
How To: Tie a tie with the 'Nicky' knot
The "Nicky" is related to the "Pratt" and provides an excellent compact, medium sized symmetric knot. The "Nicky" is a very practical knot which can be used with most any tie.


The "Nicky" is related to the "Pratt" and provides an excellent compact, medium sized symmetric knot. The "Nicky" is a very practical knot which can be used with most any tie.

DIY Guide to building a birdhouse. This easy to make bird box can be built in 1 day out of one 6 foot long 1" by 6" plank of cedar. Attract more wild birds into your garden (or provide for those already there).

Watch this guide to the adductor muscles. This video provides professional advice on massaging techniques for the abdominal muscles. After some physical exercise, there's nothing better then a relaxing massage.

For the urban artist, this video shows how to leave your own personal touch to whatever you desire via a sticker. While there is no verbal instruction, the music is relaxing and the text messages provide clear directions. Get out there and make your mark!

Franklin Crow teaches you about edge bevelling. Depending on the terrain where you snowboard, you want to bevel your edges to provide the best riding experience.

Using an egg yarn dispenser provides more consistent results, is quicker, and results in less material waste than tying egg patterns without a dispenser. You can use a drinking straw, the empty shaft of a ball-point pen.
Adobe Photoshop's Magic Eraser Tool provides you with a quick and easy way to change a pictures background or other color area with just a few clicks.
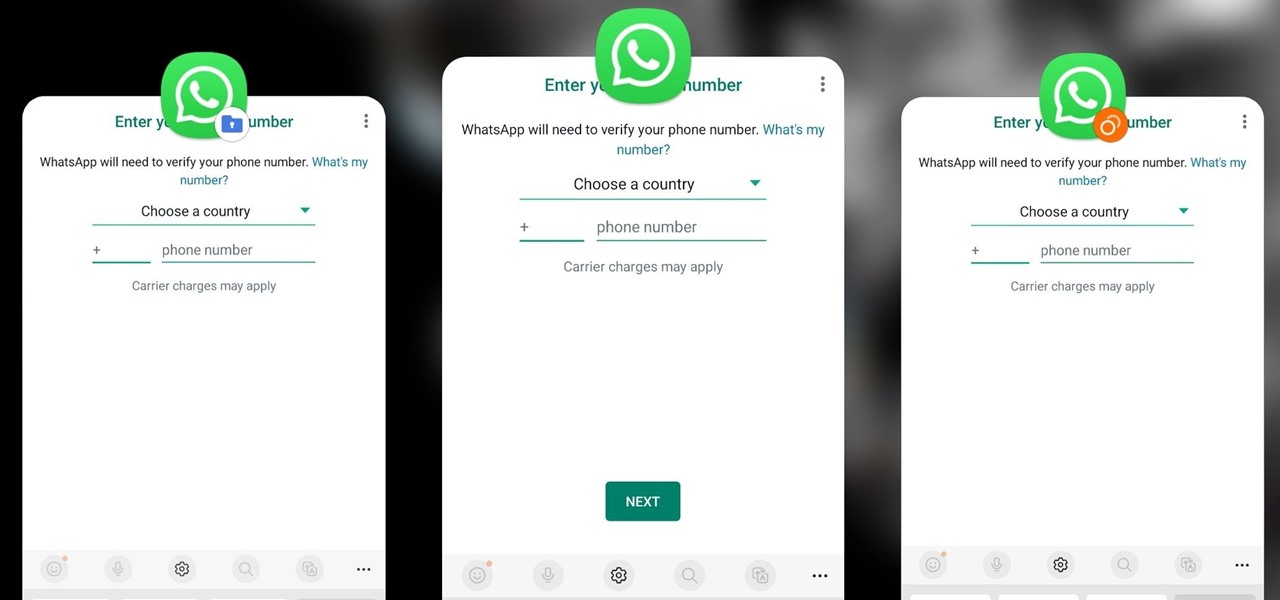
Samsung has a cool security feature built into One UI that has an interesting side effect, one that lets you have two separate copies of any Android app on your Galaxy phone. And that's not the only integrated Samsung tool for cloning apps.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.
With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.
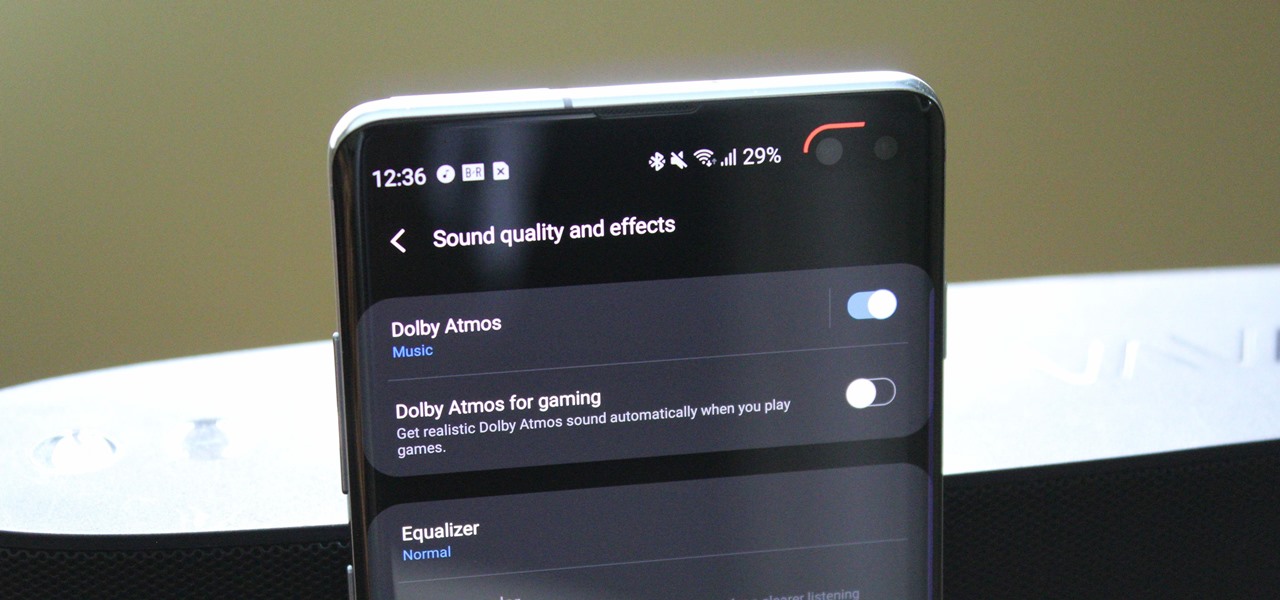
While the audio experience is solid on Galaxy phones, it isn't the absolute best out of the box. That's because Samsung has partnered with Dolby Laboratories to provide its industry-leading sound technology known as Dolby Atmos, but it's turned off by default. Once enabled, your audio experience will go from good to great.

