Matildo Nieva and VideoJug demonstrate how to make a Banana Rum Cream cocktail. Go bananas with this creamy concoction perfect for an after-dinner treat. To make it, fill the cocktail glass with ice to chill it and place to one side. Half fill the shaker with ice cubes. Into the shaker add the dark rum, crème de bananas and single cream. Ensure that the lid is firmly secure and shake vigorously. Discard the ice from the cocktail glass, attach a strainer to the top of the shaker and pour it in...

You won't need to comb the beach to make this tasty treat - quick, easy and sinful! Pour the caster sugar into a saucer. Rub the wedge of lime around the rim of the cocktail glass then rub the rim of the cocktail glass in the sugar. Keep the lime for later. Fill the shaker half full of ice cubes. Into the shaker add the rum, the maraschino liqueur, the cherry brandy, sugar and the lime juice. After ensuring that the lid is secure, shake vigorously. Make a Beachcomber cocktail.

As we age we need to consider certain factors in our homes. The reason for most deaths in a home is fire;the cause of most injuries to seniors in their home is falling. Check for clutter, many seniors have failing eyesight and the clutter can't be seen. Be certain the home has adequate lighting and that a working flashlight is handy. Avoid throw rugs, all carpeting should be secure. Make a home safe for seniors.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

An alternative to trick-or-treating every Halloween is to have kids participate in a scavenger hunt. The activity provides the same excitement and still allows you to be with your kids while they participate. A scavenger hunt can be easily organized – here are some steps in preparing for a Halloween scavenger hunt:

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

DOTTREL 58 points (8 points without the bingo) Definition: dotterel; a shore bird [n]

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

Developers have created many tools for testing the strength of passwords (1, 2); there are also plenty of tips for coming up with a strong password in the first place. But why do the grunt work when an app could generate a perfectly secure one for you?

Assisted pull-ups, as the name implies, allow you to perform pull-ups with help. In this exercise, the help is in the form of heavy duty rubber bands. This version of the pull-up is a great alternative for those who are unable to perform a traditional pull-up.

The use of heavy duty resistance bands (also referred to as "Powerlifting Bands") as a strength training aid has become increasingly popular over recent years. The bands are used for accommodating resistance; a technique that involves creating maximal tension throughout a full range of motion.

The crab walk is a great exercise for the hips and butt. This exercise is fun, yet challenging. It is relatively easy to perform, although it can be demanding for some. You will want to ensure that the legs are thoroughly warmed up before doing this exercise.

Here is an exercise that really works the gluteus muscles. It is relatively easy to perform. However, for this exercise to be effective, it does require a bit of skill and proper technique. A workout mat is recommended.

The quadruped is a highly effective exercise that doesn't require expensive equipment. You will definitely feel this one working. The quadruped leg lift is also referred to as the "fire hydrant" exercise.

There are a number of unconventional training methods which can be used to improve strength. The truck pull is one of them. When performing this exercise, the speed at which the vehicle can be pulled is very slow. Thus, it is ideal for building strength in the lower body.

Watch this video from This Old House to learn how to work with fiber-cement board. Steps:

Hi fellows! I finally decided to join this forum, which I find very interesting and has some great contributions into the tech and security space, appreciate it!

How To Do Braid Bun Hair Style Tutorial For Beginners!!!! Check-Out this awesomely cool Braid Bun Hair Style which has been especially made for all the fashionable and Contemporary Girls. Made in few easy and simple steps, this modish hairdo will take your elegance quotient to a new level. Step 1: Comb Your Hair and Make Them Smooth and Tangle Free.

Successfully Complete Your CNA Training Program You must finish your CNA (Certified Nurses Assistant) training program and must secure a CNA training certification in order for you to be qualified to apply for CNA state exam.

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to change the engine oil in your car properly.

Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.
Ron Paul's 2012 campaign has won the majority of Washington's delegates to the Republican National Convention, and a number of other states are expected to follow suit, pointing to a hectic convention in which Mitt Romney's path to the nomination may face a major insurgent opponent.

Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Truly spectacular and one the most breathtaking DIY endeavors to grace the front page of WonderHowTo, a recreation of Pixar's UP house was launched to an altitude of 10,000 feet in a private airfield near Los Angeles this past week. The project was executed by a team of engineers, scientists and veteran balloon pilots—(meaning, please, Do Not Try This at Home).

