Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

A vending machine is an invaluable yet totally frustrating piece of equipment. It's a godsend whenever your tummy's growling or you need an ice-cold drink on a hot summer day. But when something gets stuck inside or the machine flat-out malfunctions, it quickly becomes your archenemy. And when you're broke, it's basically just one big tease.

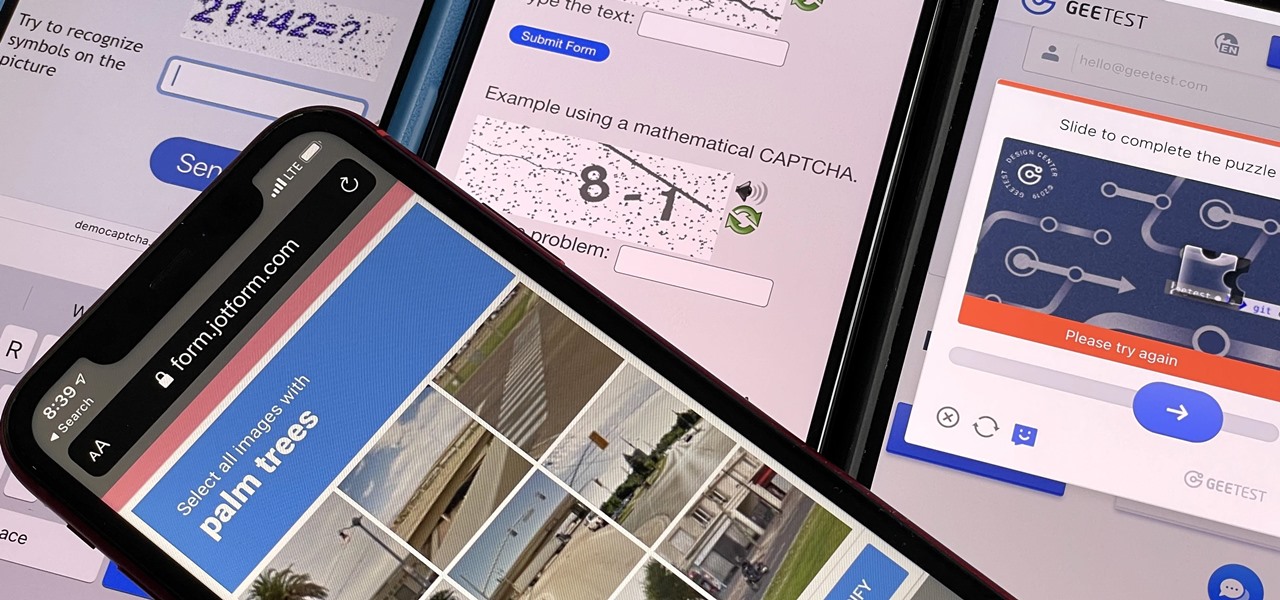
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

It's 2022, and the coronavirus pandemic is still going strong, meaning many people still wear masks. If that's you, unlocking your iPhone with Face ID is still very inconvenient when donning a face covering — until now.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.
Welcome back Hackers\Newbies!

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

If you use Apple's Mail app on your iPhone for iCloud and third-party email accounts, install the new iOS update ASAP if you haven't already. While there's not a colossal number of new features, the latest tools and improvements are powerful enough to make the update feel like Mail's biggest ever — and there are features we've been waiting for for years!

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.

Just as expected, Apple pushed out iOS 14.3 to the masses on Monday, Dec. 14, which coincided with the pumped-up release of Fitness+, Apple's subscription workout service for Apple Watch users. It also came one day before the new AirPods Max hit buyers, and the iPhone needs iOS 14.3 to use all of its features.

With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.

When Tim Cook, Craig Federighi, and other core Apple leaders take the stage for WWDC 2021 on June 7, we'll hear a lot about exciting new things to come. We're likely to see what's in store for watchOS 8 and macOS 12, but more importantly, we'll get a glimpse at what iOS 15 and iPadOS 15 will be like.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

In this tutorial, we learn how to discipline a teen with Dr. Felicia Ferrara. Since teens have always been known to be hard to discipline, it's very important to do this. When you punish a teen, make sure you are giving them a punishment that suits the crime they did. It's very important that you set guidelines with your teen, they will most likely thank you when they become an adult. Always remember, making wrong choices will shape your teen and how they are as an adult. Allow them to make m...

Meet Krampus, St. Nick's evil companion of traditional Alpine mythology. According to Wikipedia, the freaky tradition was particularly popular with the Austrian Nazi-allied fascists, circa mid-1930s:
By FrontierVille Post - Schoolhouse goals and lessons The schoolhouse is open!! Time for learning with the first day of school goal.

U.S. slaps new sanctions on Syria, extends those against Hezbollah - CNN.com. The United States announced new sanctions against Syria and those supporting its embattled government Friday, focusing on Hezbollah and a Syrian oil company. » James Holmes’ Psychiatrist Lawyers Up Alex Jones' Infowars: There's a war on for your mind!.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.
California grad student on no-fly list gets home after stranding An American student who discovered he was included on the government’s no-fly list and was barred from a U.S.-bound flight from Costa Rica was reunited with family and friends after he flew to Mexico and then walked across the U.S.-Mexico border Thursday evening.

Adobe, eBay, and iCloud have been hacked...now add Spotify to that list. The company has stated that on May 27th, they became aware of "some unauthorized access to [their] systems and internal company data" but that "only one Spotify user's data has been accessed and this did not include any password, financial or payment information."

everyone has a habanero eating contest and the losers pending on their place has to be punished. last place has to drink a bowl of habanero salsa wih don vitos back hair in it. second to last has to mouse trap their penis. third to last has to drink a pubic hair smoothy. first place gets to have their pubic har in the smoothy.

I've decided to write this post so some of the fledgling street artists who may or may not follow this world in the future are informed about two things in the urban art world that are either not discussed at all, or distorted (intentionally or otherwise) to the point of misinformation. Those two things are, as the title says, the dangers of street art, and the morals of street art.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

So... The MPAA, who are (obviously) in favor of SOPA, are crying about how the anti-SOPA blackouts are being caused by the ''big corporations'' and any who support it are apparently turning into pawns of said corporations.

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.