
How To: make a preggie belly cast
Just to prove definitively that I am in touch with my feminine side, to all the doubters, here you go.


Just to prove definitively that I am in touch with my feminine side, to all the doubters, here you go.

One great, award winning How-to. Produced 20 year ago. You might have observed that on Sundays we tend to slow down the pace. Which is to say that we enjoy offering a leisurely How-to on the Lord's holy day. Be patient, Tonto: the subtitling is primitive: and the running time is as long as it needs to be: and yes, it was produced before the frenetic era of the internet.

Cakes. They're delicious and we eat them at birthdays, weddings, and wakes (that aren't ours). In the splendorous world of culinary creations, there is no comestible that allows for such decorative flexibility as the cake. It can be simple, it can be complex. It can be amazing, it can be disastrous.

Welcome to the Mad Science World! Hold onto your radiation-shielded hard hats—we're going to be posting a ton of great how-to articles and videos every week, showcasing the maddest of the mad science experiments on the web. We hope you will be inspired to try these projects at home, but always remember—safety first!

Kevin Van Aelst creates witty visual "one-liners" by recontextualizing everyday, ordinary objects. With a few simple tweaks, the viewer recognizes a roll of tape as the ocean or reads gummi worms as chromosomes or understands mitosis through the use of sweet, sugary donuts.

For some reason, McDonald's hamburgers are mysteriously unsusceptible to Mother Nature's inevitable toll of decomposition. Yep, you pretty much have to dip a McDonald's cheeseburger in acid if you want it to decompose. So we're left with the question: Why? Why does a McDonald's hamburger retain its original shape, color and texture after 12 years?

Wow, kids and their wild imaginations... Monster Engine is a gallery of kids drawings copied by painter Dave Devries. The project began in 1998, when Devries posed the simple question: What would a child's drawing look like if it were painted realistically?

Diego Stocco is back (previously, the incredible Music From a Tree). This time Stocco has created the experibass:

Oh yeah. I finally found a sublime joke which every girl should try. That tasty concept, we at Wonderhowto call the "category-crossover." Food + Prank. Martin + Lewis. Ebony + Ivory.

This video works. Watch this ordinary guy shovel mounds of bone-dry corn starch into his mouth. A combination of six step tutorial and gratuitous chestpounding, this video is a simple example of the cornstarch (or flour) bomb.

tell if she is a hooker or a cop. His arrogance too great. Above the law. Not even this tutorial would have slowed him.
Fort Leonard Wood Public Affairs director Tiffany Wood has provided the first official response to the shocking U.S. Army document that outlines the implementation of re-education camps, admitting that the manual was “not intended for public release” and claiming that its provisions only apply outside the United States, a contention completely disproved by the language contained in the document itself.

Watch this video to learn how to make a stencil for graffiti and attach it to a public place with wheatpaste.
Education Laws: Compulsory Education Law

Google+ launched their API for public data today. For now it provides read-only access to public data in the form of People & Activities. Here are some links to get you started:

Any random public bathroom in anytown USA. Release bugs or mice or any other critter, real or fake, and see what happens as people are using the john or urinal when the critter (s) runs past their feet! No one should really get hurt with this prank other than maybe making a massive mess or a random heart attack Idont have a picture of this actually happening so I present you my doggie. He says "WUZ UP"

This tutorial will show how to use GPG and the FireGPG plug-in to encrypt and decrypt messages in Gmail. GPG is an open source implementation of OpenPGP (Pretty Good Privacy) , a public-key-encryption system. With public key encryption you don?t have to give away the secret key that decrypts data for people to be able to send you messages. All senders need is the public key which can only be used to encrypt, this way the secret key never has to be sent across unsecured channels. Encrypt Gmail...

As many of my viewers know, I have an interest in metadata and how it can be used in a pen-test. Thanks to PaulDotCom I found out about a tool called Metagoofil that makes it easy to search for metadata related to a domain name. Use Metagoofil to get metadata from public documents.
Sputnik, Apollo and the Space Race. If you watched the State of the Union address last night, you probably heard President Barack Obama mention those three things.

