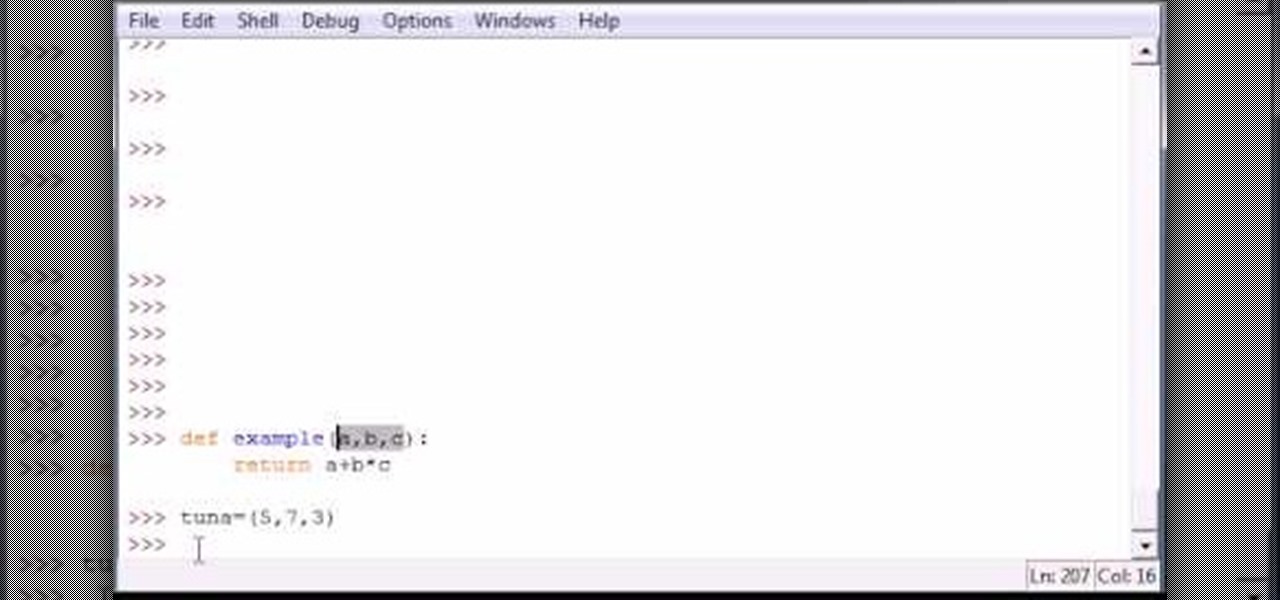
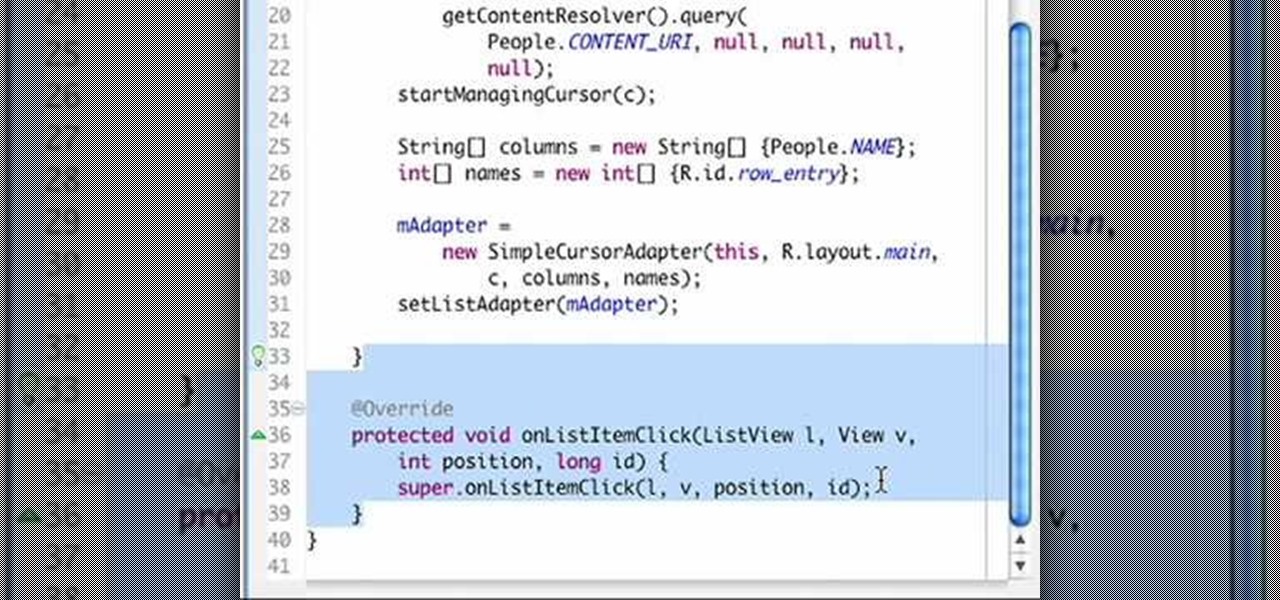
How To: Use tuples as parameters in Python
Bucky from The New Boston serves up this Python video tutorial on how to use tuples as parameters in Python. This is the program you use to write all of your Python code down. Fun with tuples!


Bucky from The New Boston serves up this Python video tutorial on how to use tuples as parameters in Python. This is the program you use to write all of your Python code down. Fun with tuples!
