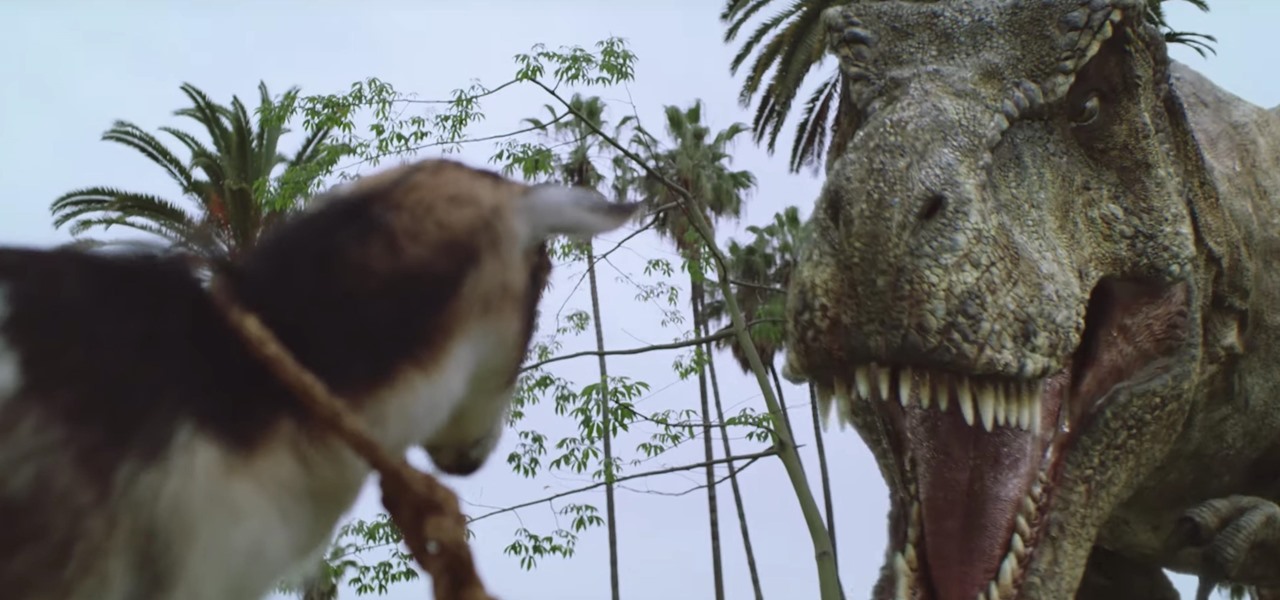It's a bit surprising that Apple hasn't seeded beta testers the release candidate for iOS 14.5. The next big iPhone update is rumored to be out soon, so it stands to reason that we'd see a "final" version of that software hit our test devices rather than another beta. But that simply isn't the case here, as Apple decided to release a seventh 14.5 beta.

Apple released the second public beta for iOS 14.4 today, Wednesday, Jan. 13. The most notable addition to this beta isn't user-facing — baked into 14.4 beta 2's code is evidence that Apple will start issuing warnings on iPhones using unapproved cameras. Of course, those warnings will only apply to phones that have had their cameras replaced.
Apple released iOS 14.3 public beta 3 today, Wednesday, Dec. 2. The update comes three hours after Apple released 14.3 developer beta 3, and 15 days after Apple released iOS 14.3 beta 2 for developers and public beta testers. The latter introduced a change that bypasses the Shortcuts app when using a custom icon on the home screen.

Apple released iOS 13.5 for iPhone on Wednesday, May 20. The update came just two days after the company seeded beta testers iOS 13.5's GM (golden master), the build everyone would get if all went well. While only available to beta testers, the GM is the same software as iOS 13.5's stable release.

Apple just released the first developer beta for iOS 13.4.5 on Tuesday, March 31. The update follows the previous week's stable release of iOS 13.4.