As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and ensure you're insulated from any potential liabilities that may appear down the road.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

While Huawei smartphones haven't always been the best choice when it comes to custom ROMs, one thing that has always been accessible is the ability to unlock the bootloader. An unlocked bootloader is the first step into the magical world of rooting, but after May 24, Huawei will stop offering this service.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.
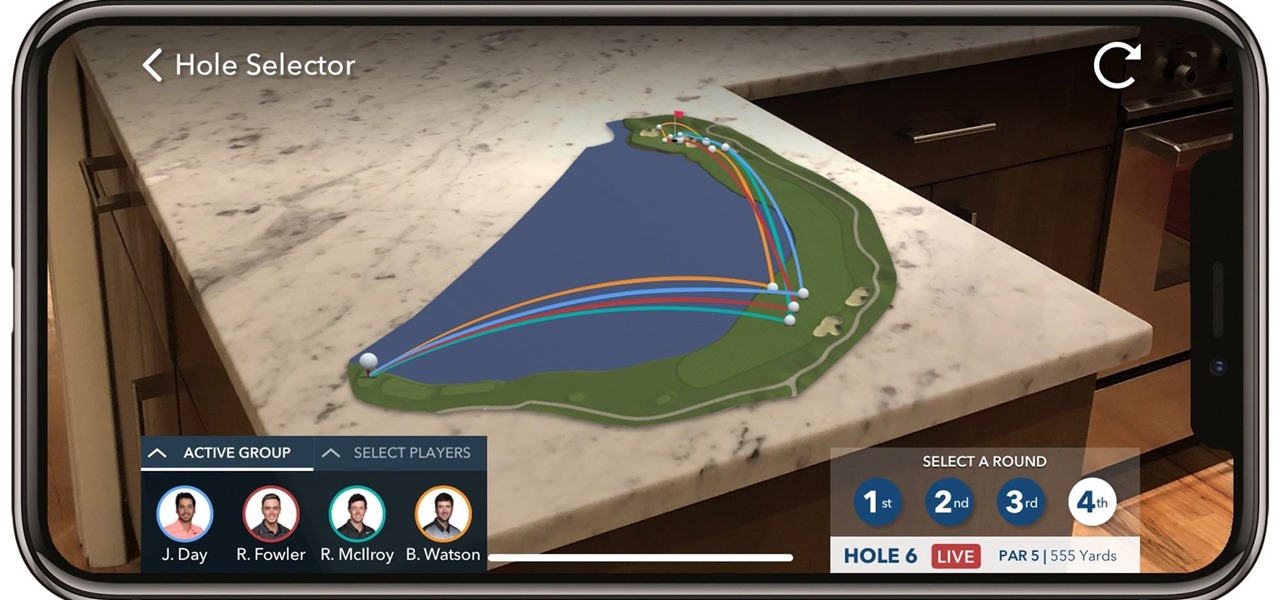
If you're a golf fan who can't attend the Arnold Palmer Invitational in person, you can still follow the next stop on the apparent Tiger Woods comeback tour in augmented reality with an iPhone or iPad.

