Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.
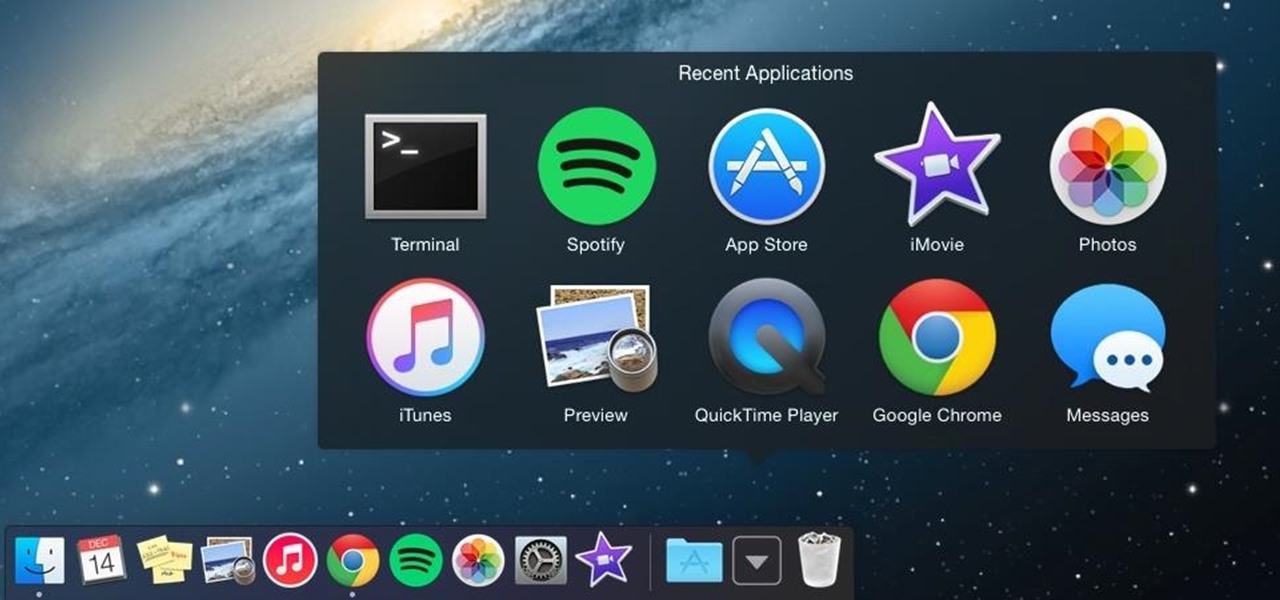
Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

With all of the productivity tweaks and usability enhancements that we cover here at Gadget Hacks, it's nice when we come across a unique and noteworthy app that's simply about having fun.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

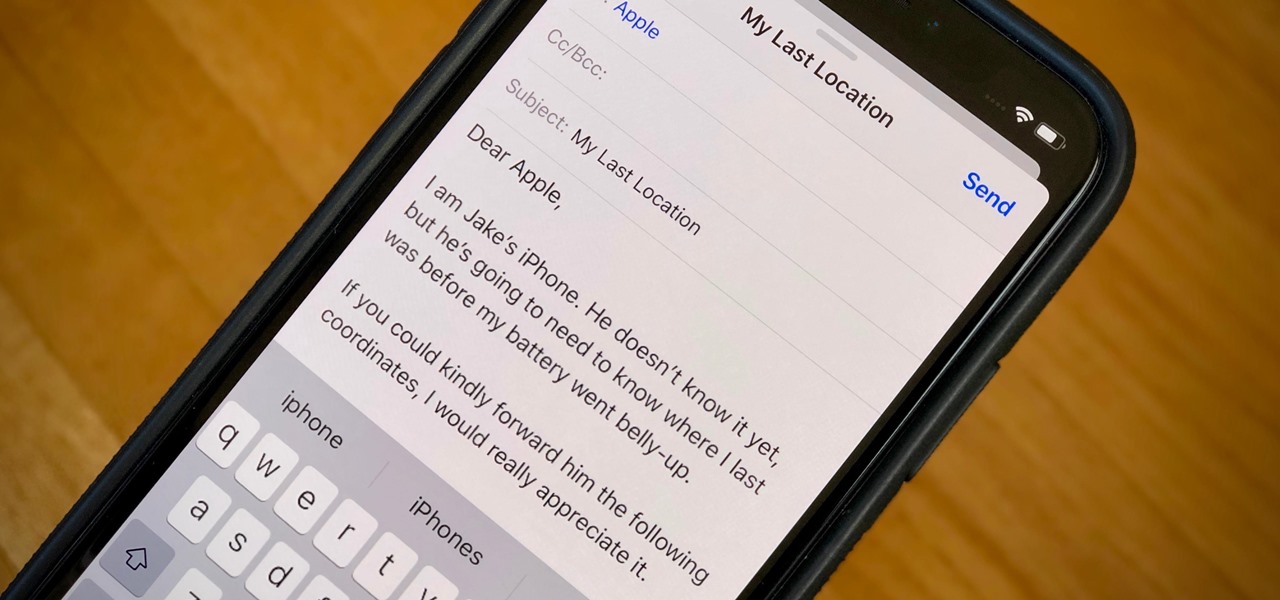
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

