Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

Your homepage should be the site you most likely need to check whenever you start a new session with Samsung Internet. However, times change — perhaps the site you're currently browsing is just what you need to see multiple times a day. In that case, you'll want to know a quick and easy way to set it as your default homepage.

Soon, kids young and old aspiring to imitate Iron Man will only need to learn how to duplicate Tony Stark's snarky wit, because Hasbro will now supply the augmented reality helmet.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

It was nice while it lasted. Samsung users who managed to get their hands on the Galaxy S8 or S8+ early enjoyed the ability to launch any app through the dedicated Bixby button. Unfortunately, Samsung wasn't all that down with us using the Bixby button for purposes other than its intended use — to provide quick access to Samsung's new virtual assistant.

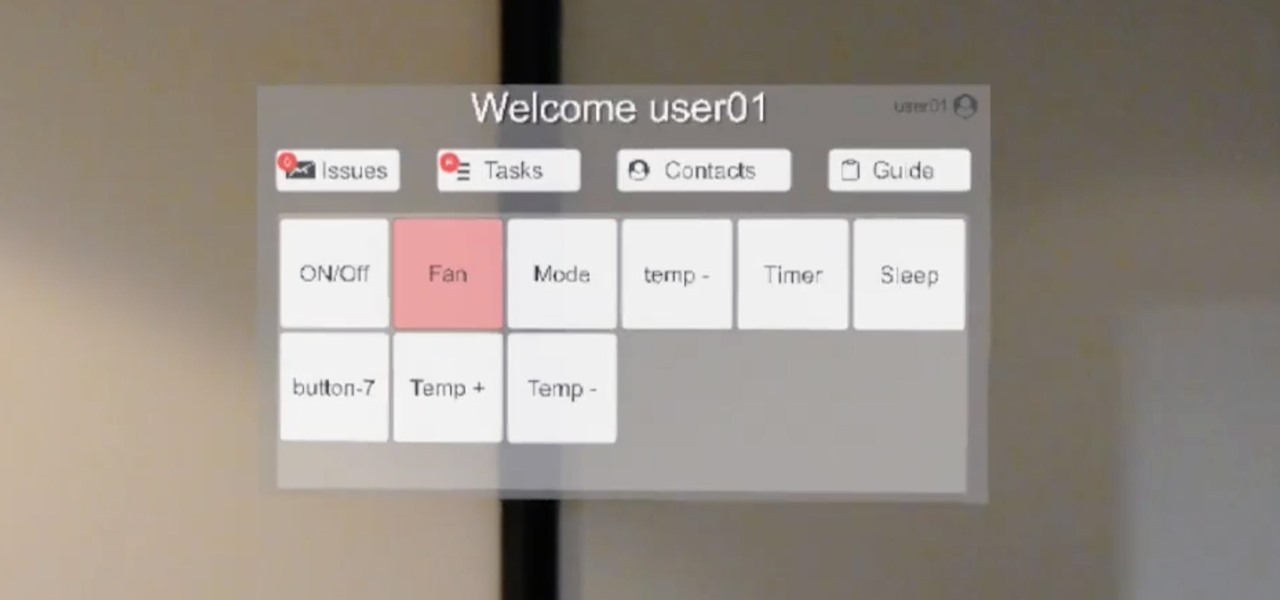
Empea Berlin, a Germany-based company specializing in augmented, mixed, and virtual reality software, released a Facebook video a few months back showing off their experiments in smart home technology. Using a Raspberry Pi and a HoloLens unit, they were able to make a virtual remote control for an air conditioning unit. The remote is complete with various modes, temperature controls, timers, and other features. There have been no updates on this project since they first showed it off, but hop...

With any continuously active software, it can start to become fairly complex after a few years of updates. New features and revisions both get layered into a thick mesh of menu systems and controls that even pro users can get bewildered by. If you are new to a certain application after it has been around for many years, it can be downright intimidating to know where to begin.

