TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked features that you may not be aware of.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

They're finally here — Samsung has officially revealed the Galaxy S9 and S9+, which run Android Oreo out of the box. Since we've spent plenty of time with the Oreo beta for the Galaxy S8, we already know about some of the best new software features coming to the Galaxy S9. Like previous updates, Samsung has enhanced its software with a fresh look and brand new functionality.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

Kylo Ren, conflicted villain of the new Star Wars trilogy, will surely be a major presence again this Halloween, with The Last Jedi fast approaching. His costume, all black and layered, complete with dark-side helmet and crossguard lightsaber, seems quite perfect for Oct. 31 — as well as your next DIY project.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

WWDC 2017 is right around the corner, where Apple is expected to reveal iOS 11, the newest version of their mobile operating system. There have been many rumors floating around about what iOS 11 will have in store for us, but not all of those features will end up in the final product — and a lot of the features you want won't actually make the cut, either. But that doesn't mean we can't hope for the best.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your time to understand why Netflix seems to cause so many headaches and what can be done about it.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Almost any video you could want is on YouTube for free, including those very high quality 1080p music videos. You just have to put up with a few ads. But what happens if you're going on a trip and won't have any Internet access? How will you enjoy your favorite YouTube vids?

Hello again, faithful readers. For today's lesson, we will be learning the correct way to restring and tune an electric guitar. I almost wasn't going to post this because it is so basic. But, as with many basic tasks, there are a lot of people who know how to do it, but can't really do it right. If you are a new guitarist, this is an essential piece of maintenance work, because guitar shops usually charge way too much for this task. Of course, I'm kinda cheap, so even 5 bucks is too much for ...

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

Thrift stores! As a Steampunk, they can be your best friend, but it's easy to make a tragic mistake. This hands-on guide will help you navigate the murky waters of successful thrifting in order to find the hidden gems that will make your Steampunk outfit complete!

Apple announced the new iPhone 16 and 16 Pro series models on Sept. 9, and the focus on this year's smartphones was Apple Intelligence with an even smarter Siri. But generative artificial intelligence isn't the only new feature these devices come with. There are improved cameras, more advanced processors, new buttons, and more.

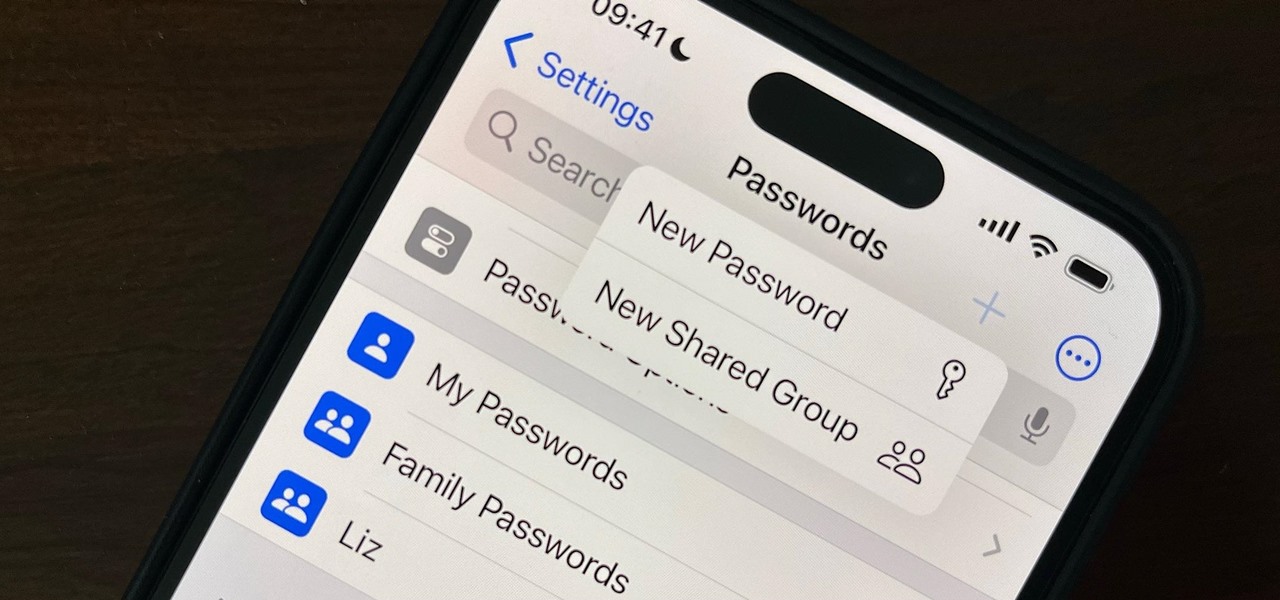
Previously, you'd have to use a third-party password manager on your iPhone, iPad, or Mac to securely share passwords with other people or groups outside of AirDrop range. And while apps like 1Password, Bitwarden, and Dashlane let you store passkeys, only 1Password has added support for passkey sharing so far. Now, Apple itself makes sharing passwords and passkeys much, much simpler.

