Fact: we live in a world where social media dictates our behaviors and shapes our perceptions. Maybe some of us are addicted more than others, but most of society uses some type of social media, whether it's Twitter, Instagram, Facebook, Snapchat , or something new that I've never heard of.

You've seen the Samsung Fingers and the Emoji Translator, and I know you spent a good part of the day catching Pokémon, but now that April Fool's Day is officially upon us, the flood of gags has reached a tipping point. Here's the best of what we've seen today.
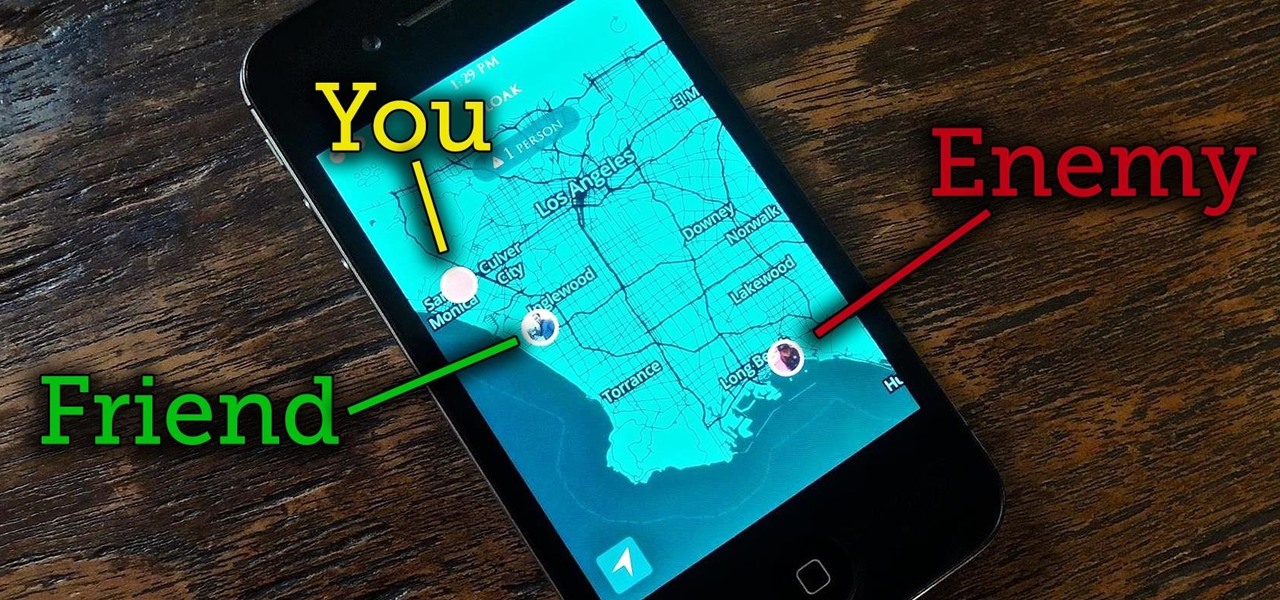
I never want to bump into my ex-girlfriend while out in the city (talk about a buzz kill), so if I could get an alert telling me that she's at Shortstops down the street, I'll avoid that area completely. This is where the new, interesting app Cloak - Incognito Mode for Real Life from dev Brian Moore comes in.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

The reason that Facebook is so popular is because it connects us to people that we could have never been connected to before. When people log on, they look for messages, comments, likes, and any other notifications that connect us to those people. These same notifications, though, distort our view of Facebook. We tend to appreciate statuses (I prefer stati) that have more likes. We're geared towards people that have more friends, so we tend to like pages that already have hundred of thousands...

Facebook is an awesome free online resource that is connected to billions of people around the world. These days, you won't meet many people who do not have a Facebook account. As a real estate agent, you can take advantage of social networking to promote your business and share your listings. By posting on Facebook and creating a page for your business, you gain free advertising to thousands of local buyers. Check out this tutorial and learn how to start uploading videos to Facebook to promo...

Computer vision is a key component in enabling augmented reality experiences, but now it can help give sight to the blind as well. In this case, that assistance comes from Envision, developers of mobile apps for iOS and Android that use optical character recognition (OCR) and object detection to provide an audio description of the user's surroundings.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

Snapchat is mostly credited as the first AR social network, and, like most social media companies, its revenue model is nested largely within advertising. As such, the company now has a new avenue for branded content.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