Location services provider Mapbox is giving developers a means for building location-based AR apps and multi-user experiences with its new Mapbox AR toolkit.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

"I'm Rey." That's what a lot of people will be saying again this Halloween, as Rey costumes are sure to be another favorite of trick-or-treaters and cosplayers. Yes, on Oct. 31 we all have a chance to be the scavenger of Jakku who just so happens to be the "new hope" for a Jedi renaissance.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.
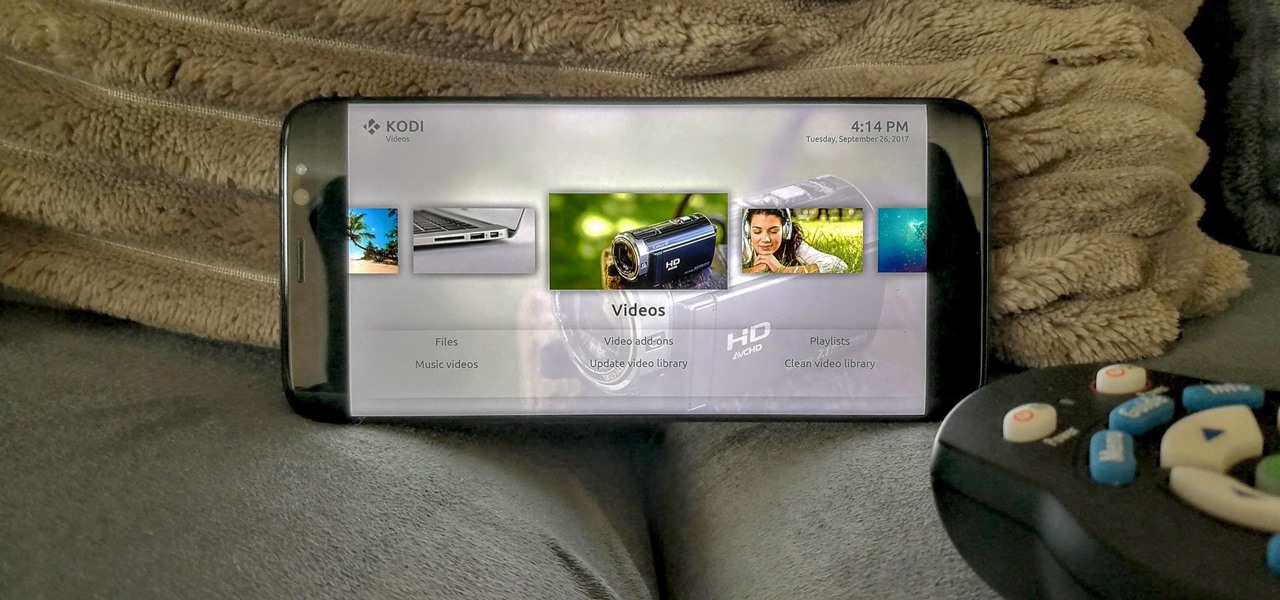
When you first use Kodi, it can be intimidating. The main menu has numerous options for the various types of media Kodi can play back, and the settings menu has a broad array of tools to customize Kodi to your needs. After poking around in theses menus, you might realize that you don't like the default look. But whether it's the color, font, layout, or just the general theme, Kodi skins can change it all.