Hello, freakje118 here, it is a while ago, but here are the winners of the easter builds! First place is this week for: Fedganac88
Hello, Freakje118 here! Today 13/04/2014 ends the Ice Castle Competition! What a shame only 3 people participated but okay, life goes on! Here are the winners and their prizes

Hey everyone, freakje118 here! This week, the first challenge ever will be to build an awesome and icy ice castle! It can be any size you want but please use the plots. Let your imagination work and make something great of it! you can use any blocks that you want! Ice, water, quartz, wool,.... But remember, it should be an ice castle!

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

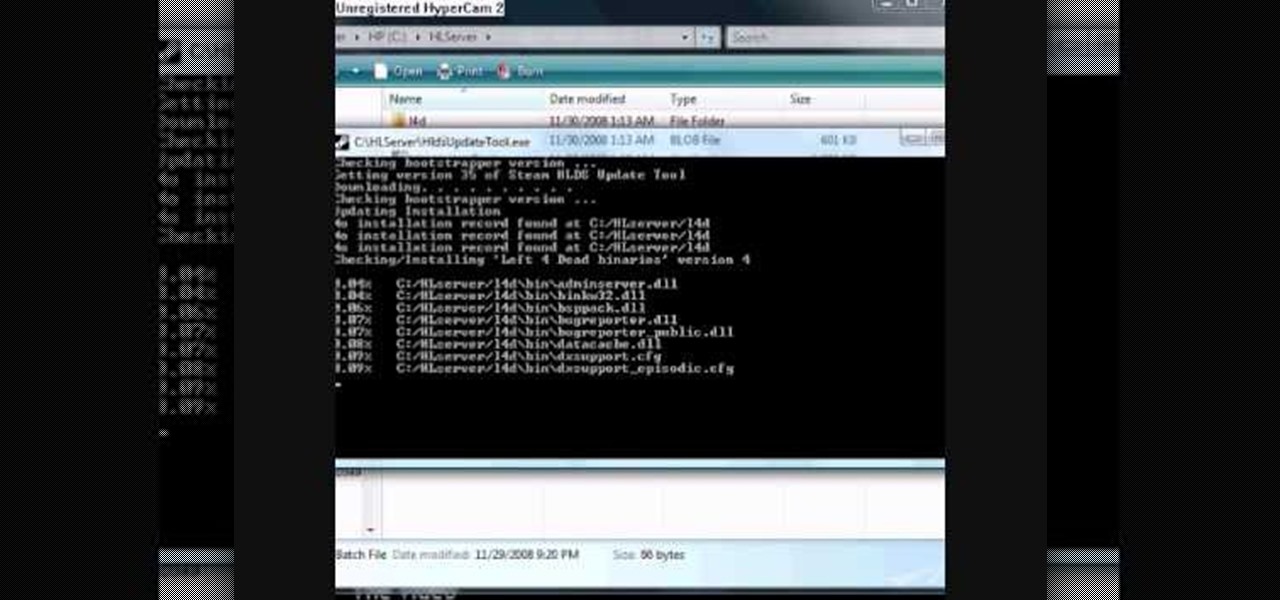
In this tutorial, we learn how to use the HLSW game server organizer program. First, go to the HLSW website and download their product. After this, save it to your computer and then install it. Next, register an account with them, then fill out your information. Now, when you are in the program you will be able to find servers that don't require key checks for games. Then, you will be able to add the servers to your computer. To download the server list, you will have to login, then you will ...

