As Hurricane Sandy barrels towards the East Coast, 50 million people are expected to be affected in the nation's most populated corridor. The behemoth super storm is a cause for concern, evident by the massive evacuations. The picture above is an eerie snap of the mostly crowded Times Square subway station in New York. Government officials have warned over half a million people to evacuate their homes and head to higher grounds. To help prepare for this storm, the internet has provided severa...

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

It's no secret that most people who got an iPhone 5 (or upgraded their old iPhone to iOS 6) have been sorely disappointed with Apple Maps. We may all miss Google Maps, but the Google says they aren't even working on an app for iOS 6 yet. Even worse, Google exec Eric Schmidt says they're waiting on an invitation from Apple, and if we know Apple, that could be a while. Users who didn't get an iPhone 5 have had an even worse time of things—Apple disabled 3D maps and turn-by-turn directions on ol...

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

For those of you still waiting for the new iPhone 5, you may be a little annoyed when you start using the new Maps application. If you're one of the many Apple users that has already updated your current iPhone to iOS 6, then you're probably already missing Google Maps. While the new Maps does have turn-by-turn directions and sweet 3D imaging for a few large cities, it misses out on everything that made Google Maps legit. Public transit routes—gone. Street-view—missing. High-res imaging of sm...

Apple announced earlier this week that the official release date for iOS 6 will be September 19, but why wait when you can get it now? The Gold Master developer version was made available on Wednesday, and it's the same file as the final version that's going to be released to users on the 19th. Anyone can download it, so if you want to avoid being part of the frenzy on Wednesday when everyone else is trying to get it too, it may not be a bad idea to get a head start. A quick note: If you inst...

Creative Commons is awesome—really. If an image, video, or audio file is tagged with a CC license, that means you can use it as long as you give appropriate credit to the owner. For bloggers with no money for pricey stock media, it's a godsend. When you license your own media under CC, you can choose how you want it to be used by others and whether or not it can be used commercially.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

RFID cards are becoming a fairly common way to purchase goods, but they're already widely used to pay fares on buses, trains, subways, and trolleys across various cities. TAP cards are quick and reliable, but it can be a real pain to remember to bring them with you, especially if you weren't planning on using public transportation that day. Luckily, an intrepid tinkerer at Adafruit has managed to find a way to embed an RFID card into her phone, something you're far less likely to leave at home.

Let's face it, pretty much everyone has an automatic dishwasher. They are super convenient and are becoming cheaper to allow the general public better access to them. With that being said, though, dishwashers are also becoming a lot smaller.

Flavored oils are amazing. They add a new flavor and depth to dishes not possible with plain oil. Most unfortunately, however, flavored oils almost always come with a hefty price tag to reflect their deliciousness and to capitalize on the general cluelessness of the public.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

No need to make a bad situation worse when running into an ex boyfriend or girlfriend. There is no need to be petty or spiteful when keeping to a nice yet vague conversation will ultimately leave you looking like a real class act.

Don't make people around you wish that cell phones had never been invented. Mind your manners by following a few simple rules.

Want to know someone's private website password? It's the biggest wanted hack: passwords, but how do you do it? Well, this tutorial shows you how to hack any password on any site with JavaScript. But this works best on public computers because multiple people log on to them, which means a better chance at unintentionally stored passwords. It helps to know a little bit about JavaScript before attempting this password hack.

