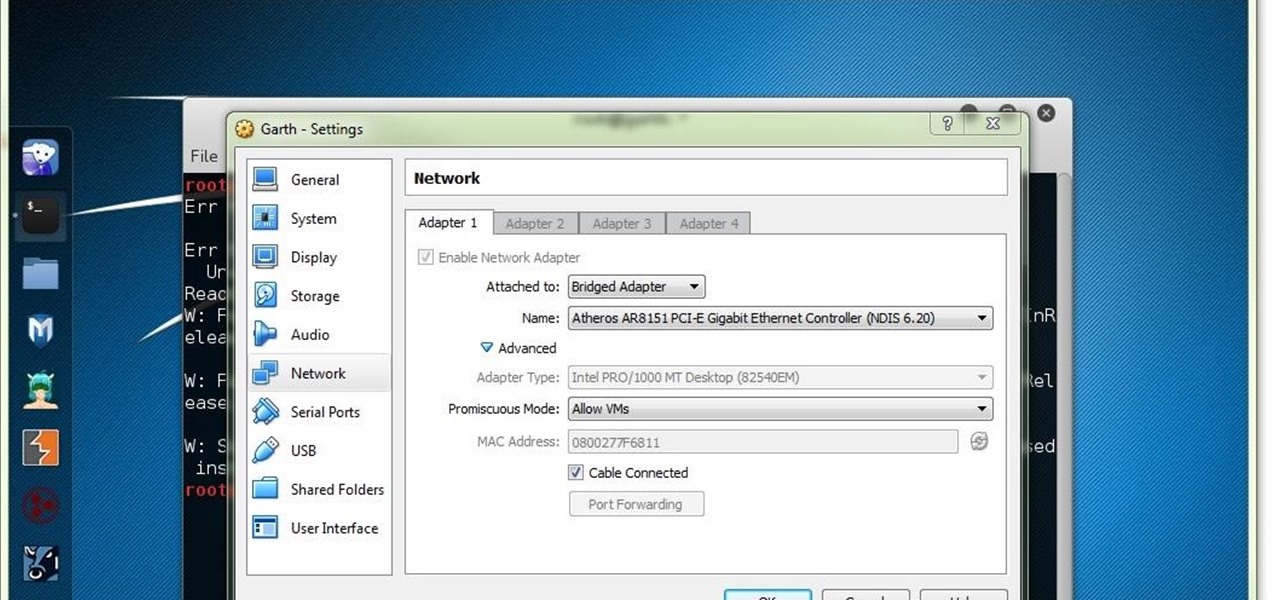
Introduction to KVM KVM is a free and open-source Kernel-based Virtual Machine using the Linux kernel for virualization and is very similiar to a hypervisor like Xen or VMware's ESXi. It is based on Qemu, a processor emulator. Any virtual machine created on or working on KVM can work on Qemu also, but with a great reduction in speed.

Friday's mission was to accomplish solving HackThisSite, basic mission 7, which required us to learn some basic Unix commands. If you have any prior experience using Unix commands, this should be a breeze for you if you sit and think for a second.

With a lot of Null Byters playing around with Linux because of its excessive use in the hacking world, some of you are bound to run into some trouble with the installation at some point or another. If you make a mistake, or you're intimidated by the wonky-looking installation screen, you may want to just stick with Windows. However, you may notice it can be hard to go back once you've crossed a certain point in the installation. Your Windows installation may be broken or unbootable.

Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and the aircrack-ng software suite, the software has become unusable.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Downgrade Firefox 5 to Firefox 4 or any earlier versions:[Windows users] 1. Visit Link

Things You'll Need A fully working operating system that supports VirtualBox (Windows, OS X, Linux or Solaris)

The Ironkey is a high security thumb drive designed to provide strong AES encryption, tamper resistance and other security services. Some of the topics covered will include: How is the drive mounted without admin privileges in Windows? How is it mounted in Linux? How does the "Self Destruct" feature work? What is Secure Sessions? How is the Ironkey better than just using Truecrypt? For answers to these questions, take a look. Use the Ironkey High Security Flash Drive.

Devil2005 has created a video on compiling and configuring dhcp daemon, or dhcpd, from source. He's using the Fedora 9 distribution of Linux for the video, but the lessons learned should be applicable to other distros. For that matter, even if you are not interested in installing dhcp in this way it's still a good lesson on how to download and compile various applications from source. Compile and configure dhcpd from source in Fedora 9.

Windows users have looked on with envy at Mac owners wrangling torrents with ease for years. Now, finally, a new Windows torrent client is making downloads easier, safer, and more customizable.

Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

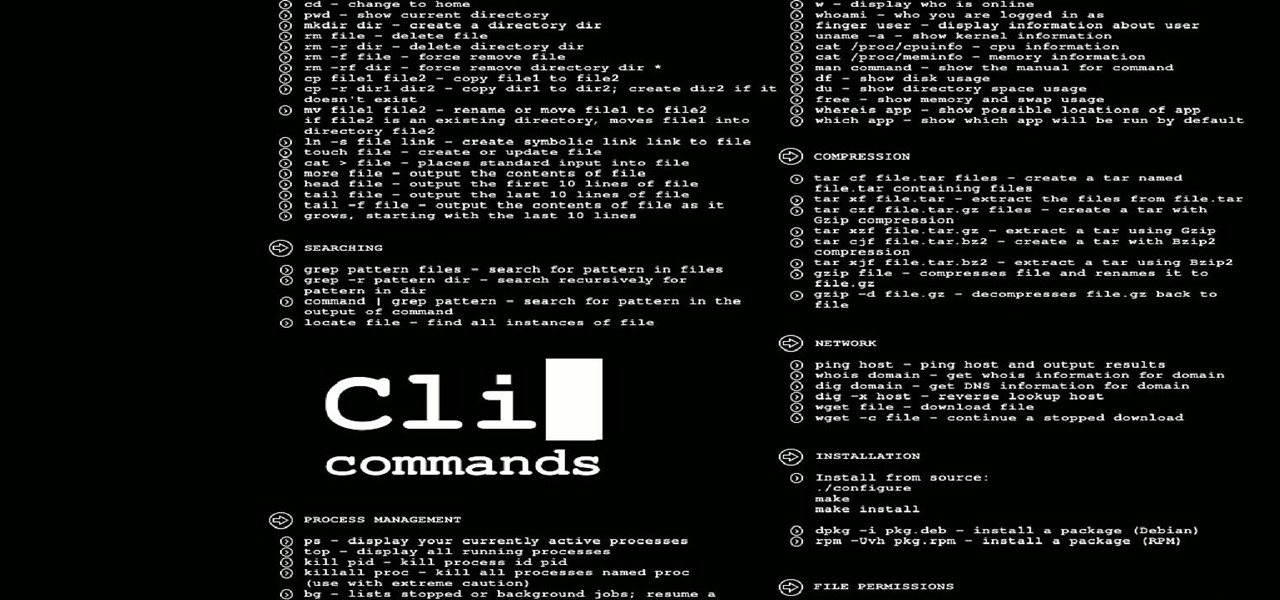
Hello everyone on null byte this is my first tutorial This Tutorial Is on Useful Lesser Known Commands on Linux

Hello everyone, I am Brandon Hopkins from TechHut and I am going to be showing you how to install Minecraft Texture Packs on Windows, Linux, and Mac. I will also link you to one of the best Texture Pack I have used and a website where you can download 100+ different texture packs.

The Ubuntu CD does not contain much in terms of software applications. So how can we incorporate other programs that would be made available after booting from a live CD?

Hello everyone today I am going to be going over installing Minecraft on Linux (Ubuntu) as if it is any regular program a game. This method makes it super easy and clean in that you will not need to run a .jar every time you want to play this game. This is very simple to do and it dose not only install Minecraft as if it is any regular game/program it also gets the best version of Java to run Minecraft. Download: http://goo.gl/DKQ6B

The right combination of an appropriately awkward protagonist, a clever script with , and truly remarkable animation (including 3-d flying scenes that trump anything in ), made this flick a blast from start to finish.

Alright, since I notcied this article was too advanced for some users, ive decided to revision this!

Welcome, everyone! While Linux distributions are almost always used for exploits, security, pentesting and other stuff covered in Null Byte, knowing the Windows Command Line (or Command Prompt) is a useful skill that can help you in various ways, such as using exploit programs made for Windows or using the command line on someone else's Windows computer.

Hi everyone This is something that I should've done the first day but hey...better later than never right?

Apple just released the latest developer preview of OS X 10.11 El Capitan, currently in its sixth beta. While this latest build mostly deals with tiny improvements and bug fixes, it also includes a brand new breathtaking wallpaper of the El Capitan rock formation in Yosemite National Park.

Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool.

Last week, we had a great contribution from Christopher Voute, who introduced us all on some of the basic moves in Python. Now, who else will share their knowledge and tackle some of the topics below?

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Pygame! And what you can accomplish with it. Another python article... (Blame Alex for getting me hooked on yet another coding language...)

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out, such as Gears of War 3 and Dead Island, to name a few.

