When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

Dreaded are the days when you're working on a masterpiece, then all of a sudden, your Windows computer crashes, loses power, or an app just gets up and quits. Well, now there's an app for that.
Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week.
Blue light (like that from our smartphone) tricks the human brain into thinking it's still daytime, even if it's coming from something as small as a screen. So while you're playing around with your new Pixel or Pixel XL after dark, subconscious signals to be awake are preventing you from getting to sleep as early as you should.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

The most genius summertime snack hack that we've come across recently is, without a doubt, the campfire cone. Astounding in its simplicity and ease of preparation, yet brilliant in its execution, the campfire cone has something for everyone: parents and children, expert and novice campers, backyard barbecuers, and oven lovers alike.

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

When Android Nougat is released sometime this fall (or sooner), a new feature called "Quick Reply" will allow users to respond to incoming text messages directly from the notification. It will definitely be nice to carry on a conversation without leaving the screen you're currently viewing, but unfortunately, most of us won't get that Android Nougat update for quite some time.

Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested their method on a Samsung Galaxy S6 and Huawei Honor 7.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

Five Phases of Hacking:- The five phases of Hacking are as follow:

A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

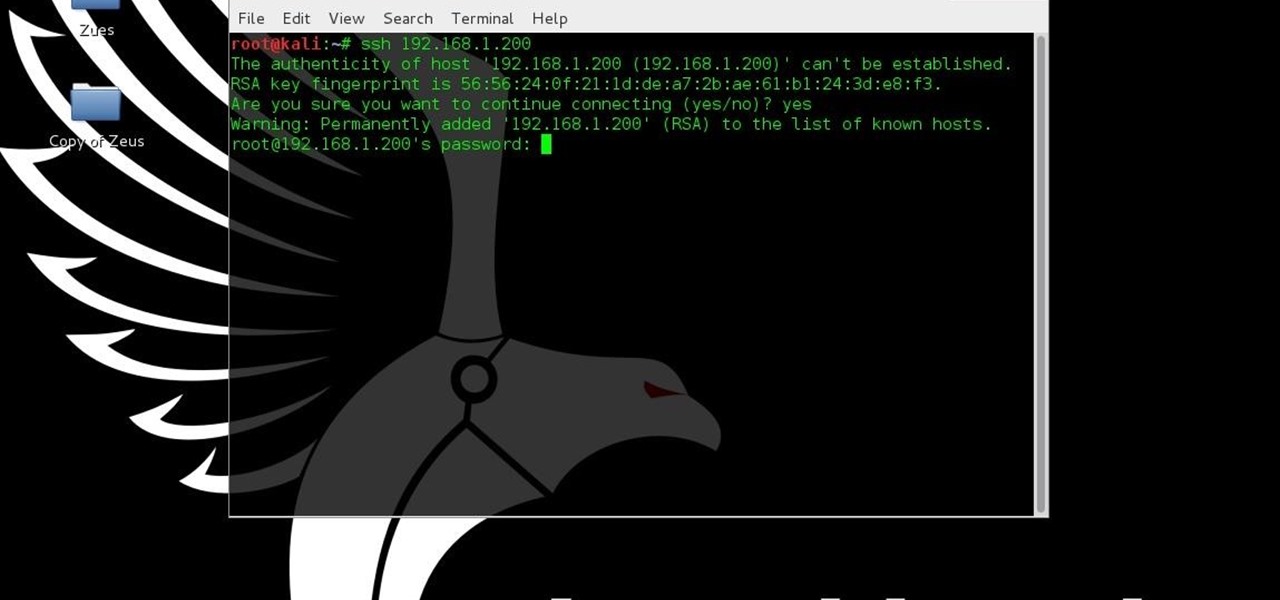
I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Thanks to the internet and its increasingly lack of privacy, secrets don't even seem safe in our own homes anymore. So how do you hide your secrets, stash your cash, or keep your valuable jewelry out of sight where no one can find it? Well, the answer might be right above you... if you're standing under the threshold of a door, that is.

Raw fruit "cakes" are all the rage these days, and this stacked watermelon cake is easy to put together and is perfect for people of all ages. It's also perfect for every diet, as it's low-calorie, low-fat, gluten-free, and full of "good" carbs.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

Your Apple Watch only looks as good as the band that it's bound to, but if you're looking to purchase one directly from Apple, expect to spend anywhere from $149 (for the Milanese Loop) to $449 (for the Link Bracelet).

Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, there may be some additional improvements on your list that you can take care of on your own. Here are five quick improvements you can check off your list before the big move.

They might be a little late to the party, but the Cyanogen team has finally released their newest ROM for the OnePlus One, Cyanogen OS 12. The launch had to be pushed back a few times due to some technical issues, but now we finally get to see what the Cyanogen team has cooked up for Android Lollipop.

