How do you safely store your augmented, virtual, or mixed reality headset when you're not using it? Cybust hopes you're willing to shell out $89 to display it like a sculpture around your house.

Most augmented/mixed reality hardware still exists in the development stage, whether that's one of the more robust headsets or a high-powered smartphone. Most everything else isn't widely used or monetized. Snapchat, however, snuck in under the radar and created the foundation for the first social network to focus on augmented reality.

Virtual reality and horror were meant for each other. You'll get all the positive aspects of experiencing a terrifying situation such as excitement and an adrenaline rush, without any of the real-life consequences, like being ripped to shreds by a herd of flesh-eating monsters.

Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

The Creative Lab at Samsung, also known as their C Lab, is trying to make wearable fitness devices more inconspicuous with its wearable smart belt, the WELT, but that might not be all.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

Collaborating with other people can be a pain, especially if you have to share one device between the entire group. Usually when you're creating a new design or trying to edit a mockup, you end up hunched around a single screen or end up emailing revisions back and forth, which can be difficult when you're short on time.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

The debate between physical and virtual navigation buttons and their respective benefits has been going on for a few years now. It looks to finally be settled, with the Samsung Galaxy S5 being the only current-generation flagship Android phone that has yet make the switch to on-screen buttons.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

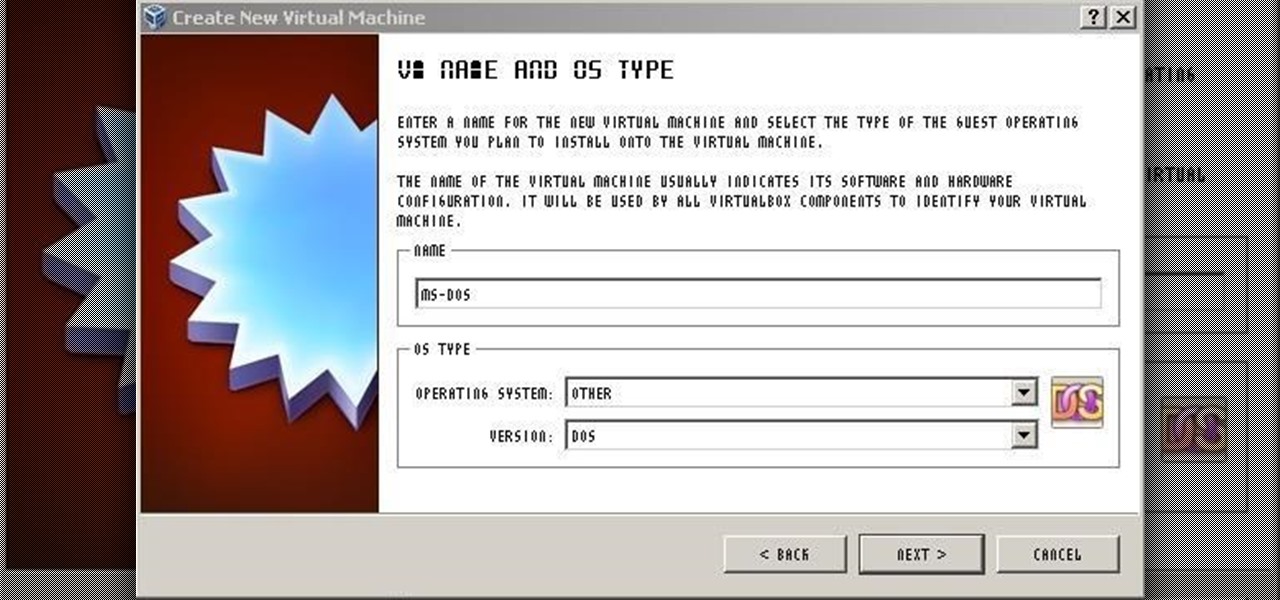
For those needing to replace old controller hardware on cutting mills, those into native retro gaming, or for those who want to see what all the fuss was about in the 1980's, or for those who just want a play with old but great technology, this tutorial shows you step-by-step processing getting the breakthrough desktop operating system running on the latest greatest hardware.

