Ever wanted to learn how to make a rekey a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... key making. Just watch this video tutorial to see how to properly make a replacement key for a lock.

Don't know the combination to your lock securing all of your important gym socks? Maybe you just want to impress all of your friends by hacking a combo lock? Whatever the reason, this instructional hacking video will show you how to open a lock with a soda can shim the easy way.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

For roasted chicken, you would expect it to have a nice, brown crispy skin. You would expect it to be moist inside with great flavors throughout. By using the rotisserie function (very common in France) on the Cuisinart Brick Oven. Check out the recipe for this delicious herb-roasted chicken from Chef Hubert Keller.

For this hijab style, start with hair completely covered and a large rectangular pashmina scarf. Pull the scarf over the head with one side hanging longer than the other. Pull the scarf tightly over the forehead to the nape of the neck and pin it together at the nape. Take the shorter end of the scarf and tuck it back toward the nape of the neck. Then pull the long end under the chin and up around the head until it is tight. Secure the end with a pin. Earrings can be worn through the scarf as...

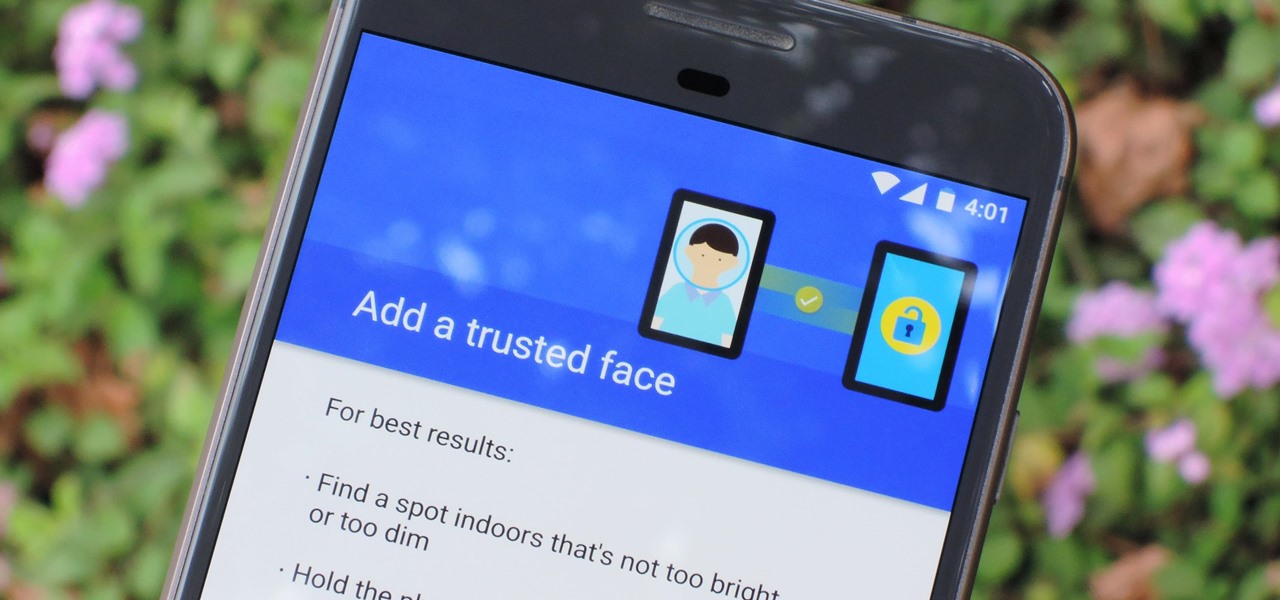
When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

