The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.
Did you take a vacation this holiday season? It appears Apple did. After the release of iOS 13.3.1 developer beta 1 (then public beta 1 one day later), iOS beta testing went silent for almost a full month. With 2019 now in the books, it seems Apple is back to work, as developers received iOS 13.3.1 beta 2 today, Tuesday, Jan. 14.

In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

The year 2018 was a rough one for Snap, the company behind the Snapchat app and the Spectacles wearable camera device. From executive departures to reports of slowed user growth, the company that once spurned Facebook's multibillion-dollar advances is now facing a moment of truth as it stares down its uncertain future.

Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public beta opened up just five days after the release of iOS 11 developer beta 2, so iOS 12 is pretty much right on track in that regard.

Apple released the third beta for iOS 11.4 on Tuesday, May 1. This update comes exactly two weeks after the release of the second beta, which, in addition to adding a new wallpaper, fixed issues with AirPlay, Music, and Keychain. The only noticeable change in beta 3 is a fix for unresponsive 3D Touch.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

The augmented reality business was all about audiences this week. Vuzix looked for an audience with the Supreme Court of New York regarding a defamation lawsuit against an investor. Magic Leap held an audience with royalty, showing off the Magic Leap One in a rare public appearance. And Snapchat wanted to remind its consumer audience of all the things its camera can do.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Apple just pushed out iOS 11.2.5 beta 7 today for iPad, iPhone, and iPod touch to both developers and public beta testers. On Wednesday, Jan. 17, beta 6 was released, and there were two betas the previous week. With Apple promising a patch for "ChaiOS" next week for everyone, it's like iOS 11.2.5 will be that update.

Whenever you attend or remotely watch a major Apple event, you're likely to see Phil Schiller, the company's senior vice president of worldwide marketing, unveiling a brand new product on stage. Outside of an official event, Schiller is the second most likely person (after Apple's CEO Tim Cook) you'll find delivering a rare tidbit of new Apple info or perspective to the public.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

The final developer version of iOS 11 was leaked a few days ago, but Apple quickly stopped signing it so nobody else could install it. With Apple's Sept. 12 event now over, the Golden Master (GM) version of iOS 11, the same version that will be released to everyone around Sept. 19, is available to install again — and anyone can get it.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

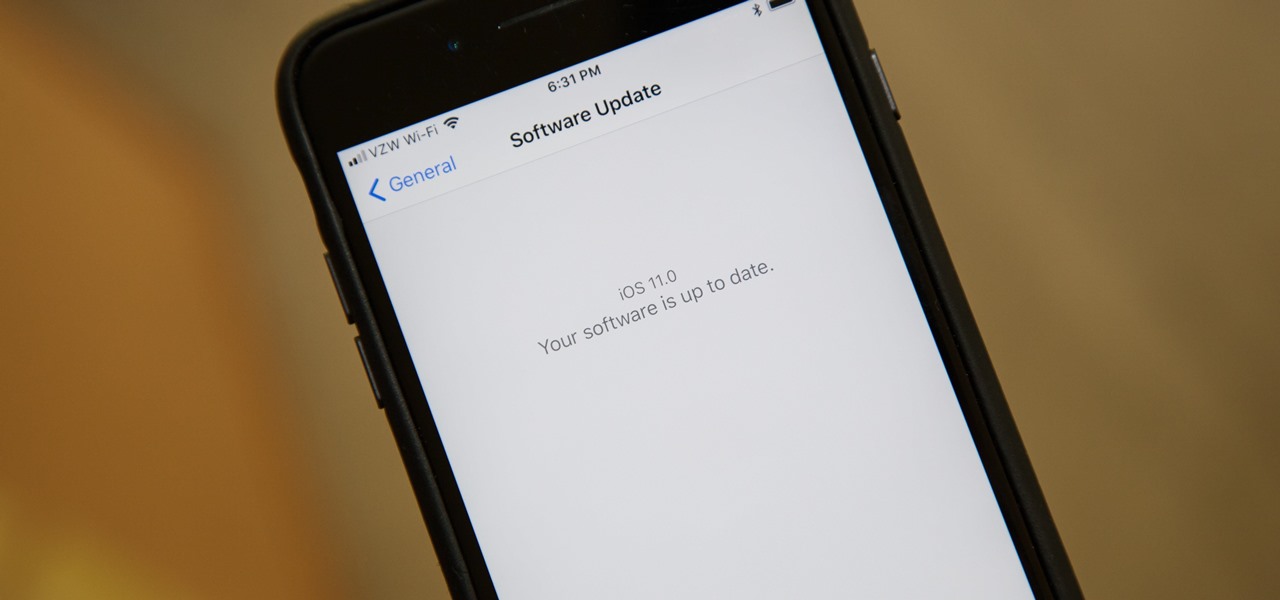
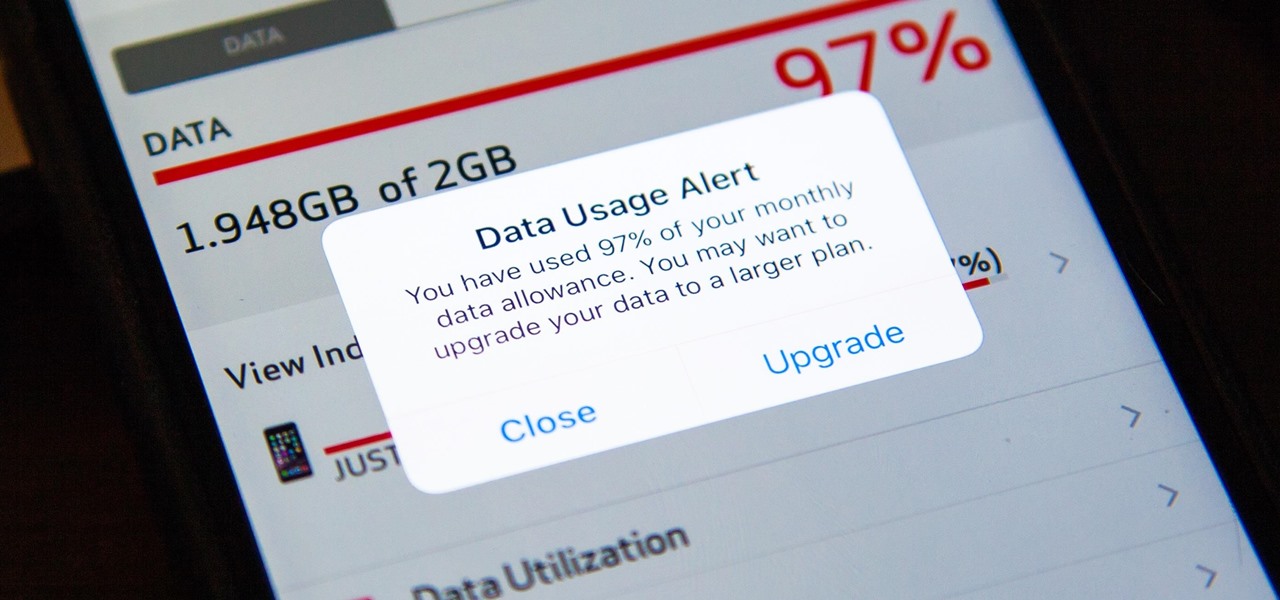
I was one of the first to install the iOS 10 developer beta, and I remember thinking that everything was working insanely well compared to the first iOS 9 developer beta—but then I got a warning that I used 90% of my data 11 days into my following cycle—one day before I updated to beta 2.