If you don't want to shell out the money to rent a dedicated server in order to host a Left 4 Dead game server, follow this tutorial on how to create one on your home computer. Keep in mind that if you intend on letting other people play it, you will need a fast connection to prevent lag.

The Motorola Droid is getting a little long in the tooth, but it is still a remarkably capable phone with full keyboard, which makes it almost unique among it's Android-based competition. If you've rooted your phone (good for you!) and for some reason want to go back to the stock configuration that your phone was in when you took it out of the box, this video will show you how to do it. One good reason is if you want to update your phone's firmware, which will not work if you phone is rooted ...

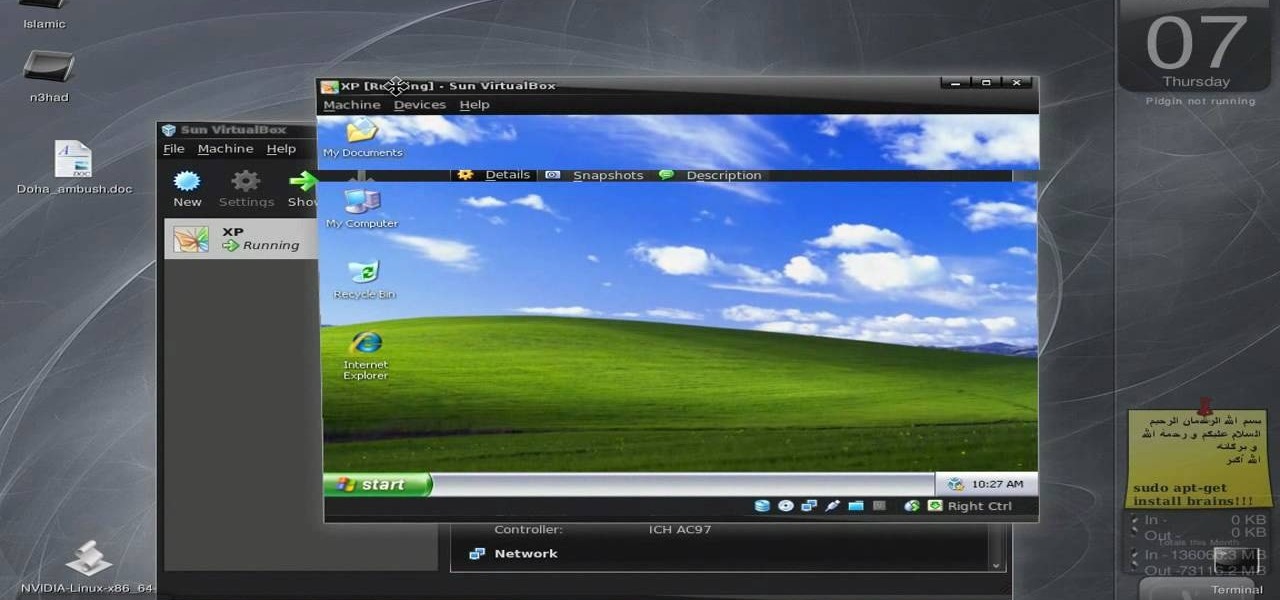
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to share files between Ubuntu (Host) & XP (Guest).

This series of ping pong / table tennis videos demonstrate how to master the table tennis serve. Jim Clegg, a Level 4 Coach with the English Table Tennis Association and Head Coach of the Preston Table Tennis Association, explains and demonstrates how to do a table tennis serve correctly. Serving today is an extremely complicated topic. These are 9 in depth thought processes for a table tennis serve.

Organize both your business and personal files on the HP MediaSmart Server to share and stream music, photos or video to any connected computer on your network.

When you need a file on your Mac as soon as possible, you usually have to get your MacBook or hop on your iMac, Mac mini, Mac Pro, or Mac Studio. But that's too much work if you're in bed, lying on the couch, or outside in the fresh air. Why even bother when you can access that file directly on your iPhone or iPad — without moving an inch?

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

There are several ways to get around location restrictions on subscription sites like Netflix and Hulu using apps, extensions and proxies, but they tend to only work on laptops and computers. Users who want to access content from mobile devices and gaming consoles are usually out of luck.