From Salon.com "AB 32 mandates that California must reduce its greenhouse gas emissions to 1990 levels by the year 2020. But California's crazy government-by-initiative system means that just because a law has been passed by the California House and Senate and signed by the governor doesn't make it secure. On the ballot this November, voters will get their own chance to weigh in on AB 32 by deciding whether or not to pass Proposition 23, the misleadingly named "California Jobs Initiative."

It's a puzzle. It's a gun. It's awesome. Titled "The Intimidator", this 125-piece puzzle requires a special key to disassemble. Once disassembled, 20 of the 125 pieces can be pieced to form a real working single shot pistol.

In this tutorial, we learn how to do the easy step interview in QuickBooks. Although you can skip this interview, go through it so you don't skip important elements for a solid accounting program. To start, enter all of your company information and then click "next". Select your industry, how it's organized, the first month of your fiscal year, and a password. Continue this information until you are at the end, then save the file for your information somewhere you can easily find it. Make sur...

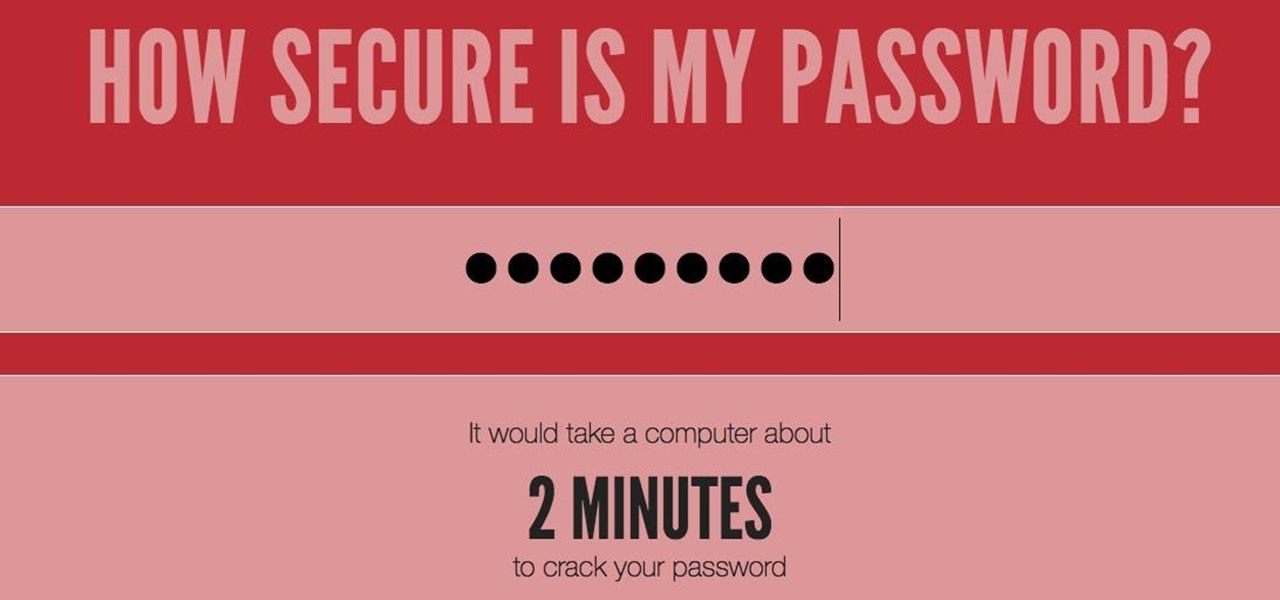
If you have any doubt about how secure that strong password you created really is, there's an easy way to check online. Just visit HowSecureIsMyPassword.net, which uses a combination of math and statistics to determine how long it would take for a PC to crack your password. It's sponsored by Dashlane, one of the top password managers available, and also gives you tips on how to make your password or passphrase stronger. The site claims the password submitted is not sent over the web, and its ...

Trusty LifeHacker brings us another helpful HowTo, but this time it's in the travel department.

Tinkernut demonstrates how to crack a wifi connection, as well as how to better secure your own personal connection. Also included in the video gallery is Tinkernut's previous tutorial on the same subject.

Side ponytails don't have to look childish. This video demonstration shows how to make a polished and pretty side ponytail. To create a unique side ponytail, brush all of the hair to one side, gather it and tie it with a hair band. Take about a quarter of the hair and twist it around the hair band, securing the ends with a bobby pin. Watch this video hair styling tutorial and learn how to pull hair up into a side ponytail. Pull hair up into a side ponytail.