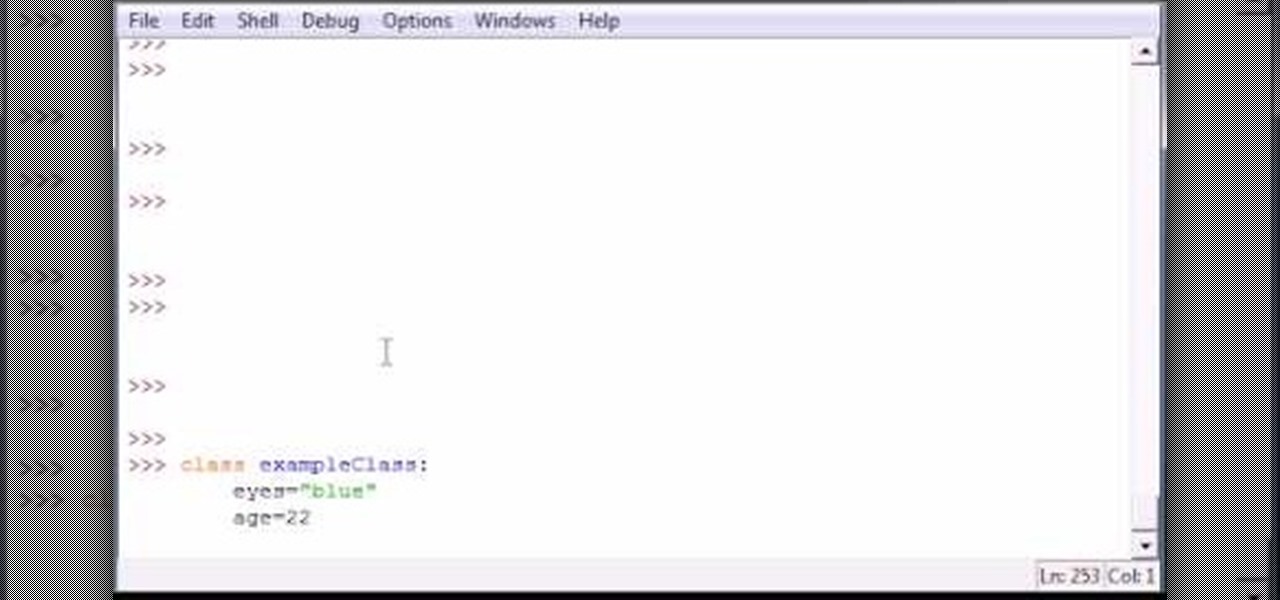
Bucky from The New Boston serves up this Python video tutorial on how to program object oriented programs in Python. This is the program you use to write all of your Python code down. OOP or the famous object oriented program. Hold on guys, the waters getting rough!
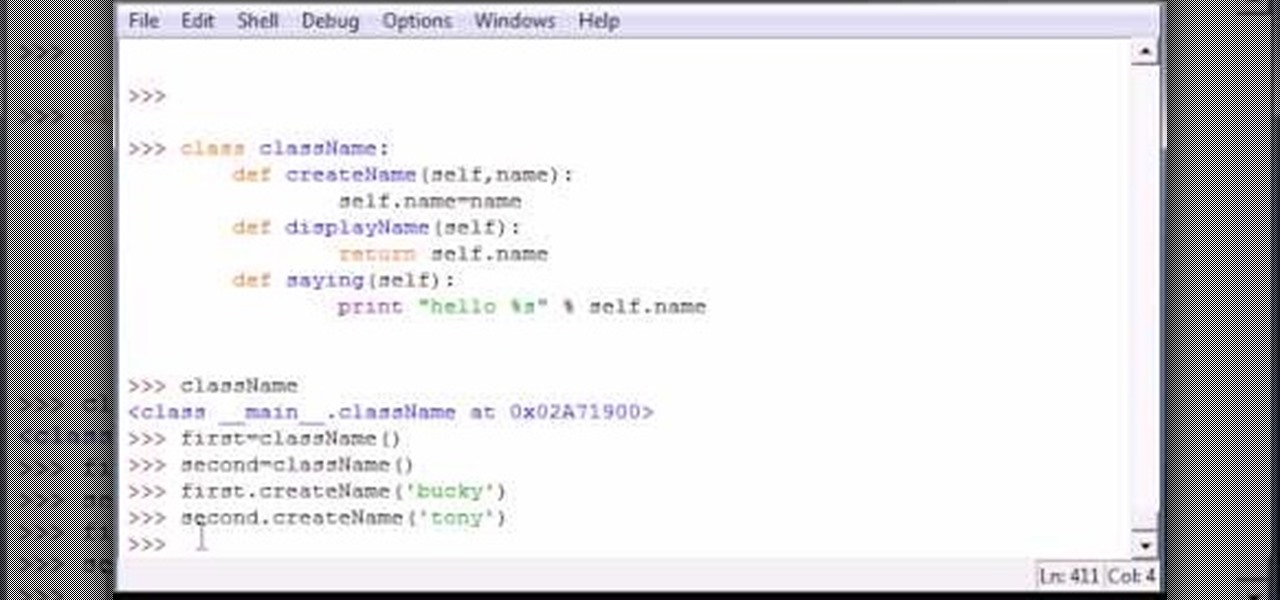
Bucky from The New Boston serves up this Python video tutorial on how to program classes and self in Python. This is the program you use to write all of your Python code down. Fun with classes and self!