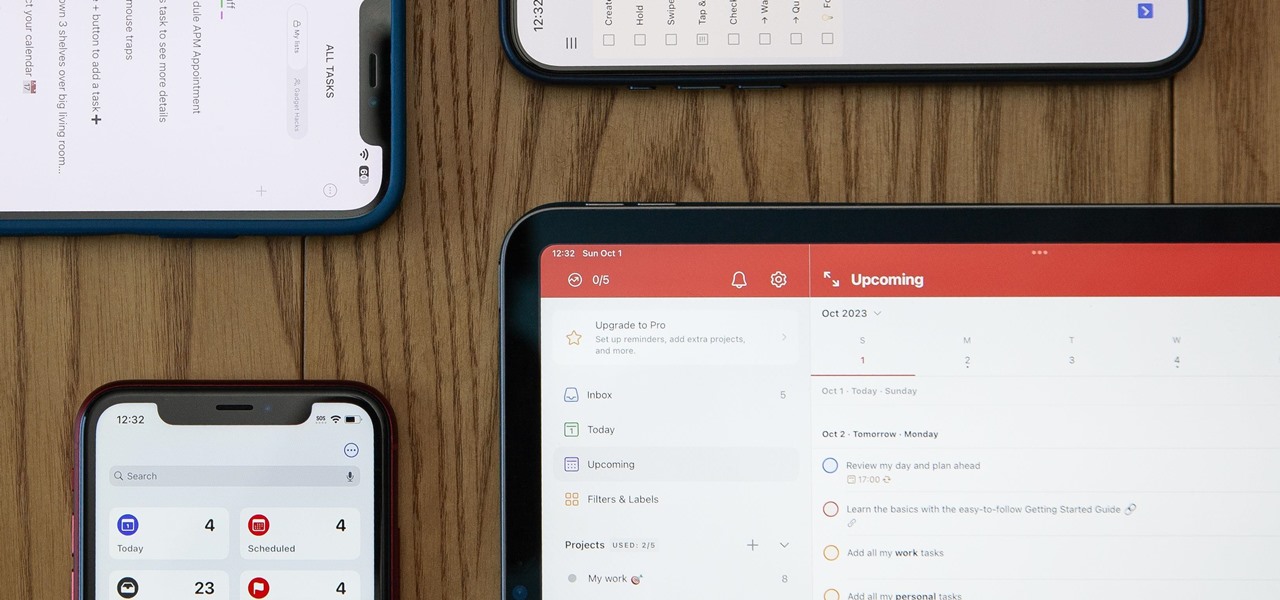
When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

Apple's upcoming iOS 17 is expected to include many new features first seen on Android, but there are also some exciting, unique features that Android needs to steal pronto.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

Apple's Dynamic Island is an animated, interactive isle surrounding the front-facing camera on the iPhone 14 Pro series. It's a small capsule when nothing is going on but fluidly stretches across the screen for notifications, alerts, and ongoing activities like music, timers, and directions. It can even expand with controls and more information. And now, you can get Dynamic Island on your Android phone.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