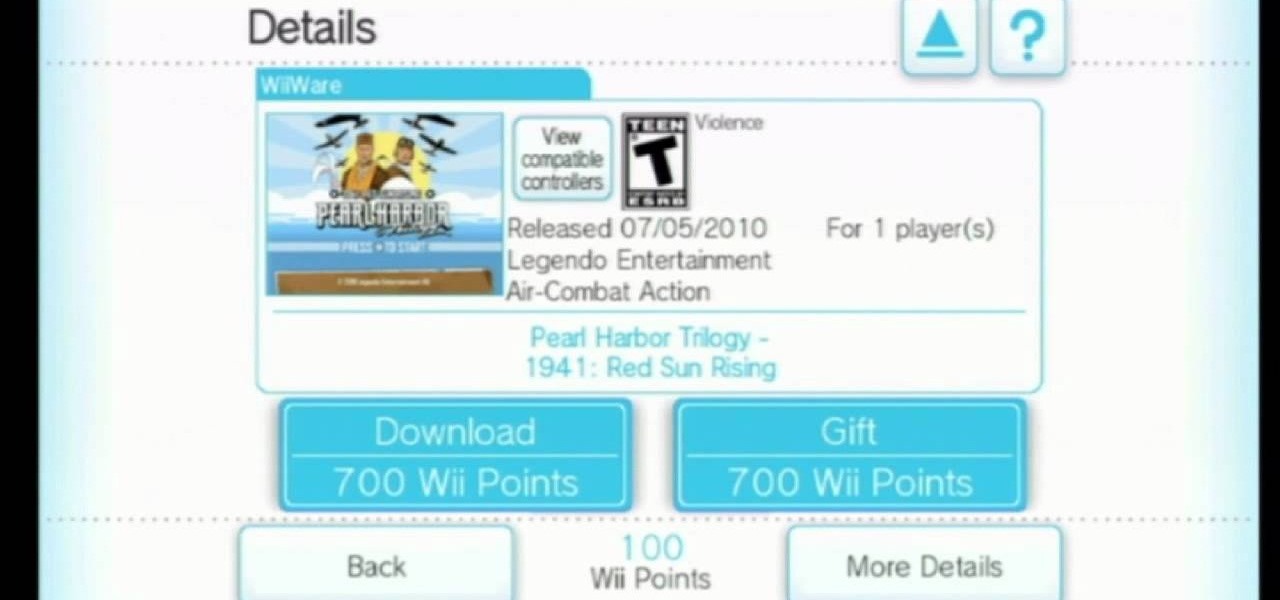
This video tutorial will teach you how to use the Nintendo Wii Shop Channel to download and play your favorite console games on your Nintendo Wii. To follow along, you'll need either a WiFi Internet connection or Wii Lan adapter.