Google switched things up this year by releasing a developer version of Android N far ahead of I/O, but that's not the only convention they've done away with this year. For the first time, Google will accept name suggestions from the public.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Hello guys, today I wanna share how to create a drag and drop with listbox using VB.net. Just copy and paste the following code under public class.

iPad, iPhone, and iPod touch owners: it's that time again. iOS 8 has been released to the public, and those who have been eager to update since Apple's WWDC announcement won't have to wait any longer. Since iOS 8 promises to pack a bunch of new, really great features, it's time to present your options for getting on the latest and greatest for your Apple device.

Samsung has shown off its new smartwatch, the Gear S, and its two new Notes, the Note 4 and the Note Edge at IFA 2014, but it had one more trick up its sleeve.

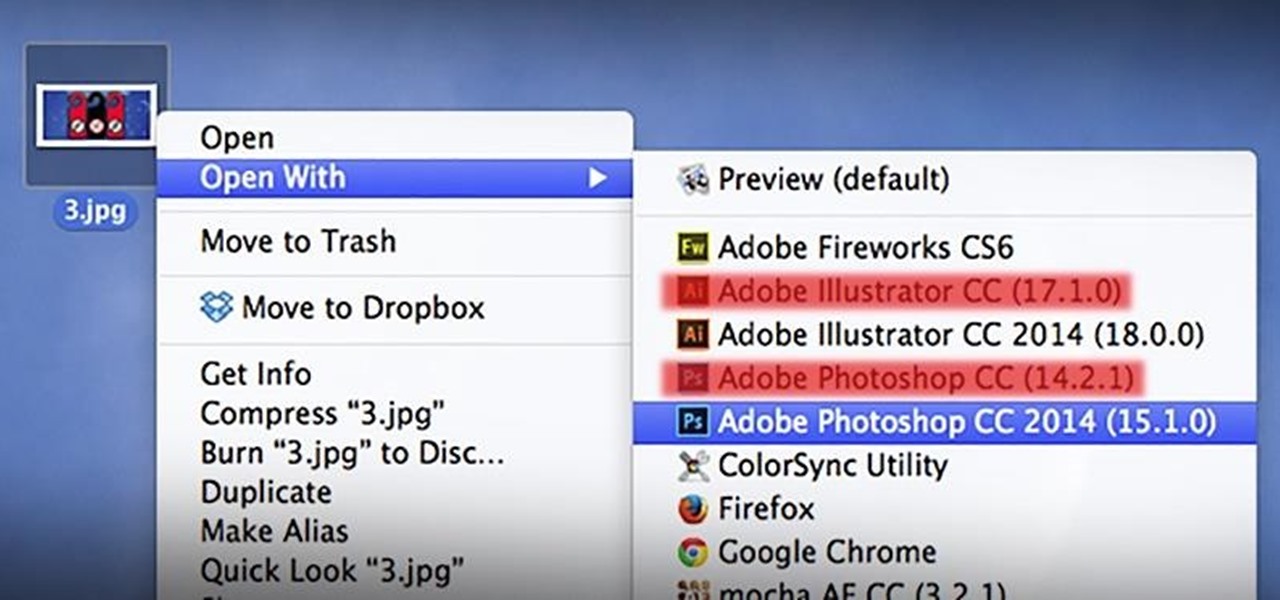
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