Check out this instructional video to learn how to use hotel room safety tips. Make your vacation or business trip uneventful when it comes to staying safe in your hotel. Check out these tips for keeping you, and your stuff, safe when you're sleeping away from home. Hotel Room Safety - Stay Safe and Secure in Hotels Video.

Welcome to the Rudi Latka's Soccer School. The basic dive is best done at speed so the referee can't see what's happened. As you approach your opponent, flick the ball past them, and then as you pass the player dive upwards and then turn in the air slightly before landing. As you land look towards the ref with puppy dog eyes in order to secure the free kick. Dive while playing soccer.

As useful as VPNs are for securing your browsing experience and bypassing frustrating barriers online, it's hard to find the right one among the horde of choices. VPN.asia: 10-Year Subscription is a great choice for a VPN that keeps your browsing safe and smooth, and right now, it's only $79.99.

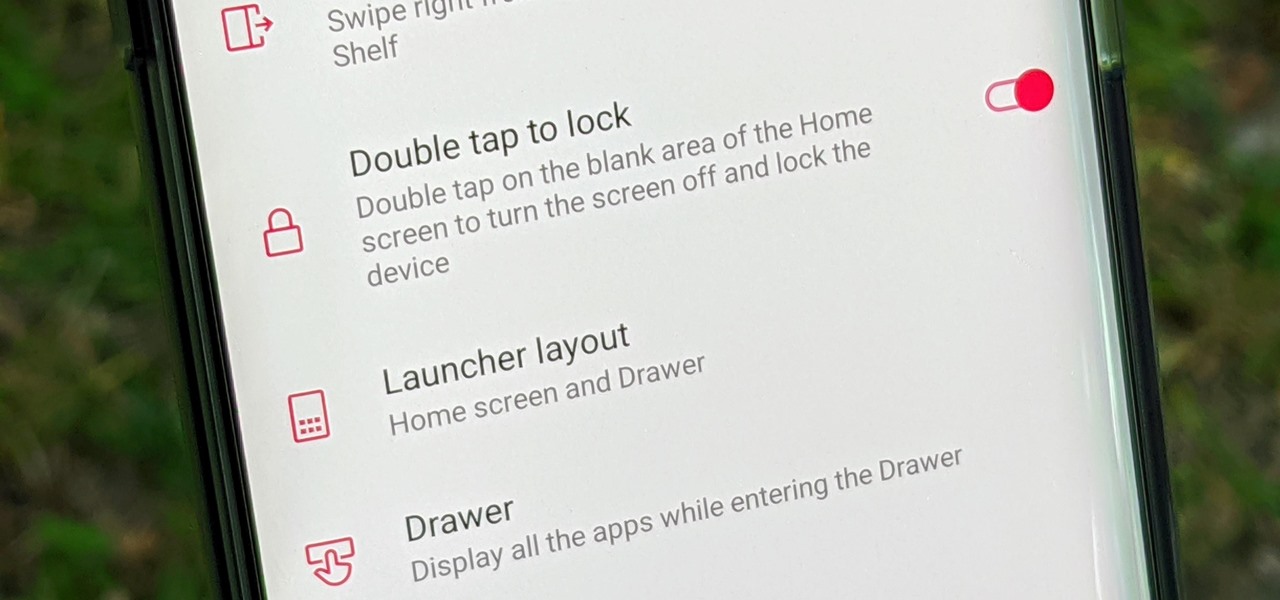
By default, most Android phones will instantly lock once you turn the screen off with the power button. Doing so is a surefire way to secure your device when you walk away, but what if there was another way to accomplish this even faster? If you're using the OnePlus Launcher on your OnePlus phone, there's something you can do to lock your phone instantly without pressing the power button.

Well this law was passed... Our privacy is slowly being pulled away from us. But I'm certainly not going to let it stop me. We'll just have to take more secure measures. If You Use Tor Browser, The FBI Just Labeled You a Criminal.

In an effort to prevent drones from being hacked, DARPA has been developing an "unhackable system," and seems to think they're almost there. The development team "proved" mathematically that their kernel was unhackable, and they hope to use it for more than just drones (power grids, cars, phones, pacemakers, etc.).