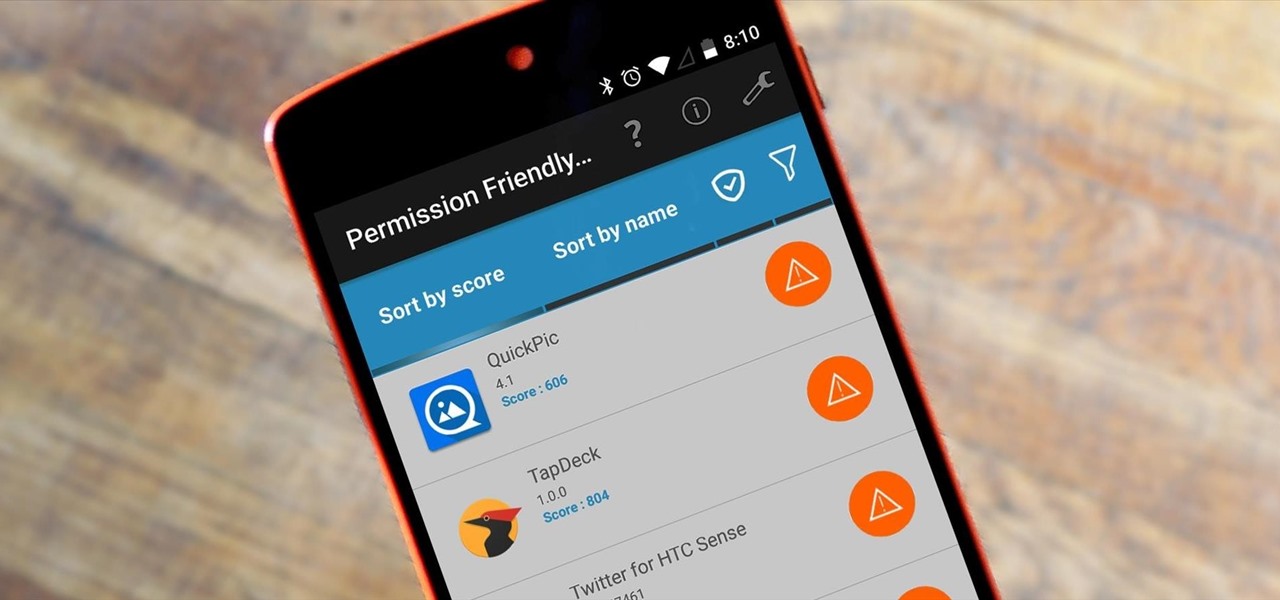
Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at all.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

The weather outside might be frightful, but heating bills are downright scary this time of year. Heat is absolutely essential during the winter season, but it's also really expensive. If you aren't blessed with a fireplace or unlimited disposable income, fear not, because you can still heat your home on the cheap using flower pots and tea lights—even if the power goes out.

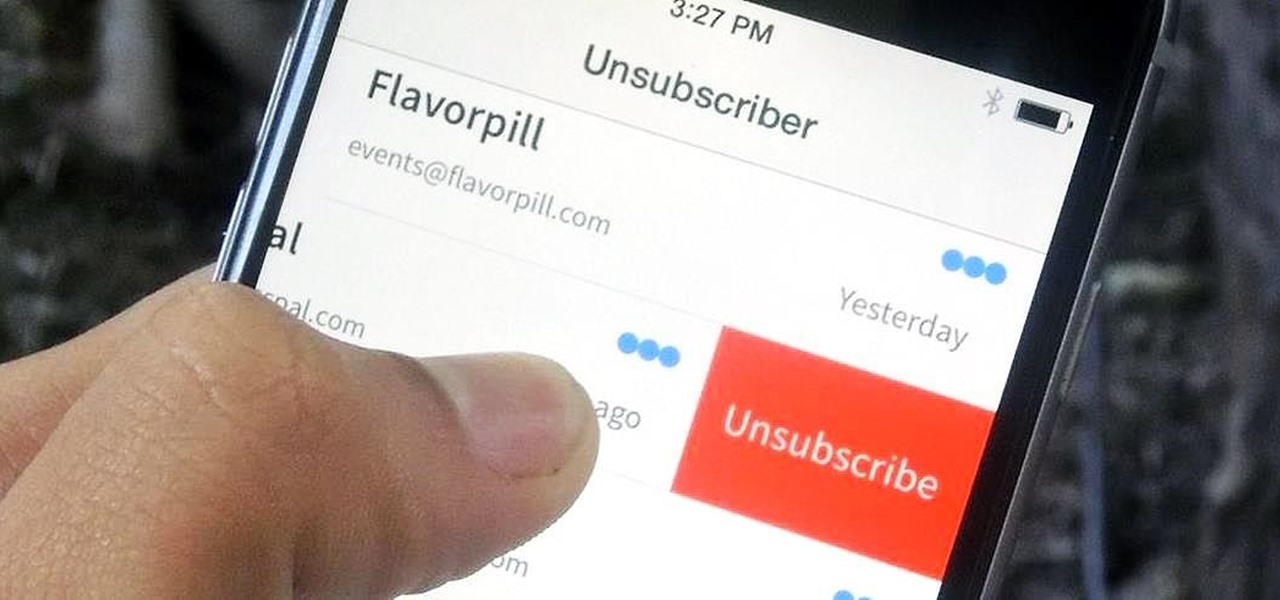
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.