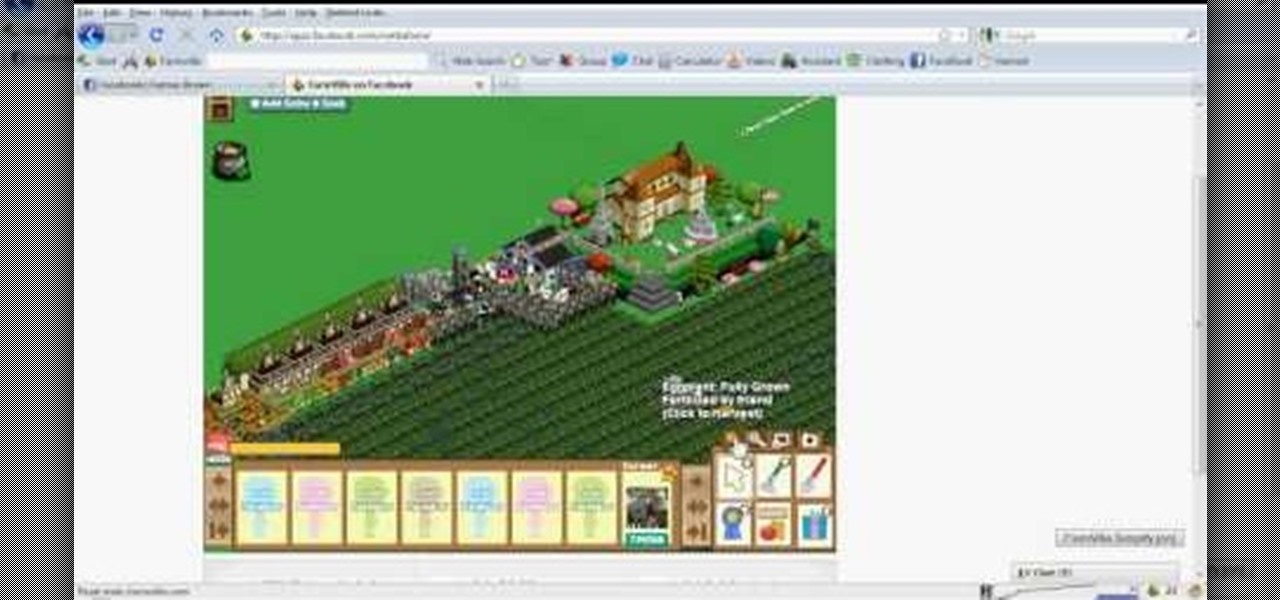
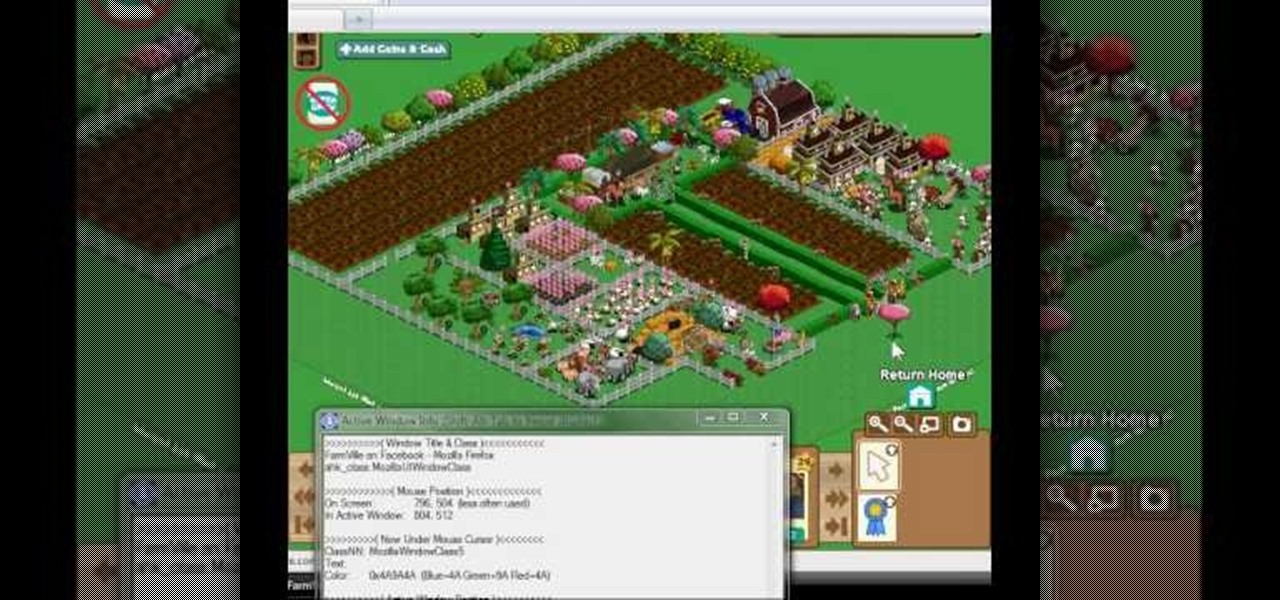
This video tutorial shows how to hack FarmVille (07/02/10).

This is a recent glitch, similar to the chicken coop glitch, where you can make your horse stable completely ready. Just watch this brief video tip to see how to benefit from the Horse Stable glitch in FarmVille (03/09/10). It's a simple glitch in the game that allows you to use a horse that is unready to make a stable 100% ready and be able to collect from it. This is very helpful when you are trying to achieve the HorsePower ribbon on Farmville.

