The future for the Meta 2 augmented reality headset will have to wait. While shipments were supposedly on their way out back in June, Meta revealed today that they need a bit more time to provide the best possible experience—and that's really for the best.

If you've seen, heard, or even tried the latest virtual reality headsets, you've probably heard about something called "room scale." It's why the HTC Vive suddenly usurped the reign of the Oculus Rift while no one was looking, and it's exactly where Oculus hopes to catch up. Here's what it is and why it matters.

Forget headphone jacks and "Courage." Look past the shiny Jet Black finish and beyond the minimized antenna lines. Sure, quad-LED flash and dual cameras are nice—but dual-SIM would've been much better.

Tricking your eyes into seeing 3D images isn't all that hard in movies or even in virtual reality, but when you start projecting holograms into the physical world, you run into some difficult problems. Microsoft obviously figured them out with their HoloLens, but how? The process is pretty amazing.

You can easily take audio for granted in virtual reality, but realistic sound in VR isn't an afterthought. It not only involves creating surround sound within a pair of headphones, but figuring out where the sound ought to exist based on your position and line of sight.

Imagine you have mastered the perfect cherry pie for your annual work picnic but, upon taking it out of its airtight pie carrier, your heart sinks as you realize the crust has turned to mush thanks to the moisture from the filling. Sound familiar?

Virtual reality, along with its siblings, has the opportunity to profoundly change the way we interact with all things digital. As a visual medium, we often don't think about the impact on audio, but it plays a significant role nevertheless. When it comes to music—and music videos—the possibilities are enormous.

When you think about consumer VR headsets, you either imagine a computer-tethered powerhouse like the Oculus Rift and HTC Vive, or something portable yet limited that utilizes your smartphone like Google Cardboard. Somehow, we haven't seen much in-between, but the Idealens aims to fill that gap.

Thanks to Snapchat, we're all familiar with face swapping and augmentation thanks to some clever, fun technology. But that's just the beginning, because this kind of augmented reality can do so much more.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

With Touch ID enabled, your iPhone needs to scan your fingerprint before you can access your home screen or last app used. Before it unlocks, your iPhone might request that you press the Home button, adding an unnecessary step between you and your data. However, you can turn the feature off so that you don't need to click any buttons to unlock your device.

Pokémon GO, the biggest augmented reality sensation ever, broke app store records this opening weekend. But it also did something even more important: it gamified physical activity.

Even today, smartphone text input leaves a lot to be desired. It's difficult to select specific words, the cut/copy/paste menu isn't always accessible in every app, and we're lacking undo and redo options, even though it's as simple as pressing Ctrl + Z on computers.

Augmented and mixed reality experiences attempt to break us out of windowed computing experiences and allow us to place software anywhere in the room. But that software doesn't have to take a rectangular form—theoretically, the web doesn't have to restrict itself to a page in a browser any longer. Does this mark the end of the web browser entirely? Probably not. A lot of information works well on the page, and the Microsoft HoloLens still uses a pretty standard version of their own Edge brows...

The world of augmented reality has seen a myriad of different products, from sensor-laden smartphones to robust holographic headsets, but Google Glass's failures nearly killed the middle ground.

If you're a tech geek who cares about the environment, you probably concerned with your personal carbon footprint. You may feel like your love for gadgets is slowly contributing to the degradation of our planet, but tech is your life. And in this scenario, small changes matter.

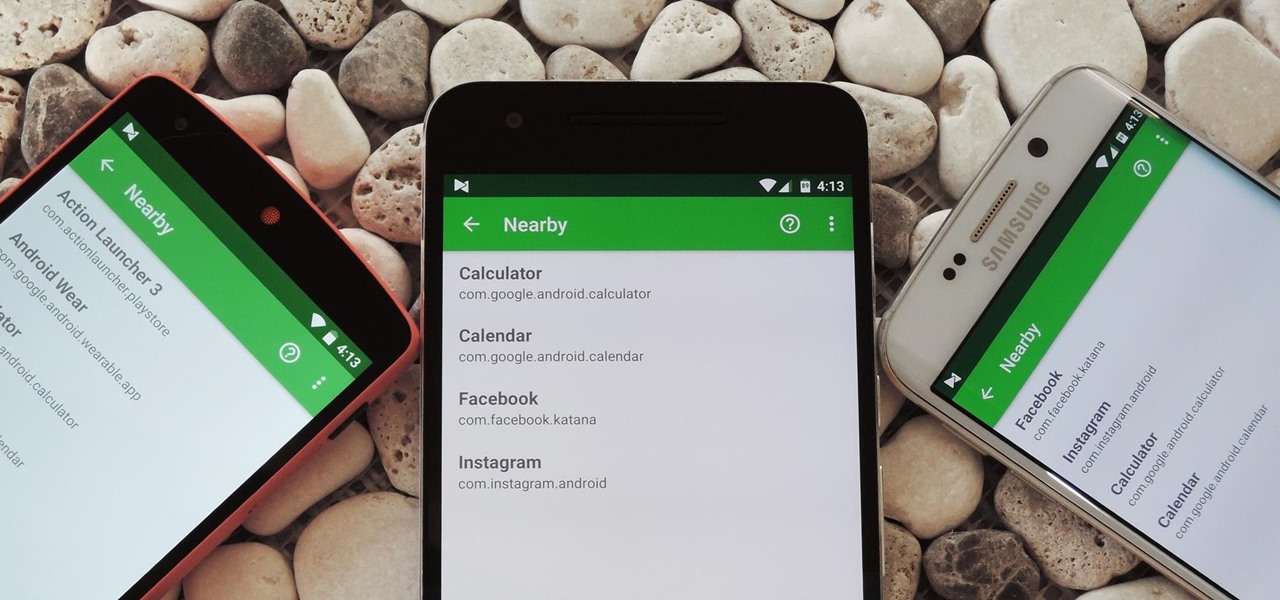
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console sales as a whole.

If you find yourself switching between Android devices frequently—for instance, your Nexus 6P and a Samsung tablet—you've probably noticed how the button placement can be different. Normally, it's back, then home, then the recent apps button, from left to right. But Samsung devices have this backwards, which can lead to frustration when muscle memory kicks in and the back button isn't where you expect it to be.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

As one of the most popular home screen apps on Android, the Google Now Launcher is used by millions of people across the world. The two main reasons behind this success are its integrated Google Now home page and an elegant, easy-to-use design.

First and foremost, let me once again apologize for that bug, which I failed to notice in time. Alright, alright... Enough sulking, oaktree. Get to it!

If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums.

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

You gotta love Android—not only can you replace your default home screen entirely, but there are tons of options that provide alternative methods for launching apps with ease. We've covered some of these options in the past, including an app called Bar Launcher that lets you launch apps from your notification tray—but that one's starting to look a little dated these days.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

Frozen fruit is always in season at your local grocery store, so you don't have to wait until the farmers market starts again to enjoy delicious baked fruit desserts. Peach pie, blueberry muffins, raspberry scones... all of these delicious baked goods can be just as delectable when using frozen fruit, too.

We've all been there. You're driving along with Google Maps pointing the way when you get a call from your friend asking you how much longer it'll be until you show up. You try to offer some lame excuse about how something came up last-minute, but you're interrupted, quite rudely, by Maps's voice guidance. The voice butts in again, and again, and again, to the point that you consider having Maps navigate you to the nearest cliff so that you can drive off it.

No crème brûlée is worth its custard without the crackled, caramelized crust it's famous for. For this reason alone, many cooks have a brûlée torch sitting somewhere in their cabinets.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.