Lightning is scary and powerful, yet when harnessed correctly, it can become a beautiful pattern for hand-crafted wooden furniture. Muchd like Zeus in ancient mythology, Canadian Woodworks is harnessing the power and beauty of lightning, but they're doing it for aesthetic purposes.

We can't be in two places at once, but with virtual touch interfaces we can theoretically use a machine to act as our second body in a remote location. Over at MIT, Daniel Leithinger and Sean Follmer, with the advisement of Hiroshi Ishii, created an interface that makes this possible.

Would you like to know what your next house is going to look like? With the HoloLens, you can just plop a hologram down in an open outdoor area and find out.

Augmented reality has a variety of applications, but lately the face has been a major point of concentration for many companies. We're all pretty familiar with face swapping by now, but ModiFace employs similar technologies for more practical purposes.

Dinner is meant to be enjoyed after a long day away from home—it shouldn't cause stress or fuss. But for many, that's exactly what a home-cooked meal represents, especially on a work night. The prep work, the steps involved in following the recipe, the numerous amount of bowls, pots, and pans you use, and... worst of all, a sink full of dishes to clean.
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

While change is good, it isn't always welcomed. All software updates with radical redesigns and brand-new features bring at least a few complaints from those accustomed to previous versions. iOS 7 got a lot of flak from iOS 6 users, as did iOS 8 from iOS 7 users.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

Now that the Chromecast development kit has been out for over a month, more and more Android apps are being released or updated to work with the Chromecast.

In this tutorial you'll learn how to fold a nice star from paper without the need for glue or scissors

Carving pumpkins into creepy looking jack-o’-lanterns for Halloween can actually become fairly boring and tedious if you’re doing the same thing year after year. This time, jump into a whole new realm of Halloween fun with some exploding pumpkin faces! I like to call them blast-o’-lanterns, but can call them whatever you want.

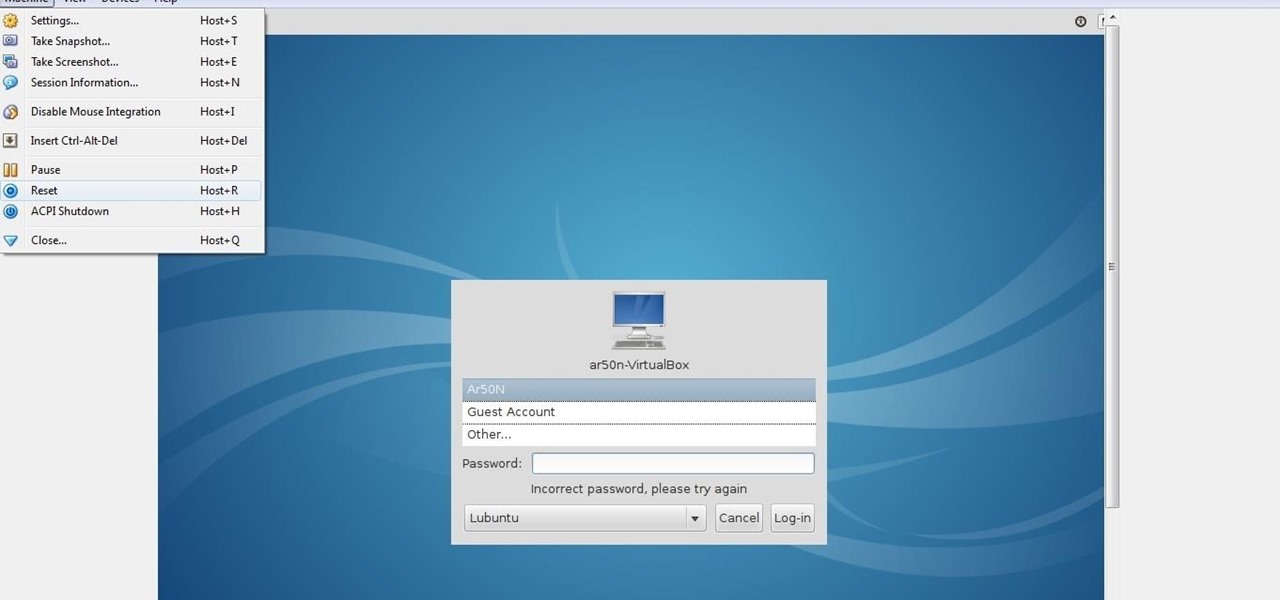
lubuntu is a is a lightweight Linux/Ubuntu that makes it suitable to virtual environments, that you run with VirtualBox to add a secondary machine to your computer or laptop. With this program you can run a number of operating systems upon the same platform.

