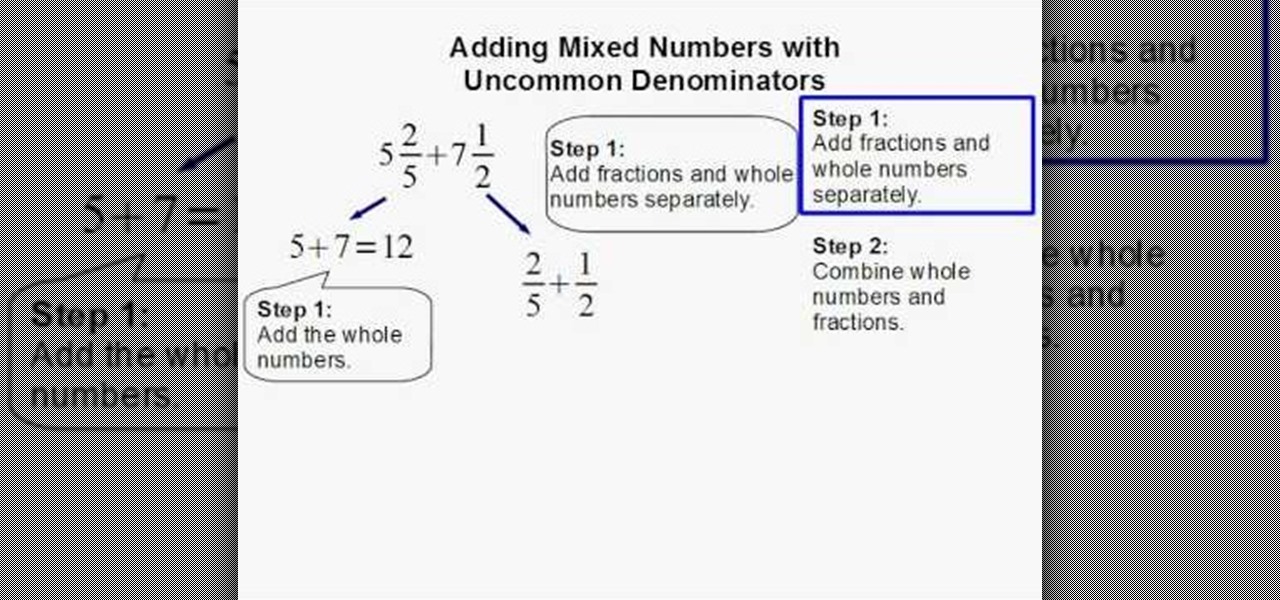
How do you add mixed numbers with uncommon denominators? Well, this video provides a detailed step by step explanation as to how to go about such problems. It also provides an example and applies the required techniques to acquire the solution. The video is very precise in its instructions and does not skip any steps. Therefore, the viewer should have absolutely no problem understanding the concepts behind adding mixed numbers with uncommon denominators after viewing this simple and helpful v...

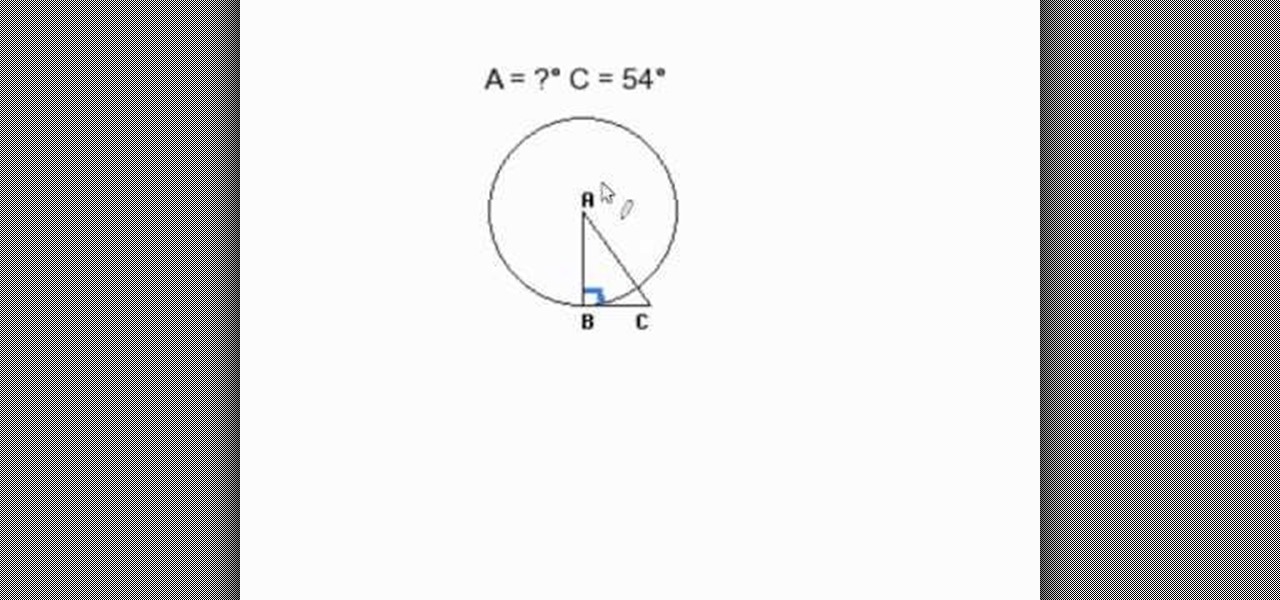
mathproblemgenerator.com provides a video about how to find a central angle with a given radius and a tangent. The angle at the intersection of the radius and the tangent is equal to 90 degrees. The second angle is also given in the problem. So the central angle is equal to 180 minus (90 plus the other angle given). In the video, the given angle is 54 degrees, making the equation = 180 - (90 + 54). Therefore the central angle is equal to 36.