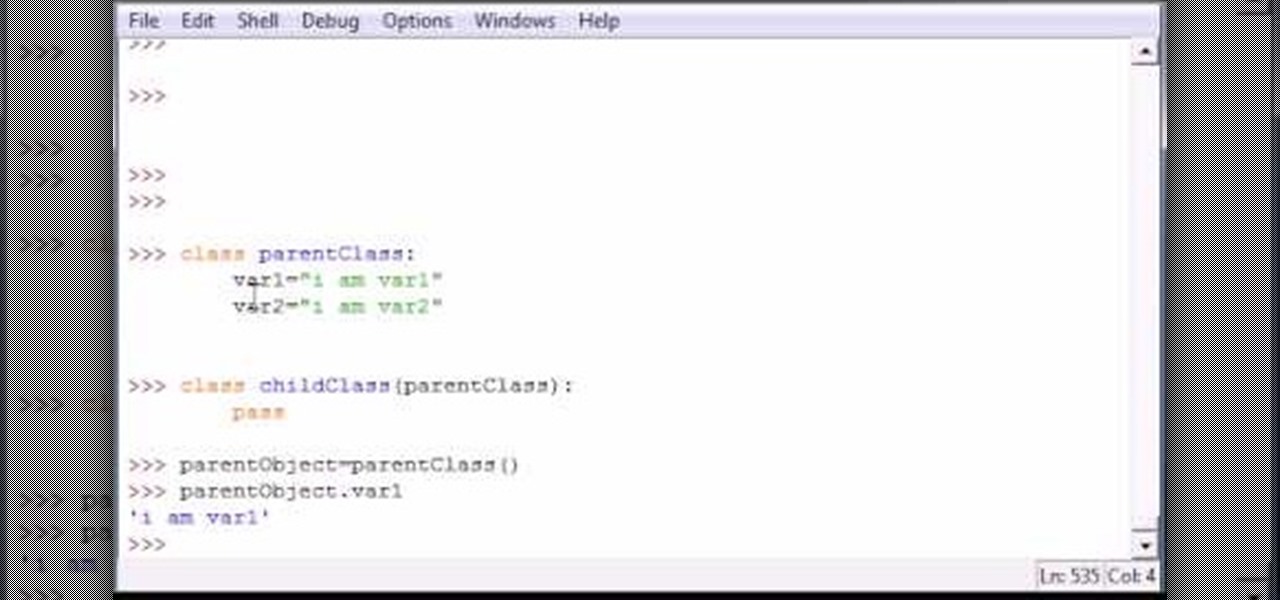
Bucky from The New Boston serves up this Python video tutorial on how to program subclasses and superclasses in Python. This is the program you use to write all of your Python code down. Learn what parent and subclasses are!
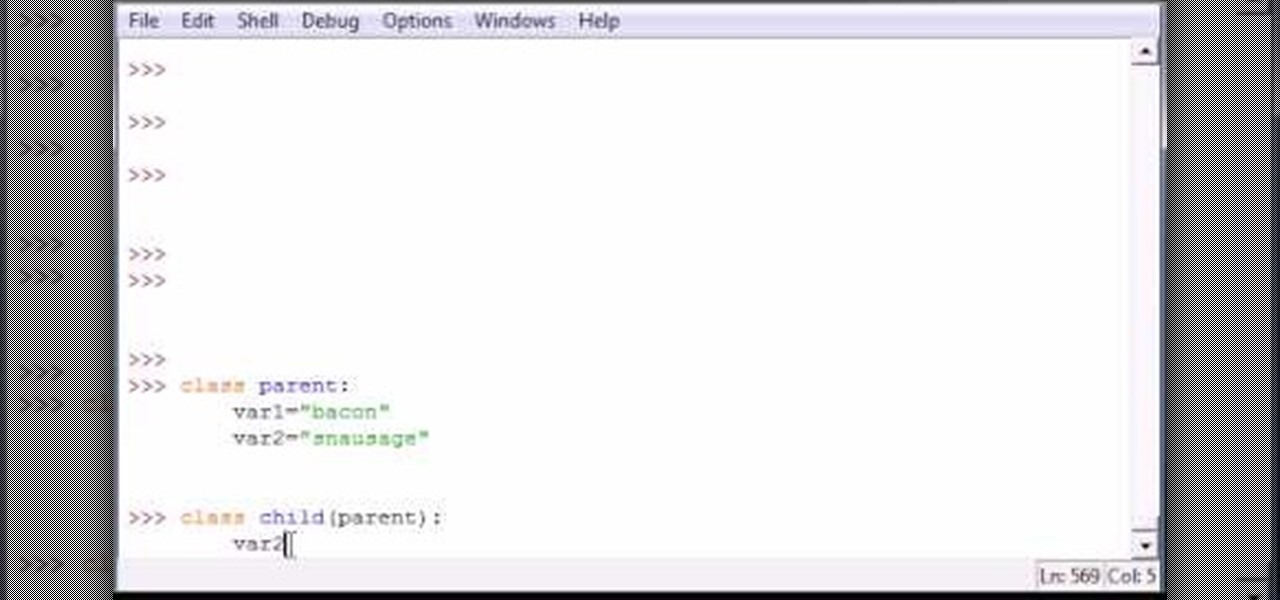
Bucky from The New Boston serves up this Python video tutorial on how to overwrite variables on a subclass in Python. This is the program you use to write all of your Python code down. Fun with subclasses!
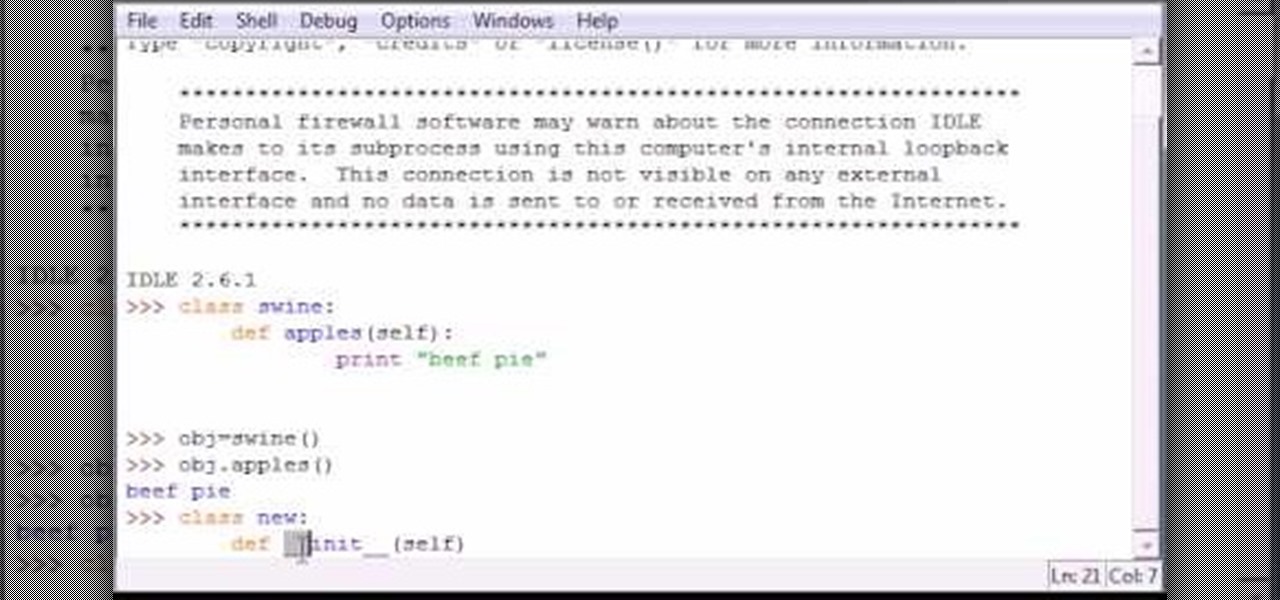
Bucky from The New Boston serves up this Python video tutorial on how to create and program constructors in Python. This is the program you use to write all of your Python code down. Learn how to create constructors and what they do!
