We're all guilty of a little social media stalking now and again. Or ... every day. Who's keeping track? Everyone secretly wants to know what their ex/arch nemesis is doing for the weekend via Snapchat or Instagram Stories.

Your friends are ditching Snapchat for Instagram. After the social network turned camera company announced it lost $13.30 per user in its first quarter as a publicly traded company, well, it doesn't look too good for the platform's future, y'all.

Facebook is aware that Snapchat is killing the social media game amongst the youths, which makes sense, because in 2017, video is king in social media currency. Facebook has continually shown that Mark Zuckerberg and crew seem to think the best strategy to keep up is to simply copy them.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

3D has been all the rage for the past few years. It seems like every other film has a 3D aspect to it, our TVs have 3D capabilities, and we can even print functional objects using increasingly affordable 3D printers. And after some trial and error (ahem, Evo 3D), it's finally taking shape on mobiles.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

The next mobile operating system for the iPhone, iOS 6, will be available in fall 2012. The major details and features were released 2 weeks ago a Apple's World Wide Developers Conference (WWDC). While the goal of these yearly OS updates is to move forward with technology, there are a couple of this to watch for. Keep reading to see the good and the not so good. Do Not Disturb

Social bookmarking sites is the way to go if you intend to increase traffic to your website or blog. If you don't know about sites like StumbleUpon or Digg, then you should watch this quick tip for information about getting more traffic to your blog via social bookmark sites.

Trust is one of the most important aspects in a relationship. You can work on some trust building exercises and activities to strengthen your current relationships. Plus some of these activities are just fun.

In this medical-minded video tutorial from the folks at ICYou, we learn about the potential risks associated with providing emergency care to an unconscious person. For all of the details, and to learning more about providing aid to a person who is unconscious, take a look.

Recognizing the signs of schizophrenia is the fist step toward getting help and proper treat for a loved one with this serious mental health affliction. With proper medication and therapy schizophrenia can be controlled so check for and understand what to look for.

Kissing friends and family members on the cheek is a common social greeting. If you are not used to it, cheek kisses can come across as awkward. Follow these steps and avoid any strange confrontations.

Heartbroken? If your girlfriend threw in the towel before you were ready, there are a few ways you can try to win her back. Follow along with this tutorial and try to mend your broken heart.

Striking up a conversation with a group of people you don't know can be an intimidating task. Come prepared with some interesting comments and ideas and you will be able to make new friends out of any crowd.

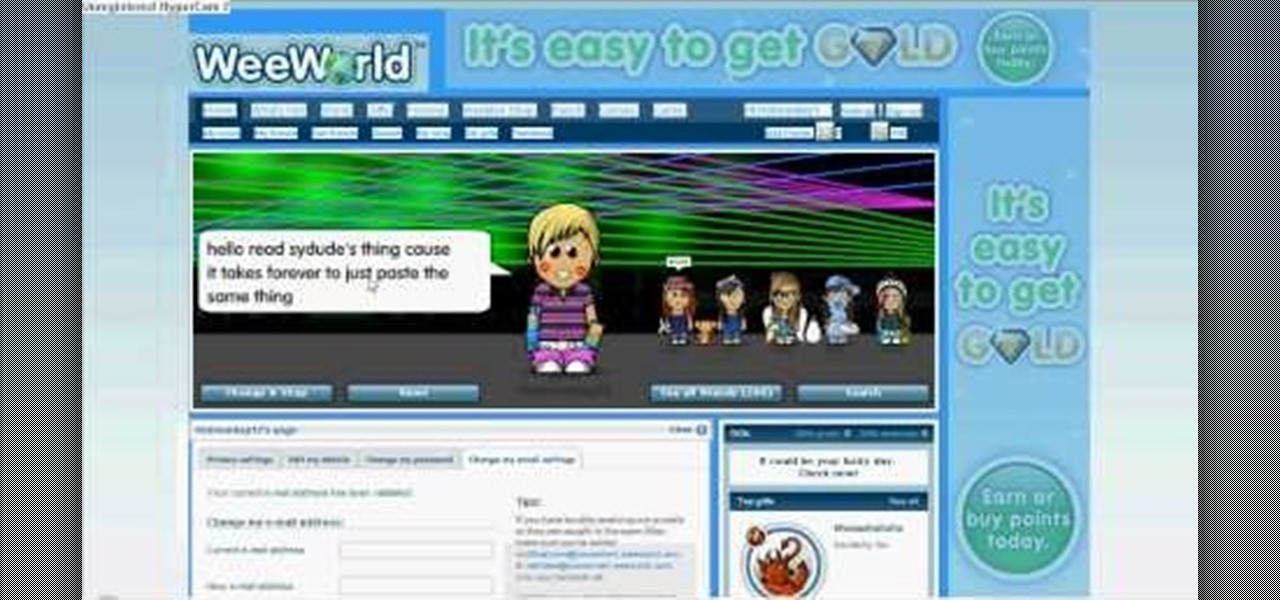
Want to know how to get free green points in WeeWorld? Sure you do. They're free! And there's 500 of them. No hacking involved, just a little trick, but you can't do it over and over again.

