Here at Null Byte, we try to inform and teach the community on ways to navigate the Internet in that special way, as well as staying safe along the trip. That being said, I need some help from all of you! There is a lot of information to cover and I know we have some smart users lurking around. We would love to hear from you.

Are you the expert hacker we're looking for? Do you have a great idea for an article on Null Byte? Do you have a passion to write, and more importantly... teach?

As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I am transitioning from C#.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmers to aspiring hackers.

The latest in the Legend of Zelda series, Skyward Sword, released a few short weeks ago to very little fanfare. I have no idea why that is, because the game is absolutely gorgeous and pretty darn good. Maybe it was the fact that Nintendo forced motion controls in to this one, or maybe it was because everyone is busy playing Skyrim/Modern Warfare 3/Battlefield 3. Whatever the reason, if you even remotely like the Zelda series, give this one a whirl.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Some people are what is labeled a power user. I am one of these people. No matter how fast I get my system, or how quick of programs I have, it is never good enough. There is always at least one program that I could swap out for a more advanced, text-based counterpart that increases performance just a bit. Luckily, you don't have to use text-based programs without graphical user interfaces to get blazing fast speeds on Linux. There are tons of open source alternatives to the mainstream progra...

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

Welcome to part three in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

Baking bread might feel intimidating in advance. The fear to screw it up can make one chicken out and instead keep buying bread as usual at the store. Personally, I am very picky about which bread to eat, and learned over time that home baked bread bits them all when made properly.

Now that I am jumping full swing into WonderHowTo Worlds here... I can see why this is platform is much better for socializing... With Facebook, you might as well flash your naked self for all to see, because there isn't much left to know about you.

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.
Hello fellow Null-Byters today I will be showing you how to change from the simple but powerful BASH system to a more powerful and faster Z - Shell system. This change can be permanent if you want but doesn't have to be, and it is an extremely simple one to perform.

Want to see your Minecraft creations in real physical form outside of your server? Mineways is a free program for Linux or Windows users that renders all of your Minecraft builds into full color 3D model files. Those files can then be sculpted using your own 3D printer (if you have one), or uploaded to Shapeways, a company that will print your 3D models creations in colored plastic, which you can then purchase or sell in their online gallery.

Many users of the virtualization software VirtualBox may have noticed that the USB system has been pretty buggy for quite a long time. I've had my USB randomly duck out on me way too many times to count. This can really be difficult to deal with when you require access to the devices and files from the host system.

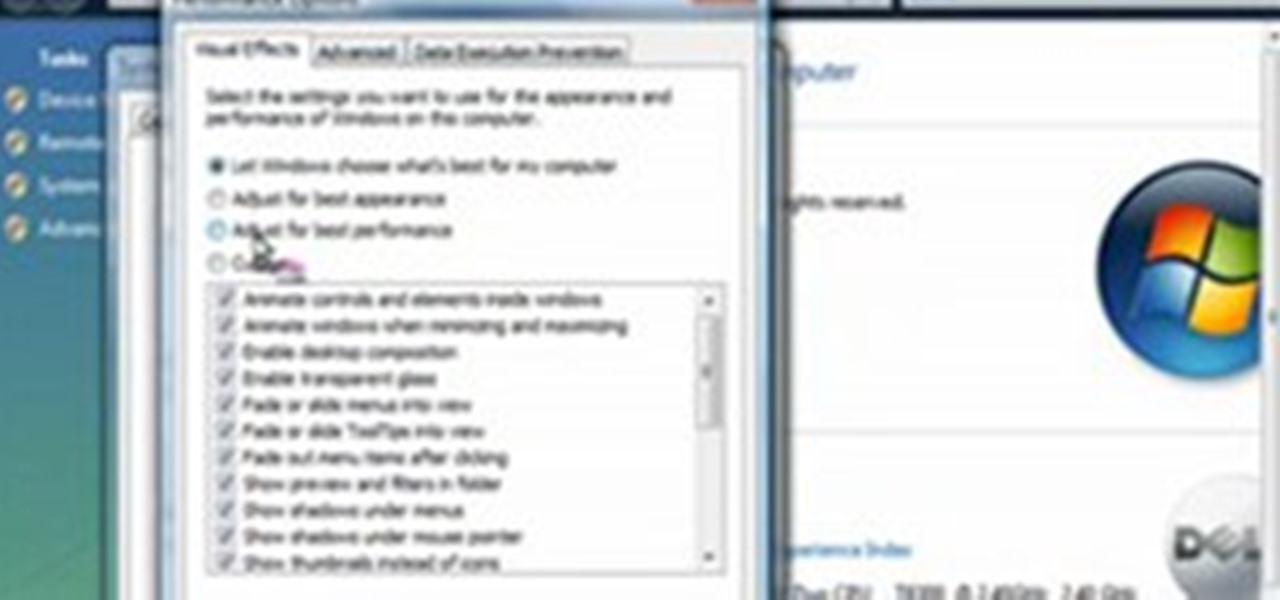
More Speed without buying expensive hardware. Windows Vista was never the step up in performance that people hoped for after XP. In fact a lot of people preferred the old XP or Linux until windows 7 arrived. Nevertheless there are a few things you can do to make your Vista OS system run faster and smoother.

