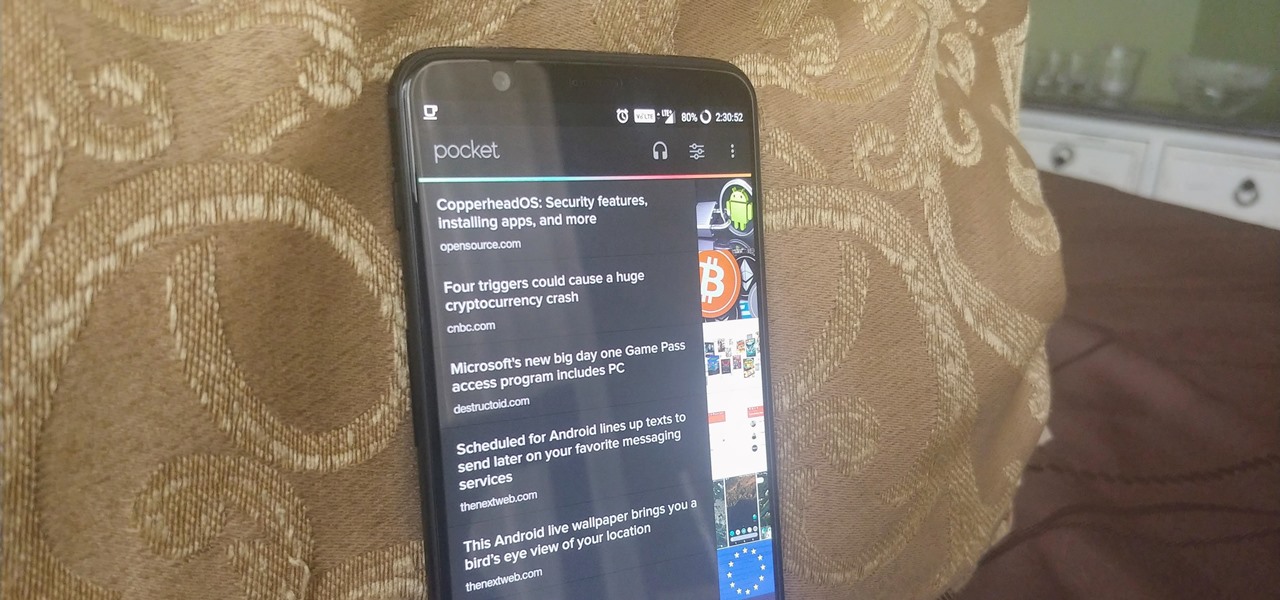
While millions eagerly await the arrival of the Galaxy S9 and all the new features it has to offer, we can actually get a glimpse of its capabilities right now — if we know where to look. The S9's home screen, in particular, is one such area that has new features we can preview now.

The S9 and S9+ are both fantastic phones. However, there's no getting around the fact that the S9+ has its advantages. In fact, it's an objectively better smartphone than its smaller counterpart — Samsung has given the S9+ features not found in the S9, meaning you'll be missing out if you choose the 5.8" Galaxy over the 6.2".

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

During the unveiling of its content partnership with the NBA, Magic Leap CEO Rony Abovitz, with an assist from former player/current pitchman Shaquille O'Neal, described at least one of the ways fans would be able to experience sports using the augmented reality device.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Nintendo set the internet ablaze Wednesday night with two big announcements. First, Nintendo revealed that the Switch's paid online service will begin in September (boo), but it was the other report that really got fans excited — Mario Kart is coming to your iPhone.

Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

Snapchat is one of the best ways for people to communicate with pictures, but it has a ton of other features baked into it. From the Memories feature to My Story, there are many ways to save save and share snaps among friends. Sometimes though, you want to add a little more pizzaz to your snaps. Luckily, Snapchat gives users a myriad of ways to interact with snaps before they're sent.

While self-driving cars appear to be as inevitable as augmented reality headsets, the auto industry and its technology partners likely have years of testing to complete and regulatory loopholes to jump through before self-driving cars hit most highways.