March is looking to be an eventful month for Apple. Even with coronavirus throwing the tech industry into uncertainty, we still expect Apple to release the iPhone SE 2, the long-awaited follow up to the iPhone SE. Is it possible we'll also see iOS 13.4 fully released this month? We wouldn't be surprised if we do, seeing as Apple just released its fourth developer beta.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

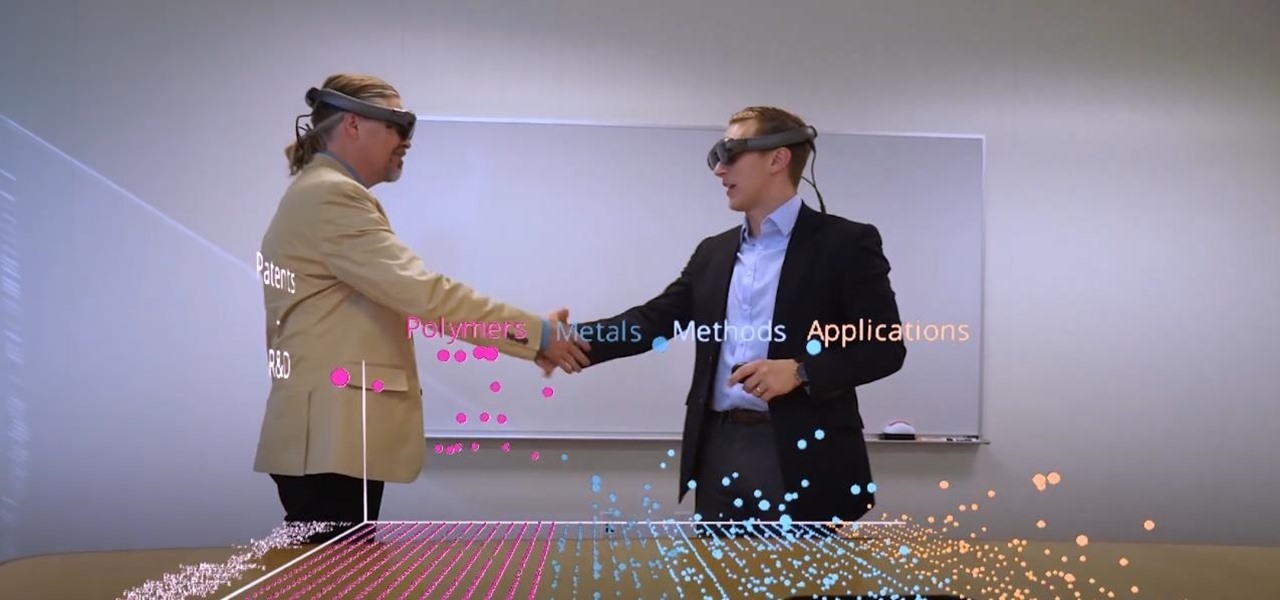
Thanks to the expanding universe of augmented reality tools being made available, increasingly, anybody can liven up sleepy office meetings with immersive computing.

The next phase of the holographic display is upon us, and Looking Glass is aggressively making sure that it's at the tip of the spear when it comes to leading that charge.

The legal drama surrounding Chinese startup Nreal and Magic Leap continues, and now we finally have an update.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

With Android 10 hitting the streets (at least for those mobile devices that get quick updates) and the public release of iOS 13 dropping on Sept. 19, Google is releasing an update on Thursday to ARCore that adds some fantastic new benefits to its cross-platform capabilities.

Apple's annual iPhone launch is set for Sept. 10 and iOS 13 is expected to be released soon thereafter, but it appears that the likelihood of a "one more thing" reveal just got a big boost.

Apple shocked us all yesterday when it released iOS 13.1 developer beta 1. It was an unprecedented move since iOS 13.0 is still in beta testing and since Apple has never pushed out a "point" beta release before the stable base version. And now, you can get your hands on iOS 13.1 for iPhone if you're on the public beta.

Apple slowly rolled out its new credit card, Apple Card, throughout August, but announced on Aug. 20 that it's now available to all qualified users in the US. Here's the problem: it's not totally obvious how to apply. Without any notification, directions, or clear settings, how do you even fill out an Apple Card application? Luckily for you, we're here to show exactly how to find it.

