Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

A crick is a sudden, spasmodic pain and stiffness in the neck caused by tight muscles that can absolutely ruin your entire day. It can last for more than one day and can be triggered by the smallest movement of the neck, such as a simple pandiculation, aka a yawn-stretch. Although you can't always prevent them, there are many natural ways to lessen a painful stiff feeling in the neck.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.
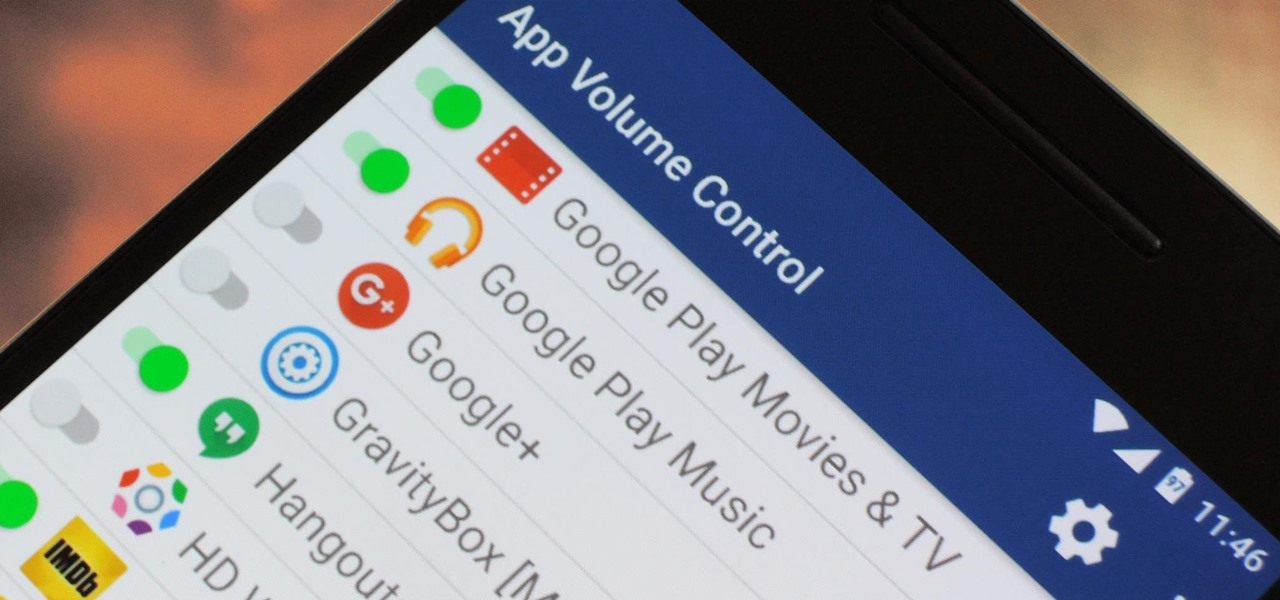
You can do practically anything with a modern smartphone or tablet, so it stands to reason that the apps you have installed may serve vastly different purposes. Picture a game and a video player sitting right next to each other in your app drawer—odds are, you want the sound turned up while you're watching videos, but would prefer that the game was muted or a little lower. As a result, we're constantly tweaking volume levels to get the best experience.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Cake decorating is one of those activities that used to leave my hands sticky and my spirits dampened. No matter what I seemed to do, the final result always ended up looking like a preschool art project.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