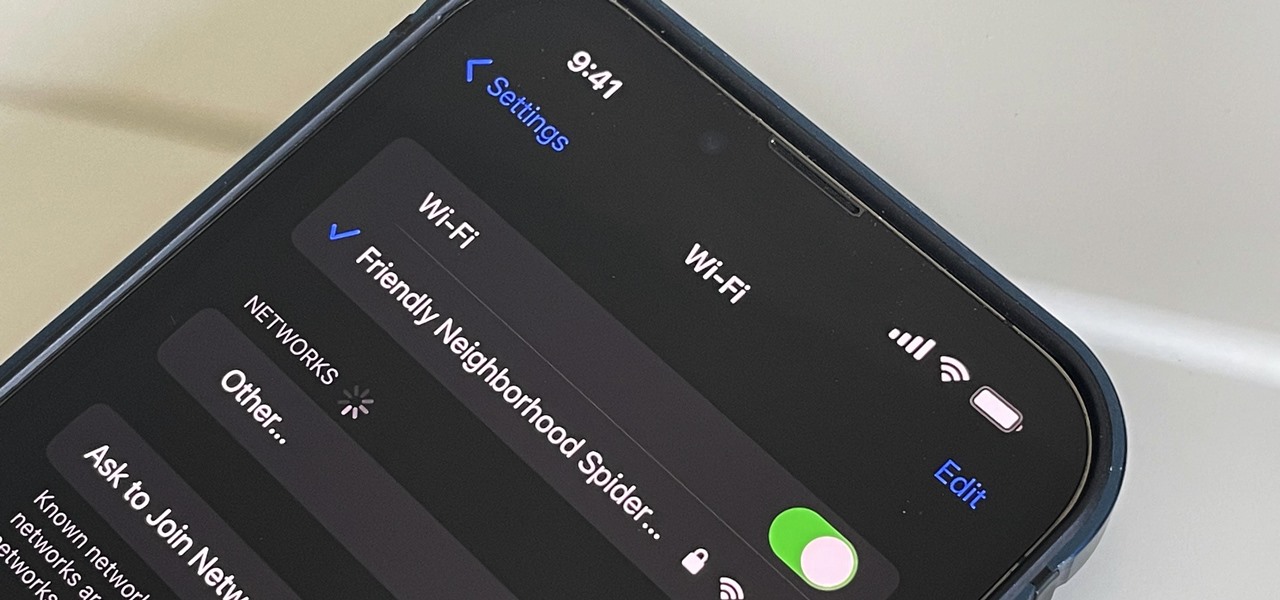
For years, Android has provided easy ways to view all the Wi-Fi networks you connected to in the past, and you can even see the saved passwords in plain text. With iOS 16, Apple finally gave us a similar way to view saved Wi-Fi hotspots, copy their passwords, and remove old ones without being near their access points.

You may use Safari on your iPhone or iPad to open links and browse the web, but there's so much more it can do for you. On updated software, you can implement third-party Safari extensions in your browser that go above and beyond content blocking, sharing, and performing basic actions.

You can set a GIF as the wallpaper for your iPhone's lock screen, but it won't animate like it does when looking at the image in the Photos app. It's an annoying limitation on iOS, but one that's easily bypassed with a tiny bit of work.

Apple's latest iPhone and iPad software, iOS 15.5 and iPadOS 15.5, became available on May 16, so you can download and install it right now if you haven't already. While there aren't as many new features as iOS 15.4 and iPadOS 15.4 had, there are a few big ones in the U.S. you'll want to know beyond Apple's minuscule "About this Update" information in the "Software Update" menu.

Whether you drop your iPhone into a toilet or your dog's water bowl or regularly take it into the shower or pool, water will likely become nestled inside its speaker grilles. Water exposure causes audio playback through the speakers to soften and sound muffled, and getting that water out is no easy task. Luckily, there's an app for that.

It's super easy to add filters, adjust levels, and crop images using the default photo editor on your smartphone, but there's rarely any built-in tool for removing the background in a photo. A third-party app can help isolate people and objects in your pictures, and we've found a free one that's easy to use, works with high-resolution images, and is available for Android, iOS, iPadOS, and the web.