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

I've previously mentioned how saving browser passwords is a bad idea, but I never went into much detail as to why. Passwords that are saved in your browser can be carved out and stolen very easily. In fact, even passwords you save for instant messaging and Wi-Fi are vulnerable. Windows is very inefficient with the way it stores passwords—it doesn't store them in key-vaults, nor does it encrypt them. You're left with passwords residing in memory and filespace that's unencrypted.

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

Minecraft may seem like a game for just hardcore gamers and computer nerds, but it's totally not. It can hook anyone and everyone, from casual gamers to online addicts to total newbies—it can even turn its users into serial killers. And now, Notch and his Mojang crew have made it possible for more people in the world to become Minecraft addicts who'll never leave their servers. A console version for the Xbox 360 will be available this winter, but for now you can all enjoy the cubed sandbox wo...

Back in 1982, the Commodore 64 home computer was released by Commodore International for $595 (which would now be close to $1,300). It featured an 8-bit microprocessor, 16-color video microchip, awesome sound chip, parallel and serial capabilities, and a whopping 64 kilobytes of memory, all of which helped make it the best selling home computer from 1983 to 1986. It surpassed anything IBM had out at the time. Its greatest competitors were the Apple II and Atari 8-bits, 400 and 800. And it had...

Designer Brenden Macaluso's Recompute is an eco-conscious desktop PC constructed with sustainable cardboard. Everyone knows you're not supposed to get electronics wet, but seriously, you really better keep this one dry.

Android-enabled mobile devices are taking the world by storm, giving Apple's iPhone a run for their money. And if you're holding an Android cell phone in your hand, getting accustomed to all the flashy features can be daunting, especially if you're new to multimedia smartphones.

David Wang of the iPhone Dev Team has achieved what is considered quite a jaw-dropping hacking feat. Yesterday Wang posted a video of Google's Android operating system up and running on an iPhone. Via CNET:

Hello Java-ers, In the previous two tutorials, we learned about installing the JDK, Installing/CreatingAProject in Eclipse IDE, and data types in Java.
I assume you are on the same network with your router 1 - open a terminal window

Hi Guys, I just decided to throw this out here for anyone who might not be familiar with the utility or would like to do some reading on it.

While the majority of reviews for the Google Nexus 4 have been positive, there are a few things that have irked customers. Two of the most common complaints are the lack of 4G LTE on the phone (which you can activate yourself) and the touchscreen's less than stellar responsiveness. Thankfully, XDA developer trter10 has come up with a solution for this issue by fixing the driver that improves the touch responsiveness of the Nexus 4. All you have to do is download and install an older version o...

So you want to learn the basics of the fantastic language Java, but you don't want to search the Inter-webs looking for a great tutorial. Well you came to the right place, now may I present to you JAVA.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you're going to write the language.

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.