Most people on Facebook accept friend requests without thinking much of it. If you're one of those people and want to figure out how to get rid of a friend, this video is for you.

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw an architectural cliff house.

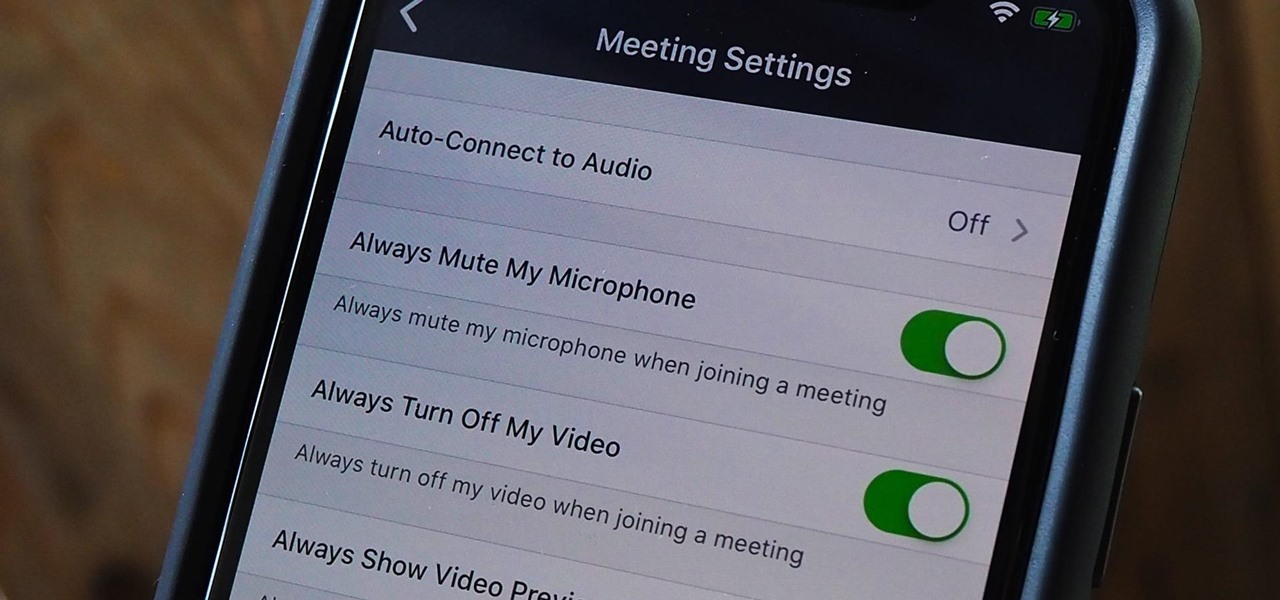
By default, as soon as you join a meeting on Zoom, both your microphone and camera turn on, sharing your audio and video to the other chat participants. While that isn't usually a problem, it can be an issue if the meeting hasn't started or you're entering in the middle of a class, and you don't want to disturb the video conference.