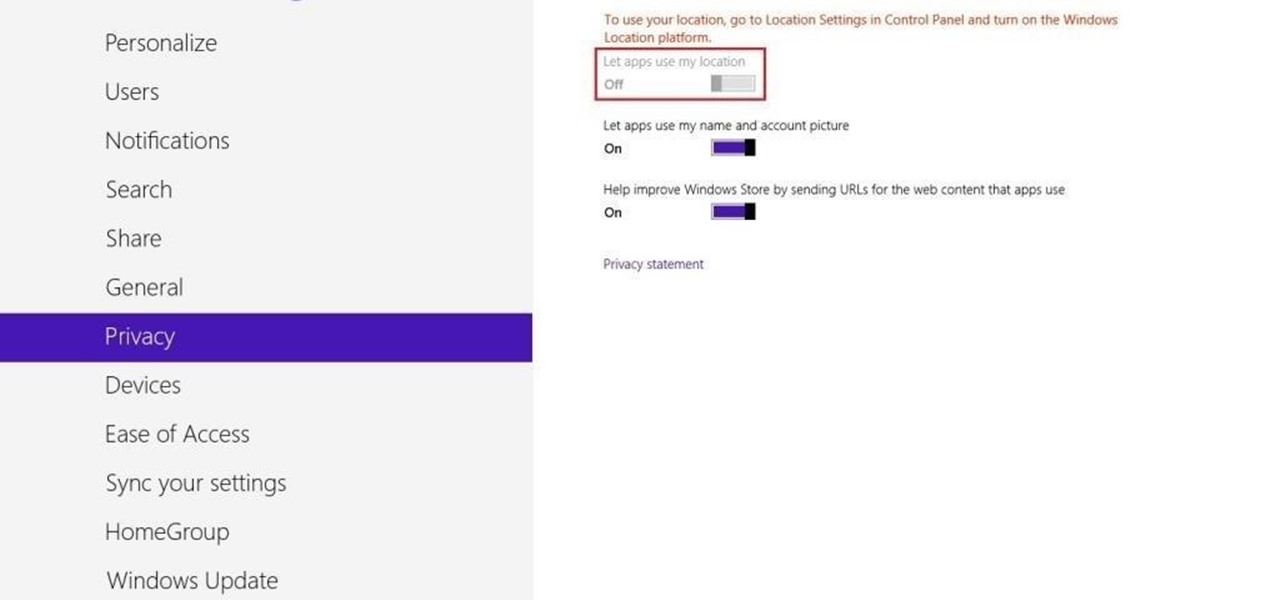
Not only does your mobile phone auto share your location. Now Windows 8 does the same thing. I'm going to show you the two (2) ways to disable that.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

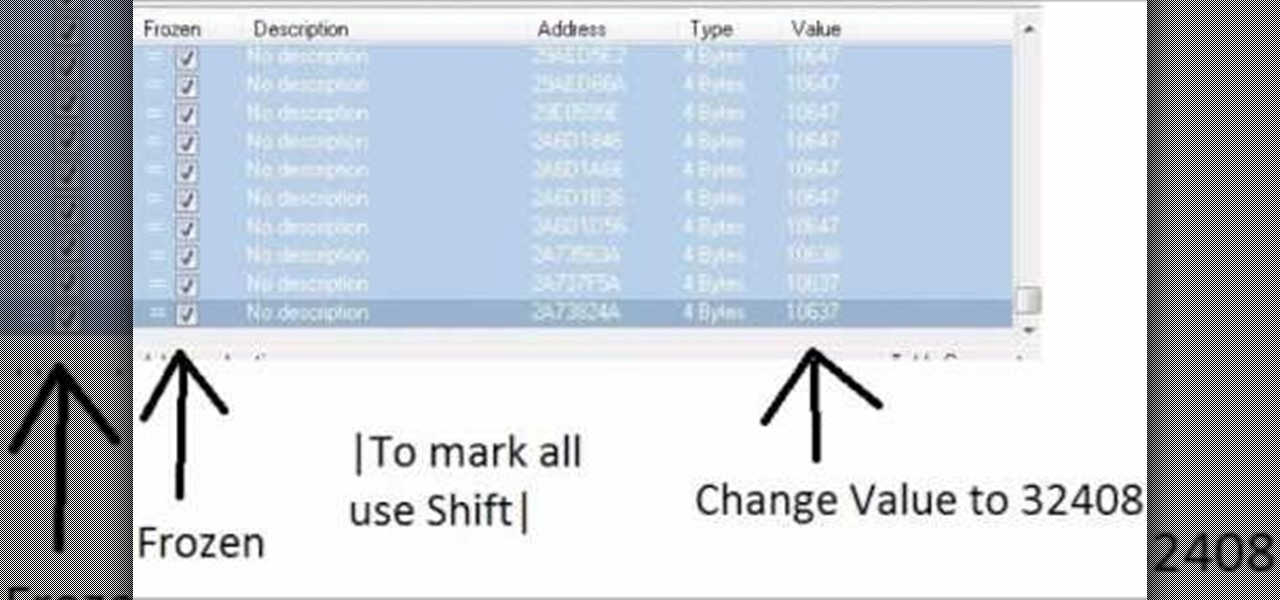
Increase your damage output in World of Warcraft! This tutorial won't work on all servers, and is better on private servers than public. All you need is Cheat Engine - buy some mundane items, and then use the program to turn them into rarer, better items.