Whether you use a third-party keyboard or the stock offering, your Samsung device keeps a history of the last 20 words you copied on its clipboard. Samsung added this feature to Android to help make multitasking a bit easier, but if you use a password manager like LastPass, this feature quickly becomes a gaping hole in security. While you're copying and pasting your various passwords, the last 20 of them become freely available to anyone that gets their hands on your device.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

Since the days of Friendster and MySpace, social media platforms have taken leaps forward, revolutionizing how we live our lives by changing the way we communicate with others. Not only has social media become a catalyst for major uprisings around the world, but on a personal level, it connects people together in ways that were unimaginable even 10 year ago—no one was taking pictures of their brunch to share with the world in 2004.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

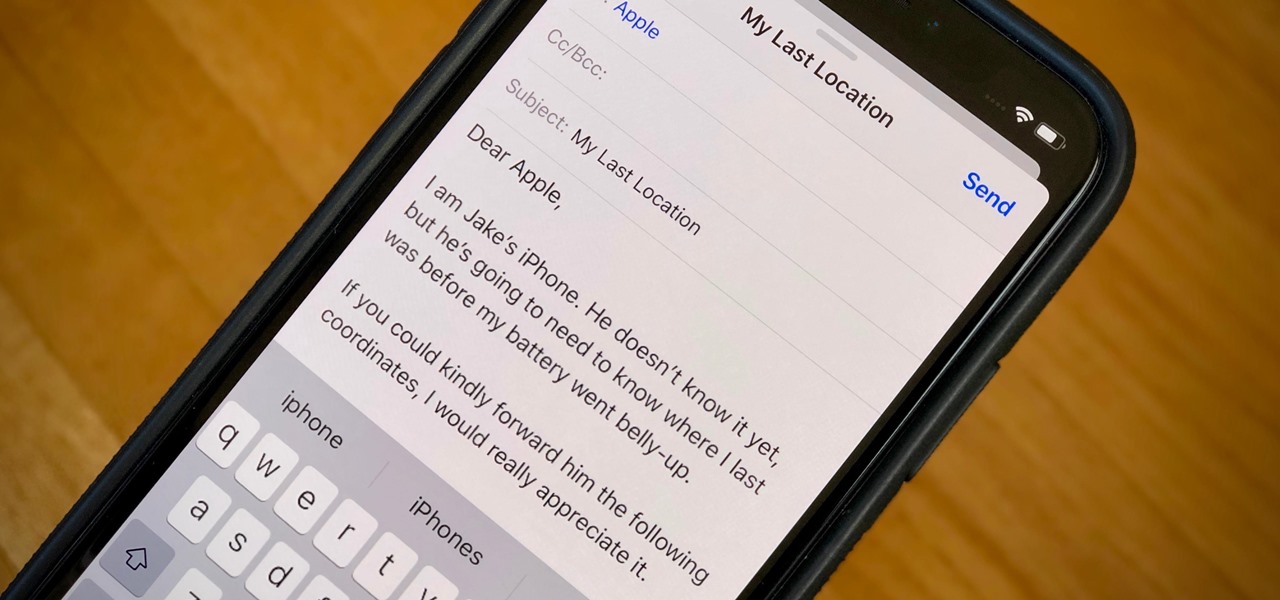
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

Being healthy and active will help you live longer, but finding the strength to work out? That's hard. What does it do for me right now? I mean, here I sit, writing this article, thinking about going for a run, and I feel good just for thinking about running. But will I do it? Nah, I'm too lazy.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

One of the coolest features of the Galaxy S5 is its IP67 certification. This means that the S5 is internally impenetrable to dust and can be submerged in water for thirty minutes at a depth of one meter. It's definitely a handy feature for folks who've lost a phone to a toilet in the past.

There are over one million apps in the Google Play Store, and many of them are restricted to certain device types, brands, and Android systems.

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.