In this video, viewers learn how to install and setup JDownloader on Ubuntu Linux Downloader is open source download manager. It simplifies downloading files from One-Click-Hosters like Rapidshare.com or Megaupload.com - not only for users with a premium account but also for users who don't pay. It offers downloading in multiple parallel streams, captcha recognition, automatically file extraction and much more. Of course, JDownloader is absolutely free of charge. This video will benefit those...

New to Audacity? Audacity is a free, open source software for recording and editing sounds. It is available for Mac OS X, Microsoft Windows, GNU/Linux, and other operating systems.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

I am back this time showing you guys how to theme your kali linux. Being true kali is good for pentesting but when it comes to looks it is lifeless , maybe the kali rolling could be an exception but even that makes you feel bored after a long time . So in this tutorial I am gonaShoe you how to theme up your kali

I wrote a python script that allows you to easily ask what service runs on a specific port and vice-versa. Now, I am sure that such a program already exists on our lovely linux OS's, but... I didn't think of that before I started, and haven't found it yet. So if you haven't found it yet either, maybe you'll find this of some use. It's just called getport. If I have a port number, and want to know what services run on that port, I do:

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.

Everybody is going digital these days, so everybody has a reason for software like HandBrake. You can save your entire DVD collection on your computer in digital files, and you can convert videos into different formats. Check out this video tutorial on how to rip DVDs and convert videos on Ubuntu Linux, Windows, and Mac.

There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

In this in depth, four part series learn how to draw a cartoon dog. The adorable puppy you will be learning to draw is top notch and would fit in nicely in any children's book or comic strip.

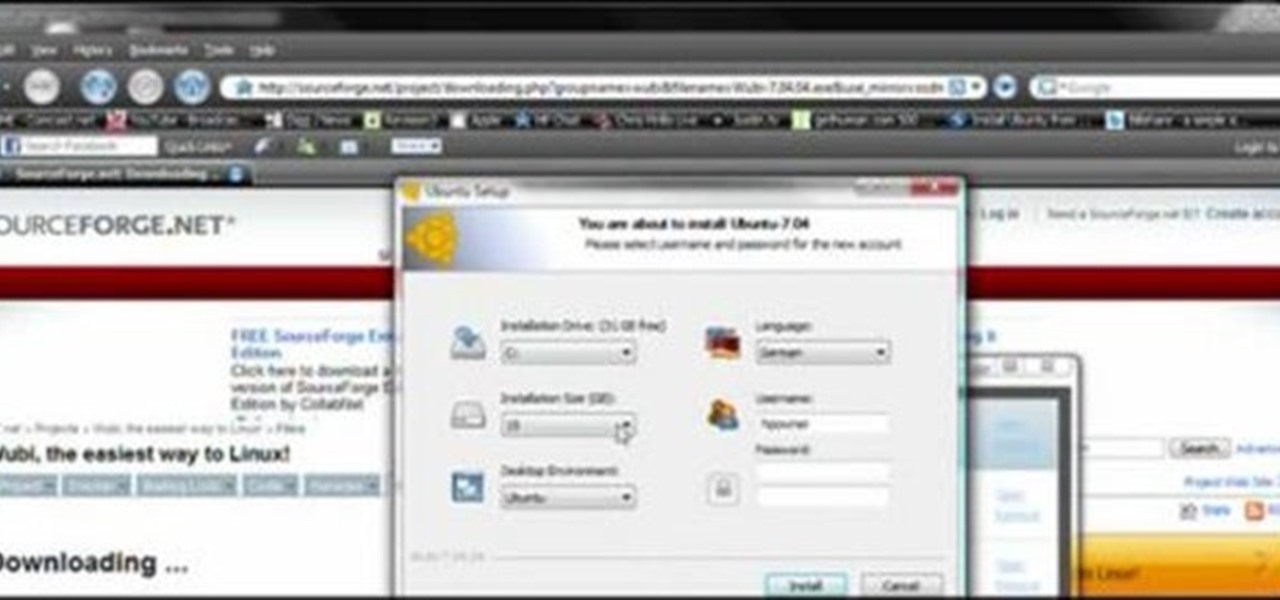
This is a easier way to install Ubuntu with out having to partition your hard drive. Wubi (www.wubi-installer.org) allows you to boot into Ubuntu by saving a file to the boot folder in Windows Vista or Windows XP. You can always uninstall Ubuntu easily without any complications to Windows Vista or Windows XP. This is not VM ware.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Recently I was trying to install Kali Live on a USB drive with persistence and struggled to find a tutorial online that was simple and actually worked. After some trial and error I figured out how to do it correctly and decided to make an article for anyone who is experiencing the same difficulty I did. You will need an USB with at least 8GB. Mine is 132GB, nice and large.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