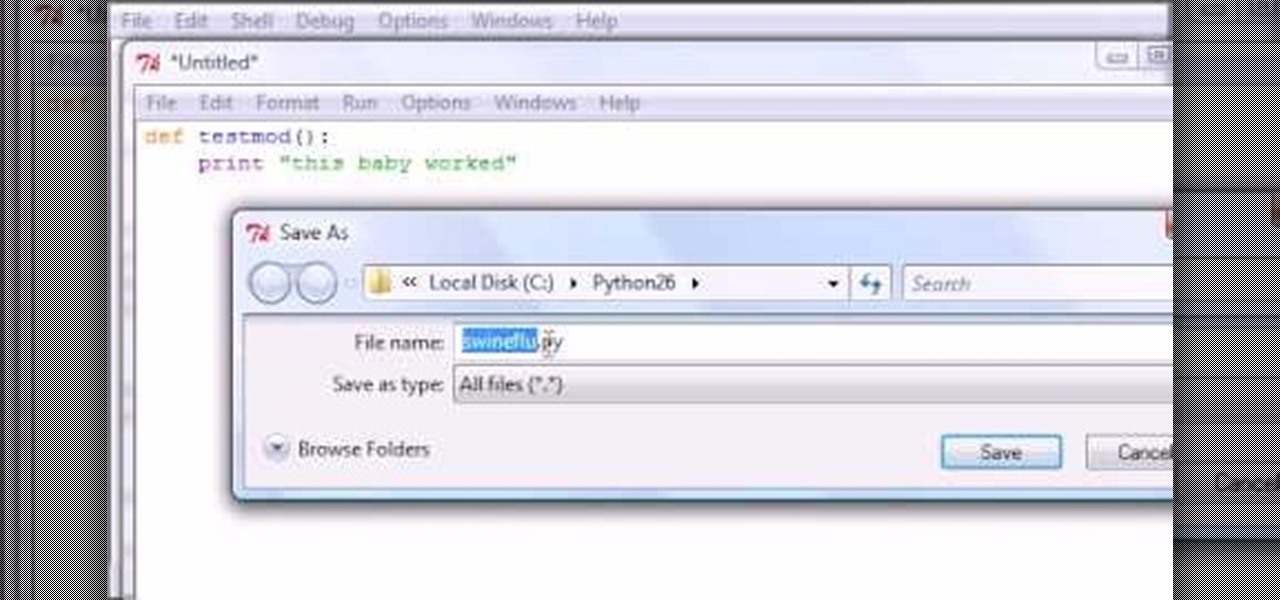
Bucky from The New Boston serves up this Python video tutorial on how to import modules into IDLE in Python. This is the program you use to write all of your Python code down. Fun with importing modules!
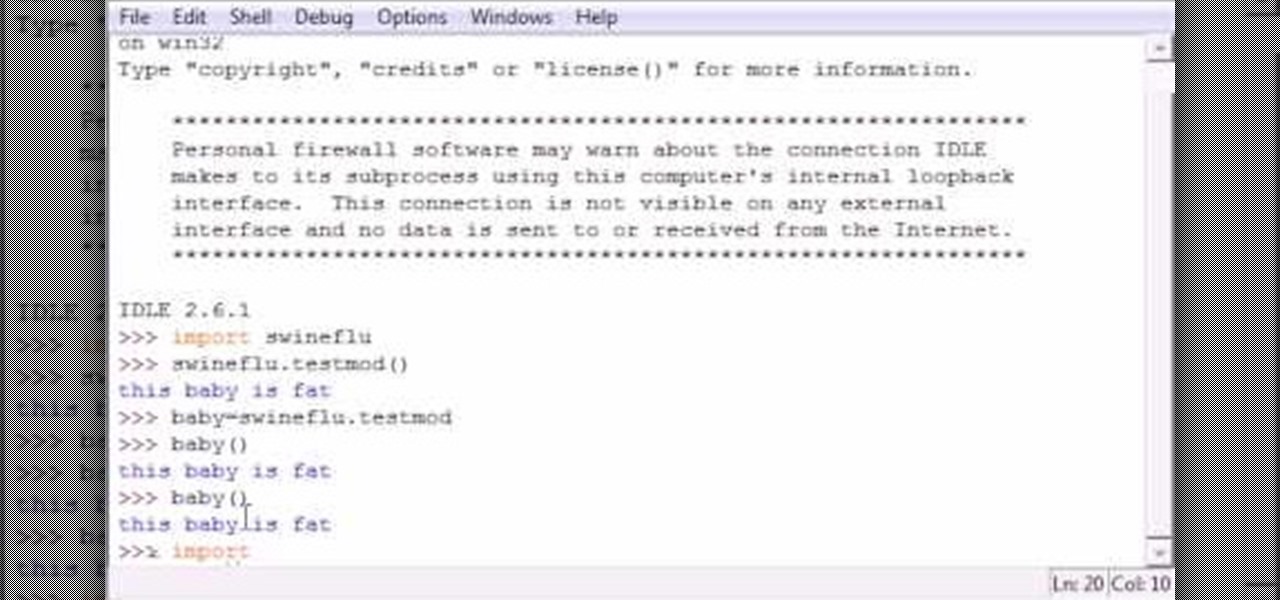
Bucky from The New Boston serves up this Python video tutorial on how to reload modules in Python. This is the program you use to write all of your Python code down. Learn how to reload modules once your source file has been edited!