On Monday, toy maker Merge virtually blasted its way into CES 2018 with a new tech-meets-toys innovation in the form of an augmented reality gun controller for use with smartphone-powered first-person shooter apps.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

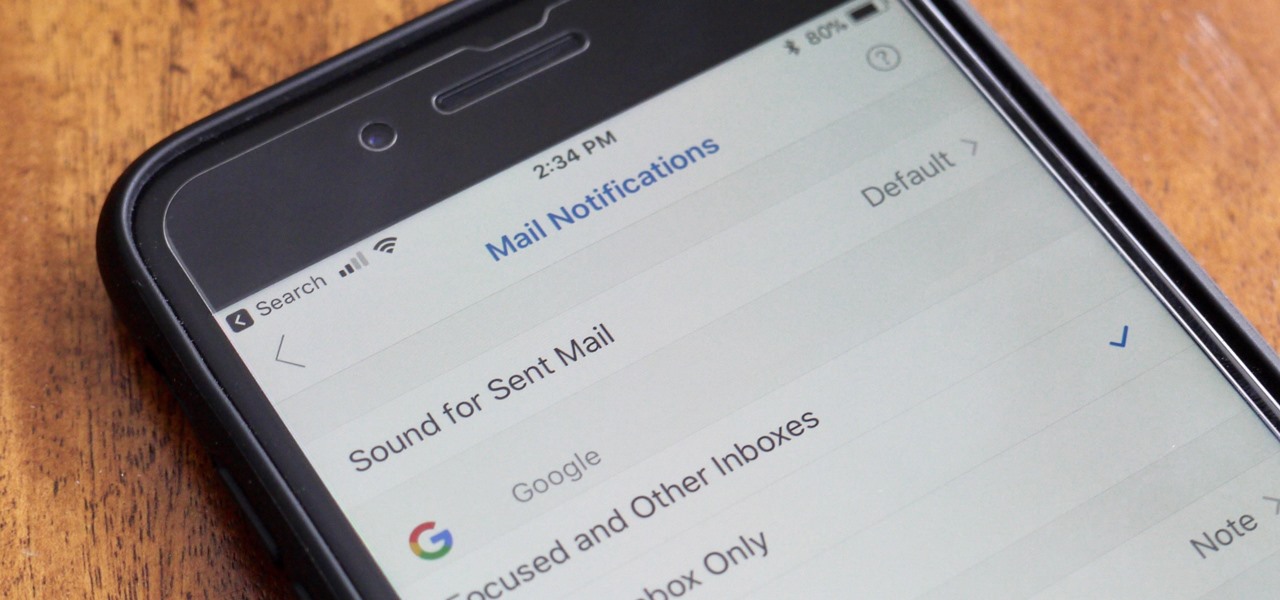
With email, one size does not typically fit all. You have multiple email accounts, each for different purposes and with varying levels of importance, so it only makes sense to customize the way your phone alerts you to each account's incoming emails. Luckily, Outlook allows you to do just that.

In addition to the standard "Raise to Wake" option that's been around since iOS 10, the iPhone X, XS, XS Max, and XR have a unique capability that lets you "Tap to Wake" the screen. But these features can get annoying real fast when your screen keeps turning on accidentally, which could even lead to some unnecessary battery drain.

When it comes to mobile gaming, you have a lot of fantastic options. Most flagship devices on the market, such as the Galaxy Note 8, iPhone 8 Plus, or OnePlus 5T, are perfectly capable of giving you an excellent, immersive experience. If you're looking for the ultimate way to experience Animal Crossing: Pocket Camp or something with more action like Into the Dead 2, the Razer Phone is the winner.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

If you used Touch ID on an iPhone before, all you had to do to install apps and games from the App Store was rest your fingertip on the Home button. On the iPhone X, there's Face ID instead, and Apple has included on-screen instructions to help everyone adjust to the lack of Home button. Still, those instructions may not be working for you, but the solution is as simple as a misinterpretation.

For those who thought the action in Pokémon Go was a bit too pedestrian, Father.io wants to recruit you for a multi-player, first-person shooter that unfolds on the streets of your own city.

Thanks to Metaverse, it has never been this easy to create your own AR game.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Christmas came early for Apple, as the company was awarded more than 40 patents by the US Patent and Trademark Office on Tuesday, including one covering a system for compositing an augmented reality construct based on image recognition.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

If you need a Halloween costume posthaste, you really can't go wrong with a LEGO man costume. And one made from cardboard that is fully functional, well, you'll probably win the "Best Costume" contest hands down. Not only will this mecha-esque costume wow everyone you meet, but it eliminates the need to apply Halloween makeup, style your hair, and get your outfit just so. With a LEGO man costume, you're ready to roll.

So, it's Halloween time, and you feel like playing around with some augmented reality apps? Well, you've come to the right place — if you have an iOS device.

We may not know what Magic Leap's product looks like. And we haven't received even a "save the date" for its launch. But we know that it will display mixed reality comics from Madefire when whatever it is arrives.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Anyone who knows me well is aware that I am a cyberpunk junkie. The conflict between lowlifes, corporations, and the government, flavored with dystopian future, high technology, transhumanism, artificial intelligence, and noir storytelling, just does something for me.