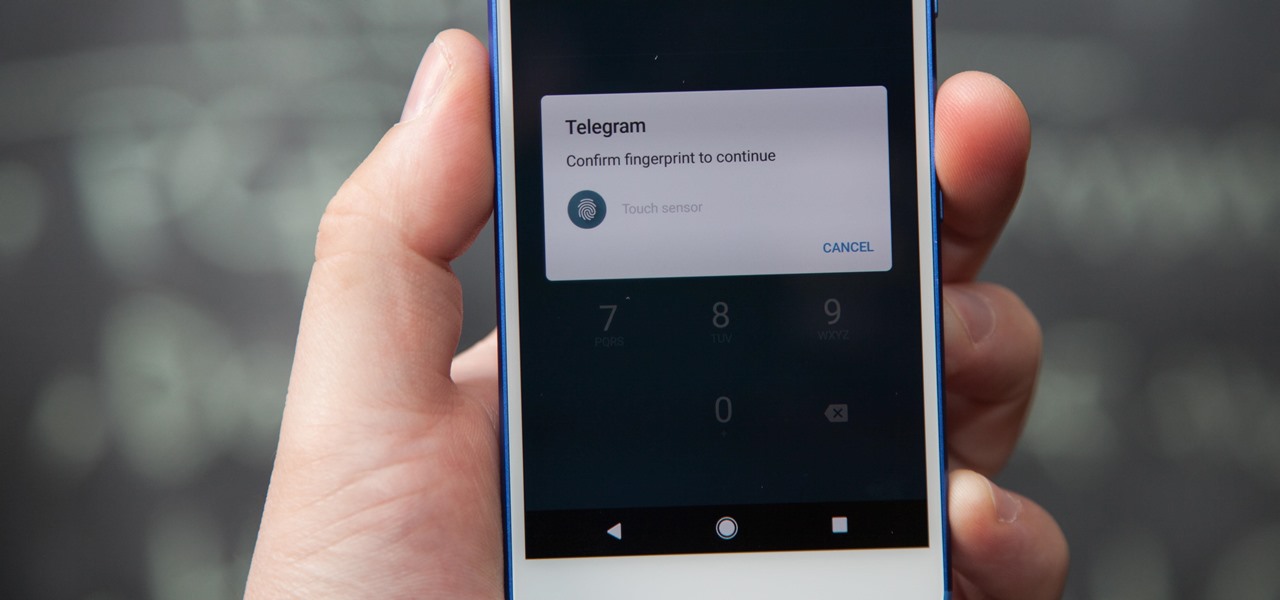
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

Welcome back, my greenhorn hackers!

Over time, the dryer belt can become hard and brittle when the drum is turning loud noises such as squeaking, squealing or thumping noises can occur. Replacing the belt is an easy task for the do-it-yourselfer. All that’s required is a few simple tools. Here’s a step-by-step guide to help you install a new belt in your dryer.

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

The narrator starts by explaining what a squash book is. A squash is designed to keep photos, journalling or what ever you like. To start we require a 4x4 pattern paper and 3x3 chipboard. We then glue the chipboard onto the pattern paper. We then cut the corners of the pattern paper. We then fold the flap in and glue down. We repeat this to form another cover. Next we grab a 6x6 pattern paper, we then complete a series of folds. One diagonal, half horizontal and half vertical folds. We repeat...

To create almost any headband look, start by using a real human hair headband with extensions. Mostly, the extensions will come with an interchangeable headband for different colors. Now, start by pinning back the front crown area of your hair, if you have bangs you can leave them out of the hair that you are pinning back. Secure the crown of your hair with bobby pins. The headband with extensions should have three little combs. These will help secure the extension and the headband onto your ...