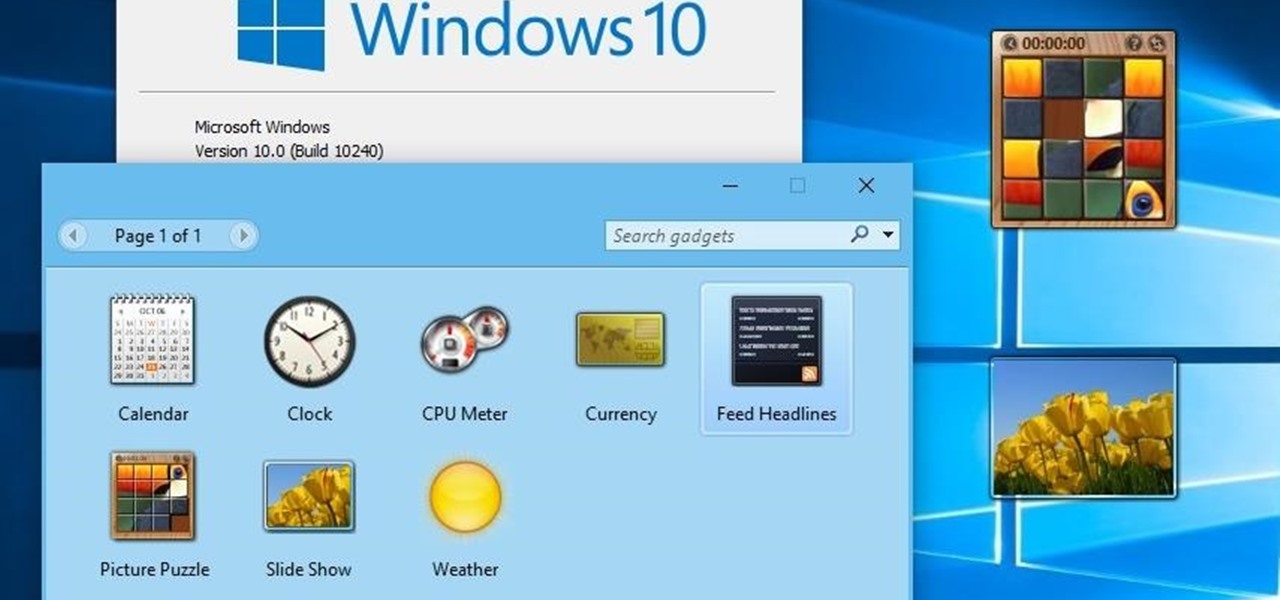
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

There is no greater food to master than steak. If you can make a steak that's only marginally better than your neighborhood Applebee's, you'll still have friends waiting outside your door for steak night. And if you can make steak as good as that expensive gourmet steakhouse you went to for your birthday? Well, your popularity is about to increase dramatically.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

There are several reasons that you might want to restore the factory firmware on your device—maybe you need to send your phone back for warranty purposes, or perhaps you're getting ready to accept an over-the-air update and need to unroot first. In some cases, reverting to the stock firmware can even resurrect a soft-bricked phone.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

It wasn't too long ago that I showed you how to unlock the LG G3 bootloader and install TWRP, and while the process was extremely easy, the custom recovery can look a little intimidating to new users. Even long-time users who know how to navigate it find it boring to look at, as TWRP has had the same basic aesthetics since its creation.

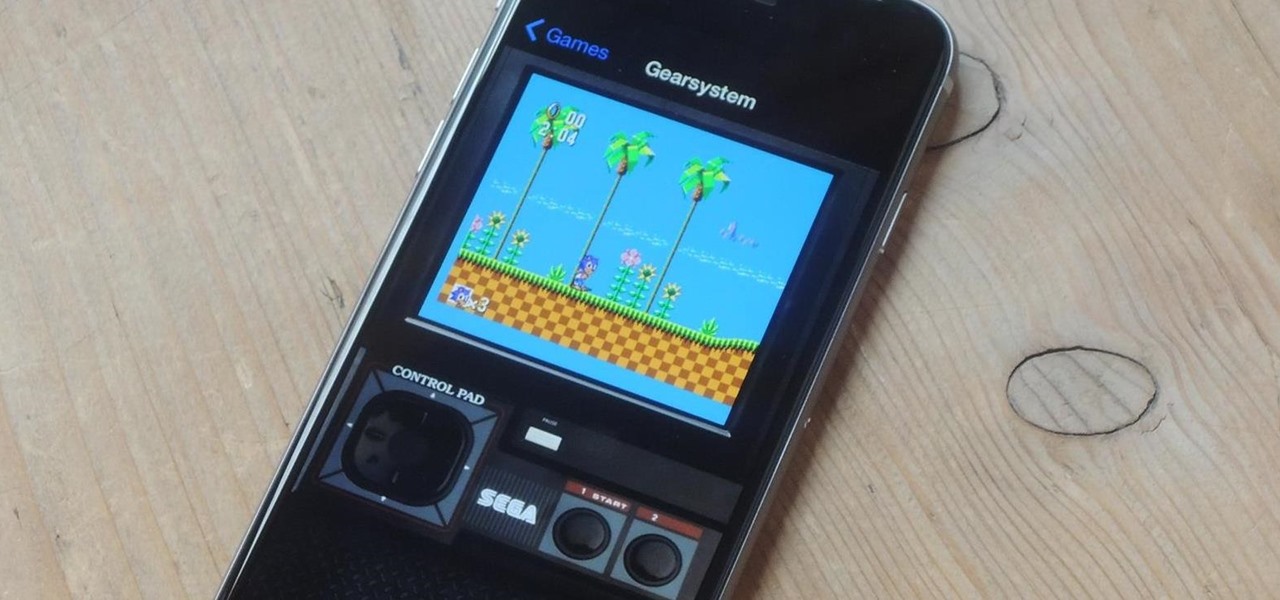
The Master System, more popularly referred to as the Sega Master System, or SMS for short, is a video game console that was released in the mid-1980's as a direct competitor to the original Nintendo (NES).