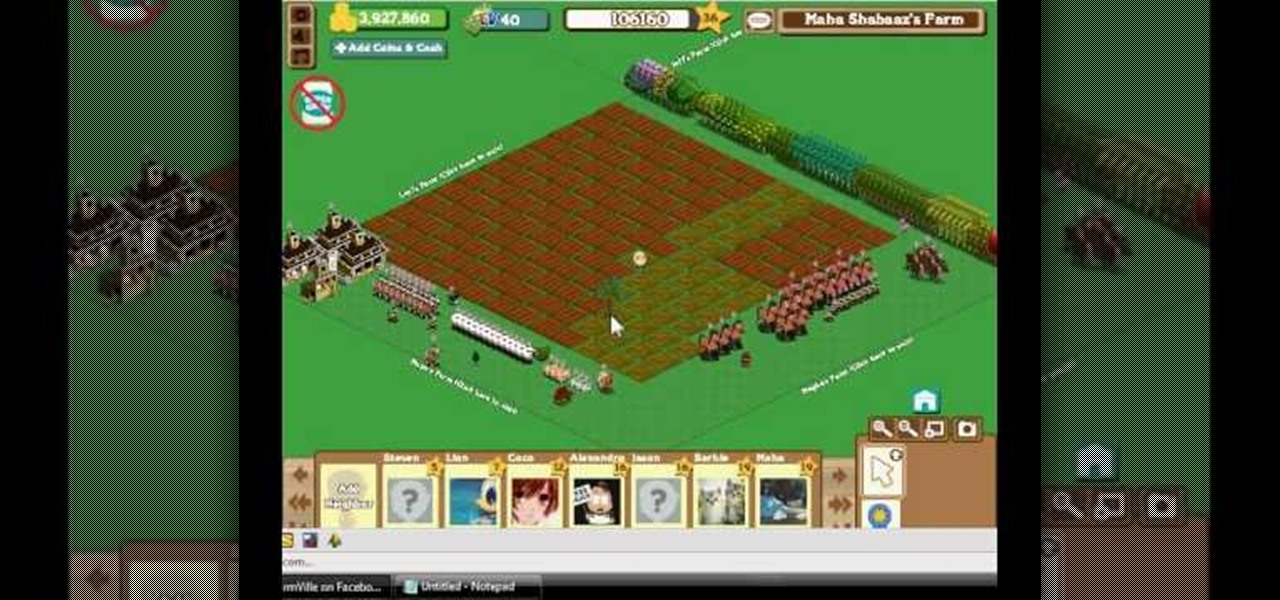
This is an easy glitch in FarmVille that's been around for a long time. Stacking crops. If you want to learn how to stack your crops in FarmVille, just watch this video tip on how to do it (02/16/10). This glitch allows you to grow many more crops than usual, using your limited space on your farm to maximize the most crops in the least amount of space. By doing this glitch, you can easily achieve mastery for all crops in a quicker time frame.

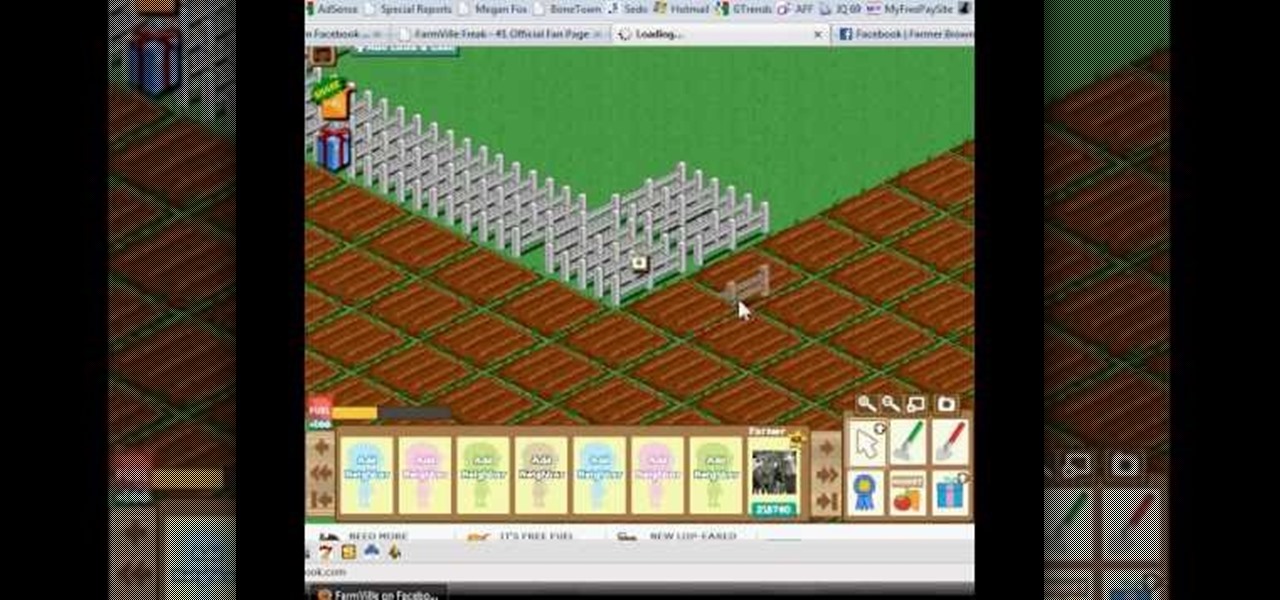
To quickly receive your blue ribbon with the fences in FarmVille, you're going to want to watch this video tip. It's a brief explanation of how you can easily get the Blue "Fenced In" ribbon in FarmVille (01/11/10). BEfore you start this, you will need 75,000 coins and 77 free plots of land to get the blue ribbon.