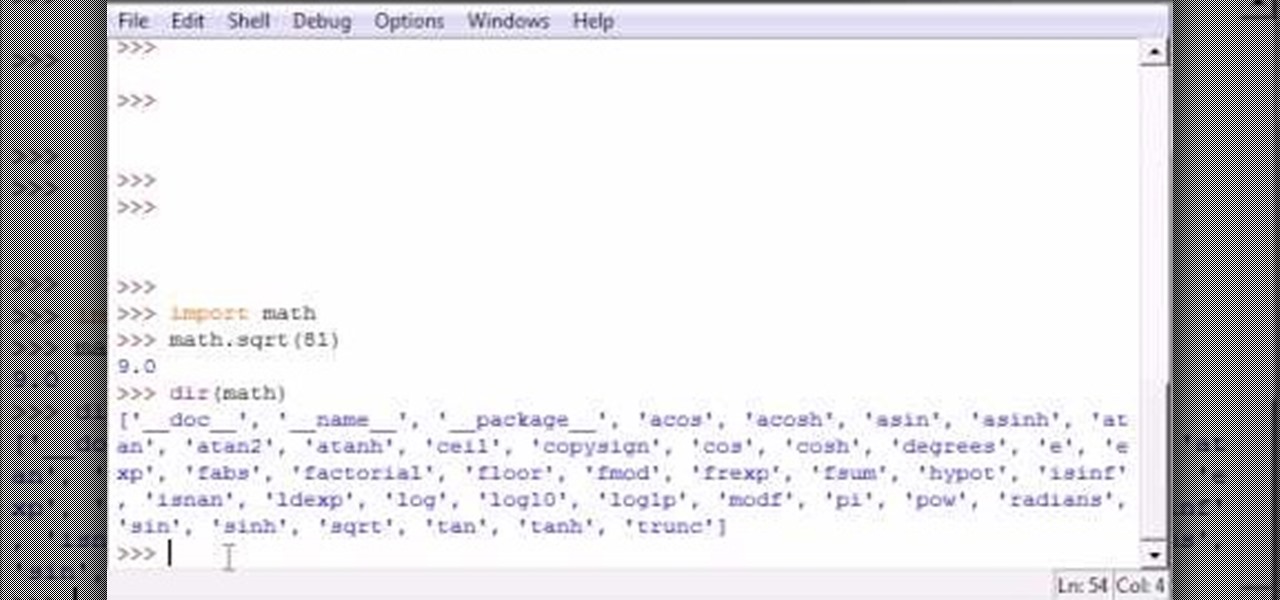
Bucky from The New Boston serves up this Python video tutorial on how to get module information in Python. This is the program you use to write all of your Python code down. Learn how to get extra info from outside modules!

Bucky from The New Boston serves up this Python video tutorial on how to work with files in Python. This is the program you use to write all of your Python code down. Fun with files!

Bucky from The New Boston serves up this Python video tutorial on how to read and write lines in files in Python. This is the program you use to write all of your Python code down. Fun with reading and writing lines into a file!
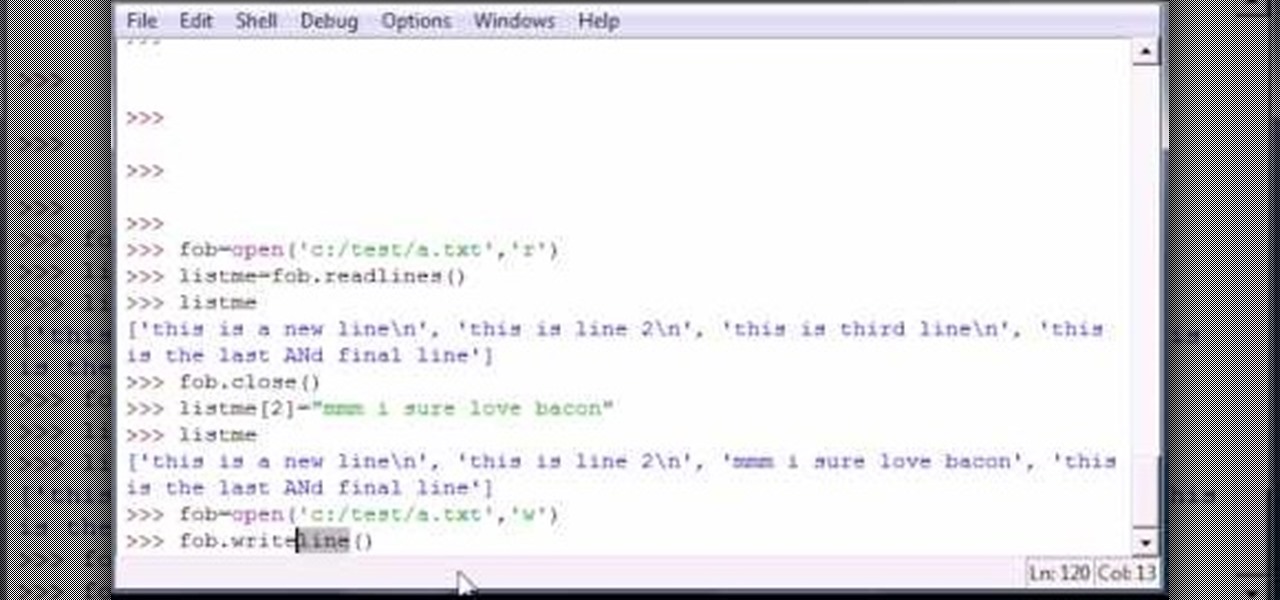
Bucky from The New Boston serves up this Python video tutorial on how to program and write lines in files in Python. This is the program you use to write all of your Python code down. Fun with writing lines into a file!

