After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

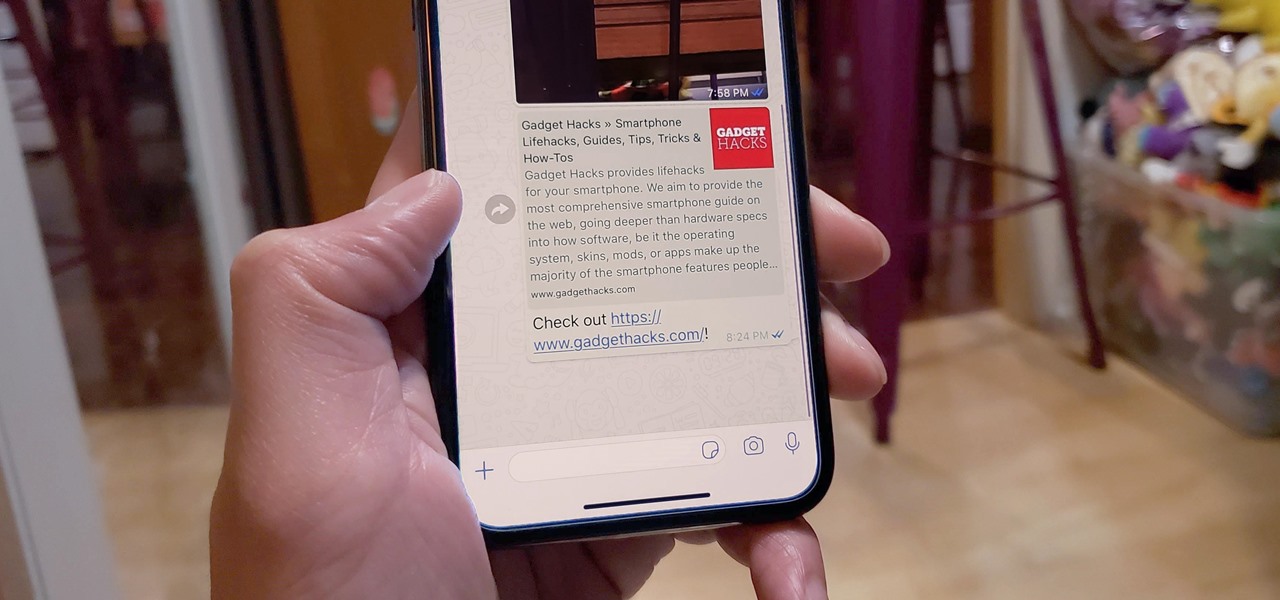
When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

Now that we've got all of our software installed, we're going to proceed with the next step in our HoloLens Dev 101 series—starting a fresh project and building it into a Holographic application. Then we will output the application to the HoloLens Emulator so we can see it in action.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Greetings my fellow hackers.

The software released in the 2015 iterations of the Samsung Galaxy line of devices—the S6, S6 Active, S6 Edge, S6 Edge+, and Note 5—have some pretty neat camera features that give these devices arguably the best smartphone camera on the market today.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for your costume.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

My bathroom is like my own private arcade room. Whenever I'm seated comfortably on the toilet, no one is going to disturb me, so I can play anything I want on my smartphone. You probably do it, too — and your parents, kids, friends, colleagues, and boss — so don't be afraid to admit it.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing up for the new streaming service, let's take you through all the changes and features you should know about before doing so.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions.

Unless you're vegan or lactose intolerant, butter is an indispensible ingredient. However, butter is no one-trick pony. It can take many forms that make it even more versatile and useful in the kitchen. Clarified butter has many advantages over regular butter—but there are certain cases where you shouldn't use it. More on that later.

Break out the office supplies and kitchen utensils, because improving your morning makeup routine is about to get a lot easier. Some of the things you have lying around the house can provide the perfect solution for some of the most common beauty problems. We've collected 10 of our favorites.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

