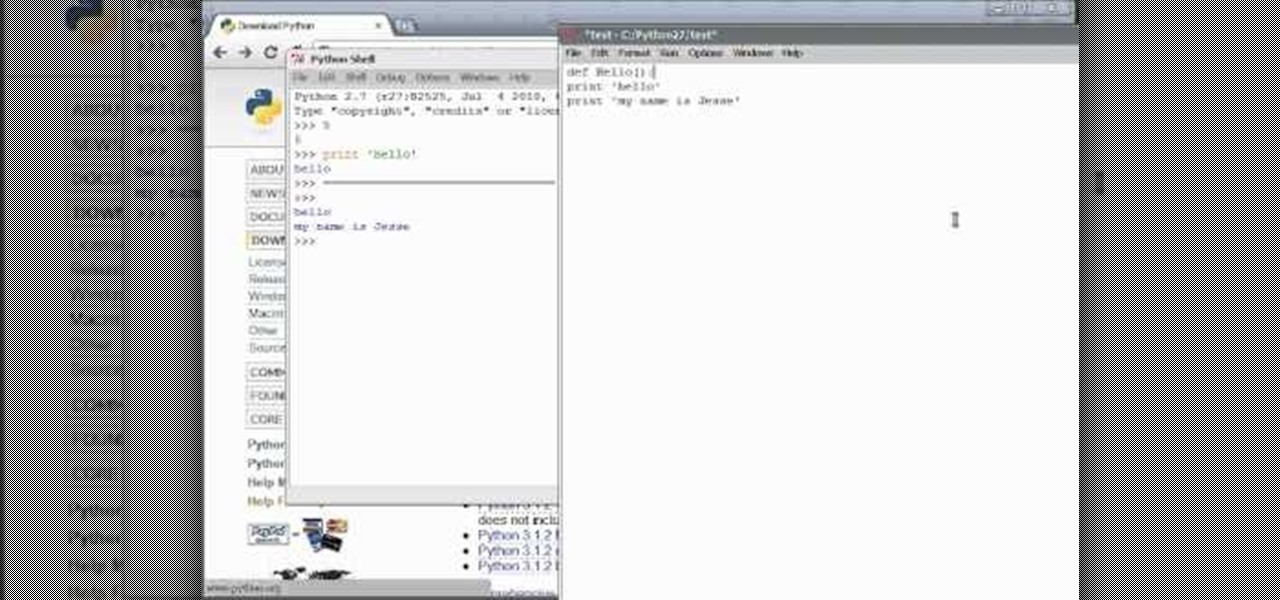
Python can be used for games, websites and operating system GUIs; and you can work with it on PCs, Macs or Linux machines. This tutorial shows you how to install the compiler and get started teaching yourself how to program in Python.