Bucky from The New Boston serves up this Python video tutorial on how to download and install wxPython for Python. This is the program you use to write all of your Python code down. Learn how to install the GUI (graphical user interface) toolkit.
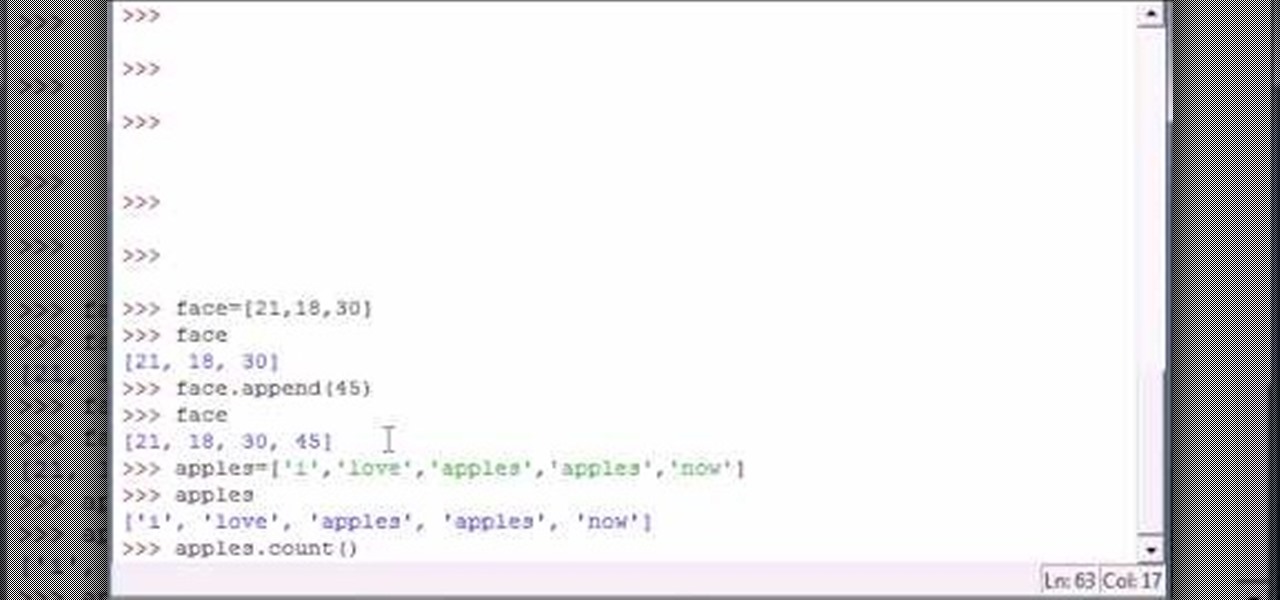
Bucky from The New Boston serves up this Python video tutorial on how to program methods in Python. This is the program you use to write all of your Python code down. Fun with methods! Learn what methods are and how to use them.

Bucky from The New Boston serves up this Python video tutorial on how to program slice lists in Python. This is the program you use to write all of your Python code down. Slice Python!

Bucky from The New Boston serves up this Python video tutorial on how to program lists functions in Python. This is the program you use to write all of your Python code down. Fun with list functions!

Bucky from The New Boston serves up this Python video tutorial on how to program slices in Python. This is the program you use to write all of your Python code down. Slice Python!
Bucky from The New Boston serves up this Python video tutorial on how to program raw input in Python. This is the program you use to write all of your Python code down. Fun with input versus raw input!

Bucky from The New Boston serves up this Python video tutorial on how to save and execute your programs in Python. This is the program you use to write all of your Python code down. Fun with saving programs!
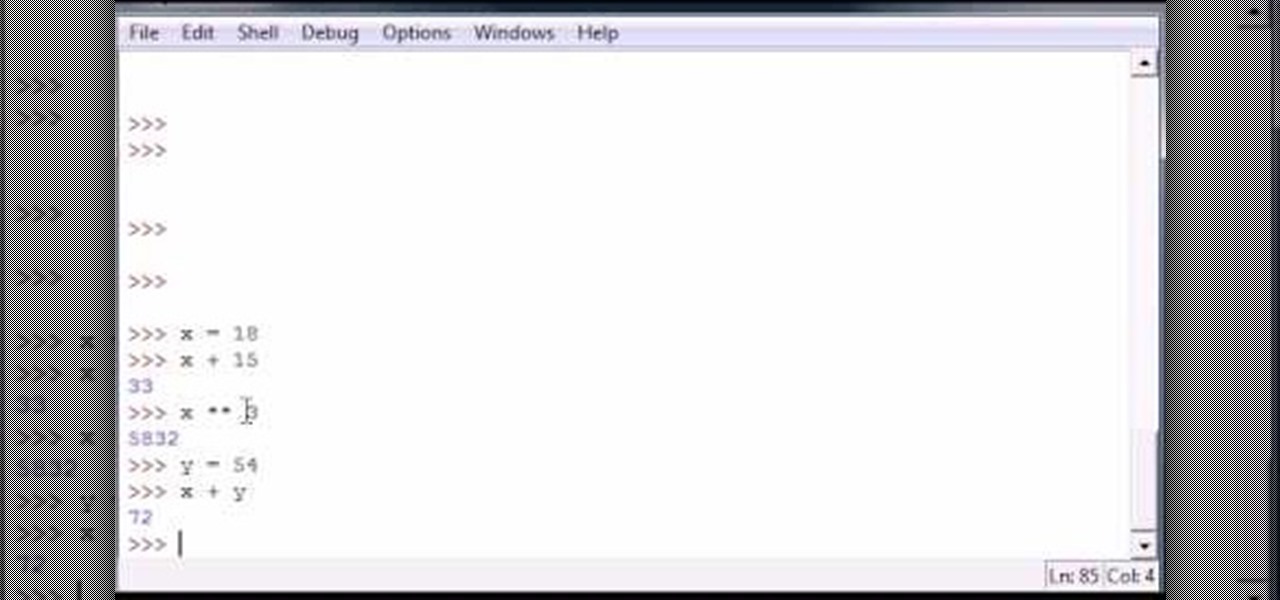
Bucky from The New Boston serves up this Python video tutorial on how to program variables in Python. This is the program you use to write all of your Python code down. Fun with variables!