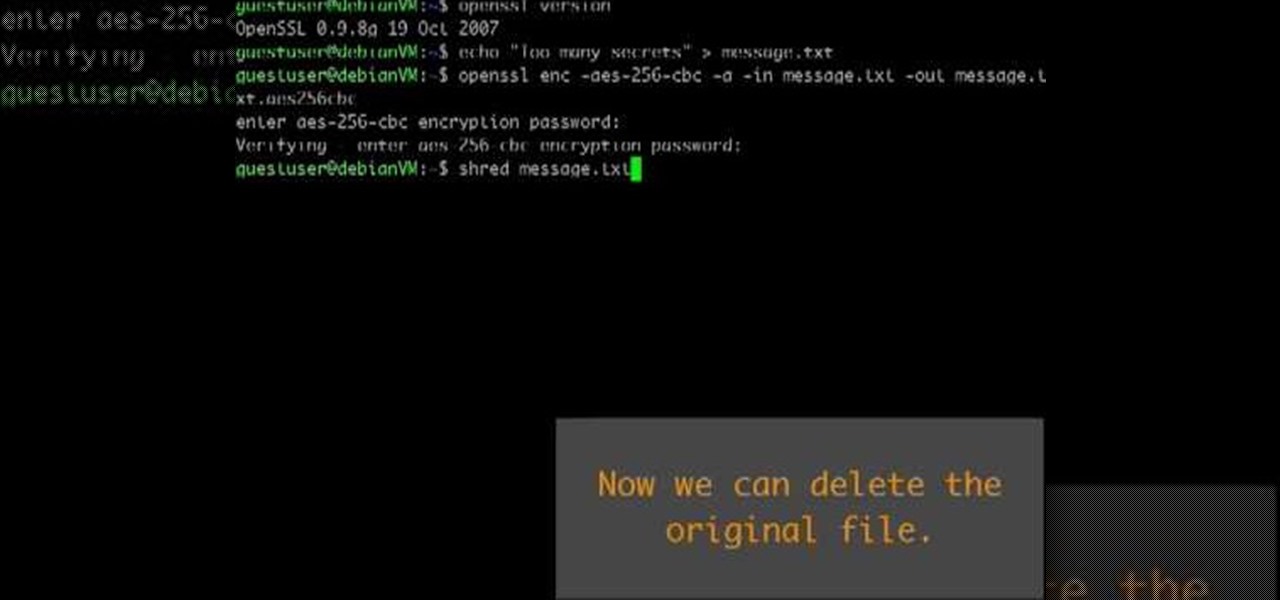
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

Cocorais shows you how to style your hair into a Selena Gomez style up-do with short hair. Start by curling your hair, which is optional but it gives the hair shape and volume. Take your curled hair and sweep it to one side (opposite side of side-part if you have one), leaving a little hair on the other side to frame your face. Ignore any hanging hairs. Comb your hair into a ponytail, and tie it to one side. Gather your hair and tie it into a bun, using bobby-pins to secure it. For the rest o...

Learn how to tie a perfect bow. To do a basic pony bow, place the gathered hair in the center of the ribbon and tie a single knot to secure it. Making two loops, cross one loop over the other and pull the loop on top through the hole you've created. Straighten out the ends and tighten so the two loops are on top and the two tails on bottom. Make a headband bow. Run the ribbon along the hairline, drawing the ends up on top of your head. Secure a knot and tie a bow. By tweaking the loops out a ...

This video teaches the viewer how to make a memo book with a paper bag. For this craft you will need two paper bags, memo paper, adhesive, ribbon, and scissors. To begin, you'll need to cut off the bottom of the bag and discard it. She explains where to make decorative edges on the bags before sewing them together or using hot glue. Fold and crease the open end down about one third of the way. Open and then fold a little farther down to allow room for the spine of your memo book. Repeat this ...

This video shows you how to use couplers for cake decoration using these steps: 1. Couplers usually come in two plastic pieces, a base and a ring. This system fits inside cake decorating bags or cones and allows you to use the same icing with different tips.

Worried about your baby or toddler either wrecking or wrecking themselves in your home? Baby proofing time! Make sure your house is safe and secure for your child when they start exploring their turf.

Save money on prom transportation by turning your parents’ station wagon into a one-of-a-kind limousine.

Seat belts save lives… but are you wearing yours the right way? Size up yours for a safe ride. You Will Need:

Moving is one of the top ten most stressful life experiences. Here’s how to pack it up without wanting to pack it in.

The modern knot is an updated version of the classic chignon. Here’s how to get the look. You Will Need:

Create a cute headband out of your own hair with this braiding trick. You Will Need:

Learn how to make an origami catfish. Get a piece of square paper. Fold diagonally from the upper right tip to the lower left tip of the paper. Fold the lower right tip to the upper left tip and open it up halfway. Hold the right fold and slightly open it placing your finger inside the flap. Gently press downward to create a square-shaped fold on top. Grab the left side of the square and fold it towards the right. Grab the other fold, the one made earlier, and do the same fold as the one done...