In the dojo, what ISN’T said is often as important as what IS said. To most of us who’ve been raised in the USA, the reticence we encounter in the dojo can be off-putting. American society is very “content” oriented. Our legal contracts, for instance, run for pages and pages. Everything needs to be spelled out. In “context-oriented” societies there is far less reliance on such a literal approach. Much more importance is placed on the relationship between the two parties entering into an agree...

FALLEN FRUIT

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.

Circle = List Share = Post

Artist Robert Wechsler has salvaged and reassembled 9 bicycles into a carousel arrangement. The best part about the project? Wechsler leaves his bicycle-go-round in public places for strangers to ride. Imagine stumbling across one of these in a public park! Genius.
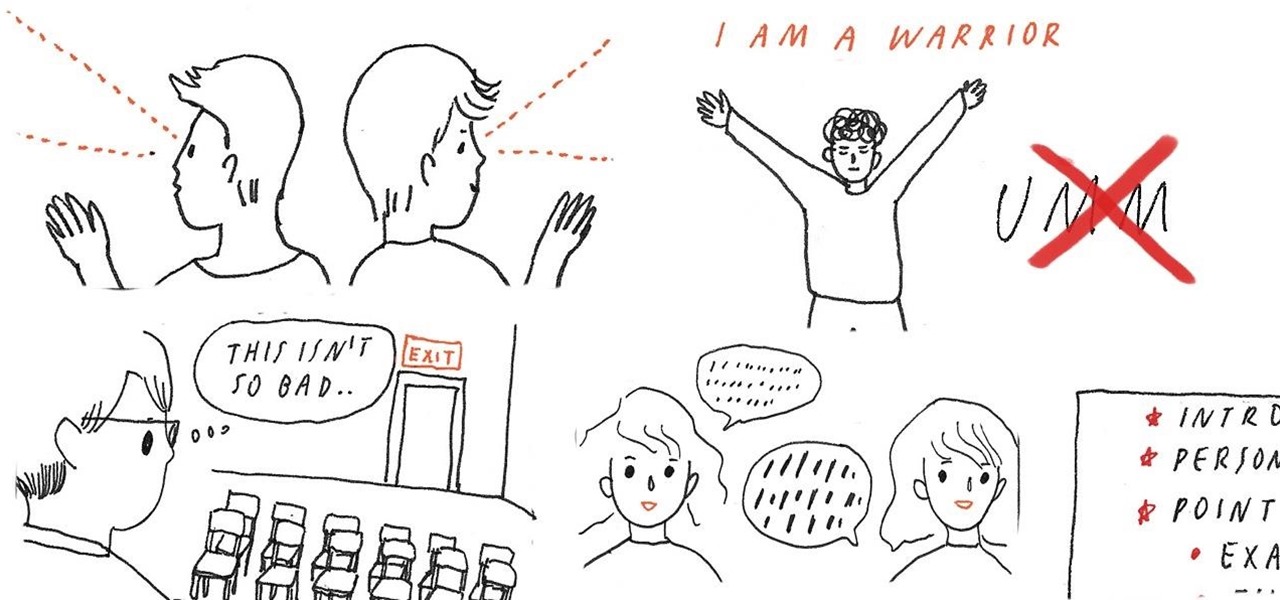
If the idea of giving a speech in front of a huge audience freaks you out, you're in good company. Approximately 75% of all people experience some degree of discomfort or fear of public speaking. Fortunately, with a lot of practice and a few mind tricks, public speaking doesn't have to be such a big, scary thing.

Remember Dan White's "Twinkie defense" in 1979? Well it turns out that the the ability to convert food into glucose is correlated with the ability to control oneself.

Our friends at Graffiti Research Lab were detained in Beijing over the weekend on charges of “upsetting public order”.

The main idea behind this prank is to have the publics attention/reactions in the city. Get people dressed up as old men

After the media outcry of Google Buzz's privacy issues, Google has set its goals on making the privacy parameters of Google+ simple to learn and as explicitly manageable as possible. No small feat.