"Cooking" with liquid nitrogen seems like one of those activities that should be strictly limited to pros who are appearing on Top Chef, but it's the only way you'd ever be able to make Dippin' Dots at home. If that isn't enough of a reason for you to get some LN2 for your kitchen, check out this dose of pretty:

There are many different reasons that you might want to revert your Samsung Galaxy S5 back to stock. The main one would probably be that you need to return your device to the manufacturer for warranty purposes. And if you've used root to modify system-level files and components, you'll need to undo those changes before you send the phone back.

Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Amazon released the Kindle Fire HDX back in late-2013, and if you picked one up or received one as a gift, you've probably had a good amount of time to get to know your tablet.

Sometimes when non-Asians go to ramen bars, they're mildly weirded out by watching the patrons eat. To the uninitiated, the eating behaviors can seem kind of extreme. Why are people hovering over their bowls like animals at a feeding trough? Why do they let endless lengths of noodles dangle from their maw as they slurp—very, very loudly—over their bowls of broth?

As Matias Duarte and the team over at Google's Android Design department ready their wares, they've given us a preview version of the upcoming "L" release of Android to try out.

Geohot's Towelroot exploit made rooting the Galaxy S5 so easy that it was almost unreasonable not to try it out—even for the first-timers out there. This, of course, meant that folks who didn't truly need root for their usage went ahead and got Superuser privileges anyway.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

HTC thought it best to cover their own ass by placing a red warning whenever you start your device if you've unlocked your bootloader. While it may help them identify a tampered phone, it does not help you in any way. Luckily, XDA member santod040 created a modified HBOOT that removes the "This build is for development purposes only..." text for you. While this will modify HBOOT, it will not change your unlocked or S-Off status.

One of the most common complaints about the Nexus line of devices is that they don't have expandable memory.

If you've ever used IFTTT, you know how well it can automate your online world. The premise is simple—If This, Then That—but the results are powerful. From automatically printing images based on hashtags to getting around Twitter bans, the service is quite useful with a wealth of possibilities.

While the Galaxy Note 3 and Galaxy S4 are enjoying their official KitKat updates, those of us with Note 2s are left to play the waiting game. While we know our devices will eventually see an update to Android 4.4.2 KitKat, it's unclear when an official update for our devices will come.

I regularly listen to music on my Nexus 7 while working or playing my Xbox. It's light and easy to carry around, and has basically become an extension of my body. The only thing that bugs me is having to constantly turn the screen on to pause or change music tracks. Even if I can do it from my lock screen instead of the actual music player app—I don't want to.

The advent of the Google Nexus 4 seemed too good to be true—high-end hardware, unlocked and contract-free at a low price. As time went on, however, we began to see the compromises. The camera was "meh" at best, and most egregiously, it shipped without LTE functionality.

With the release of iOS 7, the entire Internet was abuzz with what's the exact opposite of excitement as Apple's servers were overloaded, causing many download fails of the new operating system. Since then, many other bugs and issues have arisen that are fairly common with new Apple software updates, like iMessage fails and wallpaper complaints (to only name a few).

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.