With Android 10 "Q" right around the corner, now would be a great time to get accustomed to the new system-wide dark mode it's bringing with it. Dark themes not only allow for more comfortable viewing at night, but can also consume less battery at the same time. With a single button tap, you'll be able to enable this new dark theme for all compatible apps without having to jump through hoops.

The long tease that is the release of Minecraft Earth continues, this time with an opportunity to start playing what might be one of the hottest augmented reality games ever, before the general public.

There's nothing wrong with indulging in guilty pleasures on Spotify every once in a while — we all need a little Coldplay and Creed in our lives. The only problem is, all of your friends and family might be watching. Anyone that is following your Spotify account can potentially see what you're listening to, but there are several ways to hide this shameful and embarrassing activity from the world.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Players who have stuck around with location-based game Jurassic World Alive just got a new treat that makes the augmented reality experience even more fun.

Snapchat isn't the only tech company transforming landmarks with augmented reality for Pride Month. About four miles southwest of New York's iconic Flatiron Building, which is getting its own Pride makeover via Snapchat's Landmarker AR, Stonewall National Monument is also receiving some augmented reality treatment by way of the Stonewall Forever mobile app published by the Lesbian, Gay, Bisexual, and Transgender Community Center (better known as The Center) in partnership with Google.

With the defending champion Golden State Warriors and Drake's favorite team, the Toronto Raptors, set to face off in the NBA Finals starting Thursday, Snapchat has gifted hoops fans with a pair of augmented reality experiences.

The potential of augmented reality is often shown in science fiction movies, but a new exhibit marries the genre with very real-world AR technology, to great effect.

Despite the recent gut punch of staff layoffs, Canada-based smartglasses startup North and its Focals are likely to be in the game for a while longer.

If you're an iOS developer, welcome back to beta testing. Apple just released the first iOS 12.4 developer beta today, Wednesday, May 15, just two days after the public release of iOS 12.3. While Apple has not shared any release notes, we know this latest version of iOS will support Apple Card, Apple's upcoming credit card.

If you need some help expressing how you feel to your mom for Mother's Day, Snapchat and Facebook are here with some augmented reality help.

The long-awaited augmented reality game based on the Harry Potter franchise from Pokémon GO masterminds Niantic is closer to release, as the developer has begun public beta testing of the app.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

The long guarded veil of mystery surrounding Magic Leap for years was finally lifted last year when the company revealed its Magic Leap One device.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

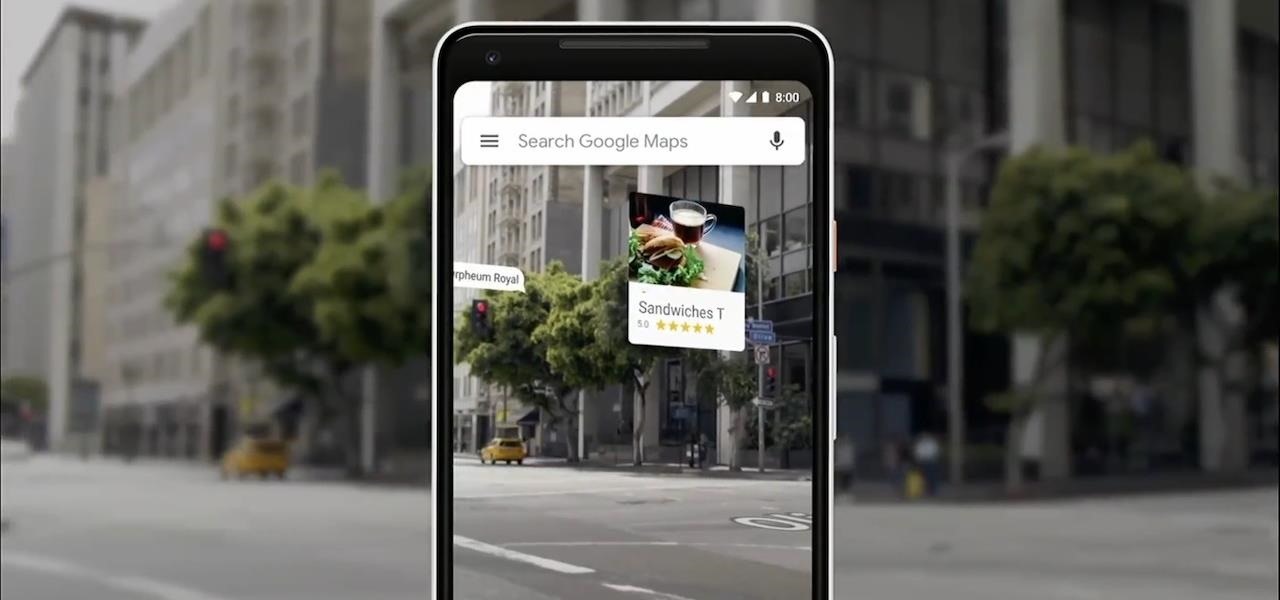
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

