
How To: Execute Hidden Python Commands in a One-Line Stager
A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.


A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.
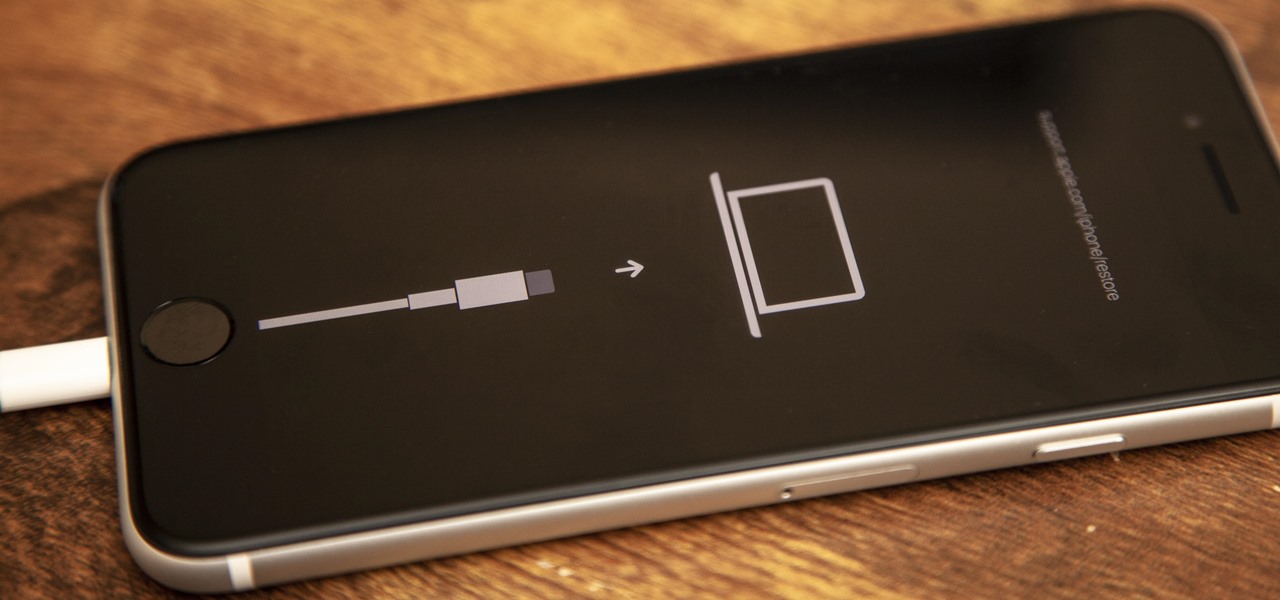
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

One of my favorite perks of this job is the opportunity to try out all the big flagship phones each year. Whether it's rating their suitability for a particular use-case or just entering their specs into our comparison tool, we have to get our hands on all major phones released in the US. We pride ourselves on being fair in our reviews and roundups, but that doesn't mean we don't have preferences.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.
After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