Back to the Future Part II missed wildly on many technological advances for the year 2015, such as flying cars and rehydration ovens. However, it connected on several predictions, such as video calling and biometric security, and it was in the ballpark (pun intended) on others, such as the Chicago Cubs winning the World Series.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

The fact that the iPhone X, XS, XS Max, and XR don't have Home buttons means that you'll need to learn a few new gestures. There's the home gesture, the multitasking gesture, and even a new way to access Apple Pay, among others. But one less-common action that has issues due to the lack of a Home button is taking a screenshot.

Generally speaking, in terms of modern devices, the more simple you make an interface to navigate, the more successful the product is.

For the first time, the US Food and Drug Administration (FDA) has approved medication to treat children with a serious infection called Chagas disease, which stealthily infects and damages the hearts of millions of victims a year.

Gonorrhea infections reached a peak in 1975, then decreased until 2009, when infection rate started rising and has increased each year since. With the rise of antibiotic resistance, those numbers are only going to get worse — unless we find new treatments against the bacteria.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

One of the more interesting improvements to the Photos app in iOS 11 includes a way to drag and drop a photo from one album into another album. In fact, you could even drag and drop multiple photos at the same time. And this is not an iPad-only feature — it works just as well on an iPhone.

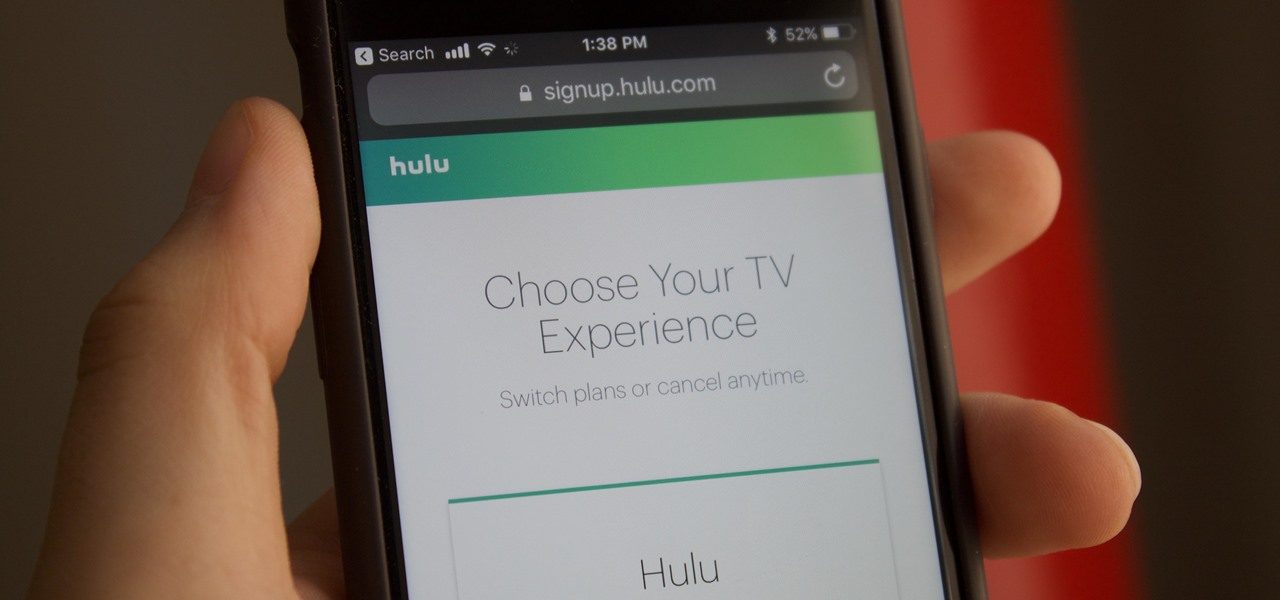
Hulu used to be simple — just a site with all the latest clips and episodes from your favorite shows. Watch some ads, watch some free TV. Easy, right? Not so much anymore. Hulu is no longer free, and on top of that, offers different pricing plans and add-ons.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

When it comes to differentiating from the competition, brands are continuing to leverage augmented reality to give consumers to the point that there are few "firsts" left to achieve in the marketplace. While L'Oreal jumps on the augmented reality bandwagon for cosmetics, Acura finds a new way to make augmented reality a spectacle in the automotive industry.

Reigns recently went on sale on the Google Play Store (sorry, iPhone users), and that inspired me to give it a go. I've wanted to try this one out for a while now, but the steep price tag kept me away. ($2.99 is a lot for me, okay?)