GRUB, or the GRand Unified Bootloader, is a program that installs to your Master Boot Record and controls what operating system you load at boot time. Normally, it is used for multi-boot systems. Multi-boots allow you to switch between operating systems installed on seperate drives, or partitions at boot time. Linux actually uses it as its default bootloader, even without multiple operating systems.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

Want to drop Amazon's DRM from a Kindle eBook you've purchased? As the saying goes, where there's a will, there's a way. And, in this case, there are actually a couple of ways: One method uses Calibre and works for both Windows and Mac users, the other uses an AppleScript and is Mac exclusive. To maximize the usefulness of this guide, we've chosen to excerpt a tutorial that uses the OS-agnostic method. Mac users looking to find a writeup of the latter method, however, should look here.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

I recently upgraded from Ubuntu 9.10 to 10.04 and now my boot screen is a bit messy. Since I'm not using the latest GRUB boot kernel (Linux 2.6.32-28-generic), I might as well delete it. For more documentation, visit Ubuntu Forums.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

Introduction PostgreSQL is a very popular Open-Source database management system. It competes heavily with many proprietary and commercial database management systems. More information on what it is and it's history can be found here and here.

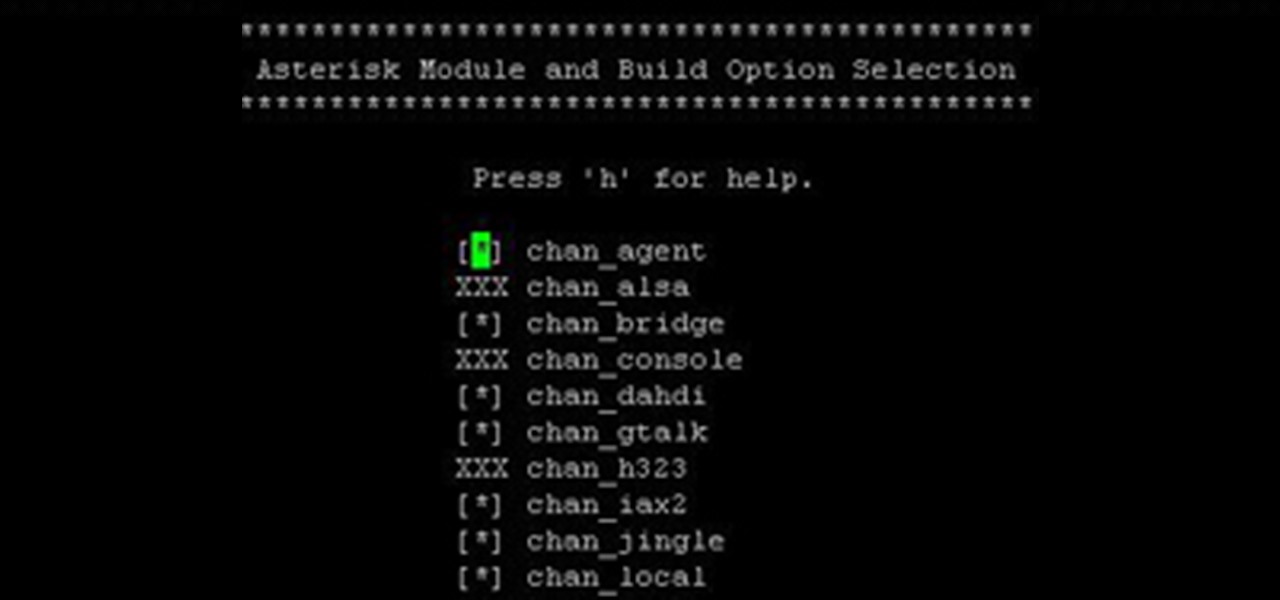
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

Thanks to online music services like eMusic and iTunes, compact discs are becoming a far distant memory, turning local music shops around the country into desolate wastelands. The once mighty movie rental store Blockbuster is now bankrupt because of online streaming services like Hulu and Netflix. And Borders and Barnes & Noble are closing stores left and right thanks to eBooks available on eReaders, like the Amazon Kindle. Everything is moving to the digital world, and everything is finding ...

OpenGL (OPEN Graphics Language) is a 3D graphics language developed by SGI. It has become a de facto standard supported in all Unix, Linux, Windows and Macintosh computers. To start out developing your own 3D games and programs, you need to know OpenGL and C++. This video lesson will show you how to use transformations and timers with OpenGL and GLUT for C++, so you can start making your own 3D programs. If you want to create your very first OpenGL project, this is the place to be.

Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.