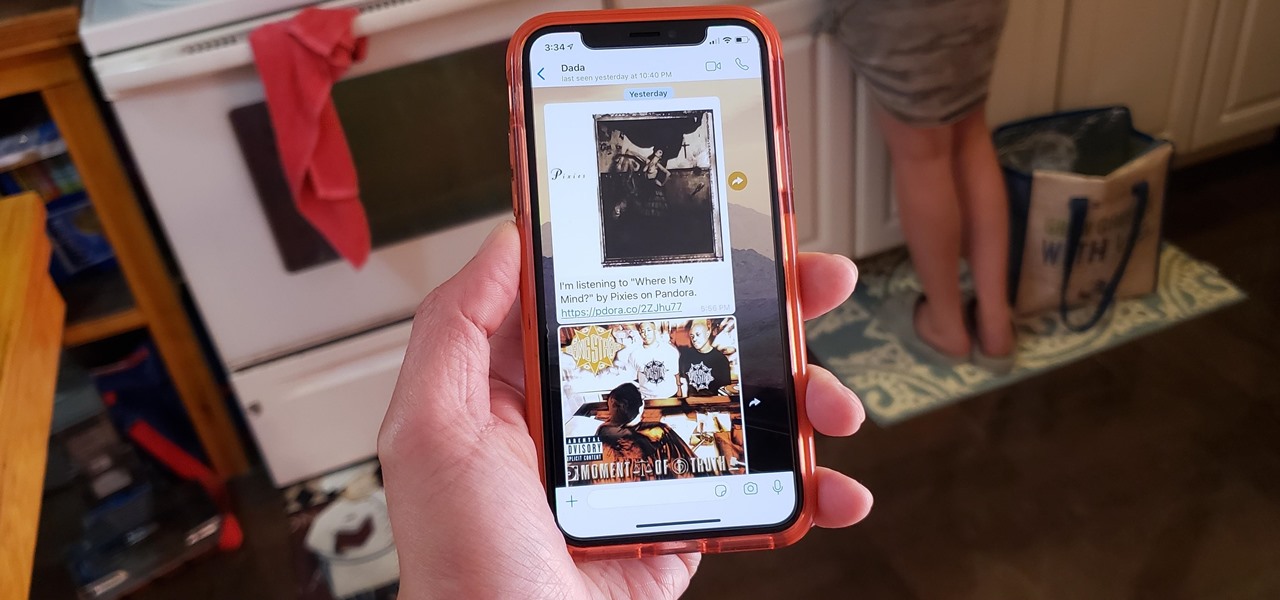
One of the best parts of Pandora is its personalized stations that auto-generate songs within the specific style or genre you've chosen. Not only does this play your favorite tracks with regularity, but it also opens your ears to previously unknown songs or artists — ones you may fall in love with and want to share with others.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Magic Leap One owners, start your virtual engines, as automotive virtual reality developer RelayCars has published an app to Magic Leap World that lets users customize and test drive a 2019 Kia Stinger.

You can never replace the skills and expertise of a professional graphic designer, but Canva comes pretty damn close. It's ridiculously easy to use the drag-and-drop design tool for both professionals and people like me who don't have the need (or knowledge required) to use more advanced graphic design software.

Kitten Planet, a spin-off company that grew up in Samsung's C-Lab incubator, has developed a connected toothbrush that teaches and motivates children to brush their teeth better via augmented reality while tracking their performance.

With the theatrical premiere of Deadpool 2 less than two weeks away, the hype train for the sequel to 2016's surprise R-rated hit is gaining steam, and augmented reality is on board for the ride.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Taking photos that are actually printed and hung on a real wall, versus being shot and shared via a social wall, is a seemingly lost art, but PhotoBloom AR wants to change that with augmented reality.

What's black and white, sounds like actress Kristen Bell, and is standing in your living room talking to your kids right now? Don't worry, that's just Genius the Panda, an augmented reality character from the Yakables app for iPhones and iPads.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

A Jedi does not seek adventure or excitement, but Star Wars fans can seek Jedi with the Find the Force augmented reality scavenger hunt promoting the launch of merchandise for Star Wars: The Last Jedi.

Drones are a fairly new craze to hit the nation. While they are accessible to the general population, good drones still typically cost a ton of money and despite all the fun they are, it's sometimes not worth it to actually buy one. If you're one of those people who would love to play around with drones — but don't want to have to buy one — Arcane Reality is developing the app for you thanks to Apple's ARKit.

We are totally buggin' about Pinterest's update to their Lens. I know, I had to.

Is technology making us disconnected? Findings from a study conducted by YouGov hint that — for millennials — the answer is yes. The research found that nearly one in five US teens prefers to video chat their friends rather than spend time with them face-to-face.

Delphi Automotive PLC has announced it is partnering with Transdev Group to develop on-demand driverless transportation systems, a deal that shows promise for autonomous development on a global scale.

One thing you don't see often in the driverless industry are partnerships. When automakers are in the news together, it usually means drama. However, an important partnership between Nissan and Mobileye was announced today. One that has the potential to make driverless cars on the road better and safer.

Snap Inc. is no stranger to augmented reality. In fact, AR has been the Snapchat app's most popular feature, as face filters continue to update and change the way we communicate with each other. But in a new move, Snap Inc. is showing its commitment to improving AR and its real-world integration with its updated world lenses.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

Live Photos is an interesting new feature introduced by Apple on the iPhone 6S and 6S Plus models that captures the moments immediately before and after you snap a picture in the Camera app, resulting in a GIF-like animation.

Time takes its toll on your home screen. Before you know it, your clean app pages start filling up with social media, music streaming, video, and dozens of other kinds of apps. And let's face it, a lot of those apps are never touched after the first few times you use them.

If you're one of the many that likes to upload collages to Instagram, the Facebook company has a new tool for you. Instagram released a brand new app in March called Layout to help facilitate the process of creating photo layouts to post onto social media or just share with friends.

Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

With over 2 million uploaded videos and over 28 million people who had talked about it online by the end of August, the ALS Ice Bucket Challenge was the most viral social media event of 2014. Its popularity provided the ALS Association with $115 million in donations to date, with everyone from students to veterans to celebrities contributing.

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...

With developments from tech giants Apple and Samsung being shared throughout the interwebs, the term smartwatch has become increasingly popular over the last year. That being said, smartwatches have been around for a while.

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

Texting something as simple as "What up, bruh?" can be transformed into something way more baller by adding emojis, emoticons, GIFs, and textspeak. Some people would even argue that texting is a form of art, similar to Shakespearean sonnets, but it still has a ways to go if you ask me.