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

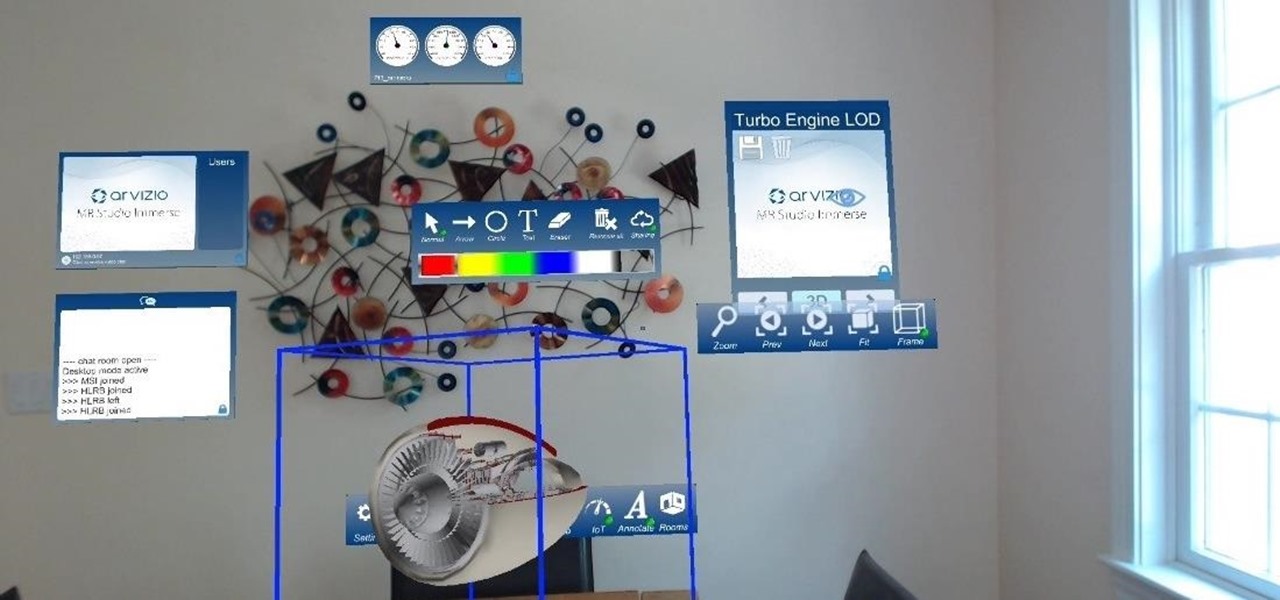
HoloLens developer Arvizio has expanded its collaboration suite of tools for enterprises with a device that can stream and record mixed reality experiences in high-definition for local and remote audiences.

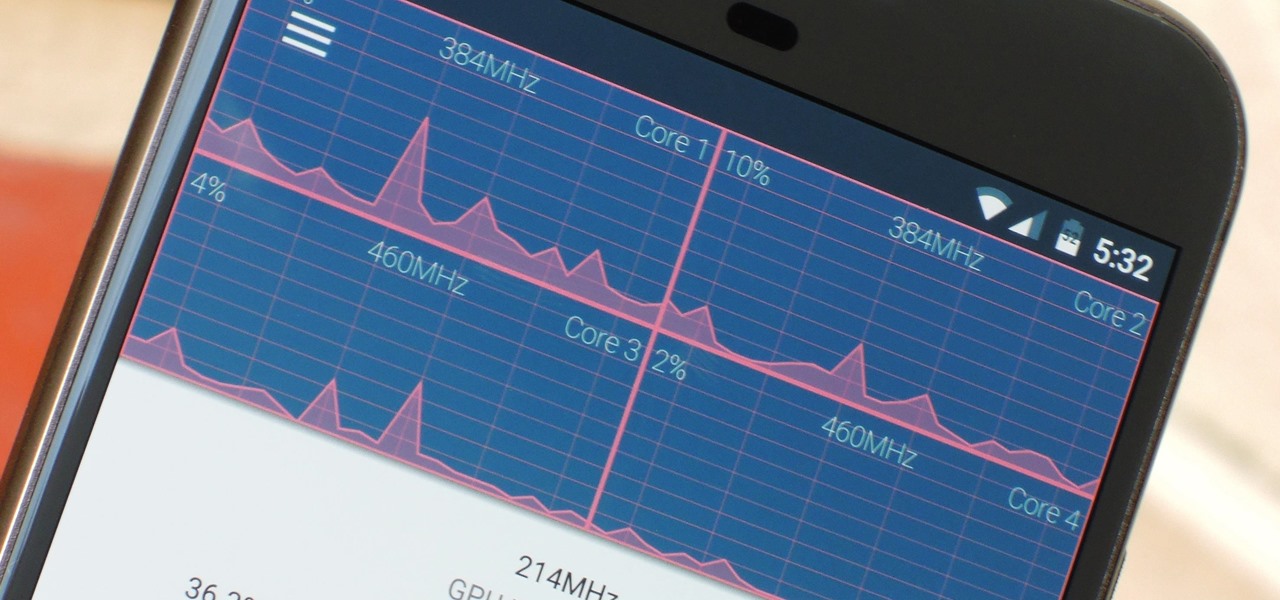
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest browsers on the market.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