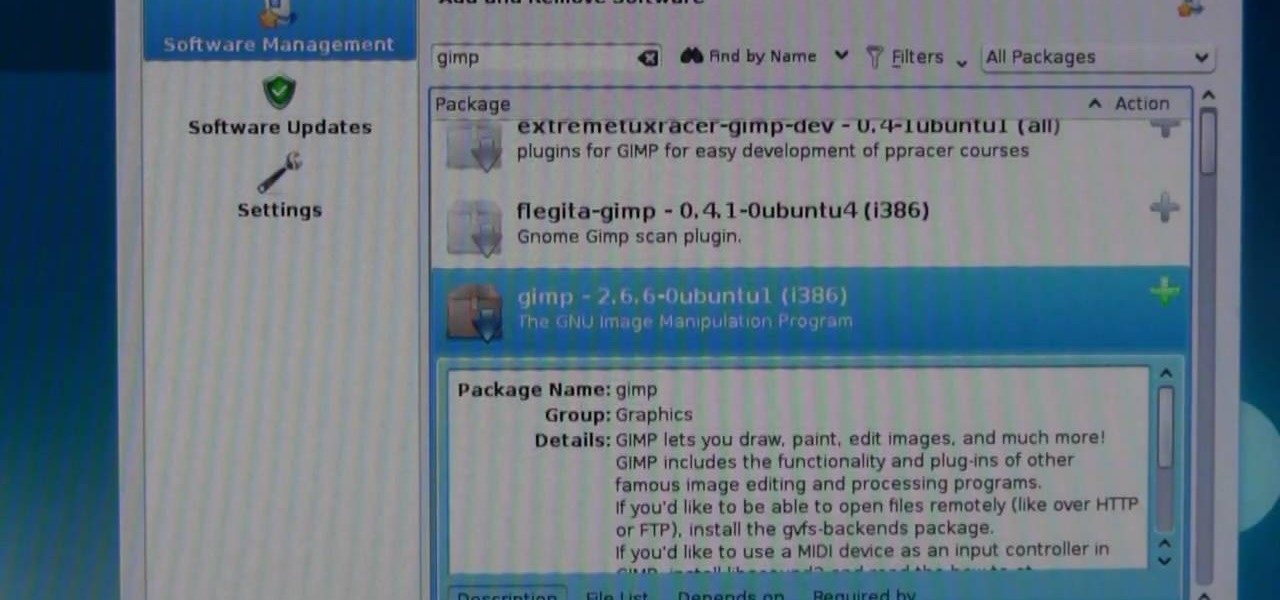
Finding Linux hard to handle after using Windows? Well this should help, here is how to install software on Linux. Start off by clicking on application launcher. Here go into applications, then into 'system' where you should find software management. In this program go straight into the settings and then edit software sources. Under 'downloadable from internet' make sure every option has a check against it. Now press the software management tab on the side. Now this is where you can get which...

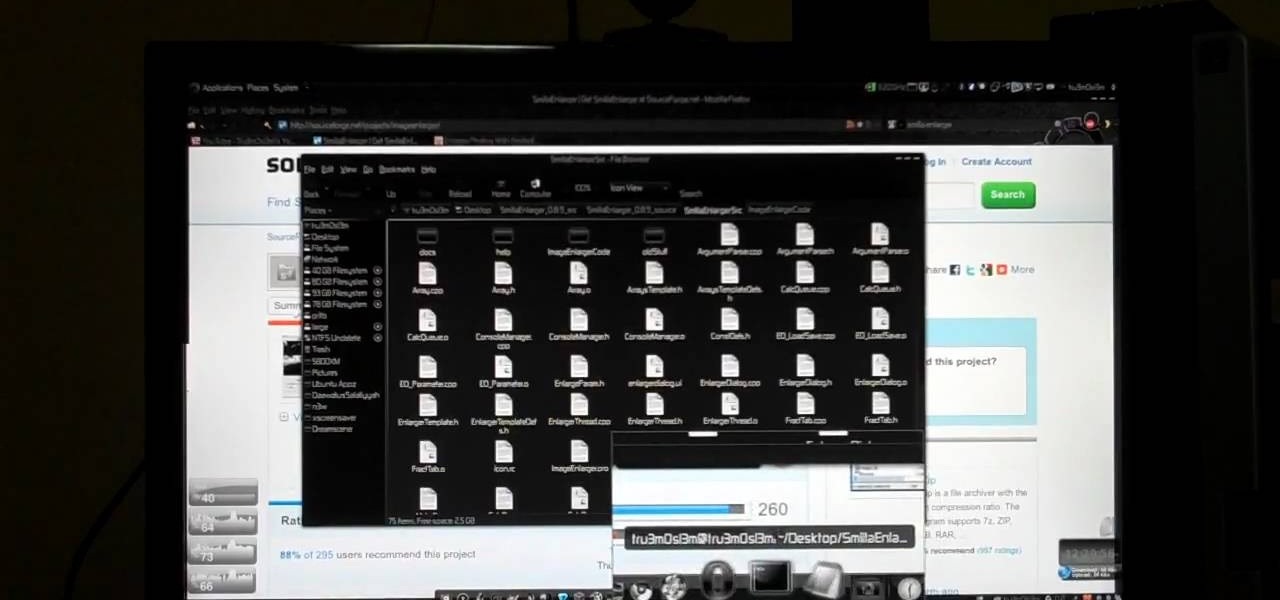
Ever hear of SmillaEnlarger? It's a small graphical tool (based on QT) to resize, especially magnify bitmaps in high quality. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

If you are interested in installing Ubuntu on your Samsung Galaxy Tab 10.1 Android tablet. You can download Ubuntu and ADB here. Root Ubuntu Linux on top of your Android OS with Ubuntu running like a virtual machine.