In this video tutorial, we learn how to use the greenpois0n jailbreak tool to jailbreak an Apple mobile device running iOS 4.1 from a Microsoft Windows (or GNU/Linux) PC. For detailed, step-by-step instructions, and to get started jailbreaking your own iOS 4.1 iPhone, iPod Touch or iPad, watch this hacker's how-to.
In this tutorial, you'll learn how to share a single keyboard and mouse across multiple Windows, Mac or Linux computers with an application called Synergy. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.
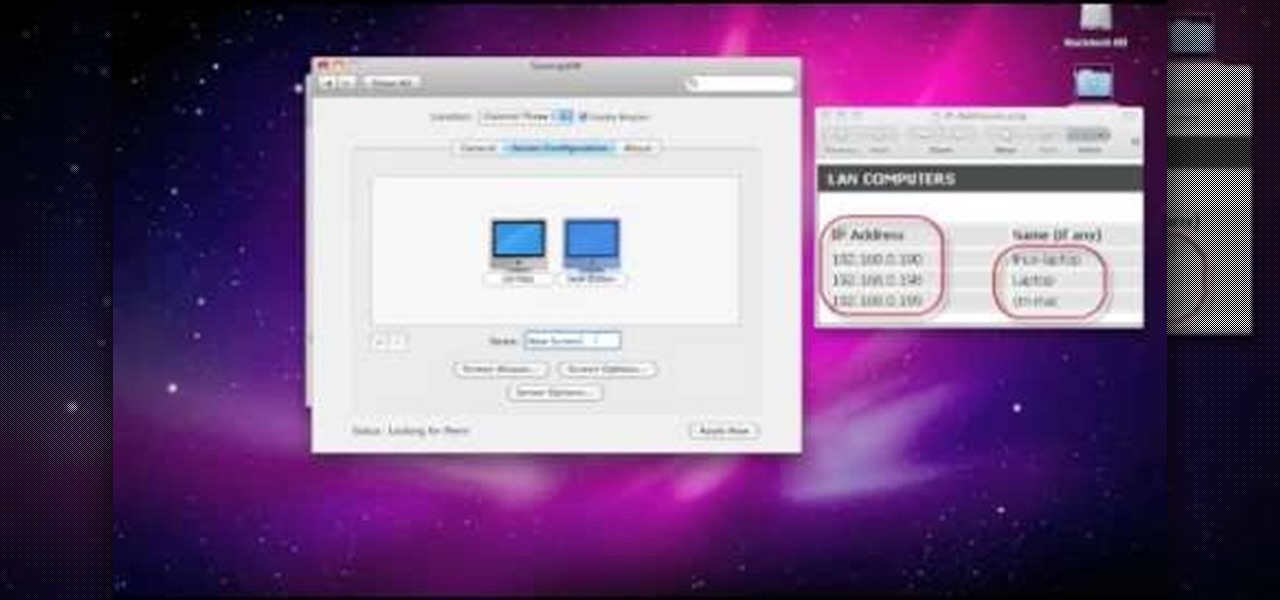
In this clip, you'll learn how to set up and use Synergy to control multiple Windows, Mac or Linux computers from a single keyboard and mouse. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started using this trick yourself, take a look.

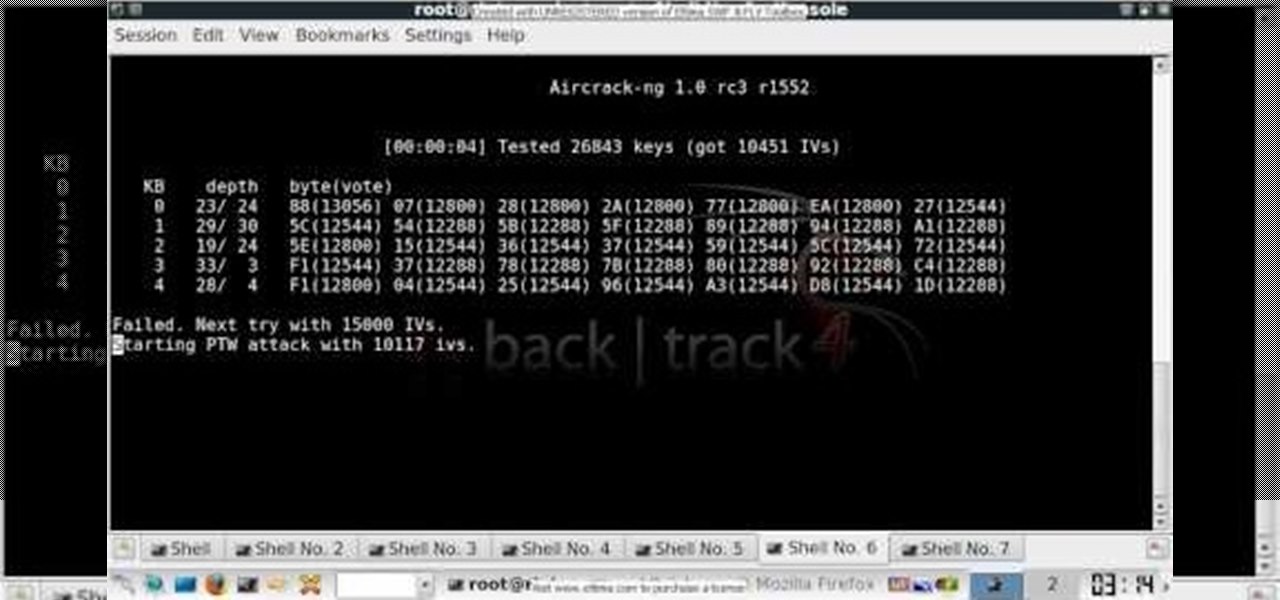
Want to test the security of your WEP WiFi wireless network? In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

By partitioning the hard drive on your Mac computer, you can install multiple versions of Mac OS or install Windows or Linux on the other other partition, increasing your computer's compatibility. This video will show you how to create a new partition quickly and easily on any Mac.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

If you have Ubuntu Linux installed, and the GNOME desktop manager, this video will help you navigate the features and functions. Wlakthrough the workspace and see what you can do! If you're a Windows or Mac user thinking about installing Ubuntu, watch these video tutorials and walkthroughs about Ubuntu and compare for yourself before you make the plunge.