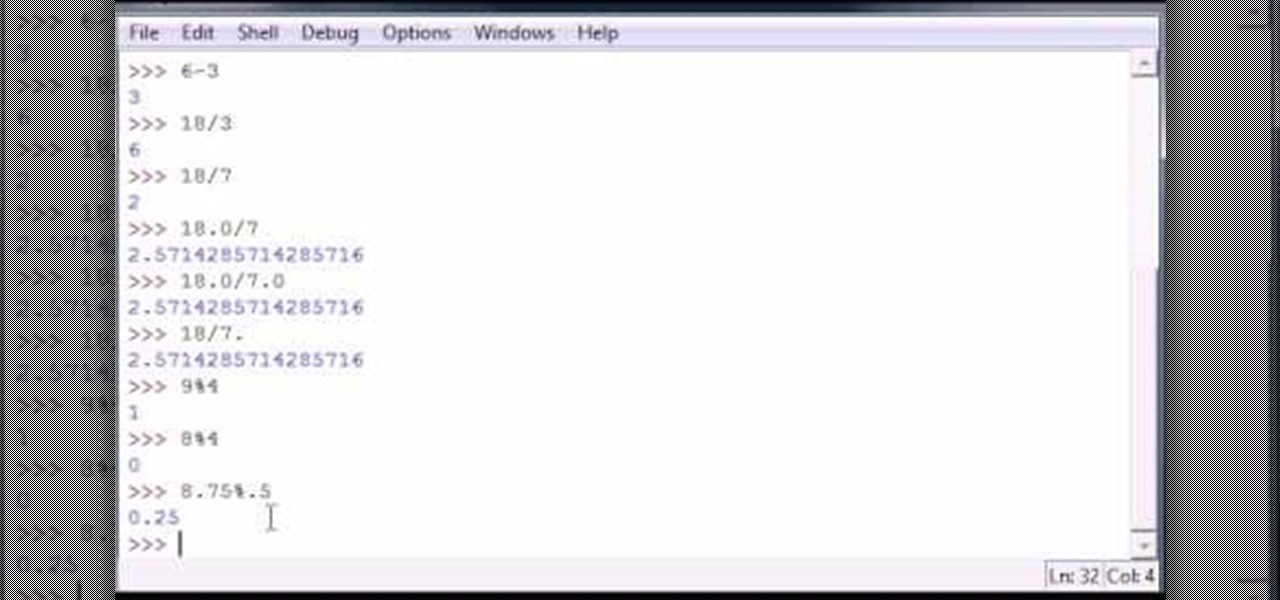
Bucky from The New Boston serves up this Python video tutorial on how to use simple numbers and math calculations in Python. This is the program you use to write all of your Python code down. Fun with numbers!
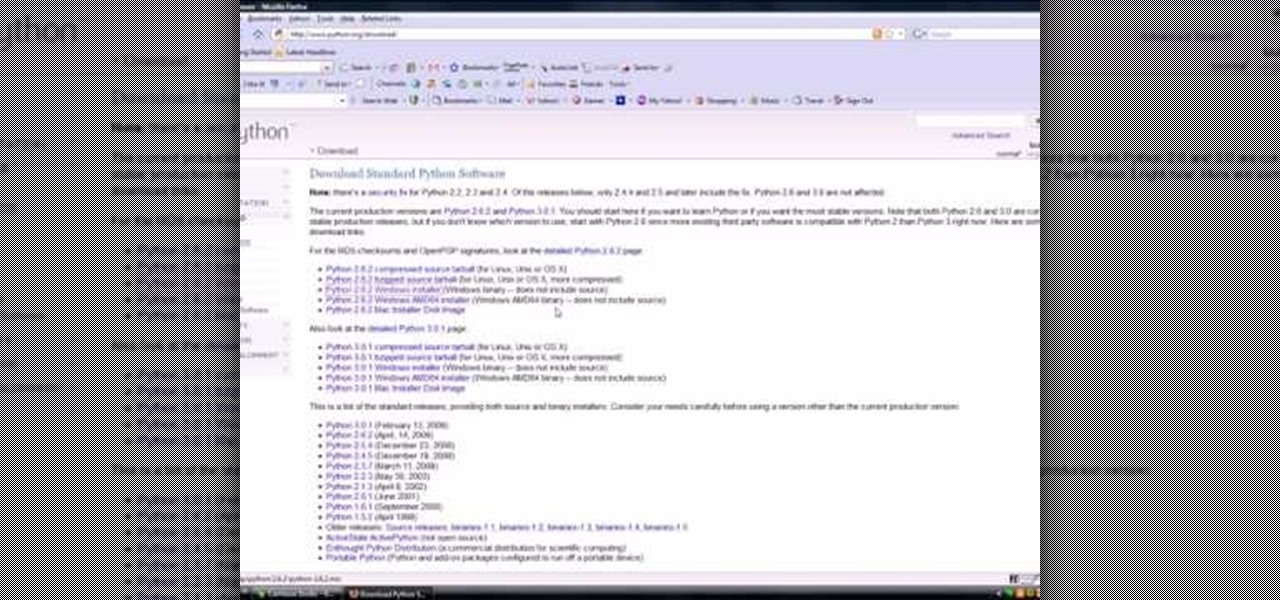
Bucky from The New Boston serves up this Python video tutorial on how to download and install Python. This is the program you use to write all of your Python code down.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to install a Wii homebrew hack using the Twilight Hack.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup Wii games to SD to play in HD.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to get free WiFi by tunneling through DNS.