Everybody wants to find out the answer to "How do I put trees on my crops?", but it's a tricky one to figure out. But this video walkthrough will show you the steps necessary to finally Put trees on top of crops in FarmVille (12/13/09). Just watch and learn.

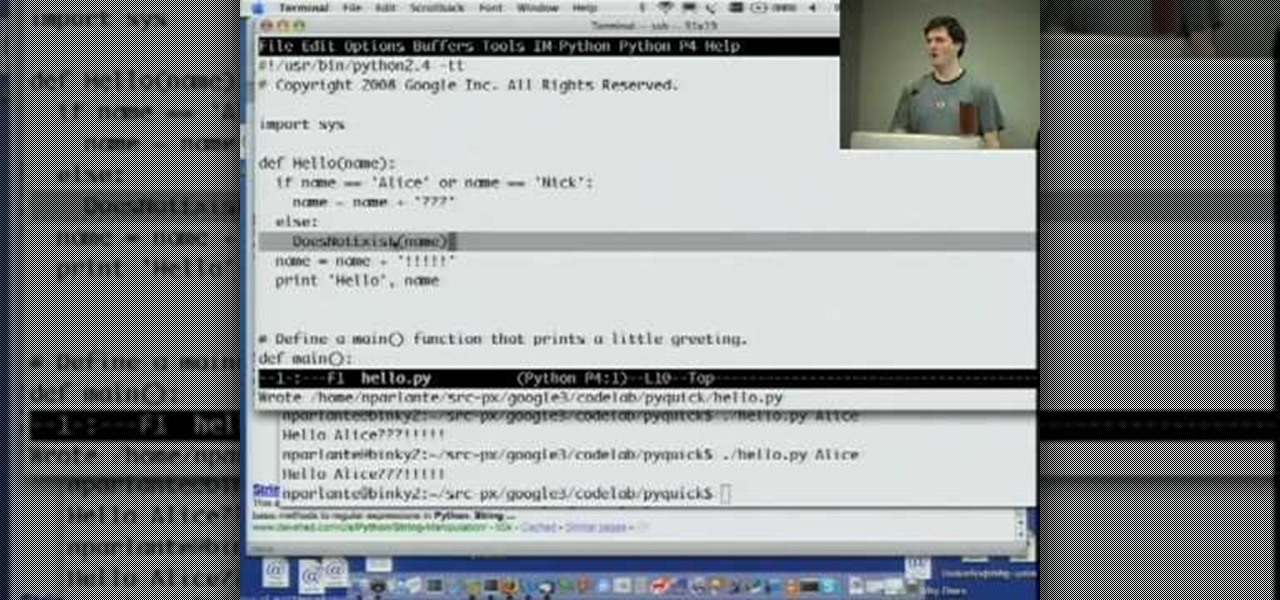
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

Is your farm looking a little bland in FarmVille? Using a basic optical illusion, you can make what appears to be hills!

