Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wireless 4G LTE networks for fast Internet. Both the iSight and front-facing FaceTime cameras were improved, too. The only downside seems to be the tinier "Lightning" connector, which replaces the standard 30-pin connector w...

The march of Amazon to insert itself into nearly every retail arena continues with the e-commerce giant's latest move to launch its own brick-and-mortar beauty salons.

Apple just released iOS 14.1 for iPhone today, Tuesday, Oct. 20. This update first hit iPhones one week ago, but not for long — Apple pulled the release almost immediately, later seeding it to iOS developers only as a GM (golden master) release.

Apple just released the public GM (golden master) for iOS 13.6 today, Thursday, July 9. The update comes three hours after Apple released the 13.6 GM for developers, and the same day as the release of iOS 14 public beta 2.

Apple just released the GM (golden master) for iOS 13.6 today, Thursday, July 9. The update comes nine days after Apple released the third developer and public betas for 13.6, and the same day as the release of iOS 14 public beta 2.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

Comparing the present-day states of the consumer and enterprise sectors of augmented reality is like evaluating the merits of sports car versus work trucks. Like consumer AR, sports cars are sexy and exciting, but perhaps a bit impractical at times. On the other hand, enterprise AR is utilitarian, but it gets the job done and, in the long run, pays for itself.

If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

On April 26, 2019, Sinemia posted a note on its website stating it has ceased all operations in the United States. It's not known if it continues to work in other countries or if US users will be getting any refunds, particularly, for annual subscribers.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

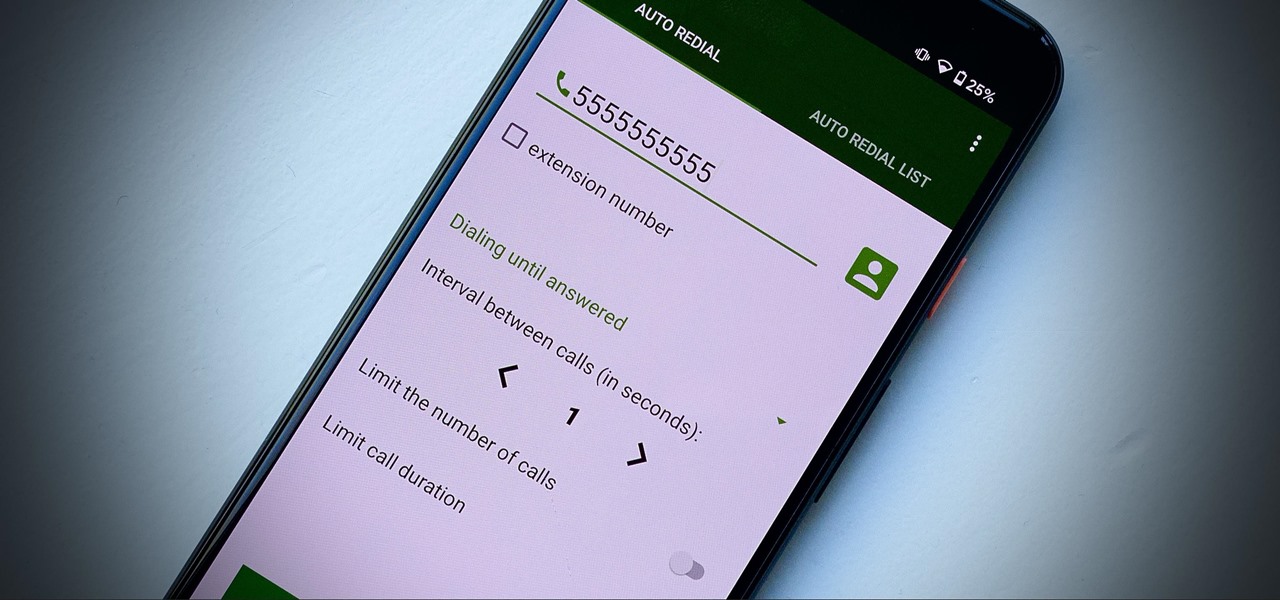
There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

Some phone lines make it nearly impossible to get past the busy tone, whether it's a viral call-in giveaway, your state's unemployment office, your local post office during the holidays, or the repair office for a broken warrantied product you have. Thankfully, there are apps you can use to help break through the noise.

Google and Snap held their annual conferences this week, and both companies managed to upstage their new AR software features with fantastic new AR hardware.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

Things just got a lot better in your iPhone's Messages app, and the most significant change lets you text Android users with iMessage-like features such as typing indicators, read receipts, large file sharing, high-quality photos and videos, and even emoji reactions.

Whether it becomes mandatory or not to show your COVID-19 vaccination card at events, restaurants, bars, hotels, airports, and other public places, it's a good idea to digitize the paper card on your smartphone so that it's always with you. It's also wise to give yourself quick, convenient access to it, so you're not holding up lines while trying to locate the file, and there are a few ways to do that on your iPhone.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use an unlisted number - such as, a cell phone number. Many also use special code *67 to mask the number so your Caller ID will show "Blocked Number" or "Private Number". There are a lot of mild cases of so-called phone bull...

If you're an owner of a BlackBerry smartphone, chances are you're going to want to use BBM, which for all of you newbie BlackBerry owners, stands for BlackBerry Messenger. BBM is an instant messaging application developed solely for BlackBerry device owners.

New to eBay? Don't worry, setting up an account and buying and selling doesn't take that much effort at all. Everyone who has an Internet connection has at one point come across eBay, to find the perfect gift for their loved ones, to find the cheapest deals on plasma televisions and computers, or to get rid of their dusty, old record album collection in their web store.