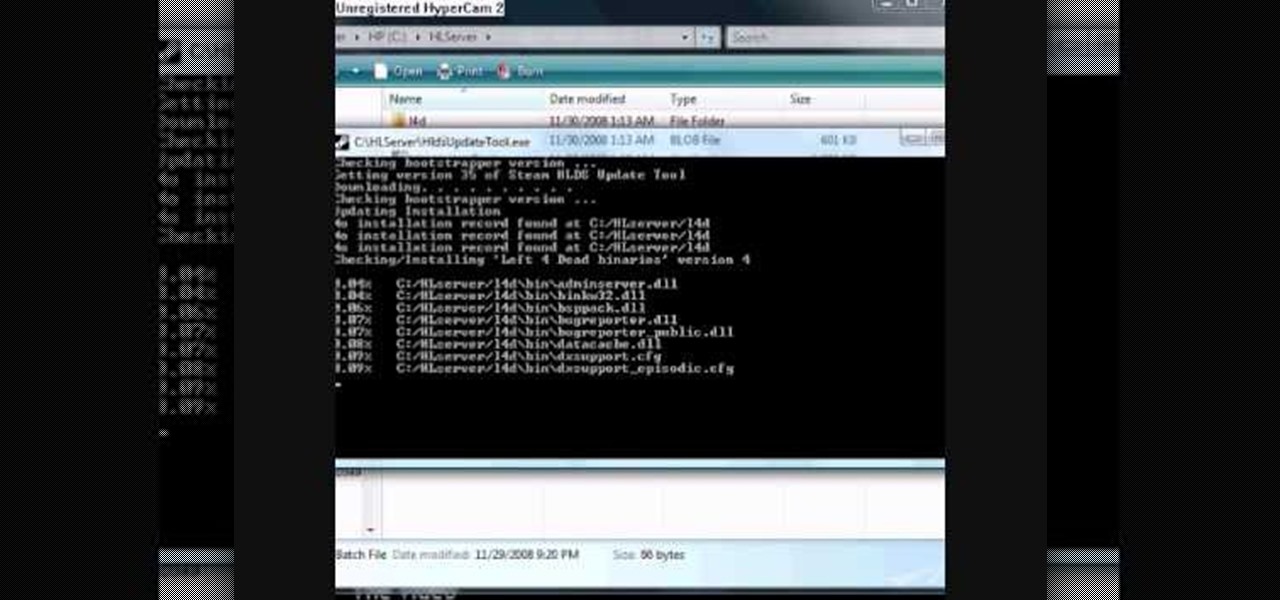
If you don't want to shell out the money to rent a dedicated server in order to host a Left 4 Dead game server, follow this tutorial on how to create one on your home computer. Keep in mind that if you intend on letting other people play it, you will need a fast connection to prevent lag.

Your brain actually needs to be refueled throughout the day, and our brains function best on carbohydrates. Brain foods like fruits and fish are important for fueling your brain all throughout the day. Learn some tips on eating brain foods and keeping your mind active in this nutrition how-to video.

Writing agendas are necessary to keep meetings organized and on schedule. Get tips on writing an agenda from a communications and public speaking expert in this free instructional video series.

Seventy-five years ago, a St. Louis widow named Irma Rombauer took her life savings and self-published a book called The Joy of Cooking. Her daughter Marion tested recipes and made the illustrations, and they sold their mother-daughter project from Irma's apartment. Today, nine revisions later, the Joy of Cooking--selected by The New York Public Library as one of the 150 most important and influential books of the twentieth century--has taught tens of millions of people to cook, helped feed a...

For whatever reason, you may want or need to remove multiple posts from your Instagram grid. If you only have a couple to hide from the public, archiving or deleting posts one by one is fine, but there's a much faster way when you have tens or even hundreds of Instagram posts to purge from your account.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