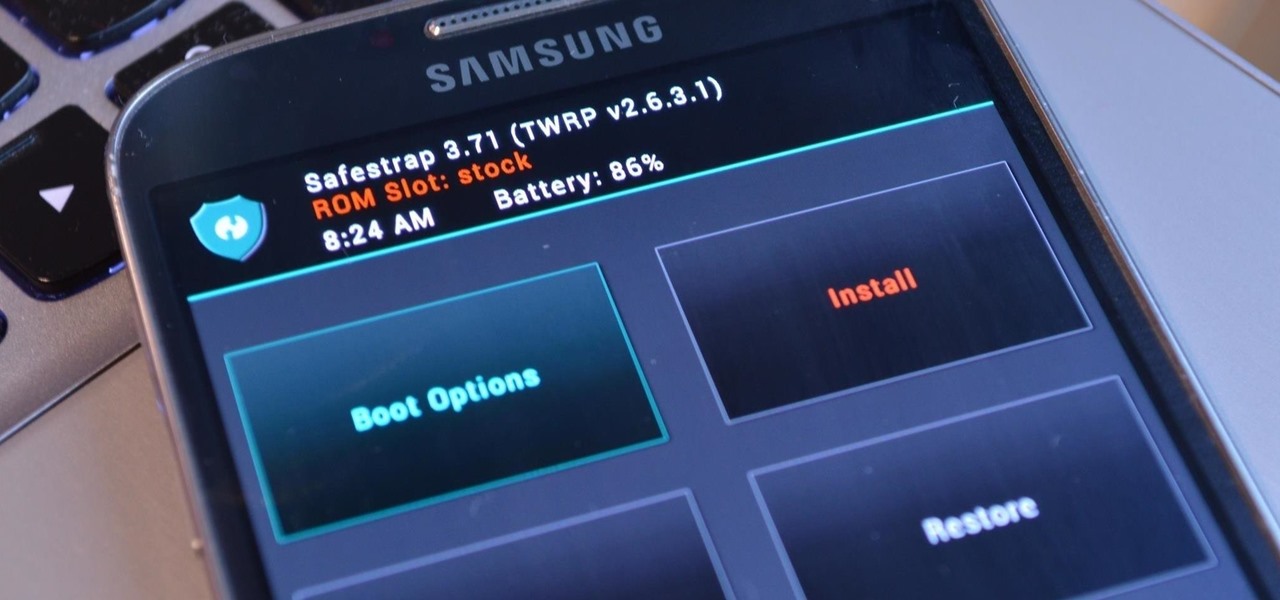
Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

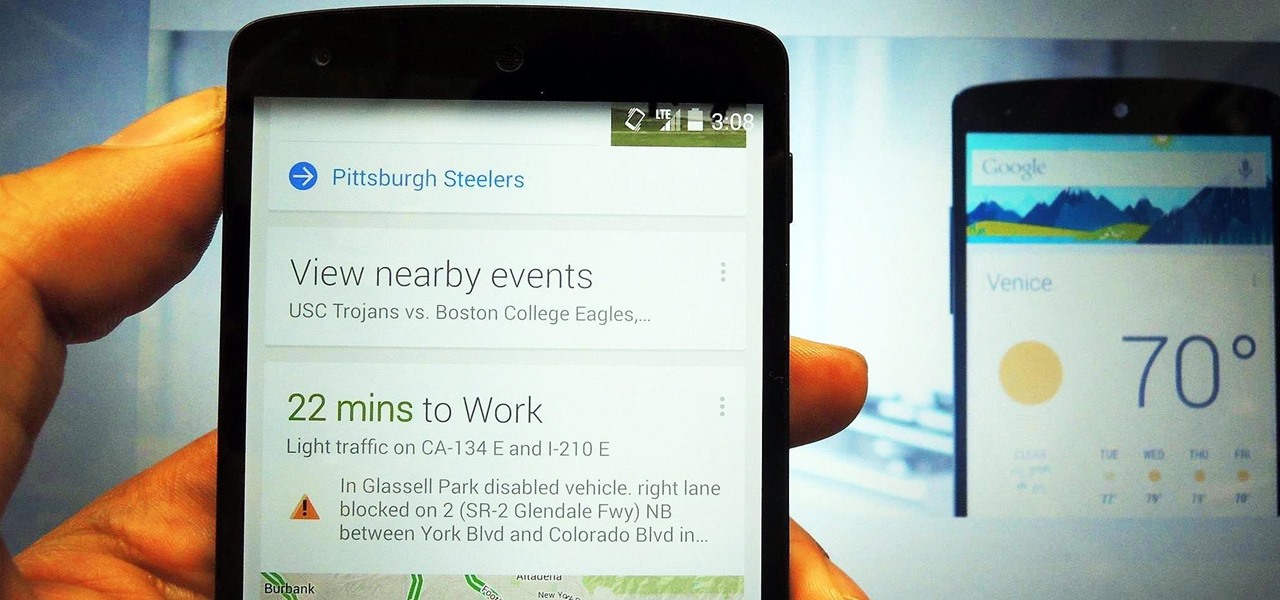
The launch of Android 4.1 Jelly Bean was also the launch of Google Now, a service that was supposed to one-up Siri, the resident personal assistant for iOS devices. Google Now offered enticing features, but its launch went unnoticed by a great many Android users.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

The best part about April Fool's Day is that everyone is fair game. Even big tech companies like Google and Twitter get in on the action every year. It encourages even the most uptight, unfunny party-poopers among us to have a little fun driving each other crazy with pranks — even at work.

In the first part of this two-part guide, I covered cutting, grooving, beveling, making holes, and stamping/tooling. I hope you enjoyed that part, because we're pushing the accelerator to the floor and moving ahead at full speed!