A year after making a splash at the annual Consumer Electronics Show in Las Vegas with Amazon Alexa integration, smartglasses maker Vuzix is bringing a notable weather app to its Blade smartglasses for the 2019 edition of the conference.

There is not a single museum that houses all of the 36 paintings of Johannes Vermeer, so Google decided to come up with a solution to give art aficionados a venue to see the artist's work all in one place — your home.

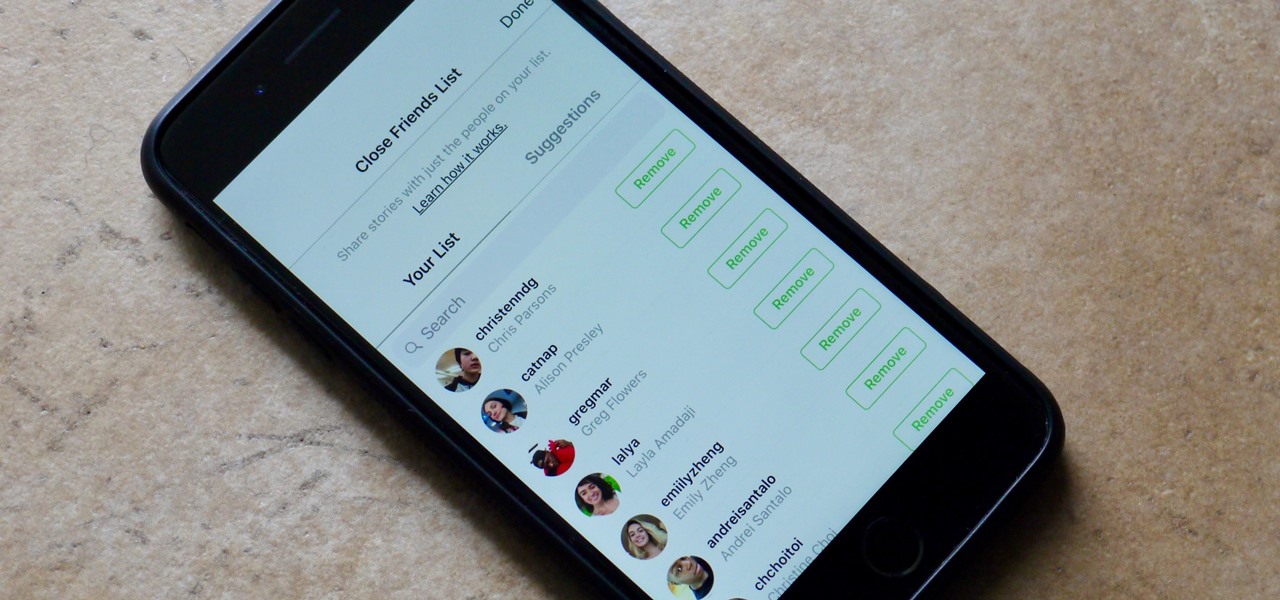
Stories make sharing your day-to-day highlights fun on Instagram. However, other than choosing who to hide stories from, by default, stories don't have much privacy control, especially if your Instagram account happens to be public. Instagram recognizes this flaw, which is what its "Close Friends List" is all about.