The new iPhone X will be released on Friday, Nov. 3, in Apple Stores located in over 55 countries and territories. For those of you who would rather skip the in-stores lines that will start building well before the 8 a.m. local time openings, you can preorder the iPhone X on Friday, Oct. 27, starting at 12:01 a.m. PDT.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

More platforms and more tools to make content for those platforms. It seems like the Dev Report —Next Reality's breakdown on the latest information on tools and processes to make augmented reality experiences — is going to be coming out on a much shorter cycle.
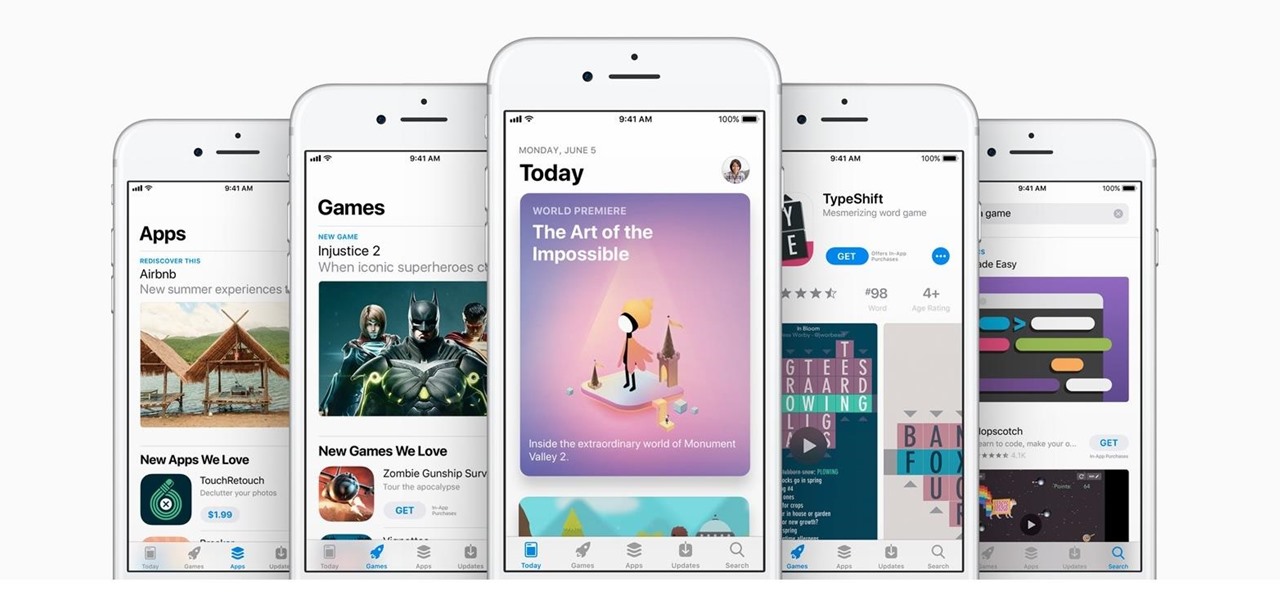
In the changes to the App Store Review Guidelines for iOS 11, Apple has announced that developers must use the App Store rating API. The API was introduced in the iOS 10.3 beta period as something that would eventually become mandatory. Now, Apple has followed through on that promise.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

If you're an Apple user and want an untethered virtual reality system, you're currently stuck with Google Cardboard, which doesn't hold a candle to the room scale VR provided by the HTC Vive (a headset not compatible with Macs, by the way). But spatial computing company Occipital just figured out how to use their Structure Core 3D Sensor to provide room scale VR to any smartphone headset—whether it's for an iPhone or Android.

Among the many new changes ushered in by the iPhone 7, only one has the potential to completely change the way you interact with your smartphone—a new 3D Touch-enabled home button. Instead of the mechanical click we've grown accustomed to, your home button will now behave like the rest of the phone's touch screen interface.

Most popular virtual reality headsets, like the HTC Vive and Oculus Rift, require a tethered connection to the computer and that imposes some obvious restrictions on how much we can move in our space. We'd all prefer a simpler, untethered option, and Intel wants to provide just that.

The headsets of tomorrow offer some amazing possibilities in both gaming and work, but what we've seen so far only begins to scratch the surface. The US Navy saw the potential to use augmented reality in a helmet to provide divers with an incredible amount of information we have so far only seen in Hollywood movies.

As exciting as it can be to crack open a beer, there's nothing fun about wandering around a party and asking other partygoers for a bottle opener.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.