This is a helpful video provided by Math Problem Generator. It deals with the complex challenges of dividing variables. The audio is great and provides specific examples of dealing with multiple types of this problem. The video lays out three simple steps. The first being to simplify the coefficient, the second being to divide the variable, and the third being to deal with the results of the division. The information is clearly presented and best of all it's free. I think we all wish there we...

Lowe's home improvement expert, Mike Kraft provides a step-by-step method for changing the oil on a walk-behind lawn mower. From assembling the proper tools and supplies you will need to complete the task, through disconnecting the motor for safety, through the proper drainage technique and finally refilling the crank case this video gives complete instructions for any mower maintenance. Changing the oil on your mower will extend its life. Following the steps in this guide will provide you wi...

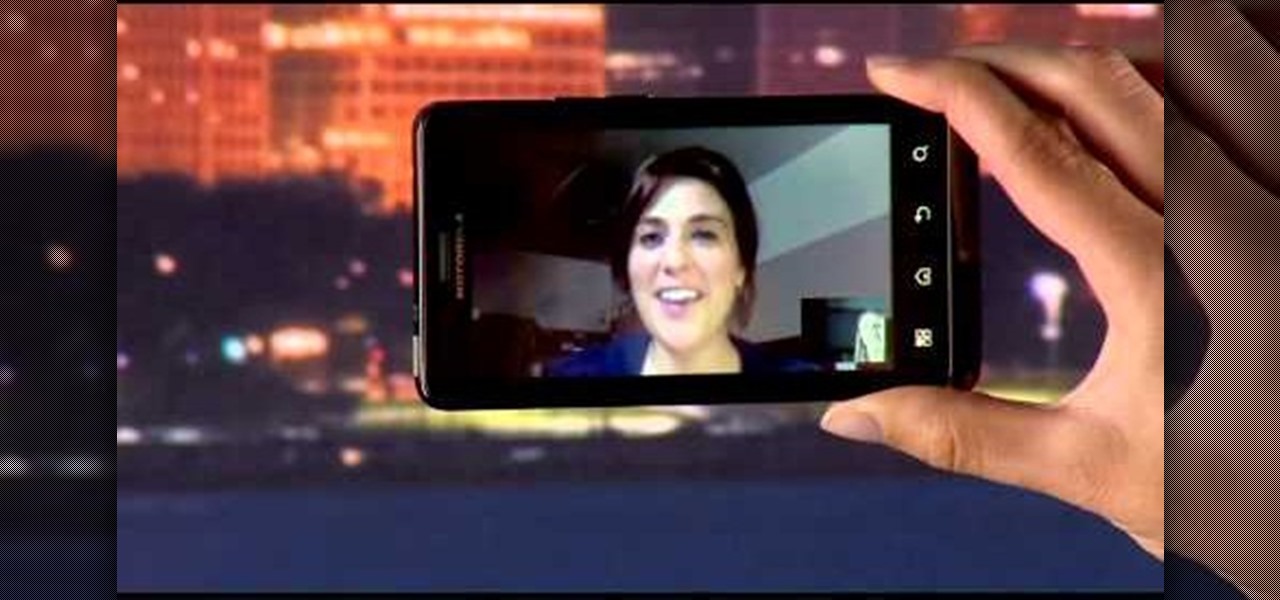
The front camera on the Droid Bionic from Motorola is a perfect match for the Google Talk application provided with the Android smartphone. Using the Verizon Wireless 4G connection, you can stream video and voice to friends and family members on the go. This guide by Motorola demonstrates how to video chat on the Bionic.