Apple released the third beta for iOS 12.1.1 on Thursday, Nov. 15. This update is not much of a surprise, as it comes just a little over one week after the release of dev beta 2. As with that beta, we expect Apple to release the 12.1.1 public beta shortly, possibly as soon as this afternoon.

After publishing two batches of videos from its L.E.A.P. developer conference, Magic Leap has made the session on Seedling from Insomniac Games available to the public.

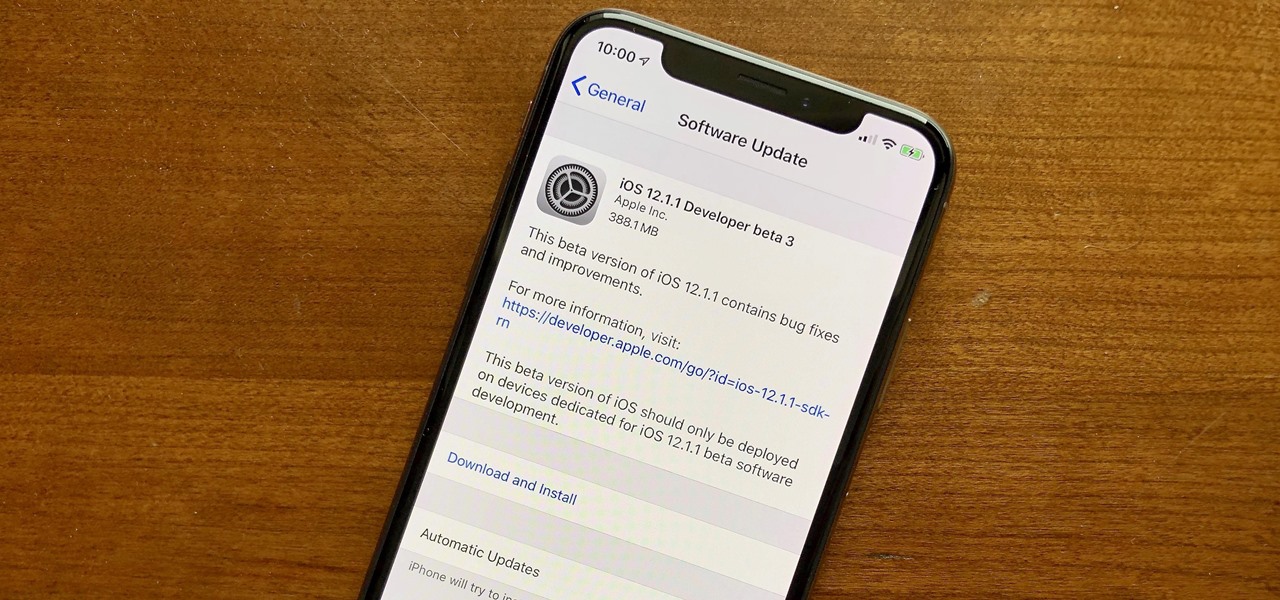
Developers opened their iPhones on Wednesday, Nov. 7, to find an update to the iOS 12.1.1 beta. Apple seeded developers the first 12.1.1 beta on Halloween, marking one week between it and the second beta. It's a quick update turnaround but in line with trends as Apple typically waits at least a week in between beta releases.

Rumors are swirling today that NASA's Jet Propulsion Laboratory (JPL) may have shown us the first public glimpse of the next-generation HoloLens. Are they real? Or just a prototype? We've been digging in all day to find the answers.

If your iPhone XS or XS Max has been suffering from Wi-Fi connectivity and charging issues, Apple just released iOS 12.0.1 on Monday, Oct. 8, as an over-the-air update for all compatible iPhones. The main focus of the update is to give fixes for users going through "Chargegate" and experiencing Wi-Fi issues.