The fill tool will allow you to alter the appearance of objects in your web design document and can be very useful for marketing purposes. The fill tool can be used to give objects one solid color for simple designs.

The lovely Kato of Steampunk Couture has gone hardcore. For those who prefer to exercise their imaginations a bit more, Voila! Veronique Chevalier in Gearhearts Steampunk Glamour Revue- click here should do... A recent kerfuffle unfolded on facebook's Steampunk Revolution group when a discussion was started by Steampunk R &D''s very own Austin Serkin on the subject of Kato's new foray into steampunk porn, which was, ahem, examined in detail. (Well, figuratively, not literally, since her websi...

The video featured in this article demonstrates the function and design of a powerful form of air cannon that operates using a purpose made valve that opens very rapidly. This allows for a massive amount of pressurized air to be released at once to throw a projectile many hundreds of yards. The design of the cannon also allows the barrel and the air chamber to occupy the same space, and so it is very compact and manageable which makes for an enjoyable shooting experience.

Brains? If you've ever played Plants vs. Zombies, then you already know that brains are a delightful treat for our undead brethren. For those of us still living, we can still indulge in some brain-related dining for Halloween next week. If you're holding a dinner party or just want to make some cool, creepy looking fruit, then this DIY Watermelon Brain is perfect. In order to create this delicious dish, all you will need is a peeler, sharp knife, cutting board, watermelon, and... a brain. Wel...

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

Invented by Philadelphia tinsmith John L. Manson in 1858 for canning and preserving perishables, mason jars are experiencing a major resurgence in the DIY community. In addition to being a handy storage device for both food and non-food items, its old-timey, quaintly antiquated look also makes for good drinking glasses, candle holders, flower vases and eye-pleasing decorations.

You can take some absolutely gorgeous photos using the natural reflection that appears in people's and animals' eyes. With the right angle and lighting, you can even see a detailed picture of what the subject was looking at when the photo was taken. Photo by Martin Cathrae

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Apple released the third developer beta for iOS 13.5 today, Wednesday, April 29. If you're confused where 13.5 betas 1 and 2 are, join the club. This appears to be, for all intents and purposes, iOS 13.4.5 developer beta 3, following 13.4.5 developer betas 1 and 2. The biggest change? The addition of Apple's joint COVID contact-tracing program with Google, which likely inspired the name change.

Decades ago, Japan rocked the automobile industry with its revolutionary manufacturing and car quality, but today that title seems to be moving over to Elon Musk's electric car company Tesla. Nevertheless, Japan isn't done innovating mass-produced hardware.

Disabling clunky, revealing link previews on Google Keep can serve multiple purposes. You know, those expanded versions of the same URL you pasted into your note, except duplicated, tacked onto the bottom of your note, and showing a preview picture. Removing these can help optimize your productivity formula.

With Snapchat making the leap into the smartglasses realm, Facebook had to find a way to try and steal its competitor's augmented reality thunder.

Fans of the friendly neighborhood Spider-Man have yet another way to experience the web-slinger in augmented reality.

It's no secret that the enterprise sector is hot for augmented reality, but the move into the enterprise AR software market by one of the biggest names in industrial engineering announces the technology's arrival loud and clear.

With a fresh infusion of $9.7 Million in funding on its ledger, enterprise augmented reality company Scope AR has now expanded the functionality of its WorkLink platform.