Warnings MTV and its producers must insist do not attempt to breastfeed grown men. Do not under any reason breastfeed 37 year old wee people in public.

ok i know lately the jack ass guys have had to resort to the old man bit to get some funny stuff in joe public so iv had this idea first as a high school prank but my friends thought it was just wrong so i assume its perfect for you guys (at least i think it would make a good prank) anyway. the prank goes that we go to some random public pool and fill the whole thing up with red die or enough to make it look like a body was thrown in there and then just throw some random plastic body parts li...

Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websites let ad companies track our private usage. We've seen how Facebook mucked up their privacy controls. We even saw how websites like Gawker are prone to hackers stealing user information. And now, Etsy has made what was ...

Google's much anticipated eBook Store has finally opened. As of today, the digital bookselling enterprise is awaiting your needs, with over 3 million eBooks to read directly on the web or on other platforms, like Android, iPhone, iPad, Sony and Nook devices.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.
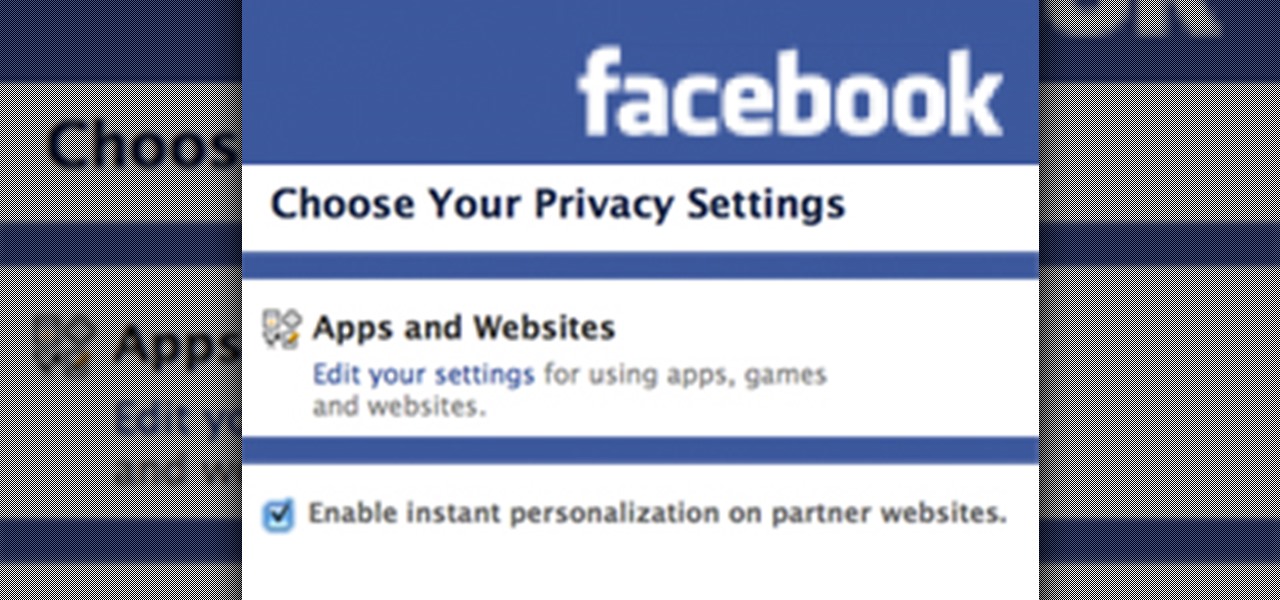
Instant Personalization. If you have a Facebook account, you've probably heard of it by now. If not, you need to educate yourself— and fast. Because they recently made some changes, affecting your privacy settings.
The Minnesota Department of Public Safety issued a press release today announcing the suspension of a drug recognition program conducted by the Minnesota State Patrol. The program was exposed earlier this month by activists and members of Communities United Against Police Brutality in Minneapolis.

You set up a toilet, could be a public toilet, or one at a fair ( it doesnt really matter where as long as people use it ), and play certain pranks when people are on it. When people they sit down they could get electricuted, stuck to the toilet, you put cling film over the toilet, a monter pops up when they lift up the toilet seat, when they flush the toilet poo explodes everywhere. That kind of thing!

Purchase a Megaphone Get in one of your mates car