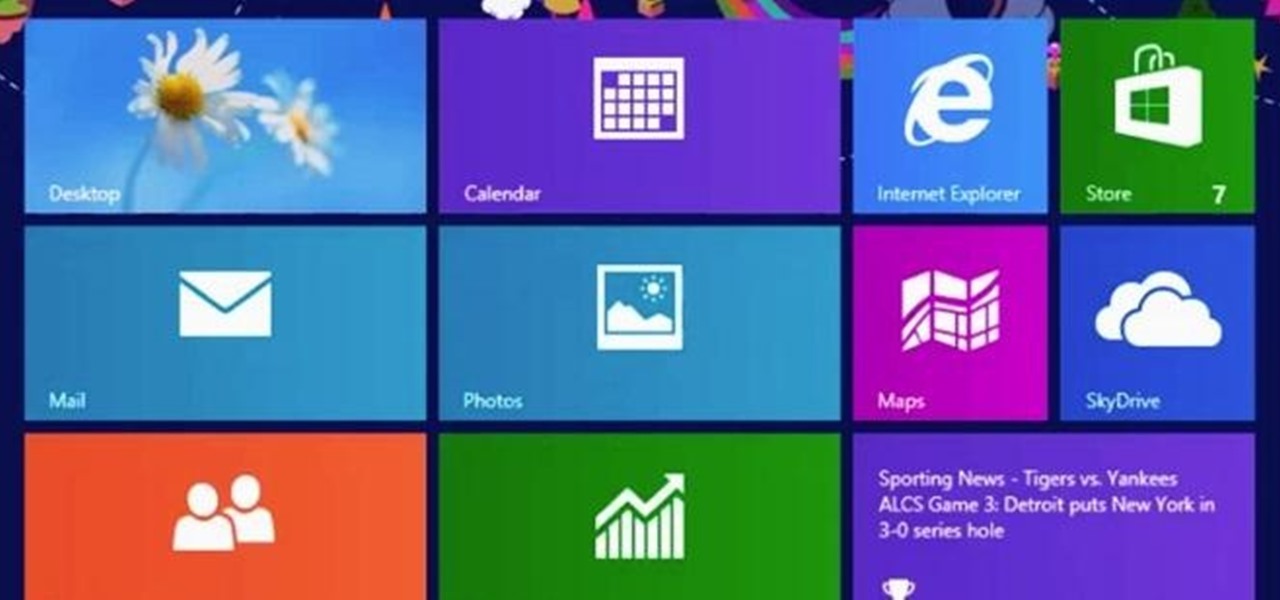
The new Windows 8 is only days away from its mass public release on Friday, October 26th. And there's a ton of new features you'll need to get used to, either on your computer or your tablet. One of them is the Live Tiles, which provide users with live information and is way more aesthetically pleasing than the traditional Windows layout. The new Tiles system adds another level of functionality and information for the user, but it definitely takes some getting used to. The video below by Pure...

In this video you will see how to use FTP client to move files to GoDaddy.

How to use XAMPP to set up a .com domain name for yourself.

Apple seeded the second beta for iOS 14.7 today, Wednesday, June 2. The update (build number 18G5033e) comes two weeks after Apple released the first 14.7 beta, and nine days after the company released iOS 14.6 to the general public.

Earlier this month, the rumor mill suggested that Apple was gearing up for a Mar. 23 event, with a possible release of iOS 14.5 to boot. That event, as we can now see, never came to be. It seems Apple is also not quite ready to unveil iOS 14.5, either, as we now have a fifth beta to test on our iPhones.

Over half of all Americans have listened to at least one podcast, and that number is growing every year. With over one million podcasts and 30 million episodes in existence, there's no end to discovering new voices expounding on a range of topics.

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

The deadly Wuhan coronavirus outbreak has not only has claimed lives in China but also has caused disruption around the globe, particularly in the tech industry. To date, the virus has claimed more than 1,000 lives in China, according to the country's officials.

While Elon Musk is in Los Angeles showing off the future of personal transport via the Cybertruck, another, unaffiliated group is taking one of his most popular ideas to market, with augmented reality as a key part of the plan.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Already among the first game makers to add augmented reality content to an existing game upon the launch of ARKit, Zynga is breaking new ground with mobile AR once again.