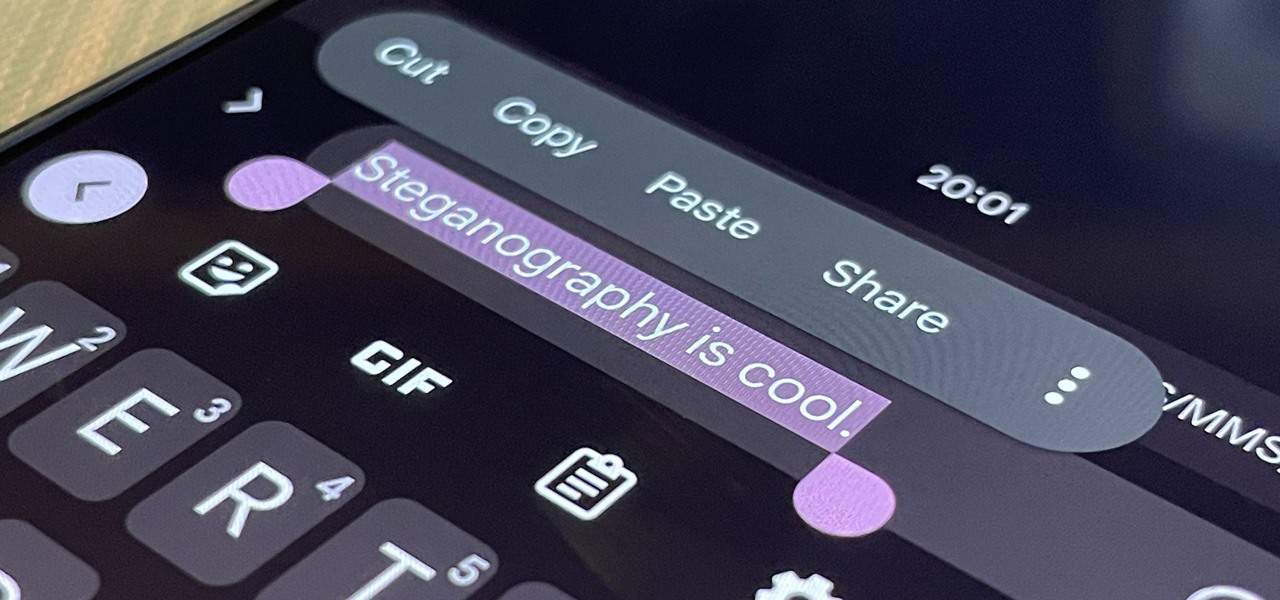
With a simple web-based tool, you can hide secret messages for family, friends, and fellow spies inside of plain text communications, and anyone that intercepts the messages will be none the wiser.

The development of virtual reality at Facebook has been evolving lightspeed in the last few years. But while a relatively small group of VR enthusiasts and gamers are enjoying the social media giant's dedication to immersive headsets, it is the augmented reality space and its potential scale that truly has the tech market enthralled.

Apple released the eighth iOS 14.5 developer beta on Tuesday, April 13. The update (build number 18E5199a) comes six days after Apple's last 14.5 beta update, which Apple pushed out to both developers and public beta testers.

Apple released the fifth iOS 14.5 developer beta on Tuesday, Mar. 23. The update comes eight days after the company released 14.5 beta 4 for public testers and developers.

Apple released the third public beta for iOS 14.5 today, Wednesday, Mar. 3. The update introduces a new "Items" tab in the Find My app that hints at the company's long-rumored "AirTags," a new Apple Watch icon when unlocking your Face ID iPhone with your watch, as well as small UI updates.

While iOS 14.3 is available to everyone right now, Apple is currently working on iOS 14.4 in its beta programs, and the second iOS 14.4 beta just came out for developers. The public beta version of iOS 14.4 beta 2 was released soon after. But what's in these new betas?

Apple released the first public beta for iOS 14.3 today, Friday, Nov. 13. The update includes ProRAW support for iPhone 12 and 12 Pro, upgrades to air quality in Weather, support for the PS5 controller, among other new features and changes.

Apple just released the fourth public beta for iOS 14.2 today, Wednesday, Oct. 21. The new update adds eight new dynamic wallpapers to iOS, including four real-life landscapes, and four digital landscapes. When counting each wallpaper's light and dark mode, there are 16 possible variations to use.

Apple just released the fourth developer beta for iOS 14.2 today, Tuesday, Oct. 20. The new update introduces eight new dynamic wallpapers, including four real-life landscapes, and four digital landscapes.

Apple just released the public GM (golden master) for iOS 13.6 today, Thursday, July 9. The update comes three hours after Apple released the 13.6 GM for developers, and the same day as the release of iOS 14 public beta 2.

Apple just released the third developer beta for iOS 13.6 today, Tuesday, June 30. This update comes three weeks after the company released the second 13.6 developer and public betas, which changed the name of the software from 13.5.5. It also comes eight days after Apple released the first developer beta for iOS 14.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.