For 2019, Sony is trying to shake its failures of the past and start fresh. Following the unsuccessful Xperia XZ series, Sony is changing the name of their flagship to a single number: Xperia 1. With the name change comes a few upgrades, one of which is its new look. Secondly, its new display is unmatched in the mobile space.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Over the last few years, the only thing teased by Magic Leap more than the Magic Leap One itself has been the company's flagship gaming title Dr. Grordbort's Invaders. The game, developed by New Zealand studio Weta Workshop, finally got its debut last week during the L.E.A.P. conference in Los Angeles.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.
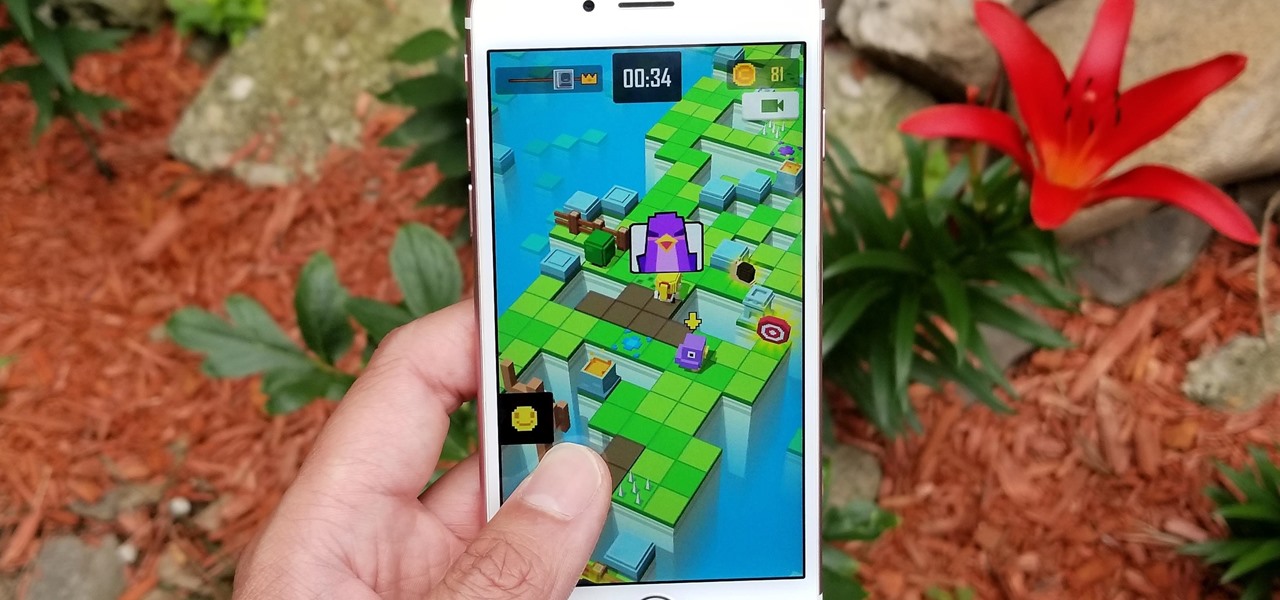
Puzzle games are a great way to kill time and exercise your brain in one fell swoop. They challenge you to think strategically and plan ahead, whether that's to create killer chain combinations for maximum points, or to plain old keep from getting killed.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Ironing is a serious chore: hot, unpleasant, and frustrating all in one, but necessary if you don't want to look like you crawled out of bed just before work. While you might only turn to your flatiron when faced with wrinkled clothing, this little appliance packs the power to tackle even greater challenges—and here are our 10 favorites.

Chances are that you've been using your microwave just to nuke leftovers, but they can do so much more than heat up last night's dinner—microwaves can help you peel garlic more quickly, get more juice out of lemons, disinfect your kitchen, dry out herbs, give beauty products new life, cause exciting explosions, and even arc weld.

Update: June 19, 2014 Android 4.4.4 has been released, fixing a small security bug in 4.4.3. The factory images have already been made available to all current-generation Nexus devices, and I've linked them out below. This does not affect the process depicted, you can still use these same steps to bring your device up to date with this latest release.

In this article, I will be showing you how to make a crude form of aspirin from the bark of a willow tree. It is a great remedy for headaches, hangovers, and other minor pain. The use of the willow tree as a mild pain reliever goes back to the Native Americans, who used it in much the same way that I do.

Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say.

Grave rubbing is more than just an art. It's a record of the past, one that so many people would just rather forget. And graves are the one way to reconnect with that world. Discover the ancient art of gravestone rubbing to record beautiful headstone images or to enhance your genealogy studies. It only takes a few simple tools, and you're on your way.

If you don't know how to raise a car off the ground by now, you don't know jack. You Will Need

One of the best recent outings in the Marvel universe is the animated series What If...?, which explores alternate universe takes on various superhero storylines that deliver fascinating scenarios if one single factor had been different in the story.