Puppies are so adorable, but they can also be a lot of hard work at times. Training your puppy to go potty is often times a very daunting task. This video will be showing you how to easily potty train your puppy in just a week. Learn when the best times to take your puppy out for a walk are and how frequently you will need to do it during the day. Follow this tutorial and find out all you need to know in order to successfully potty train your puppy in a short amount of time.

What could be more Southern than catfish? But how do you cook it up? Betty shows you a recipe for delicious broiled breaded catfish!

First in the training for a German Shepherd is that your dog should start the very first day you bring your German Shepherd puppy or adult home. In general, Dog obedience training benefits are to give proper mental and physical activities. Secondly, there should be existence of friendly relation (bond) between you and your dog. The third is to ensure that your dog's safety and happiness. Lastly correct many types of dog nuisance behaviors like digging, barking and chewing etc. Two levels of D...

Watch this informative video tutorial on how to create shaped photo collages with Shape Collage. Shape Collage is an automatic photo collage maker that creates collages in different shapes in just a couple seconds. You can create picture collages in the shape of a rectangle, heart, text, or logo, with just a few clicks of the mouse.

From housebreaking to traveling, crate training a puppy or dog can have long-term rewards for both owners and pets. Watch this how to video to learn how to teach a dog to shake hands.

Guinea pigs rarely need baths, but if your furry friend is dirty or oily, a quick wash is a good idea. He’ll squeal in protest now, but he’ll thank you later. Watch this Howcast video to learn how to bathe your guinea pig.

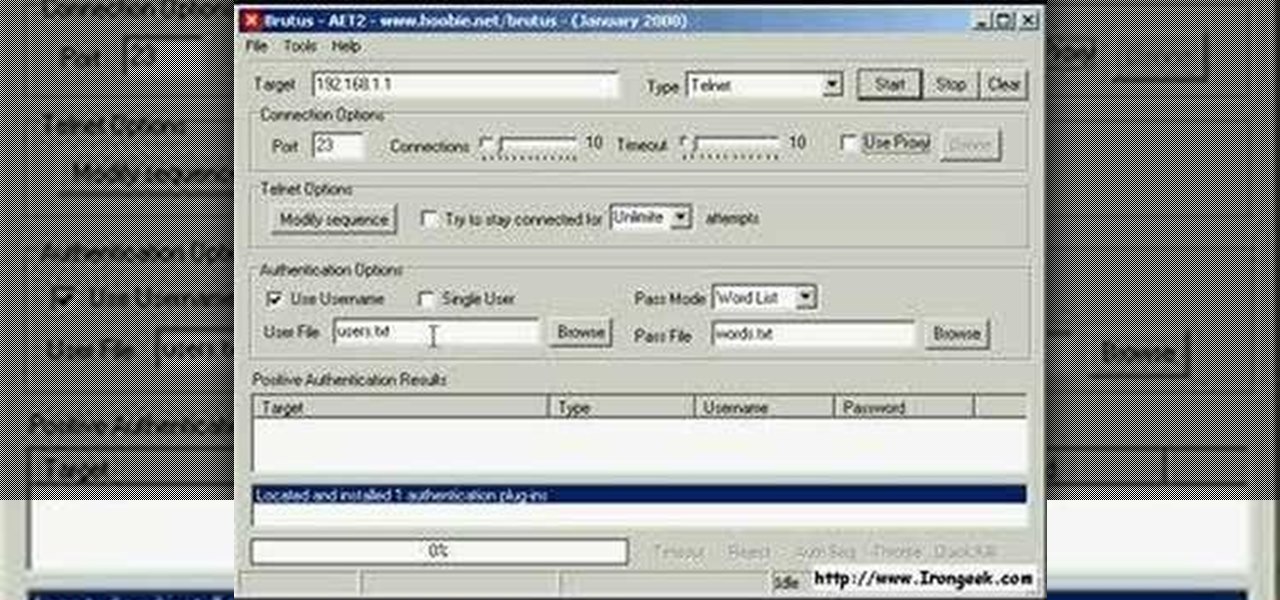
Brutus, first made available in 1998, is one of the fastest, most flexible remote brute-force password crackers you can get your hands on - it's also free. It is available for Windows 9x, NT and 2000. In this video tutorial, you'll learn how to use Brutus to crack a Linux box a running telnet daemon. For more information, and to get started hacking with Brutus yourself, watch this video tutorial.