There are two parts to the StormShield product: The server components (including the relational database and server) and the various agents that run on each endpoint. Among other things, the agent contains a host-based firewall and policy engine that can be customized to control applications and particular endpoint device features such as USB peripherals and registry entries. So watch this tutorial and learn how to protect your PC computer with SkyRecon's StormShield.

So you've watched this video, done your research, and decided that you want to flash the firmware on your XBox 360 with a LiteOn DG-16D2S rev. 7485 disc drive. Good for you! This video will walk you through the whole process. Be very careful, as messing up in small ways at any point can ruin the results which, when done properly, are really awesome.

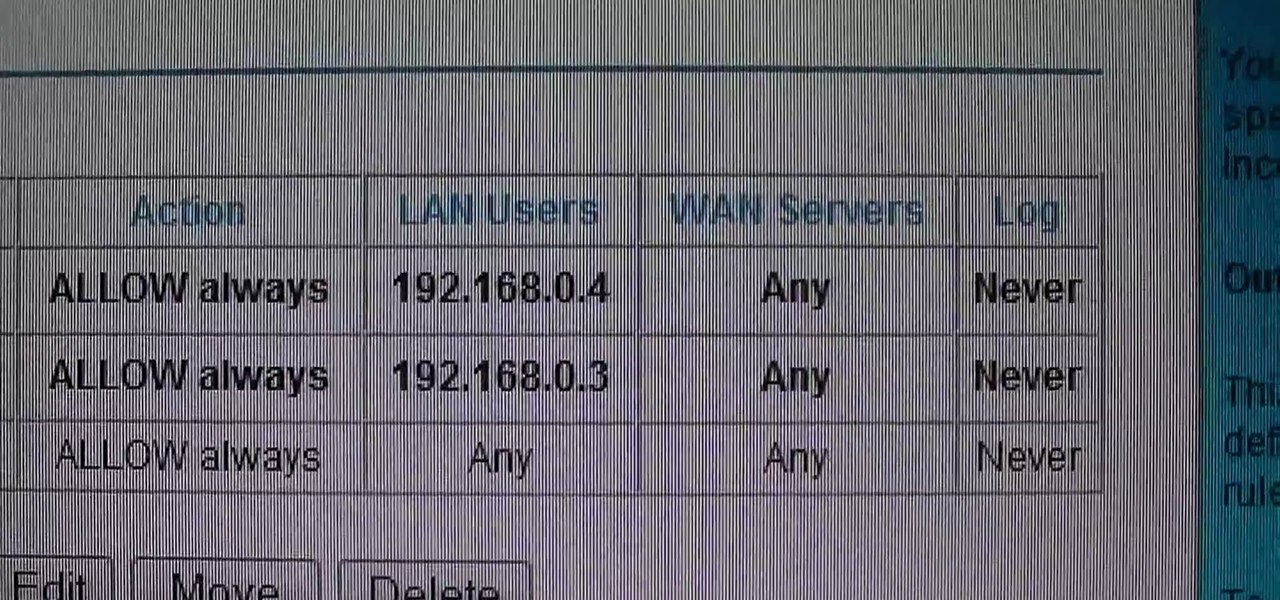
This video shows how to change the NAT type on a PS3. Go to connection settings>network settings>internet connection settings>OK>custom>wired connection>auto detect>manual. Choose an IP address that is different from your router, any other consoles, etc. Click right>automatic>do not use>enable. Press x to save settings, and test your connection. In this example, NAT type is 2. Now go to your PC and open IE. In the address bar, input router IP address, username and password. Go to Firewall Rul...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.