Need to print something but you're on the go and only have your smartphone or iPad with you? No worries! This tutorial shows you how to use a little app called Dropbox to print to your home printer anywhere, anytime, with any mobile device. Print THAT!

Blip TV user Mr. Root teaches you how to mount an ISO image file using the Unbent Linux terminal. To do this and have access to the files inside of an ISO, without unarchived it, start the terminal. Type in dirk CD. Make sure the ISO image is on your desktop. Then type in sud o mount -o loop -t iso9660 and then the name of your image file, followed by CD/. This will create a new disk drive, which can be seen on the desktop. You can explore that disc like a real one. To unmounted your image, s...

Here is the answer to the question that a lot of people have asked lately, "How does one install Linux Ubuntu on Windows without causing any modifications in the original boot record of the PC?" Software wiz-kid Matt Hartley walks the viewer through a step-by-step process of installing Ubuntu on a Windows-driven computer. The secret is to download Ubuntu to a CD instead of downloading and installing it directly on the hard drive of one's PC. This also ensures that the Ubuntu is easy to delete...

Rolling over is a simple trick that any dog can master, and it will help you build confidence in your dog. Learn how to teach your dog to roll over with this how to video.

Learn a quick fix that'll patch up your slow Internet connection on Ubuntu Linux 7.10

Two computers, two displays...one keyboard and mouse. Molly Wood from CNET shows you how a free software app (Synergy) can make beautiful music between PCs, Macs, and even Linux.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

Valentine's Day is upon us, and it's the perfect time to show those you love (or like) how you feel about them by making them a homemade sweet treat.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

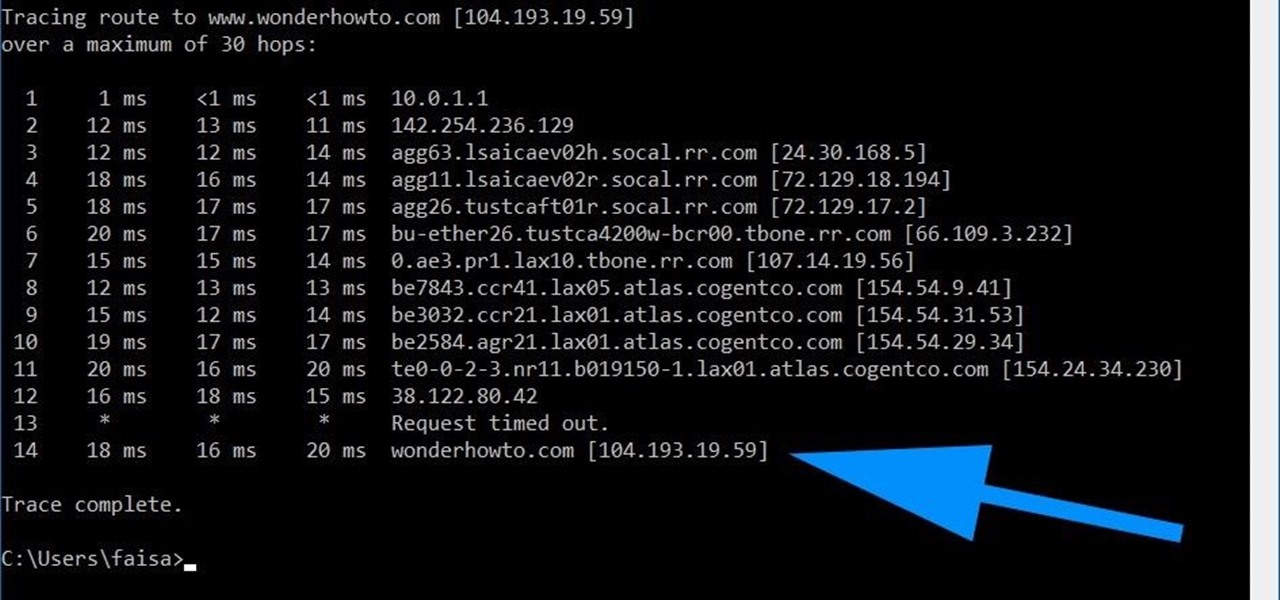
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

Of course, you'll want other people to be able to interact with your program. Linux sets up a command shell automatically, but if you're programming with Python on a Windws machine, you'll need to do it manually - and this video shows you how.