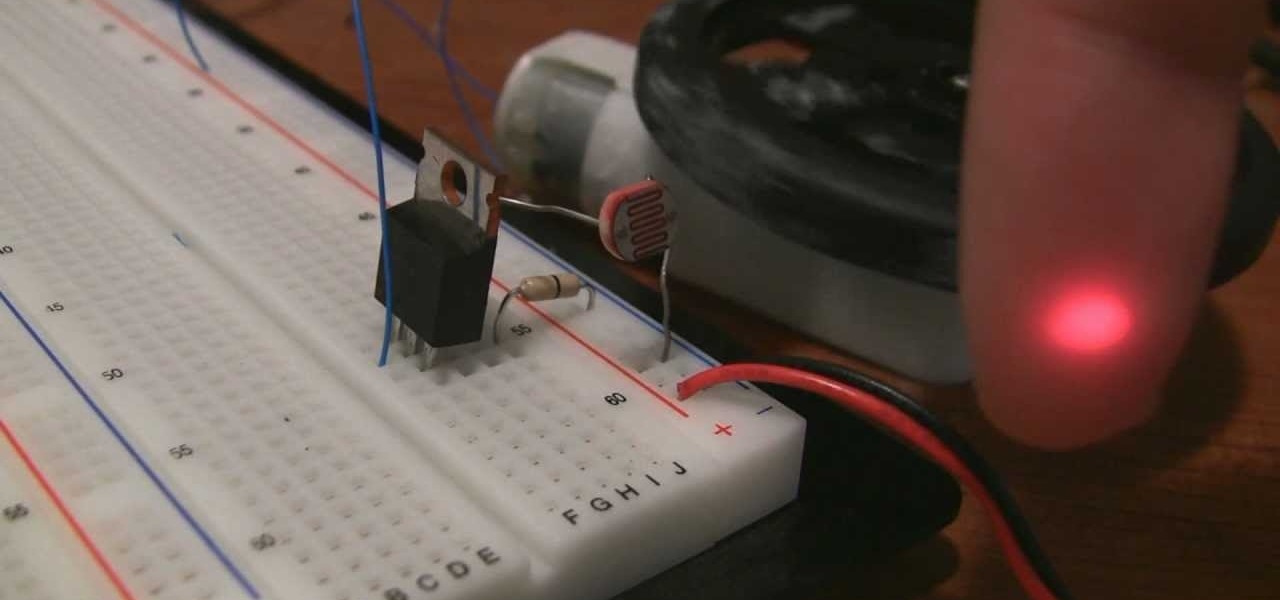
This video, incredibly short for it's massive content, will teach you how to make a laser tripwire that, combined with a photoresistor, can trigger just about any device. You can make traps, alarms, awesome party decorations, and all sorts of other awesome things with this easy-to-make device, provided you have a soldering iron and a local electronics store to buy some parts.

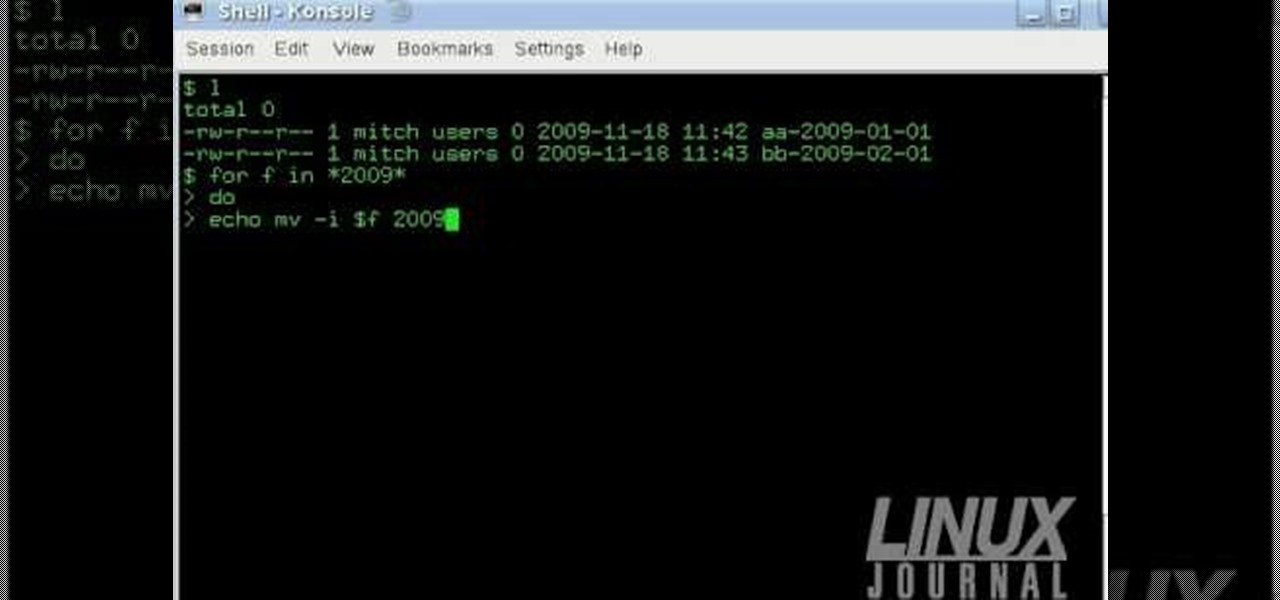
The Linux command shell provides a very powerful interface for doing various system tasks. This video explains with an example, how to use a bit of programming techniques to batch rename files with similar naming conventions.