This video demonstrates how to install Webmin via SSH. Once you've downloaded the Webmin interface package, you'll want to install it onto your serve. In order to do that, you'll need to depackage it. If you're new to Linux or otherwise unclear about how to proceed, then watch this video for step-by-step instructions.

In this instructional video, learn how to transfer files from your Windows PC to your iPhone or iPod Touch using DataCase. Datacase basically converts your iPhone or iPod Touch into a wireless drive that you can access your information on the Mac, PC, or Linux.

A brief overview of the removal of Windows, and the downloading and Installation of Fedora. The end is a montage of screen shots taken during the install.

A how-to on how to share files and folders from Ubuntu to Windows XP and XP to Ubuntu.

Want to create an instrumental or a cappella from a song? Learn how to remove vocals or instruments from MP3s using a freeware program called Audacity for Windows, Mac, and Linux.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

I spent hours writing a guide on how to record a screencast, or record what is on the desktop, and convert it. I then found out that this is much simpler & faster and doesn't even involve opening the commandline.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

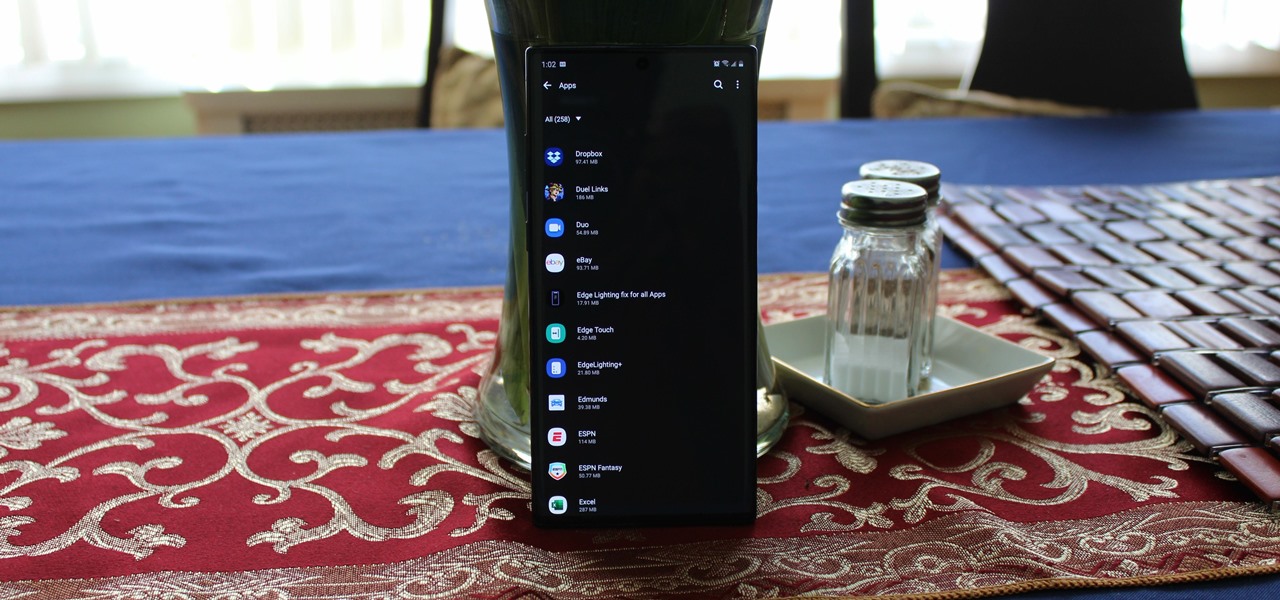
You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Google I/O is like Christmas for Android enthusiasts. Every year, this conference showcases new and upcoming features for the world's leading mobile operating system, and this year's was no different. Shortly after announcing Android M, Google released a preview version of the upcoming firmware for Nexus devices.