Since bringing augmented reality features to Search and Maps, Google has made them arguably the most useful augmented reality products in its portfolio.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

The new Samsung Galaxy S8 and Galaxy S8+ phones were announced on March 29 at the Samsung UNPACKED 2017 event. Preorders start on March 30 for the Korean tech giant's latest flagships, and sales officially begin in the US on April 21. Samsung will need a smooth release to win back consumer trust after the Note7 mess, and it's already looking like the S8 won't disappoint.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

In this video the tutor shows how to mount an ISO using Daemon tools. Using daemon tools you can install virtual drives and mount ISO files on them. First download and install the daemon tools from the link given in the video. After installing right click the daemon tools icon in the notification area. From the right click menu go to CD/DVD-ROM option and from the sub menu select the number of devices that you want. You can set up to 4 drives from the options. Dameon setups the drive in a few...

Have you ever wanted to go into another user's account on your computer but had trouble finding the energy to log out, then log out, only to log back into your own account? Well, here's your solution: XNest will let you log in to another user's account from your account in a virtual way. It's very simple to set up and may just help you with your virtual account crisis!

The Fourth of July, the celebration of US independence, as well as the second paid holiday of the summer, has arrived.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

In the technology space, there are certain brands you grow to depend on. Whether it's due to a long, multi-decade track record of success, or new innovations that blow you away, some tech names accrue a rare kind of brand equity with users that's difficult to earn.

While Toyota ranks as the leading automotive brand in the world, the company is a follower when it comes to augmented reality.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

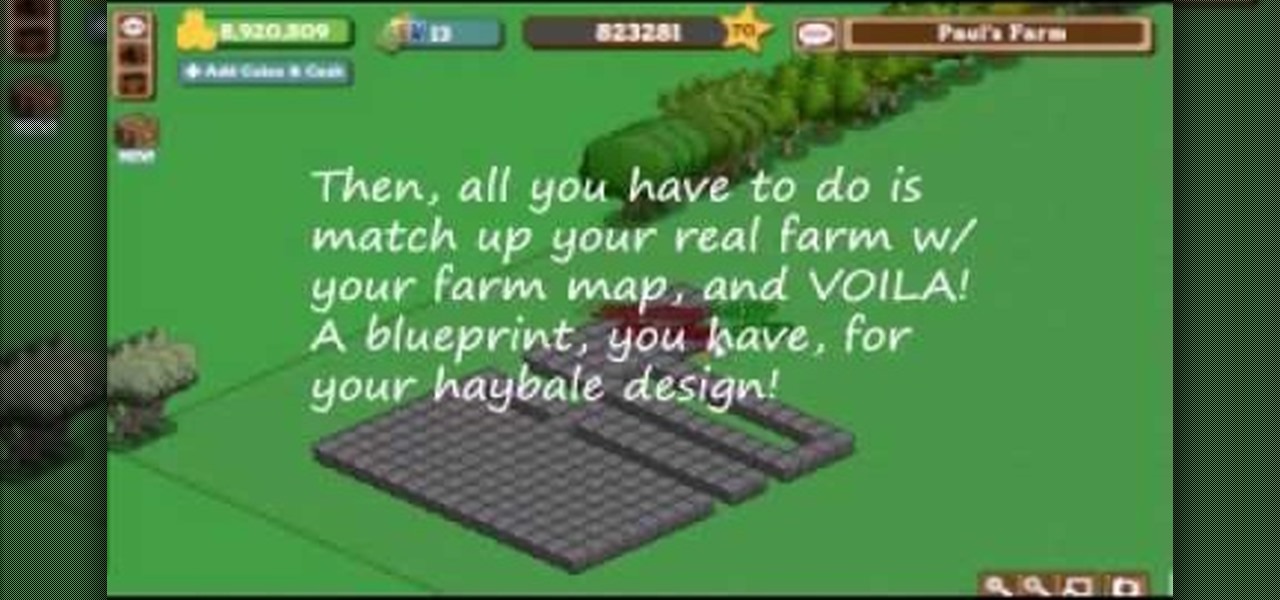
This video tutorial shows how to create hay bale art in FarmVille (10/22/09). Are you a jaded FarmVille player? Do the joys of harvesting just not do it for you like they used to? Why don't you start using FarmVille as an artistic medium? This video will teach you how to use Excel to plot out images which you can then create out of hay bales! The options are limited only by your creativity, now open up Microsoft Office and start creating!