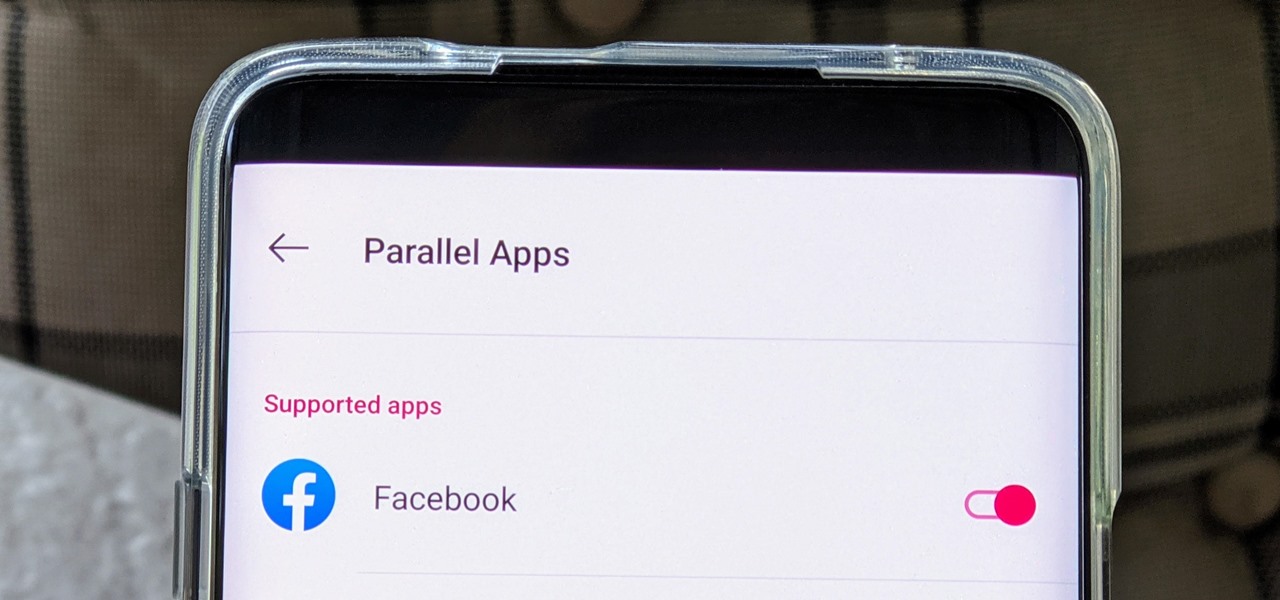
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

Commenting on Facebook pictures is a commonality. But you may not want to share your private and personal pictures on Facebook. Maybe you just want a select few to comment on your photos. Fear no more, you can send your pics and get private comments using Google Photos.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Every year, fans of Irish culture, as well as those looking to celebrate their own culture, come together on St. Patrick's Day, March 17.

The recent pitfalls and media fallout hitting Facebook hasn't stopped the social media giant from looking to the future.

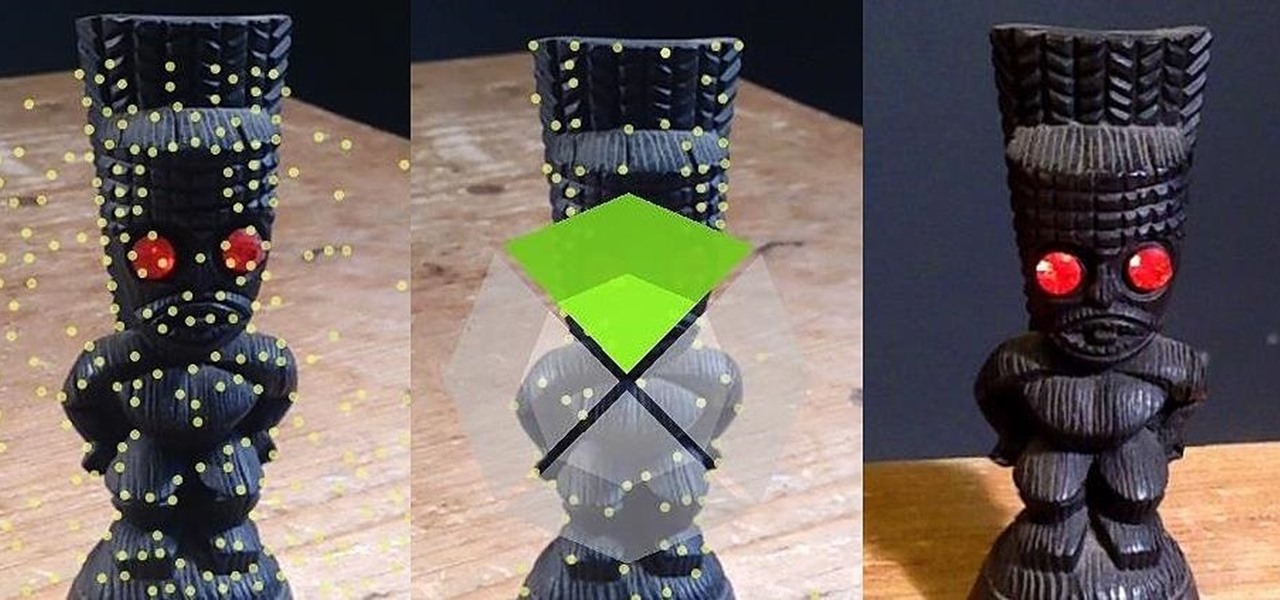
In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

If you've gone anywhere near a television in the US in the last 48 hours, you've probably seen some of the reports of Hurricane Florence and its devastating wind and rain making its way toward the Carolina coast.