With just a Phillips head screwdriver and this walk-through, you can open and close any bObi robot vacuum. So long as you have a replacement wheel, follow these steps to install it yourself.

bObi has four floor detection sensors on her underside that warn her not to drive over ledges and stop her from falling down stairs.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

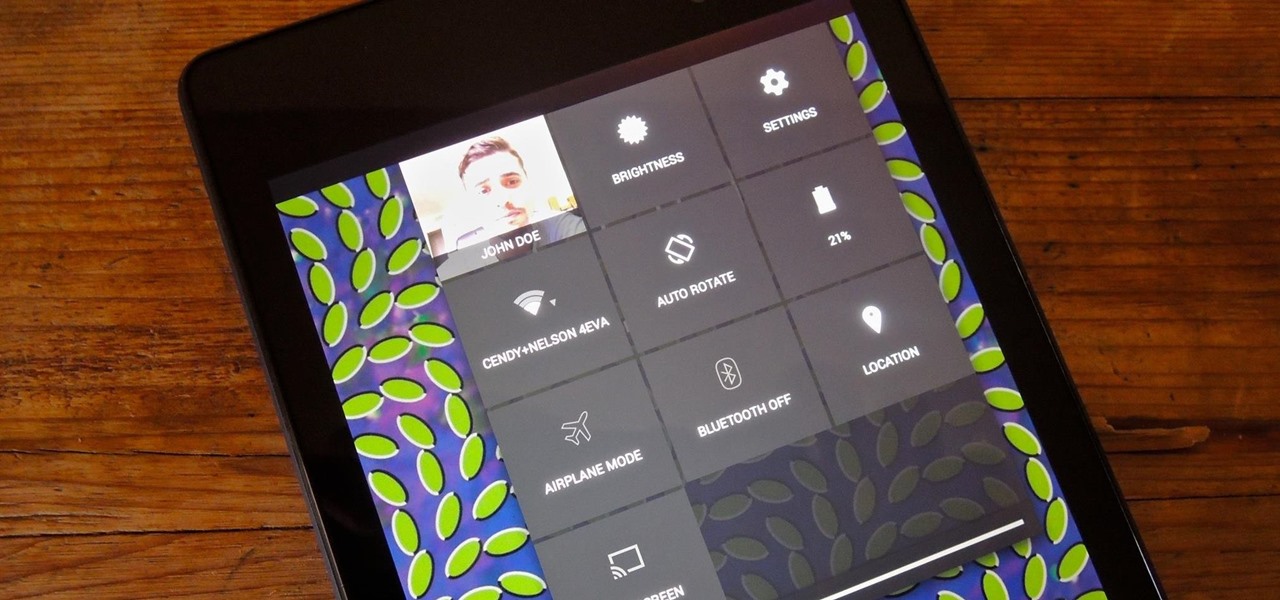
Accessing notifications and quick settings from the lock screen just makes things move quicker and more efficiently, unless of course we're using a secure lock screen. It makes sense that if we have face, pattern, or pin security enabled, we may not want notifications accessible, but really, that should be something we decide for ourselves—and now we can.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

This homemade hairspray-powered PVC rocket takes less than an hour to construct and only costs about 20 dollars to make. Check out my video below for the step-by-step instructions on building your own backyard rocket, and follow the written guide below for reference.

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.