Learn how to exercise your dog. Follow a regular exercise routine together with your pet. It will benefit you both!

This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.
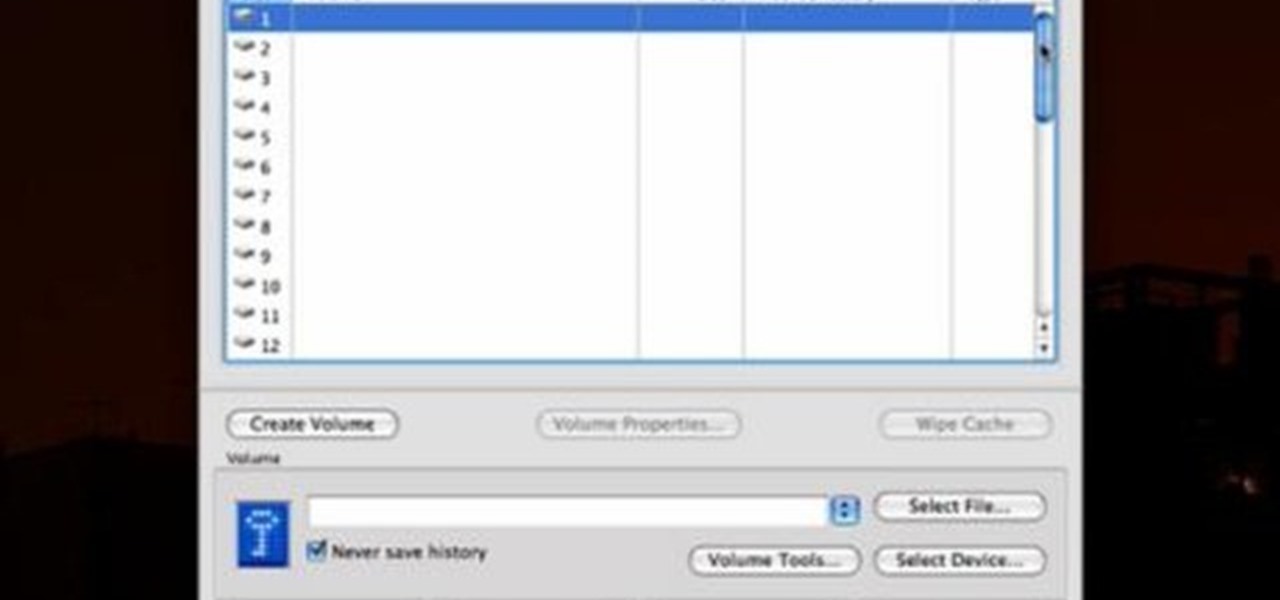
Check out this video tutorial to see how to keep your private files private, even if you have to email them to yourself at your office? TrueCrypt, an open source piece of software, lets you encrypt your files so they remain accessible only to you. This works on any platform; Windows, Linux, or Mac. So, watch this video to see the TrueCrypt download process, how to install it, and how to create an encrypted volume on your hard drive.
This video tutorial is about Android, and no it's not a robotic creature, it's a software platform and operating system form mobile phones and PDAs. The Android system is based on Linux and was developed by Google and the Open Handset Alliance. Code is managed in the Java language, but can be written in C also, although C is not officially supported. A lot of the new cell phone and other mobile devices will be running off of Android, so know how to use it.
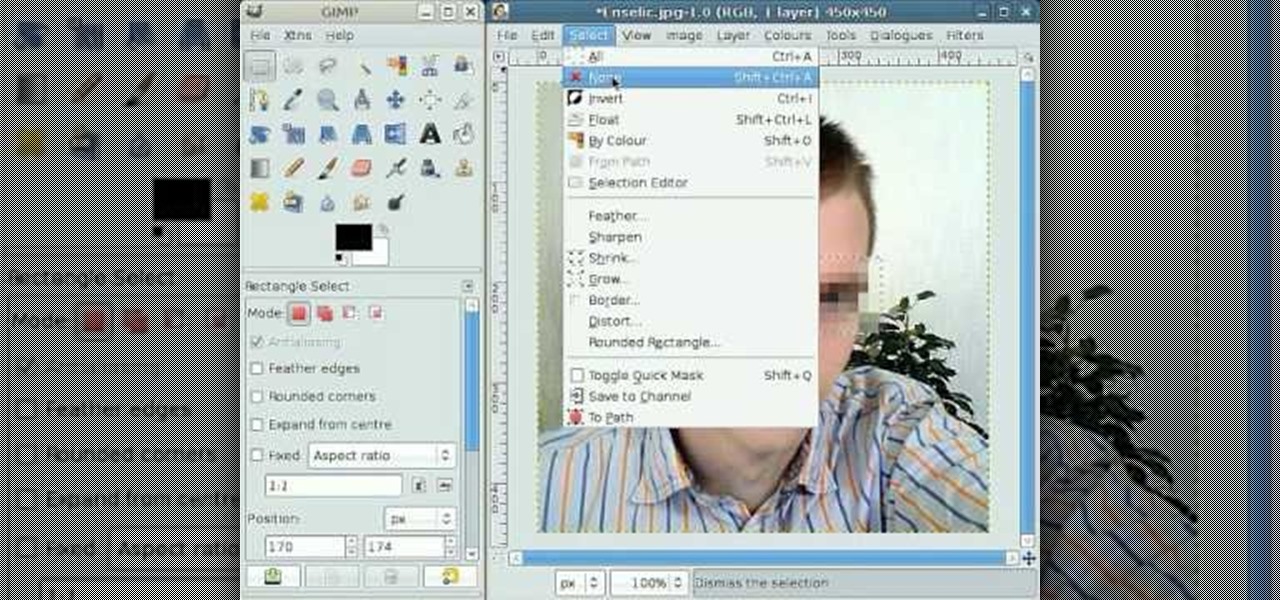
By following this tutorial you will learn the concept of selections in GIMP. Whenever he says "layer mask" he really meant "selection mask".

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.