Magic Leap has been promising to launch a developer conference for years, and now the company is finally making good on that promise. On Wednesday, Magic Leap sent out the official announcement for its first L.E.A.P. conference, which will be held in Los Angeles in October.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Now even muggles can see how they'd look chasing the Golden Snitch on a Nimbus 2000. That's because Snapchat is gifting Harry Potter fans with a 3D Bitmoji Lens that adorns their digital doppelgängers in the robes of the houses of Hogwarts.

With the opening round of Wimbledon, one of professional tennis's four major tournaments, beginning on Monday, Snapchat is serving up an augmented reality tennis mini-game.

With the 2018 FIFA World Cup underway in Russia, soccer (aka "football") fans worldwide can show support for their favorite teams and players in augmented reality via Snapchat and Facebook.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

As if its users weren't already having enough fun with dancing hot dogs and face effects, Snapchat is upping the ante with a new kind of shared augmented reality content.

Snapchat has added yet another social feature to its mobile app, and this one makes it possible to use augmented reality with a group of friends over video.

Given Dwayne "The Rock" Johnson's blockbuster movie pedigree and the promotional power that usually accompanies his work, there's a certain predictable symmetry in the news that Rampage, a movie adaptation of the classic arcade game, has now become an augmented reality mobile app.

Having pushed more than two million downloads of its Bait! game for the Gear VR and Daydream platforms, VR developer Resolution Games is bringing the virtual fishing fun to augmented reality.

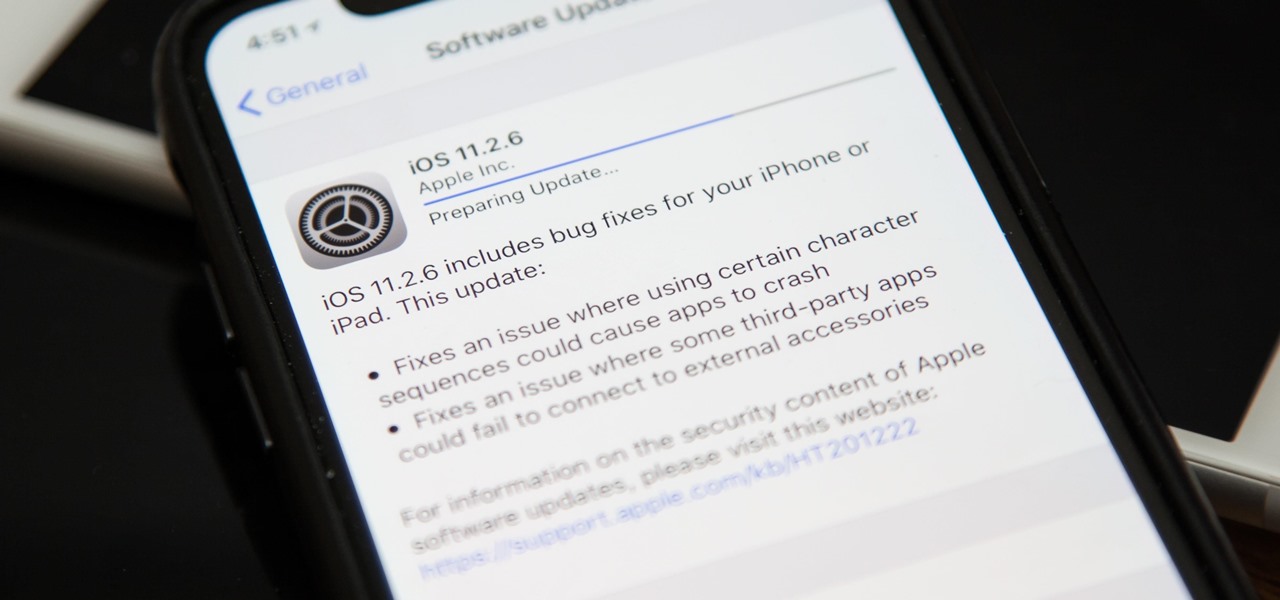
Apple released the official iOS 11.2.6 update Monday for iPhones, which comes just under four weeks after Apple pushed iOS 11.2.5 to users. This latest update was released off Apple's normal release schedule to quickly patch the "Telugu" character bug that causes erratic behavior when viewed in apps.